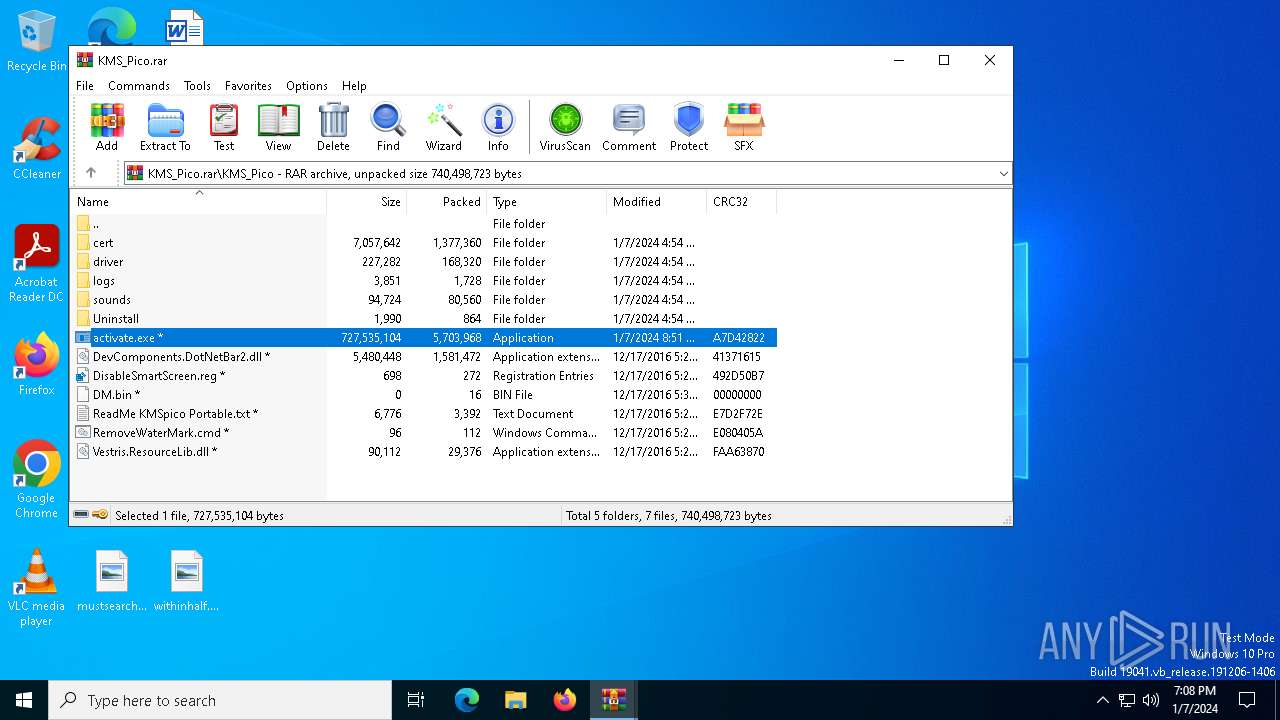
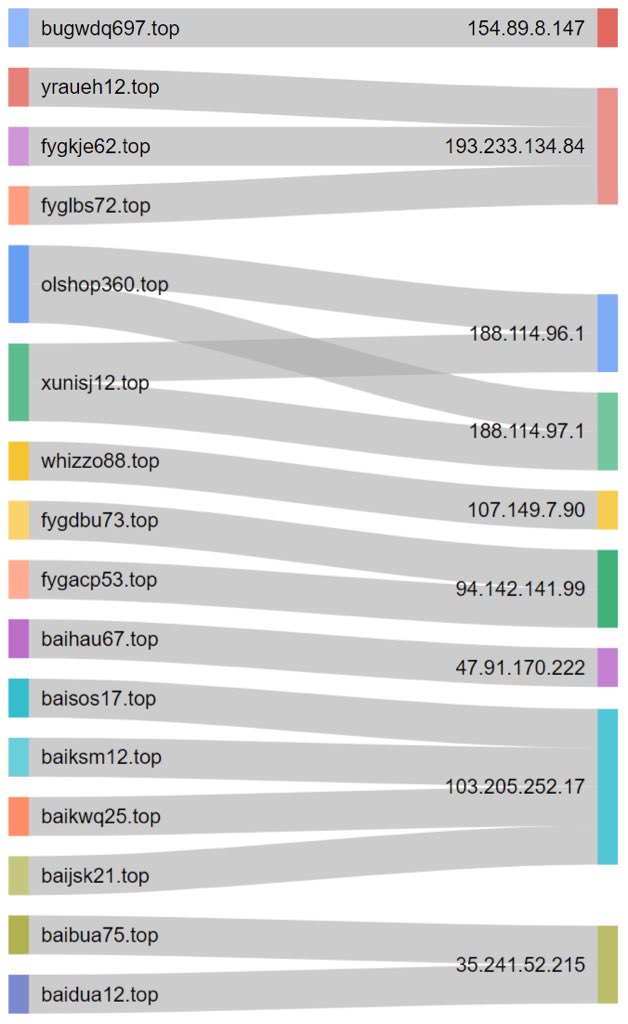
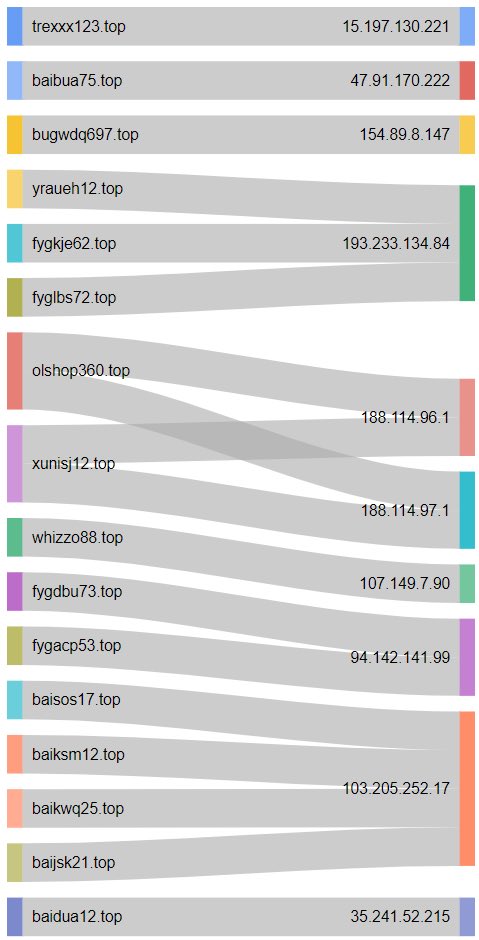
#cryptbot 搜尋結果
🤖New #Cryptbot activity detected. Of course, the campaign is delivered through pirate sites with "cracked" software. 🔍Investigated website: mycrackfree.]com (with cloudflare protection) ↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3iPcWIAA7ACN.png)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3whHXkAAHo3f.jpg)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3_tUWoAAa_ZV.jpg)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw6RPGXsAAC6YV.png)
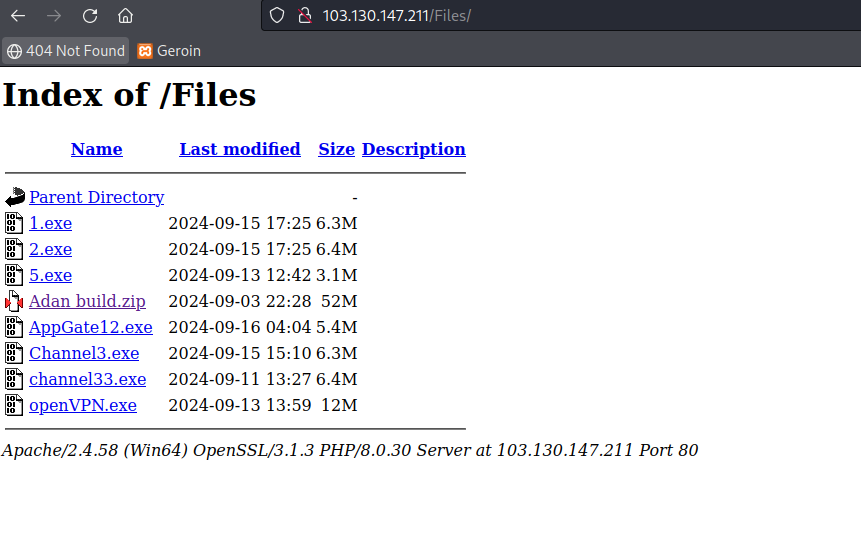
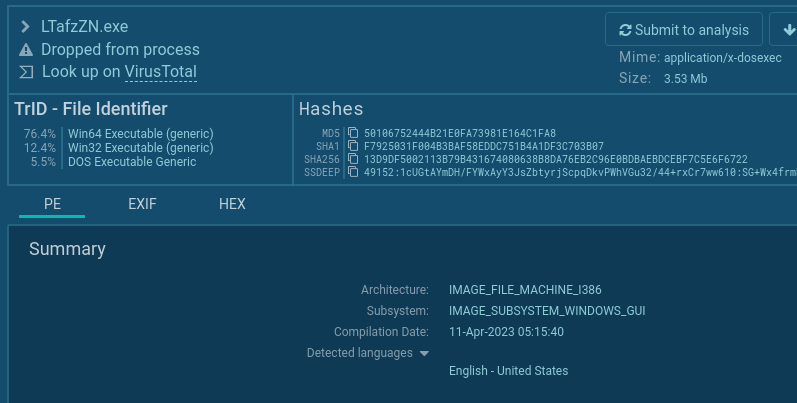
Found a #cryptbot sample. Bloated AutoKMS installer. Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe 🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt 🌐 whiueo14[.]top/gate.php 🌐uhfyl01[.]top/trombe.dat
