#ransomwaretech search results
Ransomware uses phishing, exploit kits, and remote desktop attacks with double extortion to encrypt and steal data, threatening finance and reputation. Wazuh offers layered detection and response through automation. #DataDefense #RansomwareTech ift.tt/emoj57H
🐙💀 Kraken Ransomware Alert! Exploits SMB flaws to hit Windows, Linux & ESXi, wipes backups, and targets SQL databases in big-game attacks. #RansomwareTech #DataEncryption #CyberSecurity #InfoSec #MalwareAlert #ThreatIntel #SecurityNews

Yurei ransomware, identified in Sept 2025, uses Go language and ChaCha20-Poly1305 encryption with per-file keys protected by secp256k1-ECIES. Targets corporate networks via dedicated dark web leak site. #RansomwareTech #EncryptionTech #DarkWebLeaks ift.tt/MRk2i7l
ESET uncovers PromptLock, the first AI-powered ransomware proof-of-concept using a local gpt-oss-20b model via Ollama API to automate malicious Lua scripts for encryption and data exfiltration. #AIThreats #RansomwareTech #Slovakia ift.tt/hdaLB3G
hendryadrian.com
First known AI-powered ransomware uncovered by ESET Research
ESET researchers discovered PromptLock, the first known AI-powered ransomware proof-of-concept that uses a local gpt-oss-20b model via the Ollama API to generate and execute malicious Lua scripts for...
Kraken ransomware exploits SMB flaws to access Windows, Linux, and VMware ESXi systems, benchmarks performance for targeted encryption, deletes backups, and targets SQL databases in big-game hunting attacks. #RansomwareTech #DataEncryption ift.tt/8W7e2bX
🔒 ¿Sabes qué es el #ransomware y cómo protegerte? Este ciberataque puede paralizar información y operaciones. Conoce cómo actúa, cómo prevenirlo y qué hacer ante un ataque. Informáte más: 👇 🔗 goo.su/64uy1OJ #Ciberseguridad @RaldelaNuezMor1 @vigintel @BioCubaFarma
🚨 🇨🇦 Alleged Ransomware Claim Industry: Technology Group: devman Victim: ravand.com Discovered: 2025-12-02 13:12 UTC
RansomHouse claims to have targeted Astrofein, a Technology organization. This reportedly threatens source code repositories, customer databases, and API credentials. Technology organizations must enforce network segmentation and rotate all authentication tokens. 🛡️…
Phishing, RDP exploits, and supply chain compromises dominate #ransomware entry points. Our latest blog breaks down the key attack vectors and how to defend against them. 🔗 Read more: dmnt.info/MnSh

