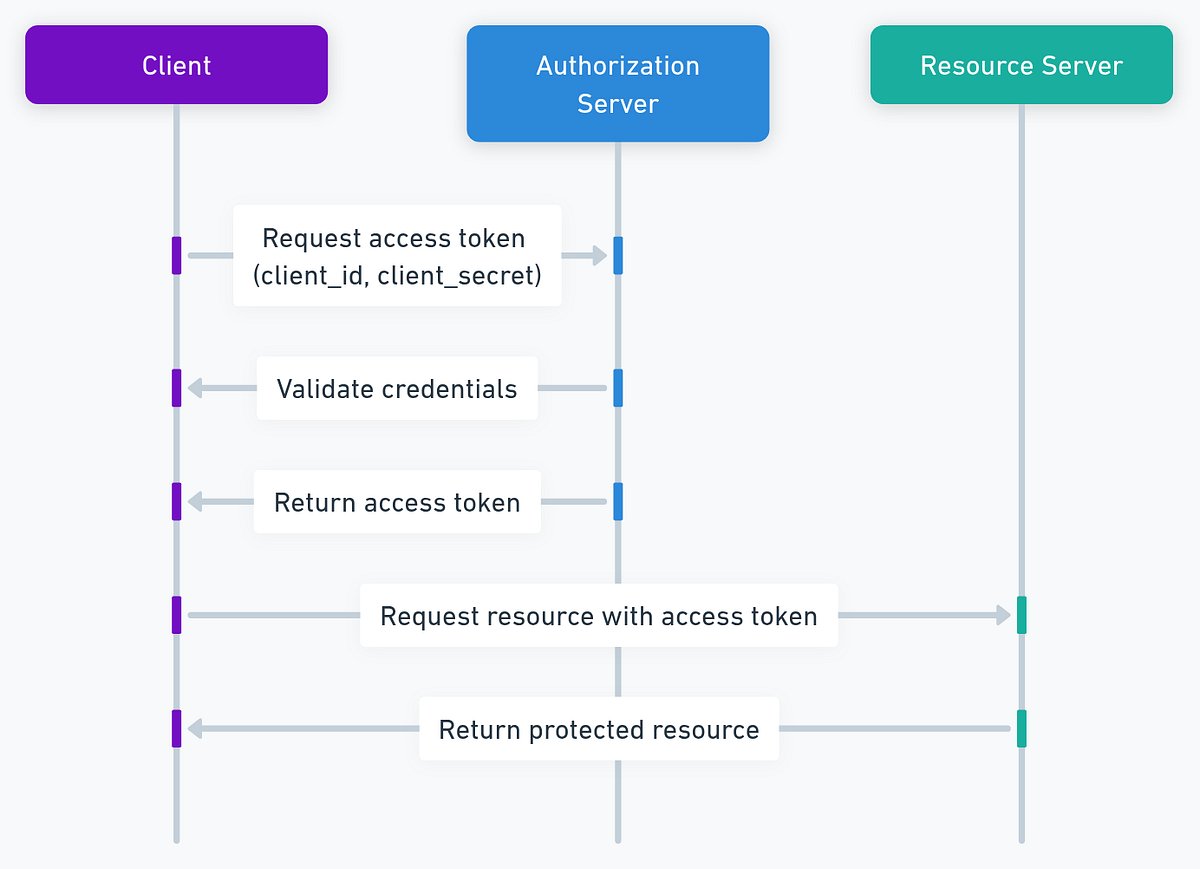
#oauth2 risultati di ricerca
Just published the very first writeup on my biggest P1 bounty 1️⃣ Check it out: medium.com/@bugbounty0901… #bugbounty #oauth2
With Pomerium, OAuth2 configuration becomes a breeze. Simply configure your routes, and Pomerium handles the upstream OAuth flow, ensuring tokens never leave the gateway for enhanced security. A definite win for developer experience! #OAuth2 #security
Congratulations to Sh Jaimandeep Singh for successfully defending his PhD thesis during the viva voce on 21.08.2024. He carried out his research on Secure Design, Architecture and Configuration of authorisation protocols with emphasis on OAuth 2.0. @NFSU_Official #OAuth2.0