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwYx2eXEAI_m2u.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwZxeWWYAE9aRp.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwbDo2WAAYYstW.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/Fnwb06HXoAAAUsy.png)
@LinkedIn accounts are compromised in a daily basis to join a big SEO poisoning campaign via LinkedIn Pulses. Users are then redirected to fake malicious sites where malware is being distributed, mainly #Lumma Stealer, #Cryptbot and #AMOS for Mac Users (finally found! 🍎) 👇👇
Cryptbot Download LINK (ALTERNATIVE).url 06996bb69b5978d822b228766c4b44c0 URL=http://gg[.]gg/1b9jyb password protected zip Sеtup.exe 4de2056db3a3b39bee9d833d403091d4 #Cryptbot C2 twex12ht[.]top #IOC
![suyog41's tweet image. Cryptbot
Download LINK (ALTERNATIVE).url
06996bb69b5978d822b228766c4b44c0
URL=http://gg[.]gg/1b9jyb
password protected zip
Sеtup.exe
4de2056db3a3b39bee9d833d403091d4 #Cryptbot
C2
twex12ht[.]top
#IOC](https://pbs.twimg.com/media/GT9MLfCXUAAfbSt.png)
![suyog41's tweet image. Cryptbot
Download LINK (ALTERNATIVE).url
06996bb69b5978d822b228766c4b44c0
URL=http://gg[.]gg/1b9jyb
password protected zip
Sеtup.exe
4de2056db3a3b39bee9d833d403091d4 #Cryptbot
C2
twex12ht[.]top
#IOC](https://pbs.twimg.com/media/GT9MLeKb0AUt6QY.png)
#CryptBot: Hunting for #initial #access vector intrinsec.com/cryptbot-hunti… Report: intrinsec.com/wp-content/upl…

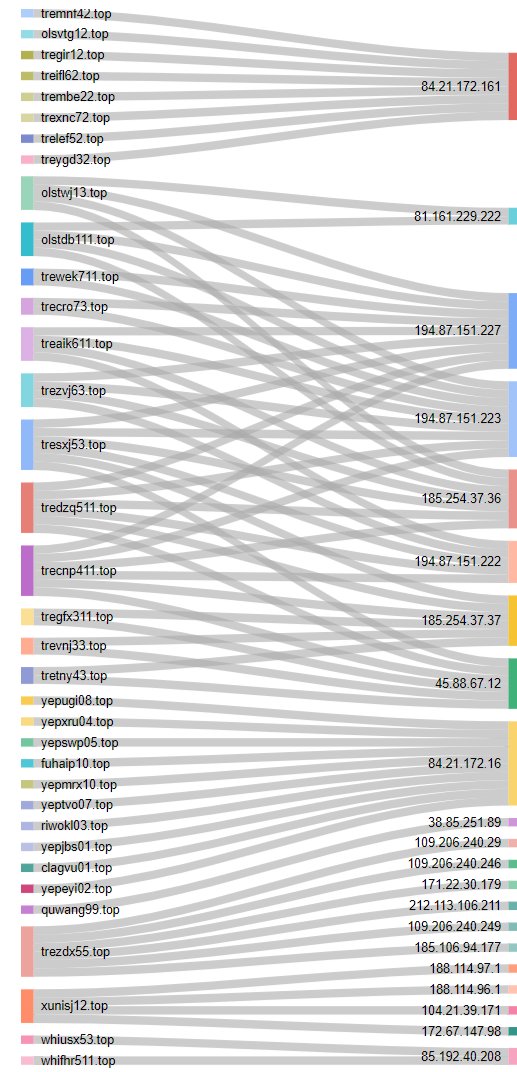
