#androidmalwaredetection résultats de recherche
📢 #highlycited paper 📚 GA-StackingMD: #AndroidMalwareDetection Method Based on #GeneticAlgorithm Optimized Stacking 🔗 mdpi.com/2076-3417/13/4… 👨🔬 by Nannan Xie et al. 🏫 Changchun University of Science and Technology/Jilin Province Key Laboratory of Network and Information…

🔥 Read our Highly Cited Paper 📚 GA-StackingMD: Android Malware Detection Method Based on Genetic Algorithm Optimized Stacking 🔗 mdpi.com/2076-3417/13/4… 👨🔬 by Dr. Nannan Xie et al. #Androidmalwaredetection #integratedmachinelearning
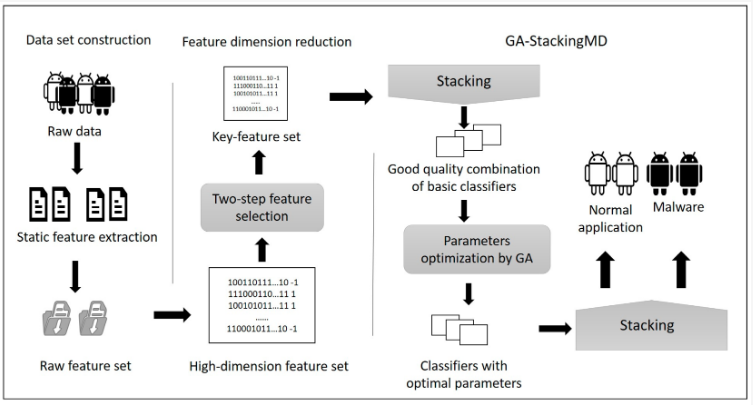
📢 #highlycited paper 📚 GA-StackingMD: #AndroidMalwareDetection Method Based on #GeneticAlgorithm Optimized Stacking 🔗 mdpi.com/2076-3417/13/4… 👨🔬 by Nannan Xie et al. 🏫 Changchun University of Science and Technology/Jilin Province Key Laboratory of Network and Information…

🔥 Read our Highly Cited Paper 📚 GA-StackingMD: Android Malware Detection Method Based on Genetic Algorithm Optimized Stacking 🔗 mdpi.com/2076-3417/13/4… 👨🔬 by Dr. Nannan Xie et al. #Androidmalwaredetection #integratedmachinelearning

🚨 ALERT Google had secretly installed this app on various android devices without users permission. it can reportedly scan through your photo gallery and occupies 2gb of space 😲 Link to uninstall: play.google.com/store/apps/det…

#Opendir sample files: ipscan221.exe, netscan.exe hxxps[:]//kandev[.]com/files/apps/ Handle with caution. Good source for #Malware analysts. Do not download or run samples outside an isolated lab. Report to vendor/CERT.
![cyberfeeddigest's tweet image. #Opendir sample files: ipscan221.exe, netscan.exe
hxxps[:]//kandev[.]com/files/apps/ Handle with caution. Good source for #Malware analysts. Do not download or run samples outside an isolated lab. Report to vendor/CERT.](https://pbs.twimg.com/media/G4sg00QWwAU_tST.jpg)
New Android BEERUS framework for dynamic analysis & reverse engineering BEERUS brings Frida auto-injection, sandbox exfiltration, memory dumps, Magisk integration and more for on device app analysis by @HakaiOffsec #AndroidSecurity #Frida #ReverseEngineering #MalwareAnalysis


Deobfuscating Android Apps with Androidmeda LLM: A Smarter Way to Read Obfuscated Code ✅As a bonus, example of deobfuscating #Crocodilus Malware mobile-hacker.com/2025/07/22/deo…

