#debugsecurity search results
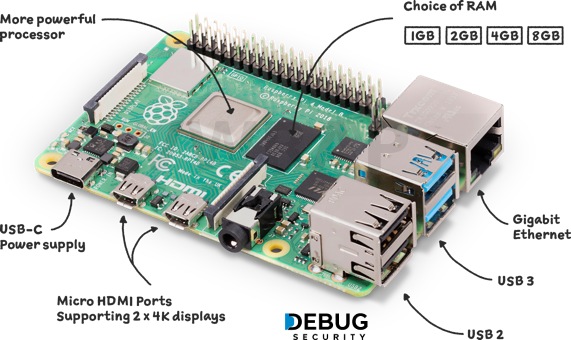
💻 Raspberry Pi – A Hacker’s Pocket-Sized Computer🔐 📌 Key Features: 🔹Quad-core ARM processor 🔹Up to 8GB RAM 🔹Dual 4K display support 🔹USB 3.0 + Gigabit Ethernet 🔹Built-in Wi-Fi & Bluetooth 🔹GPIO pins #RaspberryPi #DebugSecurity #CyberSecurity #HackingTools #VWrap
🎫Proxmark3 — The Ultimate RFID/NFC Hacking Toolkit 🔍 A professional-grade device for analyzing, reading, emulating, and cloning RFID and NFC systems. It’s widely used in cybersecurity, red teaming, and physical security assessments. #Proxmark3 #DebugSecurity #RFID #NFC #Vwrap

Red Team Assessments debugsec.com/service/red-te… #debugsecurity #debug #security #cybersecurity #company #pentent #Vulnerability

Penetration Testing vs Vulnerability Assessments debugsec.com/blog/penetrati… #debugsecurity #debug #security #cybersecurity #company #pentent #vulnerability
USB Rubber Ducky– The Hacker’s Flash Drive in Disguise In Cybersecurity, it’s used for: ✔️ Launching reverse shells. ✔️ Stealing credentials. ✔️ Installing backdoors. ✔️ Downloading and executing malicious files. #USBRubberDucky #DebugSecurity #CyberSecurity #HackingTools #VWrap

Why are Penetration Tests Important for Business debugsec.com/blog/why-are-p… #debugsecurity #debug #security #cybersecurity #company #pentent #Vulnerability
Red Team Assessments debugsec.com/service/red-te… #debugsecurity #debug #security #cybersecurity #company #pentent #Vulnerability

Why are Penetration Tests Important for Business debugsec.com/blog/why-are-p… #debugsecurity #debug #security #cybersecurity #company #pentent #Vulnerability
Penetration Testing vs Vulnerability Assessments debugsec.com/blog/penetrati… #debugsecurity #debug #security #cybersecurity #company #pentent #vulnerability
🎫Proxmark3 — The Ultimate RFID/NFC Hacking Toolkit 🔍 A professional-grade device for analyzing, reading, emulating, and cloning RFID and NFC systems. It’s widely used in cybersecurity, red teaming, and physical security assessments. #Proxmark3 #DebugSecurity #RFID #NFC #Vwrap

USB Rubber Ducky– The Hacker’s Flash Drive in Disguise In Cybersecurity, it’s used for: ✔️ Launching reverse shells. ✔️ Stealing credentials. ✔️ Installing backdoors. ✔️ Downloading and executing malicious files. #USBRubberDucky #DebugSecurity #CyberSecurity #HackingTools #VWrap

💻 Raspberry Pi – A Hacker’s Pocket-Sized Computer🔐 📌 Key Features: 🔹Quad-core ARM processor 🔹Up to 8GB RAM 🔹Dual 4K display support 🔹USB 3.0 + Gigabit Ethernet 🔹Built-in Wi-Fi & Bluetooth 🔹GPIO pins #RaspberryPi #DebugSecurity #CyberSecurity #HackingTools #VWrap

Red Team Assessments debugsec.com/service/red-te… #debugsecurity #debug #security #cybersecurity #company #pentent #Vulnerability

💻 Raspberry Pi – A Hacker’s Pocket-Sized Computer🔐 📌 Key Features: 🔹Quad-core ARM processor 🔹Up to 8GB RAM 🔹Dual 4K display support 🔹USB 3.0 + Gigabit Ethernet 🔹Built-in Wi-Fi & Bluetooth 🔹GPIO pins #RaspberryPi #DebugSecurity #CyberSecurity #HackingTools #VWrap

🎫Proxmark3 — The Ultimate RFID/NFC Hacking Toolkit 🔍 A professional-grade device for analyzing, reading, emulating, and cloning RFID and NFC systems. It’s widely used in cybersecurity, red teaming, and physical security assessments. #Proxmark3 #DebugSecurity #RFID #NFC #Vwrap

USB Rubber Ducky– The Hacker’s Flash Drive in Disguise In Cybersecurity, it’s used for: ✔️ Launching reverse shells. ✔️ Stealing credentials. ✔️ Installing backdoors. ✔️ Downloading and executing malicious files. #USBRubberDucky #DebugSecurity #CyberSecurity #HackingTools #VWrap

Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 105K posts
- 2. Branch 31.5K posts
- 3. Mahomes 32K posts
- 4. #TNABoundForGlory 52.7K posts
- 5. #LoveCabin 1,035 posts
- 6. LaPorta 10.3K posts
- 7. Goff 13.5K posts
- 8. Bryce Miller 4,349 posts
- 9. #LaGranjaVIP 58K posts
- 10. Kelce 16.1K posts
- 11. Dan Campbell 3,671 posts
- 12. #OnePride 6,337 posts
- 13. Rod Wave 1,028 posts
- 14. #DETvsKC 4,900 posts
- 15. Butker 8,415 posts
- 16. Mariners 48.6K posts
- 17. Pacheco 4,907 posts
- 18. JuJu Smith 3,964 posts
- 19. Red Cross 28.2K posts
- 20. Baker 54.1K posts



