#redlinecybersecurity search results
Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Log all PowerShell script execution • Block macro-enabled docs • Limit access to remote management tools #DetectionEngineering #RedlineCyberSecurity #StayAhead

Throwback Thursday: NotPetya 2017 Originated from a weaponized update to Ukrainian accounting software (MeDoc). Spread via EternalBlue and Mimikatz, destroying systems across the globe. #ThrowbackThursday #RedlineCyberSecurity

If your last assessment started with a scan and ended with a PDF, it probably missed what matters. Professional testers. Meaningful findings. Real results. Redline delivers #PenetrationTesting #CyberSecurity #RedlineCyberSecurity #ManualTesting #SecurityAssessment #InfoSec

If your last pentest felt more like a scan than a test... #MemeMonday #RedlineCyberSecurity #PenetrationTesting #CyberSecurity #RealTesting #ScrollOfTruth #ManualTesting

Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Remove default credentials from all appliances • Separate production and test credentials • Separate databases and user account roles #RedlineCyberSecurity #SecurityTips

Throwback Thursday: Heartbleed 2014 Remember when every vuln got its own logo!? A flaw in OpenSSL's heartbeat extension exposed sensitive memory contents of vulnerable servers. No authentication needed. #ThrowbackThursday #RedlineCyberSecurity

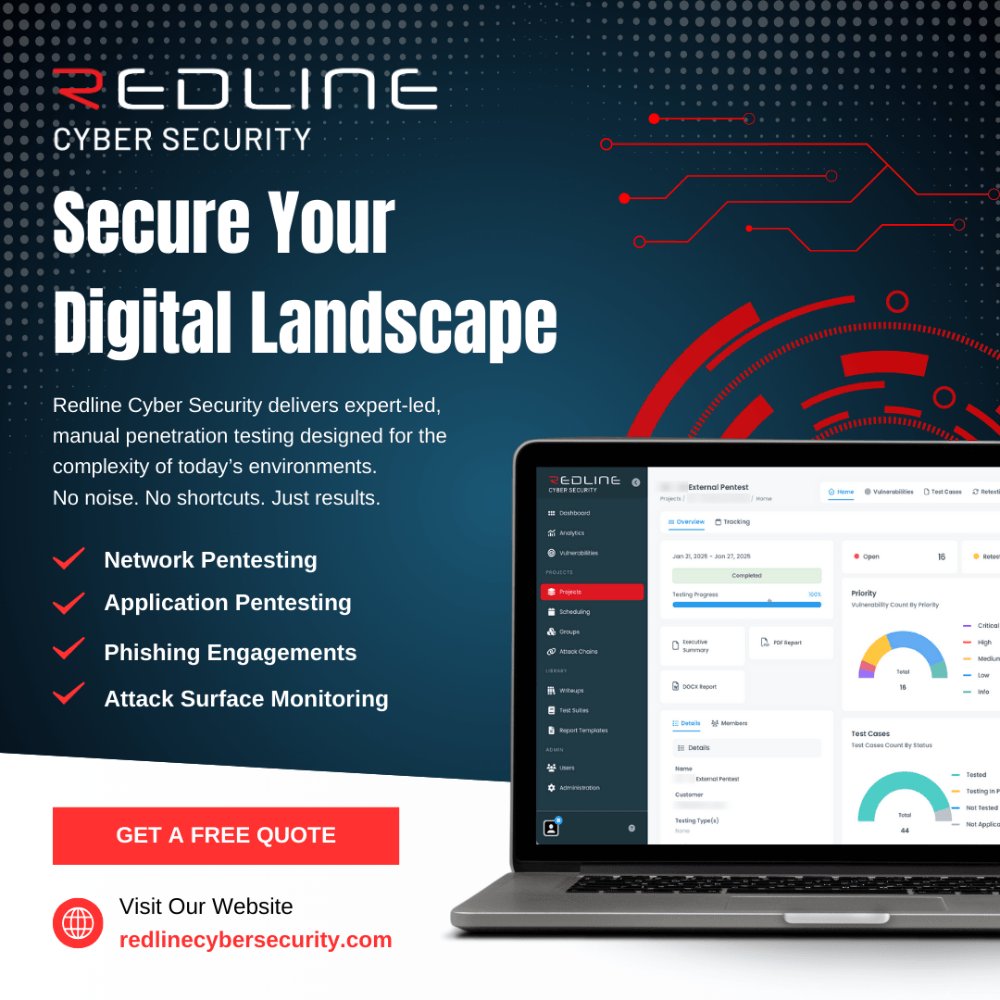
Secure your digital landscape with pentesting that delivers real results. • Network & Wireless Pentesting • Web, Mobile, API & Cloud Testing • Phishing Engagements & Social Engineering • Continuous Attack Surface Monitoring Get a free quote. 👇 #RedlineCyberSecurity
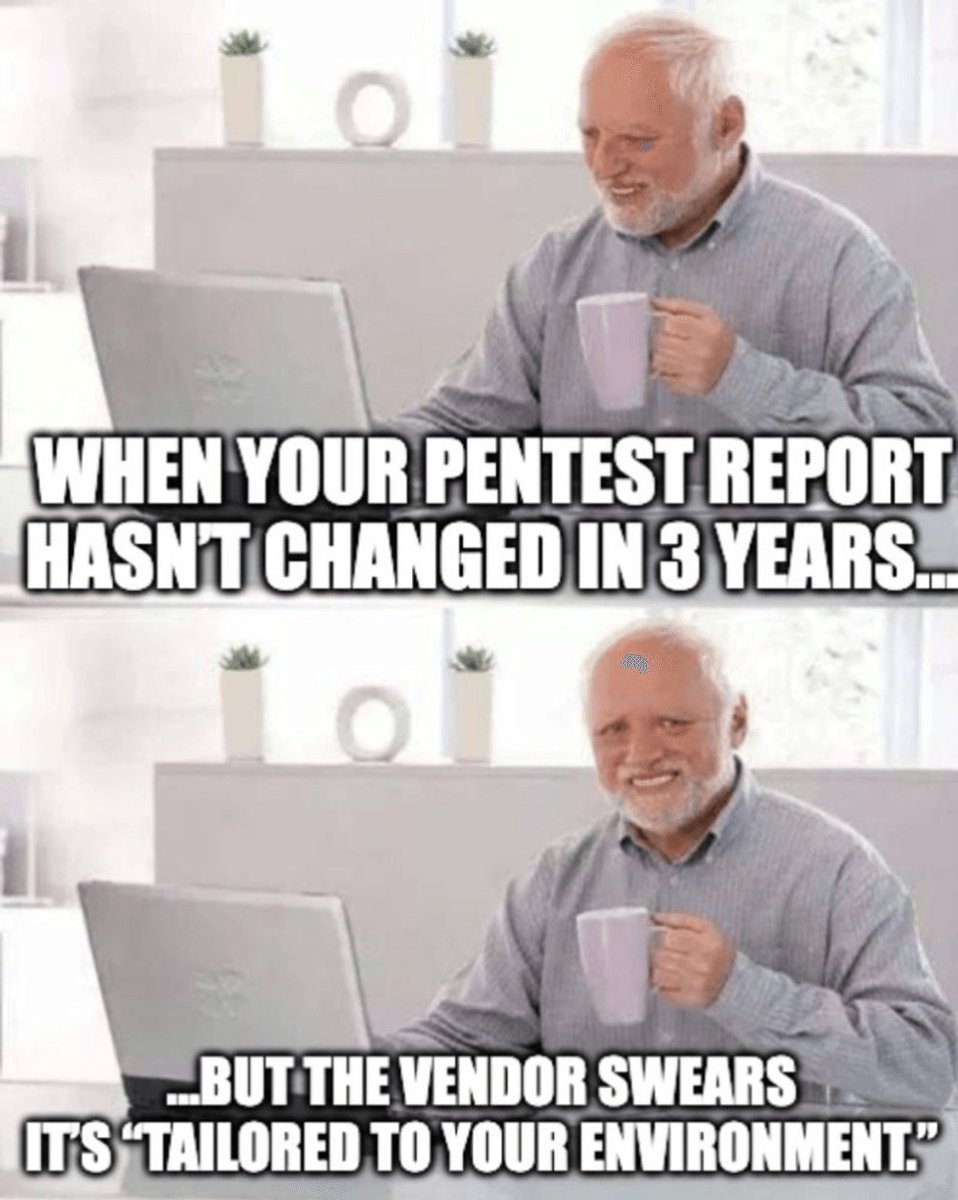
That look when your pentest report hasn’t changed in 3 years… ...and you start wondering if it was ever a real test at all. Redline delivers manual, expert-driven testing designed to uncover real risk... not recycled PDFs. #MemeMonday #PenetrationTesting #RedlineCyberSecurity
Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Enforce SMB signing • Disable local admin on standard user devices • Monitor AD groups for privilege escalation paths #IAM #CloudSecurity #RedlineCyberSecurity