How #Android provides the most effective protection to keep you safe from #mobile_scams ift.tt/AuanPd9
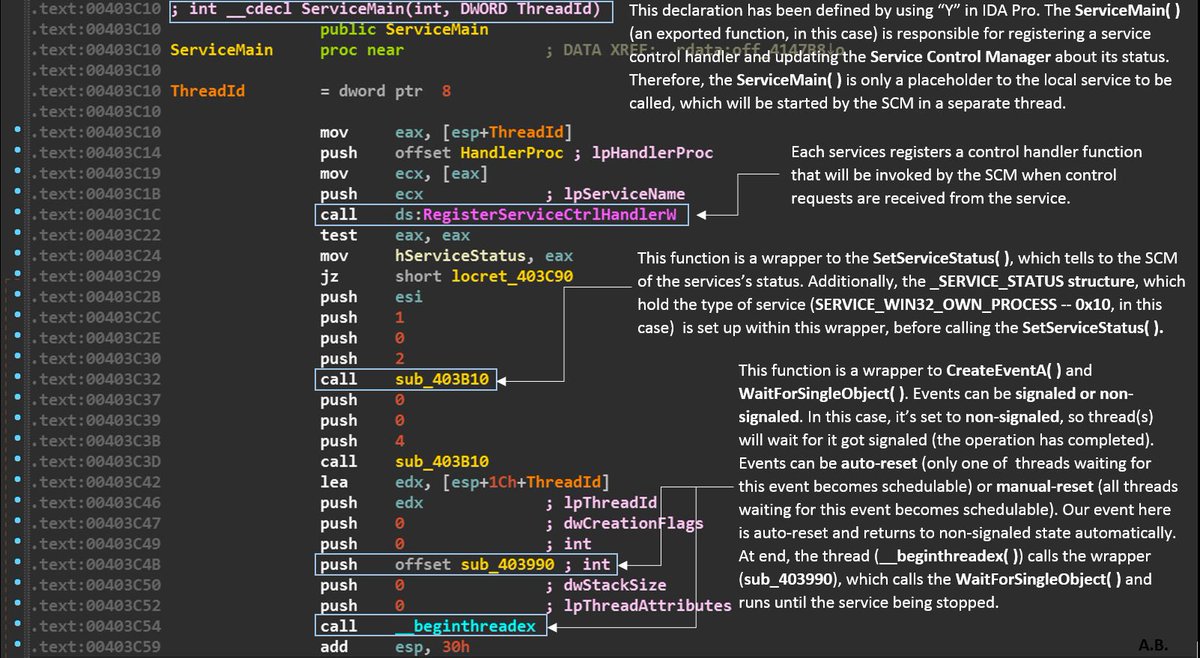
In malware analysis, every detail is important. This picture comes from a malicious DLL, whose exported function is called by an executable (not found on VT). You'll find these instructions several times, so it's relevant to understand what's going on. #malware #CyberSecurity
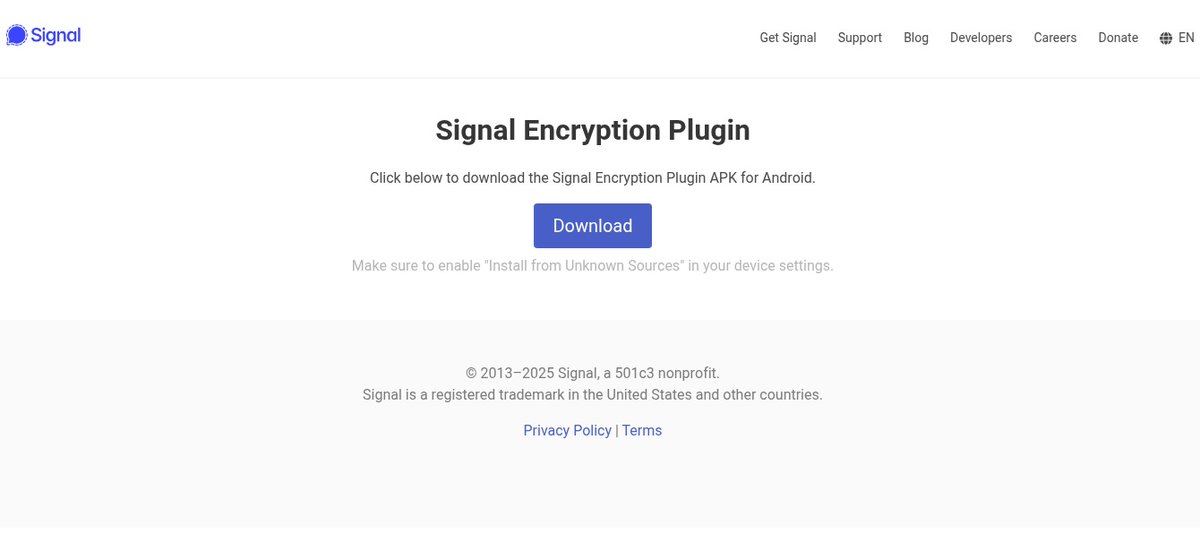
We identified two campaigns targeting #Android users with previously undocumented spyware impersonating #Signal and #ToTok via deceptive websites welivesecurity.com/en/eset-resear… #ESET #ESETresearch