There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔 🛜 C2: vdeight8vt[.]top (81.94.159[.]120) 🔥 @unpacme did a great job with unpacking unpac.me/results/1a23fb… 📁 More related samples:…
![RussianPanda9xx's tweet image. There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔
🛜 C2: vdeight8vt[.]top (81.94.159[.]120)
🔥 @unpacme did a great job with unpacking
unpac.me/results/1a23fb…
📁 More related samples:…](https://pbs.twimg.com/media/GIKqqCHXUAAuK15.png)
![RussianPanda9xx's tweet image. There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔
🛜 C2: vdeight8vt[.]top (81.94.159[.]120)
🔥 @unpacme did a great job with unpacking
unpac.me/results/1a23fb…
📁 More related samples:…](https://pbs.twimg.com/media/GIKqsdBWwAAByTA.png)
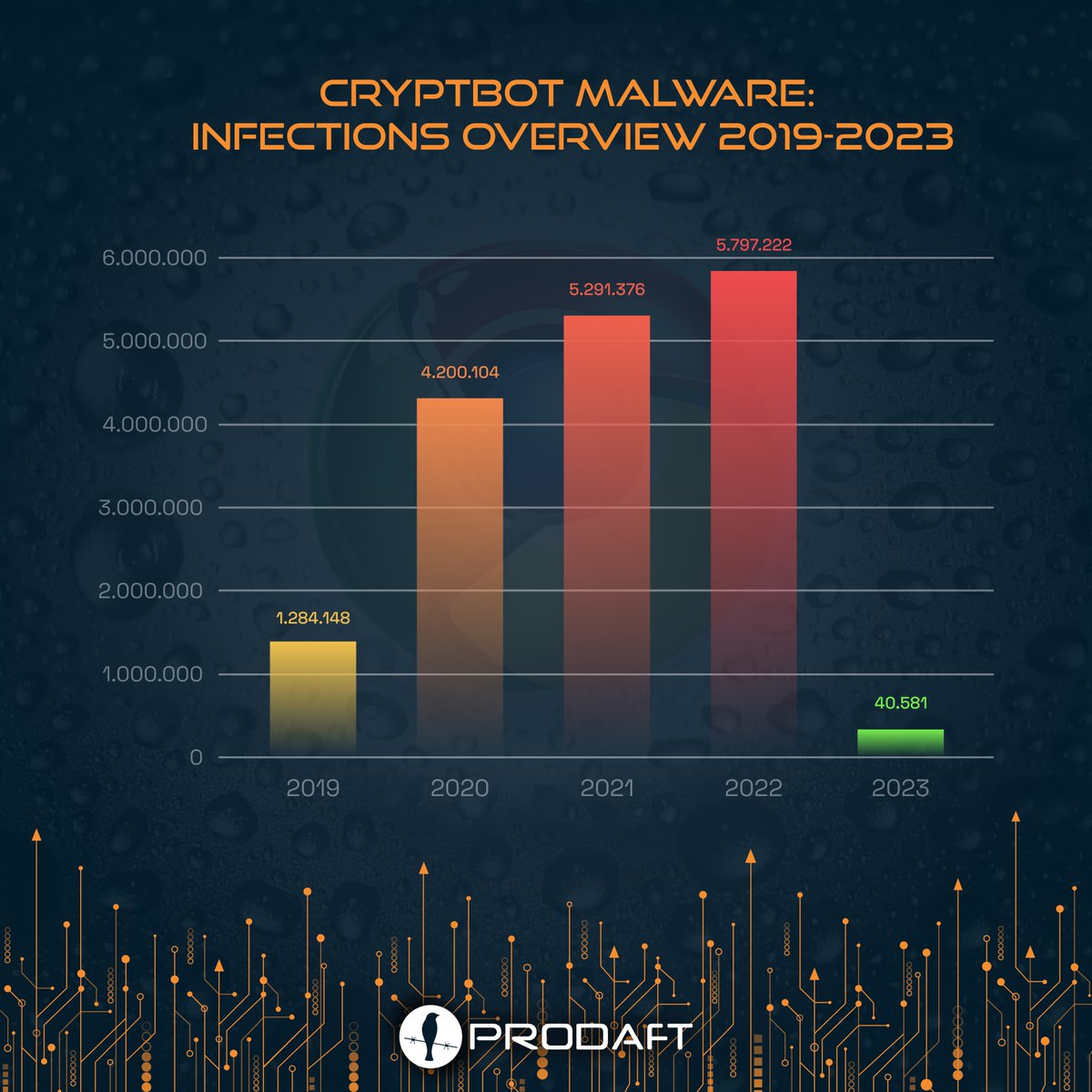
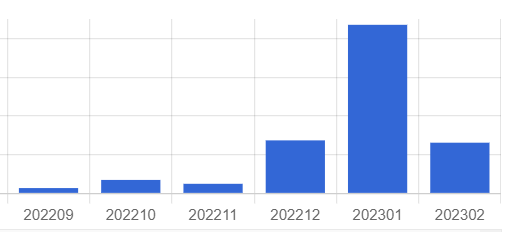
