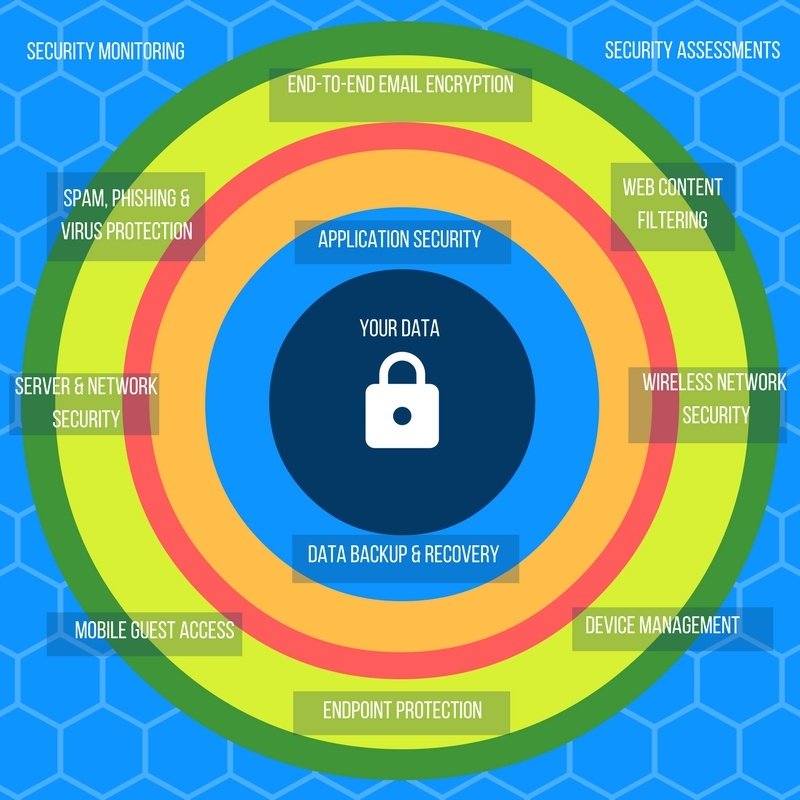
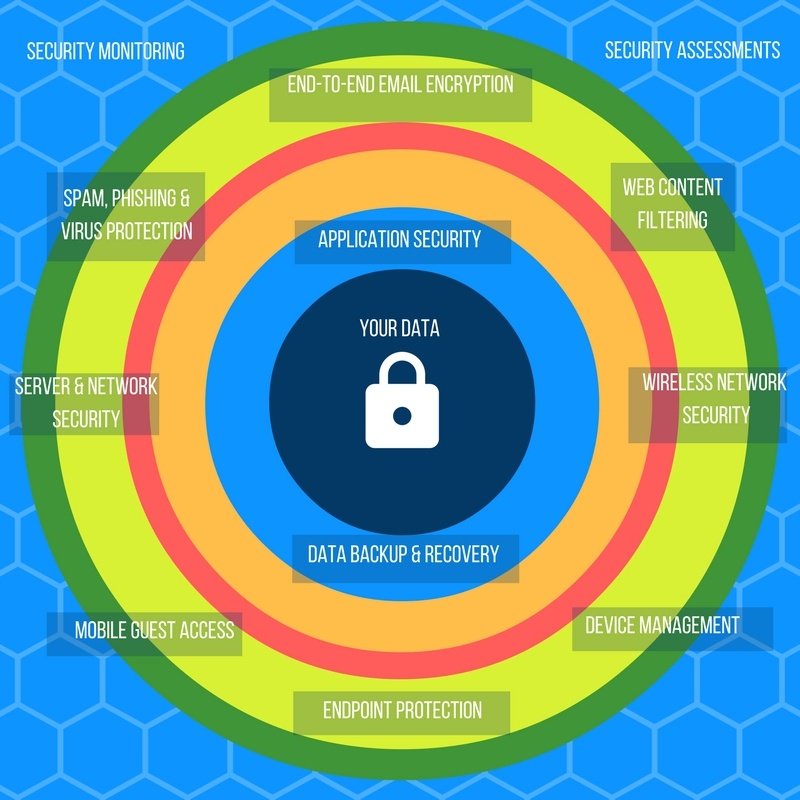
#multilayersecurity 검색 결과
The new normal #Cloud + #ZeroTrustSecurity + #MultiLayerSecurity + #ProActiveMonitoring Post #Covid19 #WorkFromHome will be the new industry norm. Less Crowded cities + less traffic on road + less pollution What else can be better than this. #CyberSecurity #Aristi
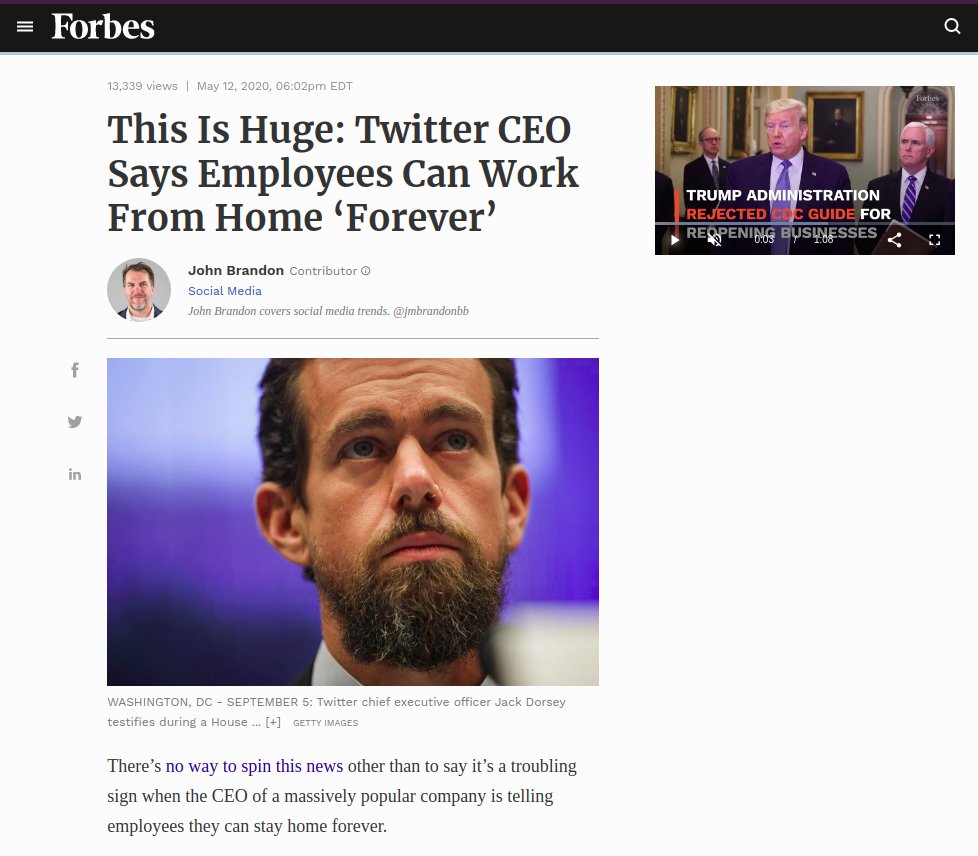
To effectively combat cyber threats, organizations must prioritize cybersecurity awareness training. This essential strategy not only complies with legal requirements but also addresses human vulnerabilities #multilayersecurity #securitynews