m[.]bureaux[.]fr #France — #Opendir includes .apk & .exe files: Advanced IP Scanner.exe, applock.2.32.7.apk, Anydesk.exe, Anydesk.apk. Domain: hxxps[:]//m[.]bureaux[.]fr/ Handle with caution. Good for #Malware analysts — do not download or run samples outside an isolated lab.
![cyberfeeddigest's tweet image. m[.]bureaux[.]fr #France — #Opendir includes .apk & .exe files:
Advanced IP Scanner.exe, applock.2.32.7.apk, Anydesk.exe, Anydesk.apk.
Domain: hxxps[:]//m[.]bureaux[.]fr/ Handle with caution. Good for #Malware analysts — do not download or run samples outside an isolated lab.](https://pbs.twimg.com/media/G4rC9rPWcAAE-y5.jpg)
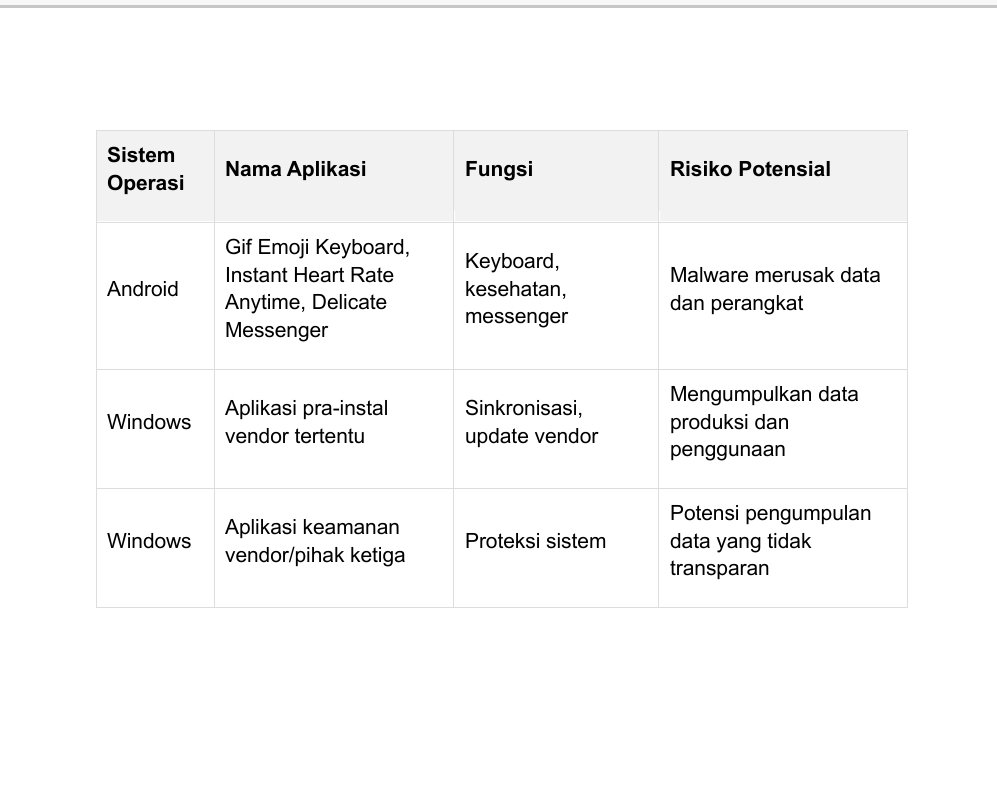
Spyware - Contoh: Fare Gamehub, Hope Camera, Same Launcher, Amazing Wallpaper, Cool Emoji Editor - Risiko: Mencuri data pribadi, merusak perangkat, memantau aktivitas 3. Malware SDK Terselubung - Contoh: Goldoson, SpinOK - Risiko: Menyusup ke aplikasi pihak ketiga,