💣Until #Google's takedown of #CryptBot malware infrastructure, the responsible threat actors infected over 17 MILLION unique devices worldwide in the last 5️⃣ years - by tricking Google users into downloading fraudulent Google Chrome versions. As you can see in our graph below,…

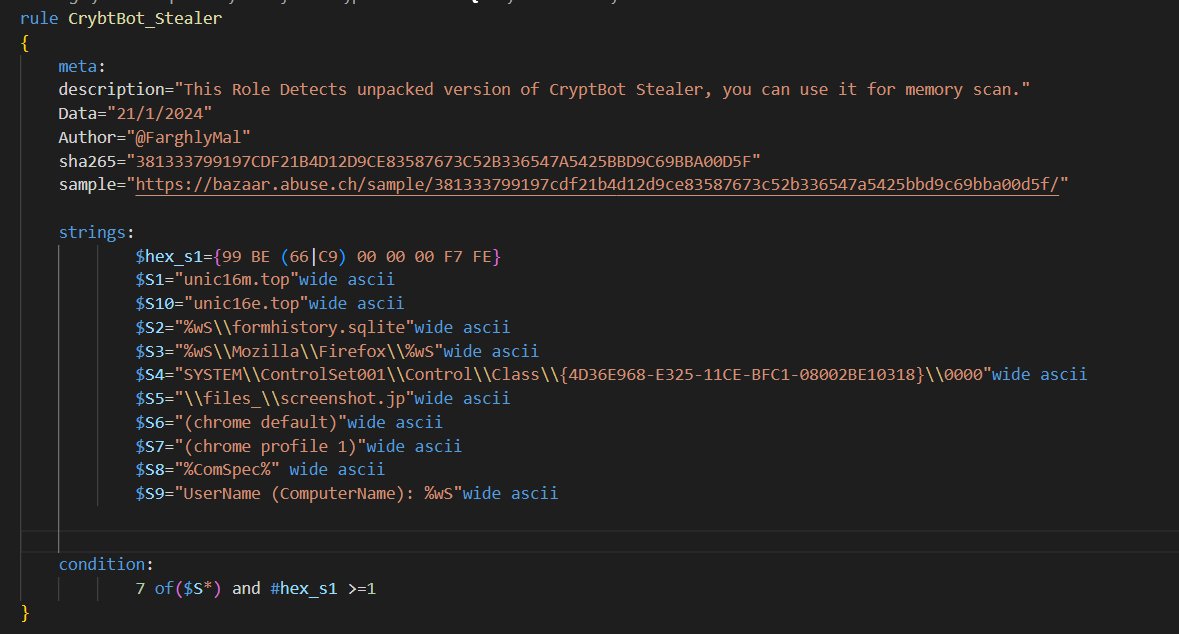
#100DaysofYARA Day21: this rule detects the unpacked version of #CryptBot Stealer rule -> github.com/FarghlyMal/Yar…
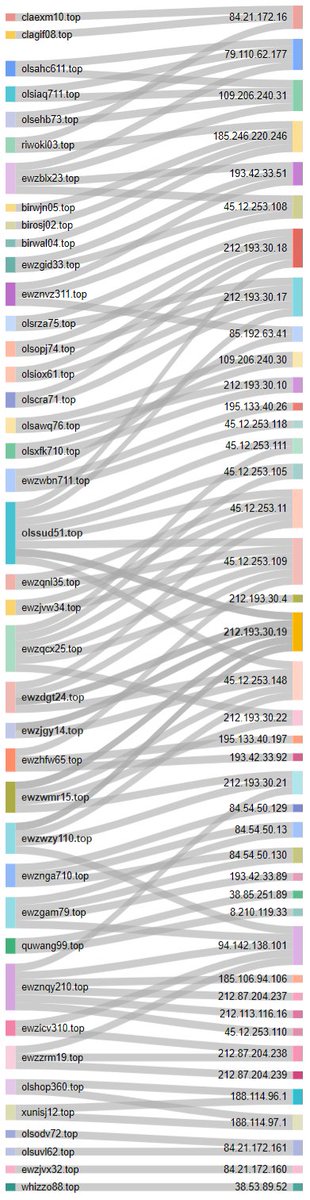
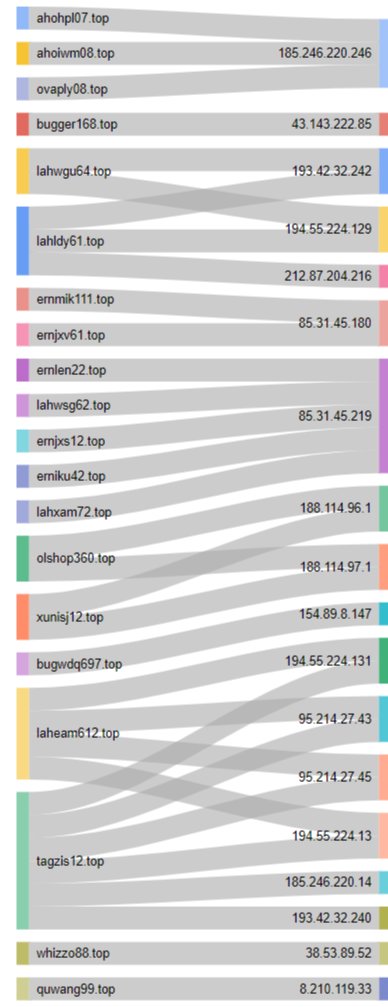
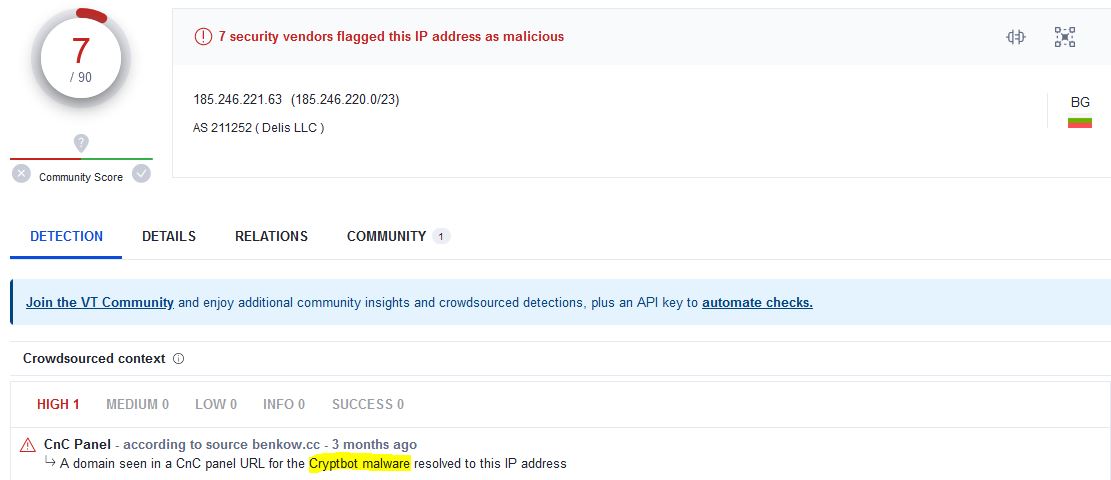
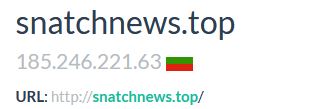
#Snatch #ransomware initially hosted in 🇧🇬 185.246.221.63, then transferred to 🇷🇺 Also found that same IP is C2 for #cryptbot #malware! snatchnews./top 176.124.222.177 80.66.64.67 #Infosec #Intel #infosecurity #security #hack #ransom #darkweb #OSINT #cybersecurity #cybersec