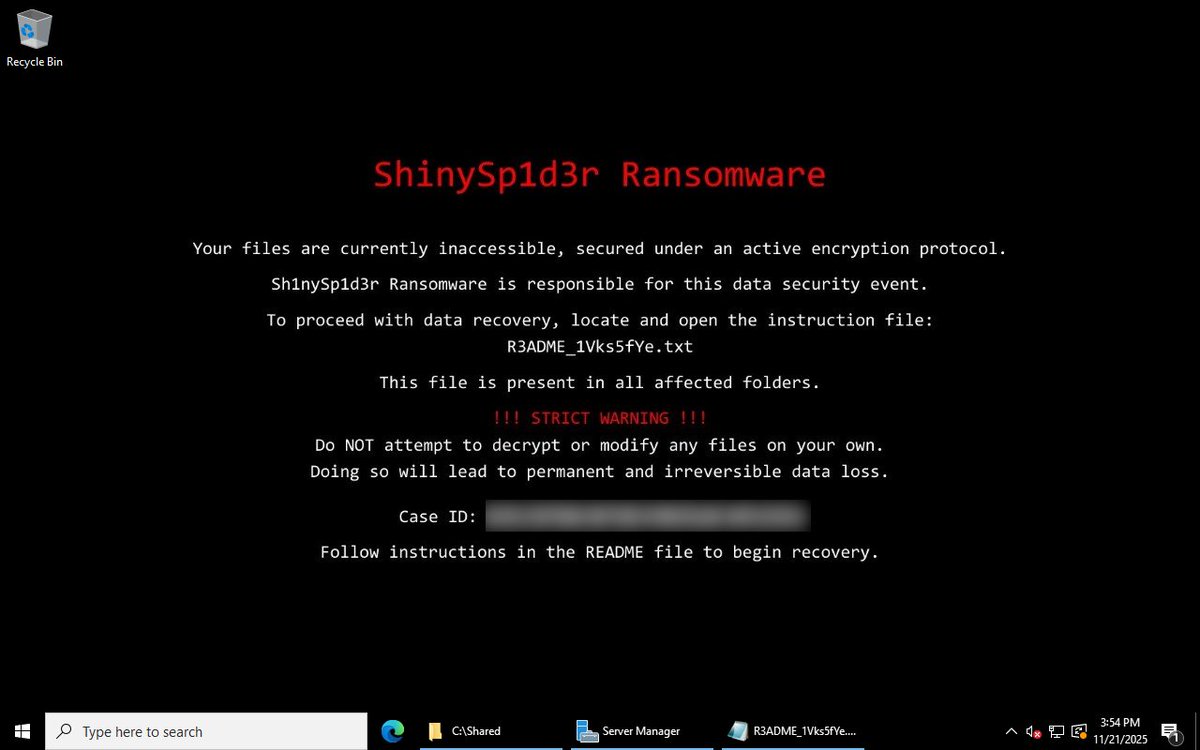
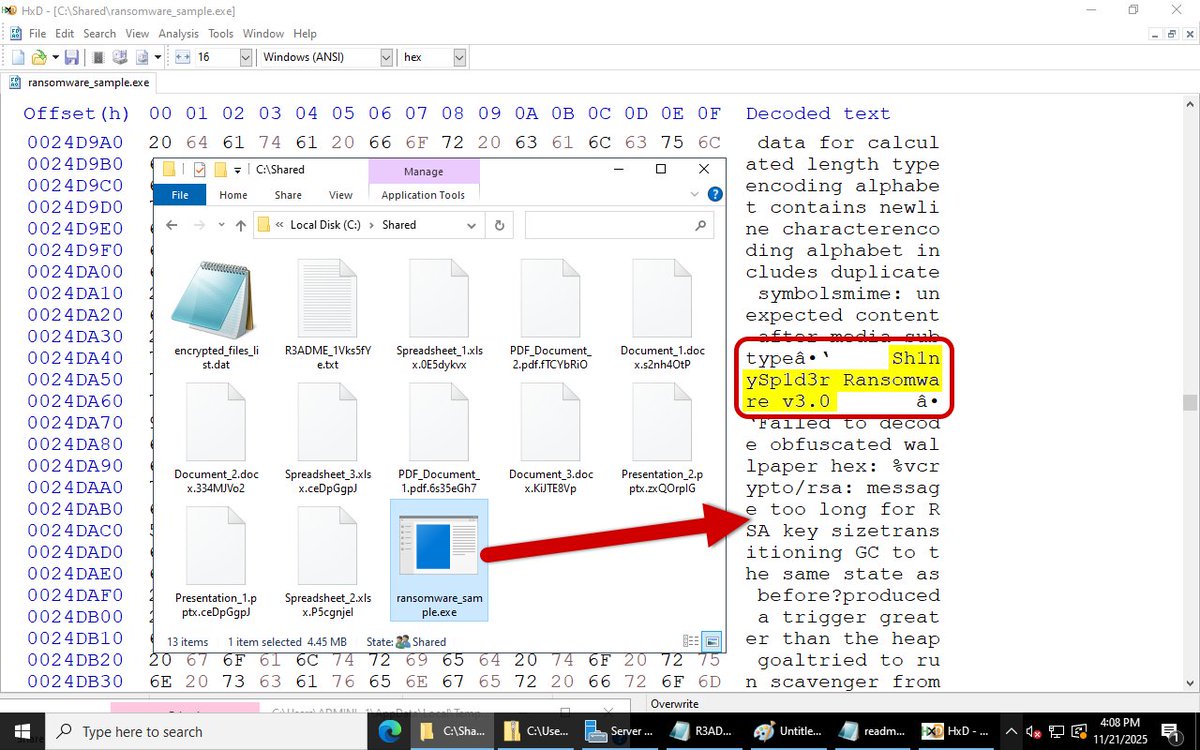
We are tracking indicators for a new #ransomware named "ShinySp1d3r" likely associated with the cybercrime group #BlingLibra (#ShinyHunters). Discovered samples are for Windows, but a Linux version will apparently be released at a later point. Details at bit.ly/4a6xMye