I've released Malwoverview 4.0.3: github.com/alexandreborge… Malwoverview gathers information from Malpedia, Alien Vault, Polyswarm, URLHaus, VT, Hybrid Analysis, Malshare and ThreatCrowd. It also checks Android devices for malicious packages. #ThreatHunting #cybersecurity




📢 #highlycited paper 📚 GA-StackingMD: #AndroidMalwareDetection Method Based on #GeneticAlgorithm Optimized Stacking 🔗 mdpi.com/2076-3417/13/4… 👨🔬 by Nannan Xie et al. 🏫 Changchun University of Science and Technology/Jilin Province Key Laboratory of Network and Information…

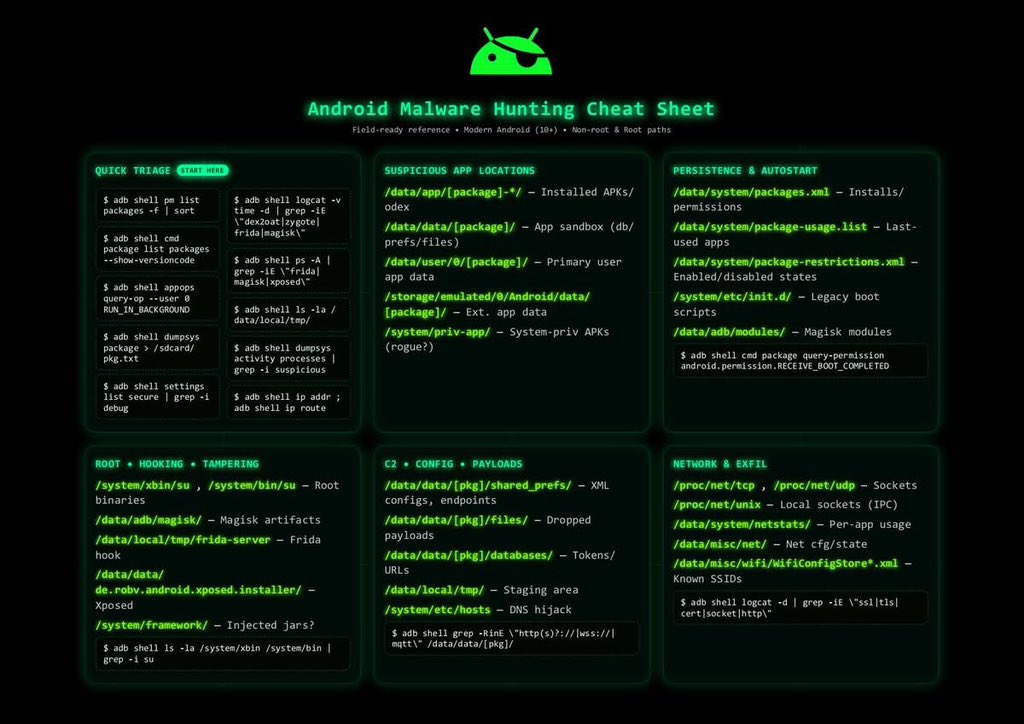
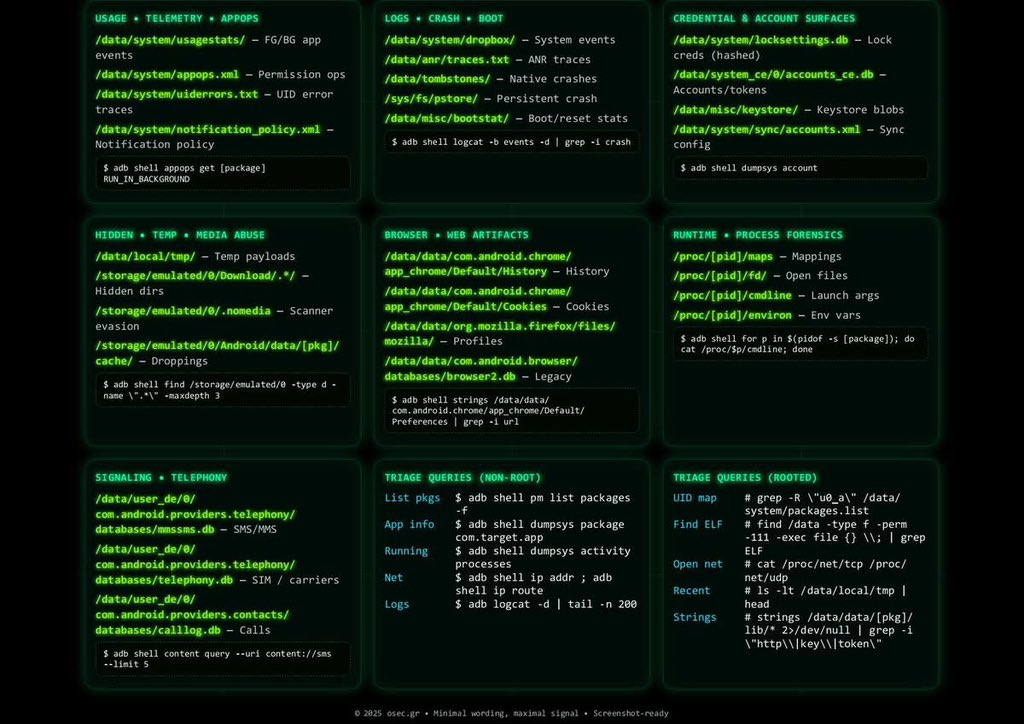
🔎📱 Android Malware Hunting Cheat Sheet Hunting and analyzing Android malware requires the right mix of tools, techniques, and a well-structured process. This cheat sheet outlines the core steps for effective detection and analysis.
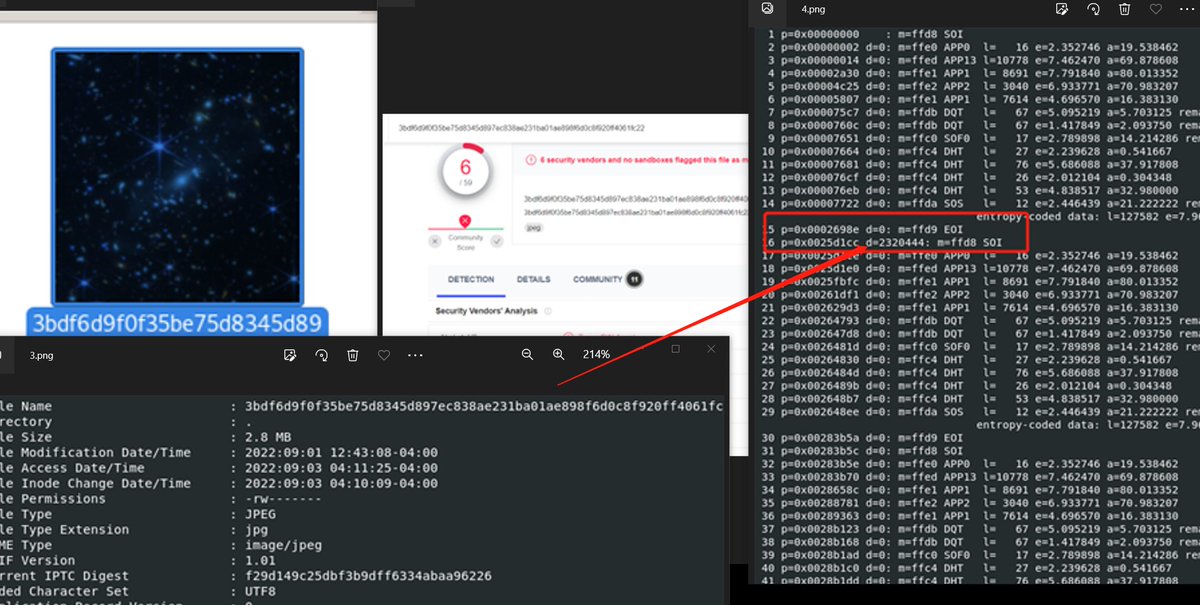
Malware hidden in JPEG images found Jpeg->find segment data>extract hex >decode base64 certutil.exe -dump .\payload.dmp > ./1.bin 1.bin de49baada80d7b2aba474251ac937236 @malwrhunterteam @blueteamsec1 @intrusion_truth @ShadowChasing1