Day 2 - REST APIs & OAuth2.0 with FastAPI 🚀 Built a REST API & learned proper naming conventions FastAPI auto-validates requests with Pydantic Used @field_validator for custom error messages 📌 Explored OAuth2.0 with OpenID Connect for authentication 🔐 #FastAPI #OAuth2 #OpenID



Starting Jan 2025, Gmail enforces OAuth 2.0 for SMTP. Stay compliant and secure with Gmail SMTP Connect for Joomla! No passwords. No downtime. Just reliable, Google-approved email delivery. 👉 web357.com/gmail-smtp-con… #Web357 #OAuth2 #GmailSMTP #Security #JoomlaExtensions

Kinde gives you a whole lot of ways to authenticate users via social and enterprise connections. Now you can bring your own custom OAuth 2.0 or Open ID connection. 🎉 Ta da! Authentication your way with Kinde. Get started —> docs.kinde.com/authenticate/c… #OIDC #Oauth2 #Auth

OAuth 2.0 is the backbone of secure API access Here's the breakdown: - Grant types: Auth Code, Implicit, Client Credentials... - Core concepts: Tokens, Resource Owner, Auth Server - Security tips - OpenID Connect: for user identity A great visual by MasteringBackend. #OAuth2

To enhance security, Microsoft will end support for Basic Authentication on Sep 16, 2024. Outlook, Hotmail, and Live users must switch to Modern Authentication (OAuth 2.0) to keep inbox access. Use apps like Mailbird to stay connected. #Microsoft #ModernAuthentication #OAuth2

🚀 Just implemented Google OAuth2 in Django! 🔐 Seamlessly fetching user data and handling tokens like a pro. 🛡️ Here's a sneak peek into the code that makes it all happen! 💻 #Django #OAuth2 #GoogleAuth #BackendDeveloper #Python #DevLife #Coding #Connect #Programming

OAuth2 with Node.js — a visual guide OAuth2 lets apps access user data securely without credentials. This image walks you through: - Picking libraries like passport - Implementing token exchange - Validating tokens & handling refresh - Build secure apps with Node.js #OAuth2

🔊 The password flow has been retired. Migrate your apps now to OAuth 2.0 to stay secure and supported. Here's how: zurl.co/XSV9n #OAuth2 #RingCentralDevs #Developers
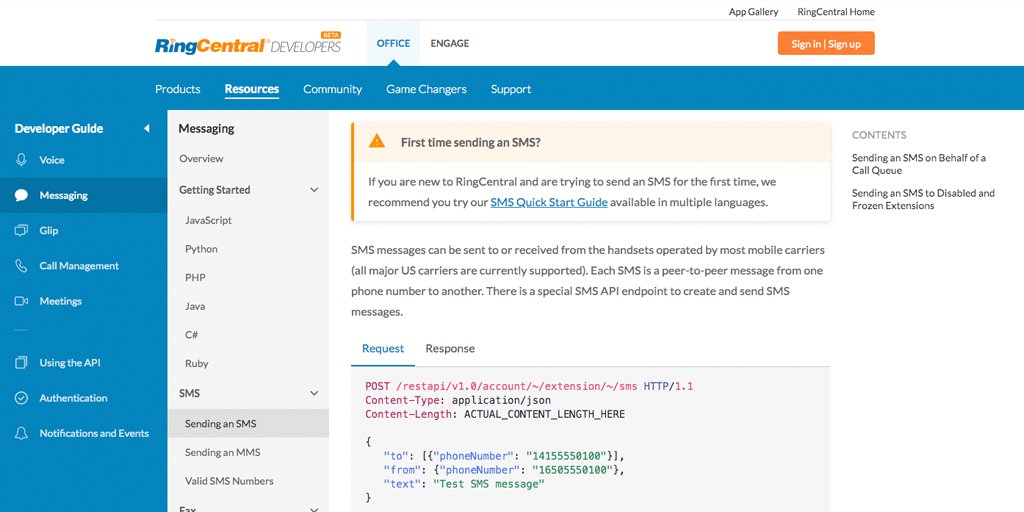
OAuth 2.0 Authorization Flow with Dropbox API and Postman #oauth2 #postman morioh.com/p/208d2916ede6…
🛡️ Use OAuth 2.0 for secure authentication. How-To: Implement OAuth 2.0 to provide secure and scalable user authentication for your web and mobile applications. #OAuth2 #SecureAuthentication #SmartSnippet #AllDayDSK
Security and usability rarely meet... but they do here. 🔐 This new guide breaks down how to integrate MCP tools in Copilot Studio using OAuth 2.0 Authorization Code Flow Read it here 👉 techcommunity.microsoft.com/blog/azure-ai-… #Azure #CopilotStudio #OAuth2 #Microsoft