Igor is now helping you "activating" your unpaid Office products on hxxps://office-activator[.]com/. What a gentleman, but don't forget to disable your antivirus if you want to see your credentials stolen in your browser also... #cryptbot #infostealer
![H_Miser's tweet image. Igor is now helping you "activating" your unpaid Office products on hxxps://office-activator[.]com/.
What a gentleman, but don't forget to disable your antivirus if you want to see your credentials stolen in your browser also...
#cryptbot #infostealer](https://pbs.twimg.com/media/F9yBvtwWMAAInE3.png)
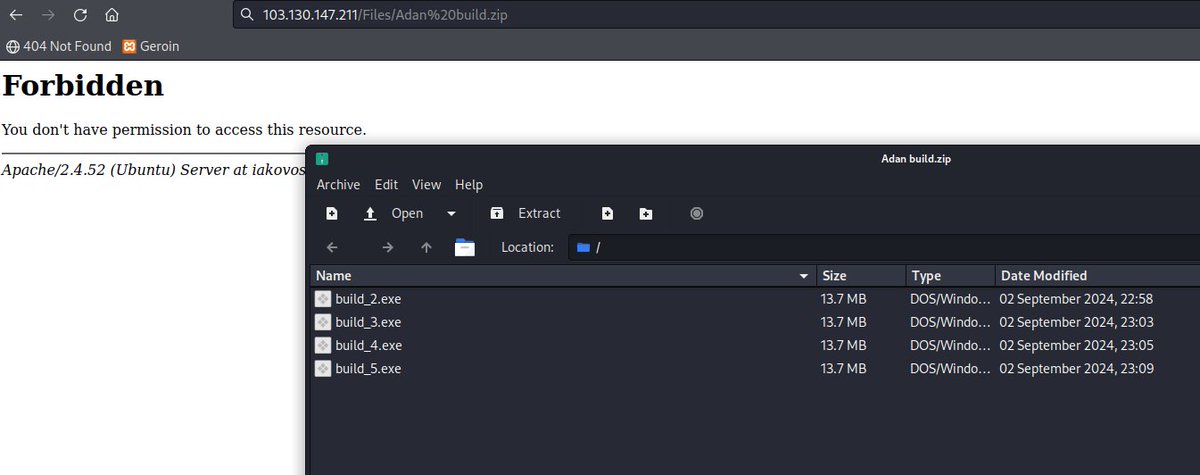
Importante lo que agrega @g0njxa, el malware podría ser realmente #CryptBot, más los dominios de distribución activos en este momento.