#Opendir sample: fully-kiosk-browser.apk — hxxps[:]//cloudio[.]dedyn[.]io/~dio/apks/ Marked by Google Chrome as “Dangerous”. Handle with caution. Good for #Malware analysts — do NOT download or run outside an isolated lab. Report to CERT.
![cyberfeeddigest's tweet image. #Opendir sample: fully-kiosk-browser.apk — hxxps[:]//cloudio[.]dedyn[.]io/~dio/apks/
Marked by Google Chrome as “Dangerous”. Handle with caution. Good for #Malware analysts — do NOT download or run outside an isolated lab.
Report to CERT.](https://pbs.twimg.com/media/G4sauE7W4AAZVK0.jpg)
A curated list of Android Security materials and resources For Pentesters and Bug Hunters github.com/saeidshirazi/a… #android #cybersecurity #bugbounty

"Aarogya_Setu.apk": 3f69bc4b7fc50db582b13835206d2480acc66919db9123b37cf97f7f3da3b443 C2: johnnj2-37916.portmap[.]io:37916 @Spam404 cc @LukasStefanko @virqdroid
![malwrhunterteam's tweet image. "Aarogya_Setu.apk": 3f69bc4b7fc50db582b13835206d2480acc66919db9123b37cf97f7f3da3b443
C2: johnnj2-37916.portmap[.]io:37916
@Spam404
cc @LukasStefanko @virqdroid](https://pbs.twimg.com/media/EX-UpnIXQAE8eS_.png)
![malwrhunterteam's tweet image. "Aarogya_Setu.apk": 3f69bc4b7fc50db582b13835206d2480acc66919db9123b37cf97f7f3da3b443
C2: johnnj2-37916.portmap[.]io:37916
@Spam404
cc @LukasStefanko @virqdroid](https://pbs.twimg.com/media/EX-UyS-XsAE20yw.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Carson Beck 3,015 posts
- 2. Vandy 11.7K posts
- 3. Clemson 10.8K posts
- 4. Miami 57.5K posts
- 5. Mario 60.7K posts
- 6. Jeremiah Smith 7,782 posts
- 7. Texas 113K posts
- 8. Ohio State 16.2K posts
- 9. Vanderbilt 9,166 posts
- 10. Julian Sayin 6,128 posts
- 11. #HookEm 3,925 posts
- 12. Pavia 4,237 posts
- 13. Caleb Downs 1,322 posts
- 14. Dabo 2,367 posts
- 15. Dawson 4,206 posts
- 16. Caicedo 40.1K posts
- 17. Duke 19.2K posts
- 18. Arch Manning 4,604 posts
- 19. The U 485K posts
- 20. Jeff Sims N/A





