oauth2-proxy Protect your web apps with OAuth2 / OIDC auth using OAuth2-Proxy, a flexible & open-source reverse proxy/middleware. Supports multiple providers & extracts user details #oauth2proxy #oauth2 #security

I've published a new article on implementing PKCE with Keycloak using the passport-keycloak-oauth2-oidc-portable library. blog.brakmic.com/pkce-with-keyc… #OAuth2 #Keycloak #PKCE



🛡️ Secure API with OAuth2: Implement OAuth2 for secure API authentication. How-To: Use Passport.js for OAuth2 in Node.js to handle user authentication and authorization. #OAuth2 #APISecurity #SmartSnippet
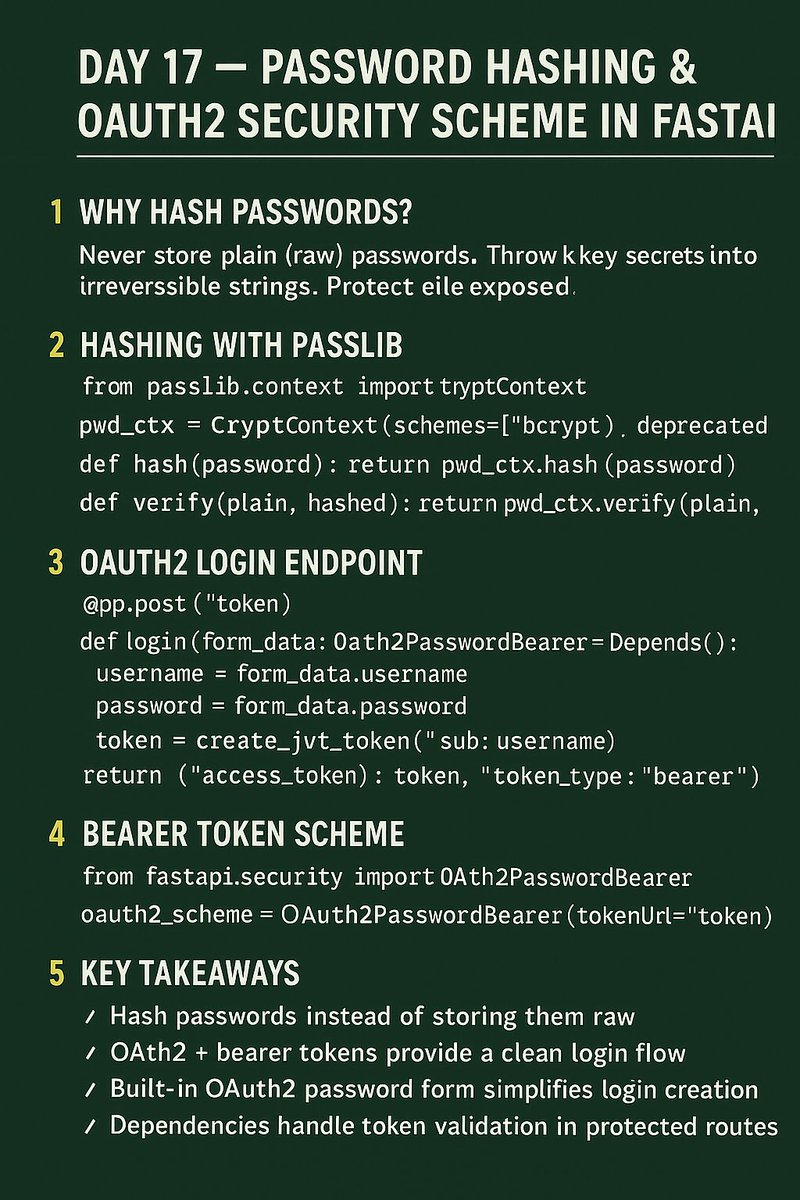
Day 17 — Password Hashing & OAuth2 Security Scheme in FastAPI Strong authentication starts with hashed passwords and a clean OAuth2 login flow. FastAPI gives first-class support for both. Let’s break it down 👇 #FastAPI #Python #OAuth2 #JWT #100DaysOfCode #jwt
Wie bleibt #OAuth2 sicher nach dem Login? #XDEV SSE löst das per Auto-Revalidierung statt komplexem Backchannel-Logout – effizient, fail-safe, frontend-ready. Mehr von Alexander Bierler: javapro.io/de/xdev-sse-ve… @XDEVSoftware #OpenSource #Vaadin @vaadin #JAVAPRO #SpringSecurity