La pagina desde donde descargo: /oficial-kmspico.com/ aun activo sirviendo #Cryptbot /rars-uploaded.com/KMSpico/ Detonacion app.any.run/tasks/7d03c494… Esta campaña es conocida y antigua, el resto es historia
🔐Сrypt🤖Bot There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸 Search by #cryptbot tag 🔍-> any.run/malware-trends… file[] - is waiting for rule📯)) DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…
![Jane_0sint's tweet image. 🔐Сrypt🤖Bot
There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸
Search by #cryptbot tag 🔍-> any.run/malware-trends…
file[] - is waiting for rule📯))
DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…](https://pbs.twimg.com/media/Fut_z-xWAAAIJR7.png)
![Jane_0sint's tweet image. 🔐Сrypt🤖Bot
There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸
Search by #cryptbot tag 🔍-> any.run/malware-trends…
file[] - is waiting for rule📯))
DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…](https://pbs.twimg.com/media/Fut_z-wWwAE0QSe.png)


Found a #cryptbot sample. Bloated AutoKMS installer. Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe 🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt 🌐 whiueo14[.]top/gate.php 🌐uhfyl01[.]top/trombe.dat
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwYx2eXEAI_m2u.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwZxeWWYAE9aRp.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/FnwbDo2WAAYYstW.png)
![nosecurething's tweet image. Found a #cryptbot sample. Bloated AutoKMS installer.
Installed by bloated KMS_Pico_Full_Setup.exe > setup.exe > PS >aspnet_compiler.exe > trombe.exe, dpeditor.exe
🌐45.93.201[.]114/docs/ynupxDnDelE4X3wIwlgB92MU5VemJf.txt
🌐 whiueo14[.]top/gate.php
🌐uhfyl01[.]top/trombe.dat](https://pbs.twimg.com/media/Fnwb06HXoAAAUsy.png)
🤖New #Cryptbot activity detected. Of course, the campaign is delivered through pirate sites with "cracked" software. 🔍Investigated website: mycrackfree.]com (with cloudflare protection) ↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3iPcWIAA7ACN.png)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3whHXkAAHo3f.jpg)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw3_tUWoAAa_ZV.jpg)
![V3n0mStrike's tweet image. 🤖New #Cryptbot activity detected.
Of course, the campaign is delivered through pirate sites with "cracked" software.
🔍Investigated website: mycrackfree.]com (with cloudflare protection)
↩️Redirects: freeinstallcpc.]xyz @namecheap -> etradistribuciones.]com -> href.]li ->…](https://pbs.twimg.com/media/GBw6RPGXsAAC6YV.png)
💣Until #Google's takedown of #CryptBot malware infrastructure, the responsible threat actors infected over 17 MILLION unique devices worldwide in the last 5️⃣ years - by tricking Google users into downloading fraudulent Google Chrome versions. As you can see in our graph below,…


There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔 🛜 C2: vdeight8vt[.]top (81.94.159[.]120) 🔥 @unpacme did a great job with unpacking unpac.me/results/1a23fb… 📁 More related samples:…
![RussianPanda9xx's tweet image. There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔
🛜 C2: vdeight8vt[.]top (81.94.159[.]120)
🔥 @unpacme did a great job with unpacking
unpac.me/results/1a23fb…
📁 More related samples:…](https://pbs.twimg.com/media/GIKqqCHXUAAuK15.png)
![RussianPanda9xx's tweet image. There is a new version of #CryptBot spreading around with VMProtect? The infrastructure belongs to CryptBot 🤔
🛜 C2: vdeight8vt[.]top (81.94.159[.]120)
🔥 @unpacme did a great job with unpacking
unpac.me/results/1a23fb…
📁 More related samples:…](https://pbs.twimg.com/media/GIKqsdBWwAAByTA.png)
#CryptBot: Hunting for #initial #access vector intrinsec.com/cryptbot-hunti… Report: intrinsec.com/wp-content/upl…