Kraken ransomware exploits SMB flaws to access Windows, Linux, and VMware ESXi systems, benchmarks performance for targeted encryption, deletes backups, and targets SQL databases in big-game hunting attacks. #RansomwareTech #DataEncryption ift.tt/8W7e2bX
Yurei ransomware, identified in Sept 2025, uses Go language and ChaCha20-Poly1305 encryption with per-file keys protected by secp256k1-ECIES. Targets corporate networks via dedicated dark web leak site. #RansomwareTech #EncryptionTech #DarkWebLeaks ift.tt/MRk2i7l
Ransomware uses phishing, exploit kits, and remote desktop attacks with double extortion to encrypt and steal data, threatening finance and reputation. Wazuh offers layered detection and response through automation. #DataDefense #RansomwareTech ift.tt/emoj57H
A resource containing all the tools each ransomware gangs uses github.com/BushidoUK/Rans…
ESET uncovers PromptLock, the first AI-powered ransomware proof-of-concept using a local gpt-oss-20b model via Ollama API to automate malicious Lua scripts for encryption and data exfiltration. #AIThreats #RansomwareTech #Slovakia ift.tt/hdaLB3G
hendryadrian.com
First known AI-powered ransomware uncovered by ESET Research
ESET researchers discovered PromptLock, the first known AI-powered ransomware proof-of-concept that uses a local gpt-oss-20b model via the Ollama API to generate and execute malicious Lua scripts for...
GitHub - BushidoUK/Ransomware-Tool-Matrix: A resource containing all the tools each ransomware gangs uses github.com/BushidoUK/Rans…
¡ELIMINA EL RANSOMWARE! Este tipo de virus es uno de los más letales para tu equipo y es común verlo infectando empresas y particulares Existen mecanismos para eliminarlos que pocos conocen Dentro mini-hilo 🧵 👇
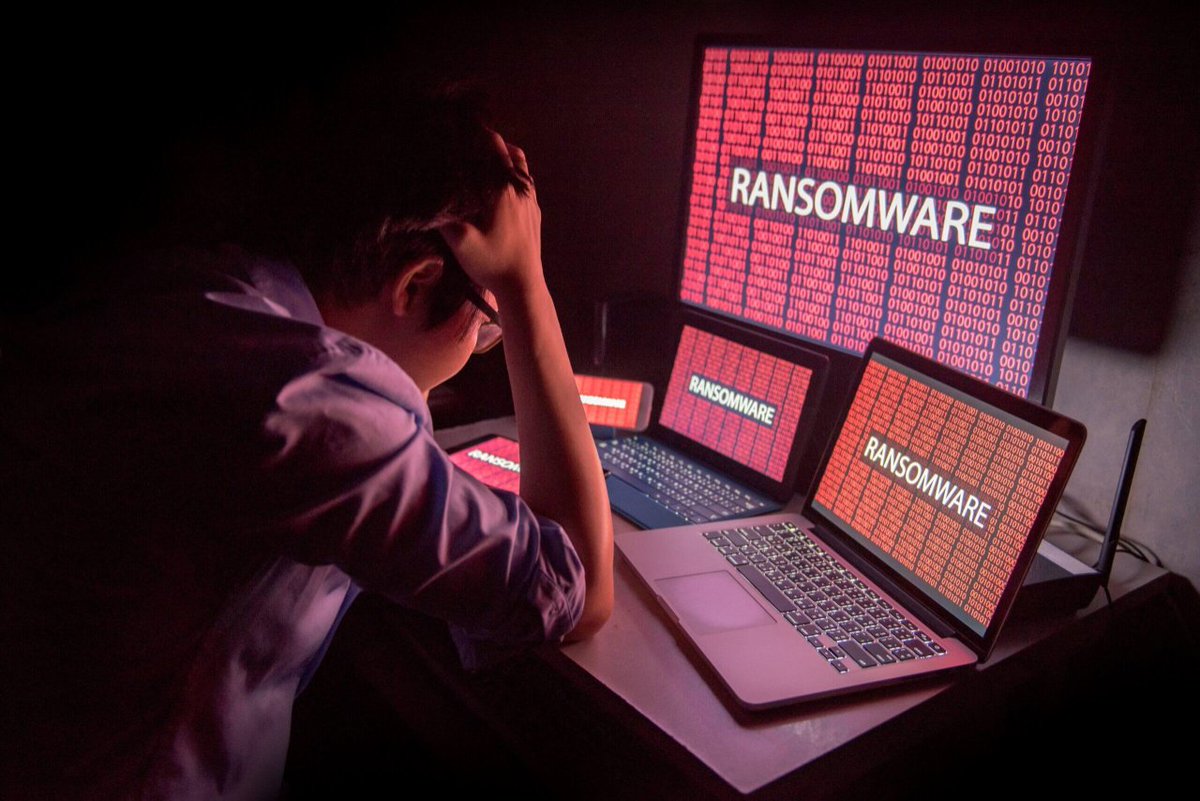
In this week’s Ransomware Roundup, #FortiGuardLabs examines the Rancoz #ransomware and how it encrypts files on compromised machines and demands ransom for file decryption. ⚠️ 💻 Learn more: ftnt.net/6019PJBSl