Pro tip: Always combine Authorization Code flow + PKCE with HttpOnly cookies. It drastically reduces the risk of token theft from XSS attacks. 🚀 #OAuth2 #AppSecurity #CyberSecurity #SecureLogin #WebSecurity #DevSecOps #PKCE #Infosec #Programming #TechTips

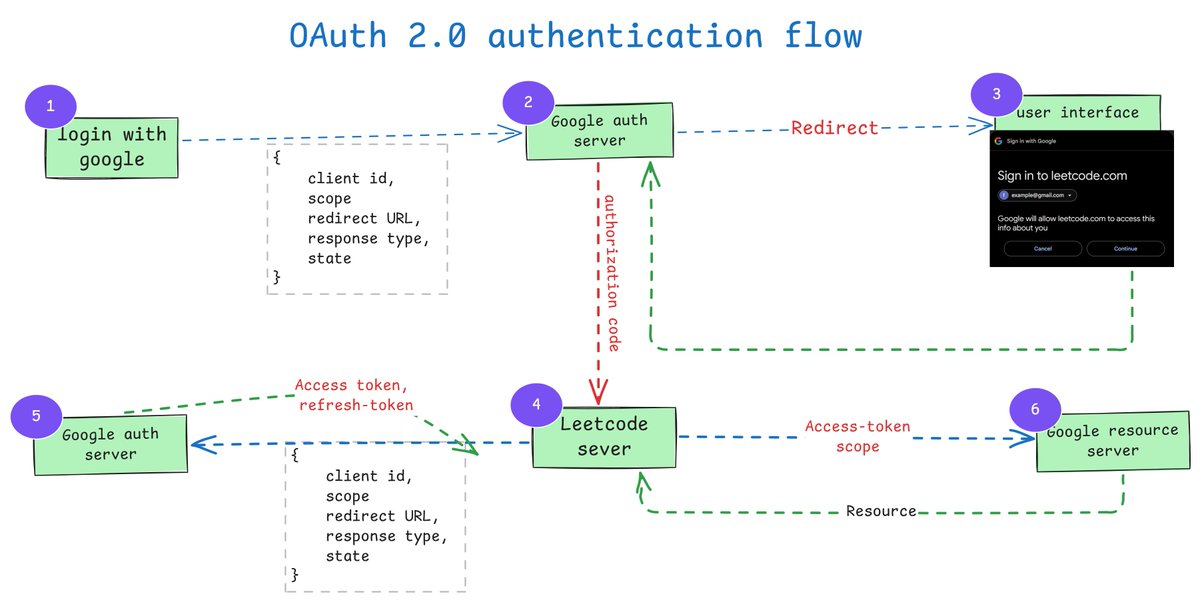
🧠 OAuth 2.0 Authentication — Visualized Ever wondered what actually happens when you “Login with Google”? I broke down the OAuth 2.0 flow into a clean diagram from the initial login click to token exchange and resource access. Leetcode via Google #OAuth2 #backenddevloper
Day 2 - REST APIs & OAuth2.0 with FastAPI 🚀 Built a REST API & learned proper naming conventions FastAPI auto-validates requests with Pydantic Used @field_validator for custom error messages 📌 Explored OAuth2.0 with OpenID Connect for authentication 🔐 #FastAPI #OAuth2 #OpenID



Hi Folks, I spent my Sunday playing with: - #Storyblok custom applications - #Oauth2 - #LaravelSocialite - #LaravelLivewire - #MaryUI (#tailwindcss + #daisyui)