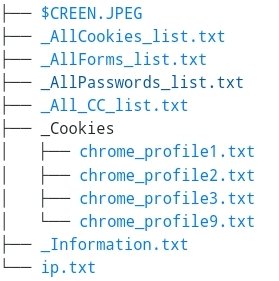
Estoy de acuerdo. Esta imagen revela el árbol de archivos de logs generados por #Cryptbot durante la infección del operador de Orange. Los nombres de estos archivos coinciden con investigaciones anteriores sobre esta amenaza, como se muestra en este interesante artículo de…
#Snatch #ransomware initially hosted in 🇧🇬 185.246.221.63, then transferred to 🇷🇺 Also found that same IP is C2 for #cryptbot #malware! snatchnews./top 176.124.222.177 80.66.64.67 #Infosec #Intel #infosecurity #security #hack #ransom #darkweb #OSINT #cybersecurity #cybersec


2ca85769db7d1e6ded7bde9f84bad2e0 taslogin[.]s3[.]ap-southeast-1[.]amazonaws[.]com u[.]arpuu[.]com 13[.]208[.]251[.]115:3158 AS16509 AMAZON-02 🇯🇵 #CryptBot @malwrhunterteam @500mk500 @abuse_ch
![skocherhan's tweet image. 2ca85769db7d1e6ded7bde9f84bad2e0
taslogin[.]s3[.]ap-southeast-1[.]amazonaws[.]com
u[.]arpuu[.]com
13[.]208[.]251[.]115:3158
AS16509 AMAZON-02 🇯🇵
#CryptBot @malwrhunterteam @500mk500 @abuse_ch](https://pbs.twimg.com/media/Gr5_Wi6XUAEtQJ1.jpg)
Cryptbot Download LINK (ALTERNATIVE).url 06996bb69b5978d822b228766c4b44c0 URL=http://gg[.]gg/1b9jyb password protected zip Sеtup.exe 4de2056db3a3b39bee9d833d403091d4 #Cryptbot C2 twex12ht[.]top #IOC
![suyog41's tweet image. Cryptbot
Download LINK (ALTERNATIVE).url
06996bb69b5978d822b228766c4b44c0
URL=http://gg[.]gg/1b9jyb
password protected zip
Sеtup.exe
4de2056db3a3b39bee9d833d403091d4 #Cryptbot
C2
twex12ht[.]top
#IOC](https://pbs.twimg.com/media/GT9MLfCXUAAfbSt.png)
![suyog41's tweet image. Cryptbot
Download LINK (ALTERNATIVE).url
06996bb69b5978d822b228766c4b44c0
URL=http://gg[.]gg/1b9jyb
password protected zip
Sеtup.exe
4de2056db3a3b39bee9d833d403091d4 #Cryptbot
C2
twex12ht[.]top
#IOC](https://pbs.twimg.com/media/GT9MLeKb0AUt6QY.png)
Importante lo que agrega @g0njxa, el malware podría ser realmente #CryptBot, más los dominios de distribución activos en este momento.

La pagina desde donde descargo: /oficial-kmspico.com/ aun activo sirviendo #Cryptbot /rars-uploaded.com/KMSpico/ Detonacion app.any.run/tasks/7d03c494… Esta campaña es conocida y antigua, el resto es historia
🔐Сrypt🤖Bot There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸 Search by #cryptbot tag 🔍-> any.run/malware-trends… file[] - is waiting for rule📯)) DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…
![Jane_0sint's tweet image. 🔐Сrypt🤖Bot
There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸
Search by #cryptbot tag 🔍-> any.run/malware-trends…
file[] - is waiting for rule📯))
DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…](https://pbs.twimg.com/media/Fut_z-xWAAAIJR7.png)
![Jane_0sint's tweet image. 🔐Сrypt🤖Bot
There could be quite a lot of text here, but the most paradoxical evidence is noted in the photo 📸
Search by #cryptbot tag 🔍-> any.run/malware-trends…
file[] - is waiting for rule📯))
DGA reminded me of one sample that I called \$CREEN -> app.any.run/tasks/581c8f3c…](https://pbs.twimg.com/media/Fut_z-wWwAE0QSe.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Black Friday 333K posts
- 2. #FanCashDropPromotion N/A
- 3. #SkylineSweeps N/A
- 4. Good Friday 55.8K posts
- 5. #releafcannabis N/A
- 6. Mainz Biomed N.V. N/A
- 7. CONGRATULATIONS JIN 48.8K posts
- 8. #AVenezuelaNoLaTocaNadie 1,763 posts
- 9. Clark Lea N/A
- 10. WHO DEY 12.8K posts
- 11. #FridayVibes 3,729 posts
- 12. CONGRATULATIONS J-HOPE 39.8K posts
- 13. Mr. President 21.3K posts
- 14. GreetEat Corp. N/A
- 15. Third World Countries 50K posts
- 16. TODAY ONLY 64K posts
- 17. Happy Friyay N/A
- 18. Victory Friday N/A
- 19. Cyber Monday 5,652 posts
- 20. RED Friday 8,787 posts