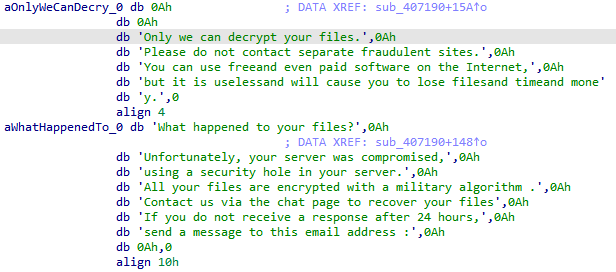
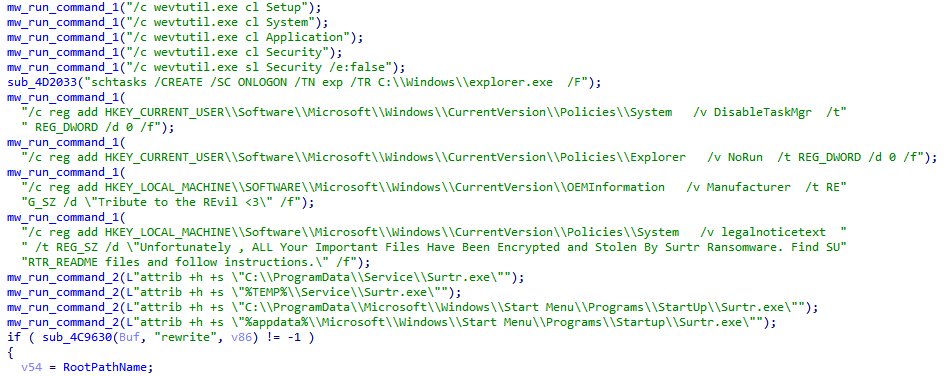
Hi people. New #ransomware called #Surtr which runs a lot of commands and applies some anti-analysis techniques like checking the debugger and sandbox.


🖥️Le #ransomware est un type d’attaque informatique relevant de la #cybercriminalité Il consiste à envoyer via une pièce jointe un programme malveillant🦹♂️
The #FBI wants network defenders to be aware of Ranzy Locker ransomware, which we have seen used in more than 30 cyberattacks since late last year. Review our FLASH alert for indicators of compromise and recommended mitigations. go.usa.gov/xecEP

El #ransomware consiste en la encriptación de tus archivos y documentos digitales para pedirte dinero a cambio de su recuperación. ¿Sabrías cómo evitarlo? 🔜Backup
📌Ransomware Keeps users from accessing critical files stored on their infected gadget. 📌Rootkits A sneaky type of malware that aims to get administrator rights to a machine without alerting you or your security software.
🐙💀 Kraken Ransomware Alert! Exploits SMB flaws to hit Windows, Linux & ESXi, wipes backups, and targets SQL databases in big-game attacks. #RansomwareTech #DataEncryption #CyberSecurity #InfoSec #MalwareAlert #ThreatIntel #SecurityNews

Something went wrong.
Something went wrong.
United States Trends
- 1. #AEWDynamite 18.9K posts
- 2. Giannis 76.3K posts
- 3. #Survivor49 2,444 posts
- 4. #TheChallenge41 1,843 posts
- 5. Claudio 28.3K posts
- 6. Jamal Murray 4,978 posts
- 7. Ryan Leonard N/A
- 8. Kevin Overton N/A
- 9. Ryan Nembhard 3,017 posts
- 10. #SistasOnBET 1,896 posts
- 11. Will Wade N/A
- 12. #iubb 1,182 posts
- 13. Achilles 5,153 posts
- 14. Kevin Knight 1,948 posts
- 15. Bucks 50.7K posts
- 16. Tyler Herro 1,648 posts
- 17. Dark Order 1,684 posts
- 18. Steve Cropper 4,474 posts
- 19. Yeremi N/A
- 20. Jericho Sims N/A