Bank Level Security For Your Patient Data by @DocEngage #DataSecurity #MultiLayerSecurity: pos.li/9GzA

We understand you have a lot of data to protect. That's why we offer fully integrated services and solutions to ensure your sensitive information is always safe. #hybridnetwork #business #multilayersecurity #cybersecurity


Our IT security solutions are built to ensure your IT at the core of your business is protected. #multilayersecurity
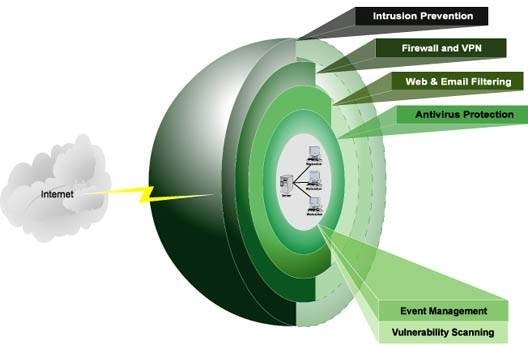
#ADMS supports integration with your existing #ERP system. It enables multiple layered security features including role-based security, a configurable manager approval process and user verification system. #multilayersecurity #securityroles #DMS #cloudsoftware @BaffleSol

Discover the Key Deliverables of our Premium Colocation Services! Seamlessly store and manage your critical data with Go4Hosting's state-of-the-art Colocation Rack Space Service. #multilayersecurity #climatecontrol #carrierneutrality #colocation