OAuth2 allows other websites/apps to access your account info without giving them your password. You give permission by clicking "Log in with" and authorise an authorization code exchange. It's secure and commonly used. #oauth2 #websecurity

OAuth 2.0 - Securely connect apps without sharing passwords. - Simplify logins, share access, stay in control. Your data, safeguarded. Read about OAuth2.0 in this short and colorful flyer. #OAuth2 #SecureConnections

Congratulations to Sh Jaimandeep Singh for successfully defending his PhD thesis during the viva voce on 21.08.2024. He carried out his research on Secure Design, Architecture and Configuration of authorisation protocols with emphasis on OAuth 2.0. @NFSU_Official #OAuth2.0


Kinde gives you a whole lot of ways to authenticate users via social and enterprise connections. Now you can bring your own custom OAuth 2.0 or Open ID connection. 🎉 Ta da! Authentication your way with Kinde. Get started —> docs.kinde.com/authenticate/c… #OIDC #Oauth2 #Auth

Secure your applications with OAuth 2.0 and Spring Security! Learn how these powerful tools protect your data and users. #CyberSecurityAwareness #OAuth2 #Spring brcm.tech/4nPmGlu

OAuth 2.0 is an authorization protocol often used to secure access to APIs. Here's what you need to know, from an API hacker's perspective. #api #oauth2 #apihacking #hackingtools zerodayhacker.com/what-is-oauth-…

Finally reached @fossasia #Fossasiasummit. I'm super excited for my talk tomorrow on #CIAM #OAuth2 #OIDC @OpenFGA . If you are in #Hanoi , I would love to meet you.

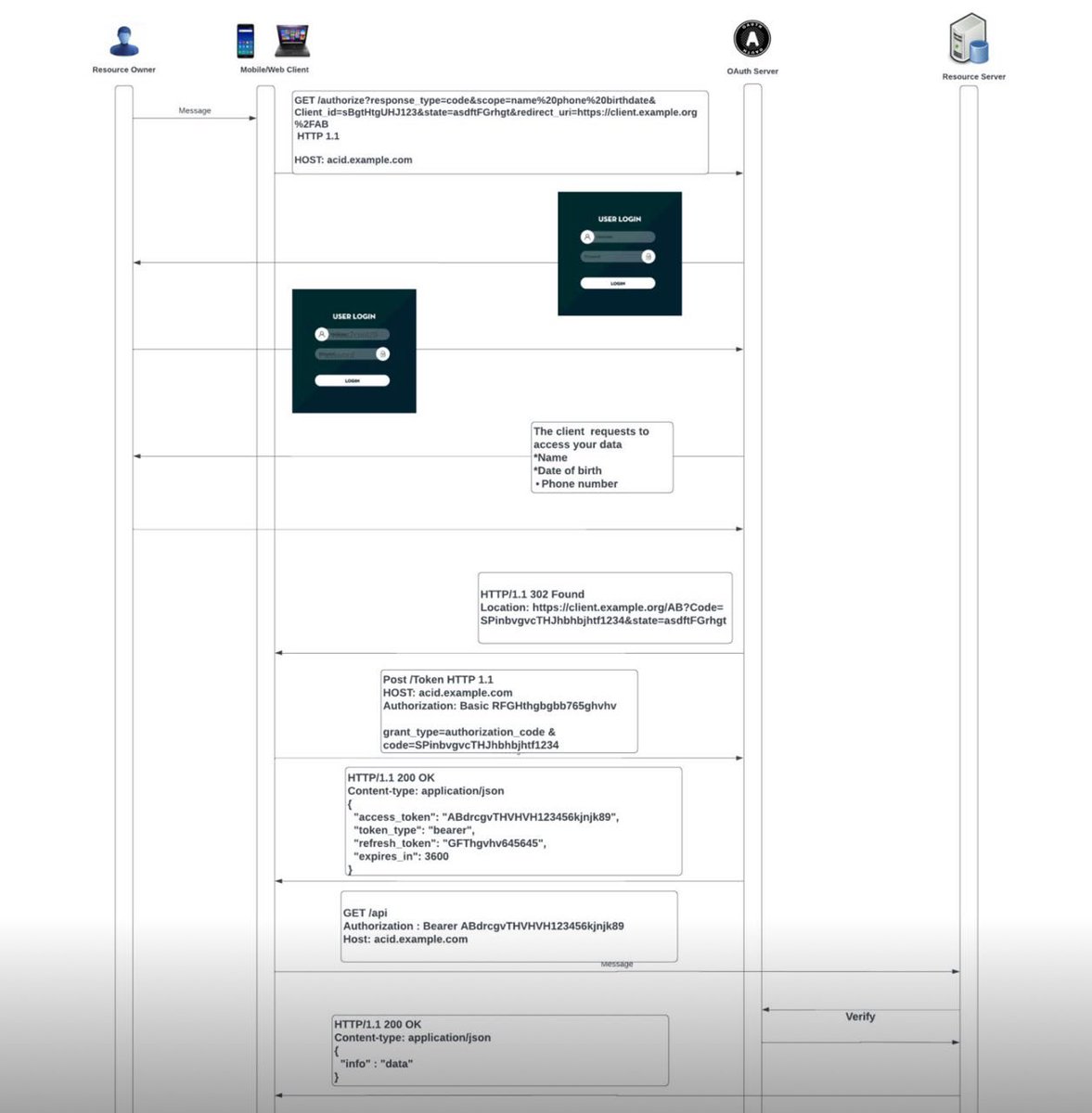
Help me out here— in #oauth2 why does IdP first return an auth code to the app, and then app calls IdP to exchange the authorization code for an access token+refresh token? Why not return the access token + refresh token in step 7?

And in a couple of minutes, a good talk about #OAuth2 to start the streak! All talks can be followed live here: bdxio.fr/live (this one's in French) @bdxio
Thank you, @fossasia for inviting me to #FOSSAsiaSummit2024 Hope my session on "Security on the Internet" which included #SAML, #OAuth2, #OIDC, #PasswordLess, @OpenFGA helped the attendees to secure their apps. Thank you, @quachanhvang for the awesome pics 🙏




OAuth 2.0 is the backbone of secure API access Here's the breakdown: - Grant types: Auth Code, Implicit, Client Credentials... - Core concepts: Tokens, Resource Owner, Auth Server - Security tips - OpenID Connect: for user identity A great visual by MasteringBackend. #OAuth2

This Saturday I will be speaking at #DefCon32 about OIDC misconfigurations and abuses in the context of CI/CD 🥴👹. Come check it out! info.defcon.org/event/?id=54867 @PaloAltoNtwks #OIDC #oauth2 #ci #cd

Security and usability rarely meet... but they do here. 🔐 This new guide breaks down how to integrate MCP tools in Copilot Studio using OAuth 2.0 Authorization Code Flow Read it here 👉 techcommunity.microsoft.com/blog/azure-ai-… #Azure #CopilotStudio #OAuth2 #Microsoft

Starting Jan 2025, Gmail enforces OAuth 2.0 for SMTP. Stay compliant and secure with Gmail SMTP Connect for Joomla! No passwords. No downtime. Just reliable, Google-approved email delivery. 👉 web357.com/gmail-smtp-con… #Web357 #OAuth2 #GmailSMTP #Security #JoomlaExtensions

Something went wrong.
Something went wrong.
United States Trends
- 1. Spotify 1.07M posts
- 2. Chris Paul 28.9K posts
- 3. Clippers 41.3K posts
- 4. Hartline 10.3K posts
- 5. Henry Cuellar 5,707 posts
- 6. #HappyBirthdayJin 102K posts
- 7. ethan hawke 4,160 posts
- 8. GreetEat Corp 1,168 posts
- 9. David Corenswet 7,008 posts
- 10. Jonathan Bailey 8,288 posts
- 11. South Florida 6,115 posts
- 12. #NSD26 25.1K posts
- 13. Apple Music 247K posts
- 14. Chris Henry 2,233 posts
- 15. Klein 16.4K posts
- 16. #JINDAY 80.6K posts
- 17. Nashville 33.4K posts
- 18. Adam Sandler 4,842 posts
- 19. #OurSuperMoonJin 81.3K posts
- 20. Ty Lue 1,440 posts