If crypto-malware gets through your network defenses, recover fast w/@Datto's BDR Solution. #MultiLayerSecurity hubs.ly/H06G0hB0
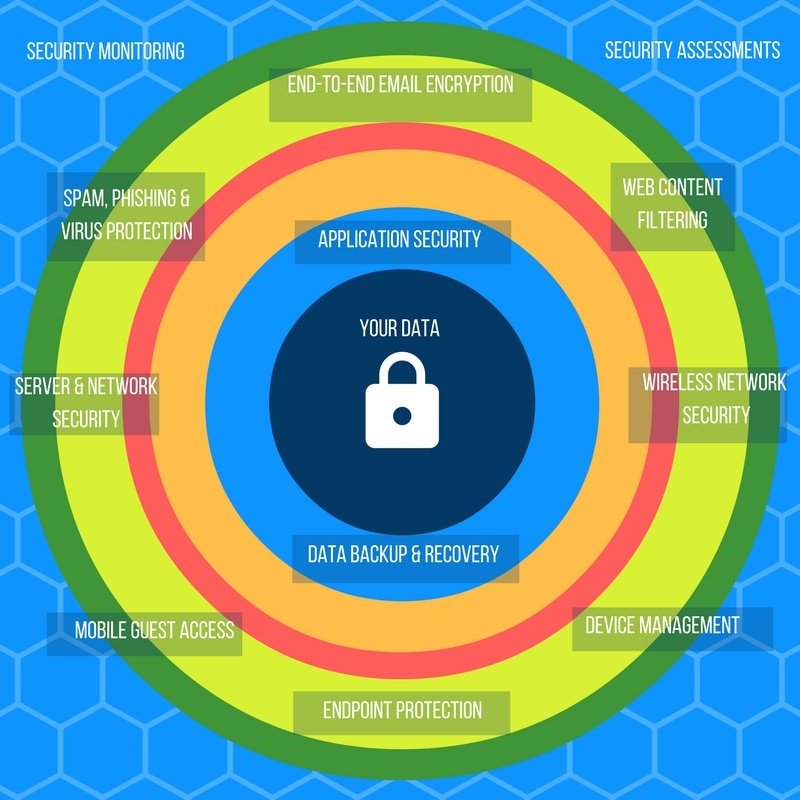
Phishing, Ransomware & Beyond: Seven types of Cyberattacks you should know #MultiLayerSecurity zurl.co/G6C1

10 Email Security Best Practices in 2023 In the age of total interconnectedness, digital dangers are all around Want a chat about how we can help? Call us on 0203 931 0199 to talk security #MultiLayerSecurity #EssentialsPLUS zurl.co/NvJ9

9 in 10 Organisations Paid At least One Ransom Last Year New analysis of cyber attacks shows ransomware attacks are running far more rampant than previously thought #SecurityAwareness #MultiLayerSecurity zurl.co/wnWl

Washington DC Police fall victim to Ransomware 2.0 -a new approach of #ransomware. Babuk hacking group have decided the DC Police incident will be their last dedicated #ransomware attack. titanhq.com/blog/even-the-… #multilayersecurity #webtitan #spamtitan

New Phishing Attack Spoofs Microsoft 365 Authentication System Phishing attack that involves the spoofing of the Microsoft 365 authentication system Prevention is always better than cure #MultiLayerSecurity zurl.co/zlwj

Babuk #ransomware 2.0 stole data from Washington DC Police, which included personnel files of police officers & informants - find out why the DC incident will be their last dedicated ransomware attack ow.ly/whCw50EPh3q #multilayersecurity #webtitan #spamtitan

The evolving nature of ransomware strains means that you cannot rely on just end-point security solutions. Some #ransomware strains detected lately show why you need a #multilayersecurity strategy that includes #emailfiltering and #web filtering. bit.ly/3EyuHo8

We ensure top notch security with extensive security assessment and solutions like multi-signature, SSL implementation and encrypted user access. Visit: primafelicitas.com/cryptocurrency… #Primafelicitas #MultilayerSecurity #CyberThreats #CyberSecurity

Phishing Emails Use SVG Files to Avoid Detection Phishing emails are increasingly using Scalable Vector Graphics (SVG) attachments to display malicious forms or deliver malware #MultiLayerSecurity zurl.co/LECm

Cybercriminals use SEO tricks to push phishing pages Search engine optimisation (SEO) has become the latest tool for attackers looking to lure in targets for phishing attacks #MultiLayerSecurity zurl.co/irVJx

@Giverep’s security: Multi-layer encryption, on-chain verification. Your rewards are protected. #MultiLayerSecurity #Encrypted
@Giverep’s blockchain is secure with multi-layer protection! Safe, reliable. #MultiLayerSecurity
4/7 🧱 Multiple Layers of Protection A password alone is not protection. BiyaPay adds: ✅ 2FA ✅ Biometric login ✅ Device verification No one’s touching your funds without you. 👁️🗨️ #MultiLayerSecurity #CryptoSafety #BiyaPay
4/7 🧱 Multiple Layers of Protection A password alone is not protection. BiyaPay adds: ✅ 2FA ✅ Biometric login ✅ Device verification No one’s touching your funds without you. 👁️🗨️ #MultiLayerSecurity #CryptoSafety
Multi-layer Security Market marketresearchfuture.com/reports/us-mul… #MultilayerSecurity
marketresearchfuture.com
US Multi-layer Security Market Size, Share and Forecast 2035
US Multi-layer Security Market to Grow at a CAGR of 8.026% by 2035, US Multi-layer Security Market Analysis by Application, Deployment Type, Solution, End Use Sector
Cybercriminals use SEO tricks to push phishing pages Search engine optimisation (SEO) has become the latest tool for attackers looking to lure in targets for phishing attacks #MultiLayerSecurity zurl.co/irVJx

SUI??s multi - layer security model is an innovative defense strategy, protecting digital assets comprehensively. #MultiLayerSecurity #SUIProtect @GiveRep
SUI??s multi - layer security model combines encryption, authentication, and more. Protect your digital assets from every angle. #MultiLayerSecurity #SUIAdvantage @GiveRep
SUI??s multi - layer security model protects your assets from all threats. Sleep soundly. #MultiLayerSecurity #SUIAdvantage @GiveRep
US Multi-layer Security Market marketresearchfuture.com/reports/us-mul… #MultilayerSecurity
marketresearchfuture.com
US Multi-layer Security Market Size, Share and Forecast 2035
US Multi-layer Security Market to Grow at a CAGR of 8.026% by 2035, US Multi-layer Security Market Analysis by Application, Deployment Type, Solution, End Use Sector
FOGO's security measures are multi - layered. Protect your investments! #FOGO #MultiLayerSecurity?
@Fogochain’s multi - layer security architecture is a fortress for your digital assets. 🏰 #FogoChain #MultiLayerSecurity
@Fogochain’s multi - layer security architecture is a fortress for your digital assets. 🏰 #FogoChain #MultiLayerSecurity
Onchain, on point. Fogees are working hard on their art! Shoutout to @noonne_art cooking it up in the kitchen 🔥

CISOs prioritize multilayered security but struggle with deployment due to excessive tools, vDefend and Avi aim to simplify this. #CISO #defenseindepth #multilayersecurity #cybersecurity #riskmanagement #vDefend #Avi #integration #simplicity #plugandplay video.cube365.net/c/969941
@FogoChain 🛡️ FogoChain’s multi - layer security system keeps your data safe from threats. #FogoChain #MultiLayerSecurity
. @soon_svm #SOONISTHEREDPILL soon_svm's multi - layer security features protect against various cyber threats. #MultiLayerSecurity #soon_svm
Businesses must plan, prepare and defend against every threat, cybercriminals only need to find a single weakness or hole in your defenses.. To learn more, click here ow.ly/5LxG50Vlp6F #multilayersecurity #MLS #cyberreadinessplan #cyberreadiness #security

Something went wrong.
Something went wrong.
United States Trends
- 1. Lamar 24.1K posts
- 2. Thanksgiving 1.74M posts
- 3. Chiefs 93K posts
- 4. Ravens 29.9K posts
- 5. Mahomes 29.4K posts
- 6. Zac Taylor 1,851 posts
- 7. Pickens 29.5K posts
- 8. Sarah Beckstrom 148K posts
- 9. Tinsley 1,103 posts
- 10. Joe Burrow 9,324 posts
- 11. Derrick Henry 2,768 posts
- 12. #AEWCollision 7,745 posts
- 13. Jason Garrett N/A
- 14. McDuffie 7,033 posts
- 15. Chase Brown 1,970 posts
- 16. Isaiah Likely N/A
- 17. Cam Boozer N/A
- 18. #CINvsBAL 1,084 posts
- 19. Zay Flowers N/A
- 20. Post Malone 5,133 posts