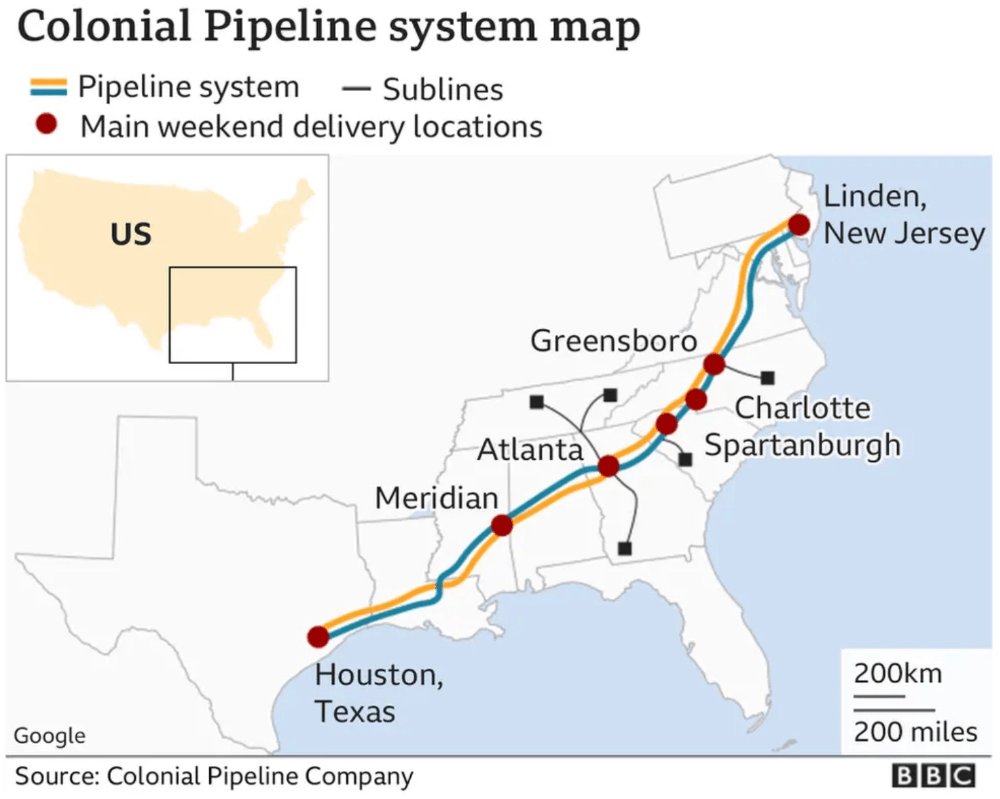
Throwback Thursday: Colonial Pipeline 2021 A compromised VPN account with no MFA led to ransomware halting 45% of the East Coast's fuel supply. The account was no longer in use but was still active and triggered a national impact. #ThrowbackThursday #RedlineCyberSecurity
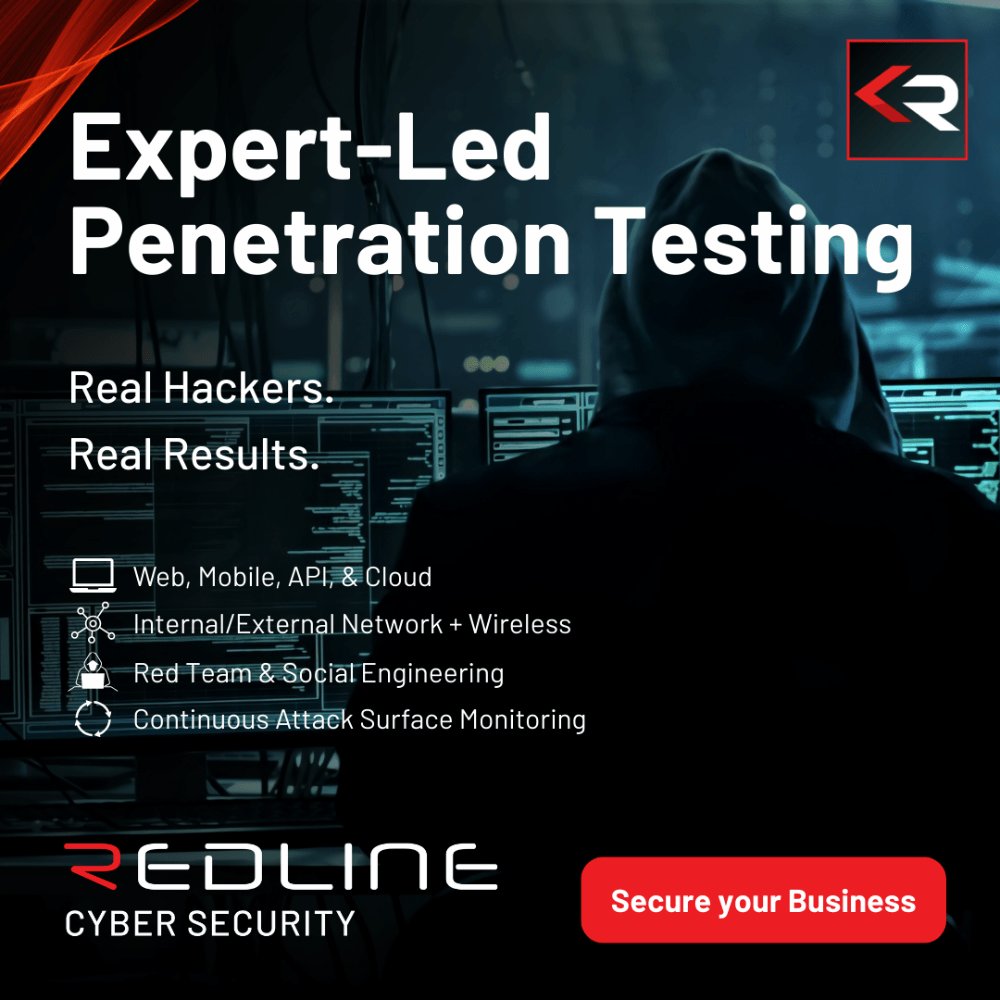
Tired of surface-level pentests and recycled reports? It's time to switch providers. Redline Cyber Security delivers high-impact, manual security testing designed to uncover real risk — not just generate another PDF. #PenetrationTesting #CyberSecurity #RedlineCyberSecurity
When a client says, “We want a real pentest — not just a scan.” #MemeMonday #RedlineCyberSecurity #PenetrationTesting #CyberSecurity #RealTestingNotScanning

Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Scan for shadow IT • Require MFA for all privileged accounts • Disable SMBv1 The older the system, the easier it breaks. #HardeningTips #RedlineCyberSecurity #SecurityBasics

Throwback Thursday: Sony BMG Rootkit Scandal (2005) Sony shipped CDs that installed a rootkit on PCs without consent. It hid itself, created vulnerabilities, and was nearly impossible to detect or remove, sparking major lawsuits. #ThrowbackThursday #RedlineCyberSecurity
If your last assessment started with a scan and ended with a PDF, it probably missed what matters. Professional testers. Meaningful findings. Real results. Redline delivers #PenetrationTesting #CyberSecurity #RedlineCyberSecurity #ManualTesting #SecurityAssessment #InfoSec

Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Monitor for unusual authentication behavior • Limit access to sensitive shares • Use separate admin workstations #CyberResilience #RedlineCyberSecurity #InfosecTips

Throwback Thursday: Conficker (2008) A Windows vulnerability (MS08-067) was weaponized into a fast-spreading worm. Even with a patch available, millions of machines were compromised into the botnet. Lesson: Patch your systems! #ThrowbackThursday #RedlineCyberSecurity

When a client says, “We want a real pentest — not just a scan.” #MemeMonday #RedlineCyberSecurity #PenetrationTesting #CyberSecurity #RealTestingNotScanning

If your last pentest felt more like a scan than a test... #MemeMonday #RedlineCyberSecurity #PenetrationTesting #CyberSecurity #RealTesting #ScrollOfTruth #ManualTesting

Throwback Thursday: NotPetya 2017 Originated from a weaponized update to Ukrainian accounting software (MeDoc). Spread via EternalBlue and Mimikatz, destroying systems across the globe. #ThrowbackThursday #RedlineCyberSecurity

Throwback Thursday: Conficker (2008) A Windows vulnerability (MS08-067) was weaponized into a fast-spreading worm. Even with a patch available, millions of machines were compromised into the botnet. Lesson: Patch your systems! #ThrowbackThursday #RedlineCyberSecurity

Throwback Thursday: Sony BMG Rootkit Scandal (2005) Sony shipped CDs that installed a rootkit on PCs without consent. It hid itself, created vulnerabilities, and was nearly impossible to detect or remove, sparking major lawsuits. #ThrowbackThursday #RedlineCyberSecurity

Throwback Thursday: Colonial Pipeline 2021 A compromised VPN account with no MFA led to ransomware halting 45% of the East Coast's fuel supply. The account was no longer in use but was still active and triggered a national impact. #ThrowbackThursday #RedlineCyberSecurity

Throwback Thursday: Heartbleed 2014 Remember when every vuln got its own logo!? A flaw in OpenSSL's heartbeat extension exposed sensitive memory contents of vulnerable servers. No authentication needed. #ThrowbackThursday #RedlineCyberSecurity

Secure your digital landscape with pentesting that delivers real results. • Network & Wireless Pentesting • Web, Mobile, API & Cloud Testing • Phishing Engagements & Social Engineering • Continuous Attack Surface Monitoring Get a free quote. 👇 #RedlineCyberSecurity

If your last assessment started with a scan and ended with a PDF, it probably missed what matters. Professional testers. Meaningful findings. Real results. Redline delivers #PenetrationTesting #CyberSecurity #RedlineCyberSecurity #ManualTesting #SecurityAssessment #InfoSec

Every Friday, we share 3 quick tips based on what we’re seeing during our penetration tests. • Log all PowerShell script execution • Block macro-enabled docs • Limit access to remote management tools #DetectionEngineering #RedlineCyberSecurity #StayAhead

Tired of surface-level pentests and recycled reports? It's time to switch providers. Redline Cyber Security delivers high-impact, manual security testing designed to uncover real risk — not just generate another PDF. #PenetrationTesting #CyberSecurity #RedlineCyberSecurity

That look when your pentest report hasn’t changed in 3 years… ...and you start wondering if it was ever a real test at all. Redline delivers manual, expert-driven testing designed to uncover real risk... not recycled PDFs. #MemeMonday #PenetrationTesting #RedlineCyberSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Monday 28K posts
- 2. TOP CALL 3,800 posts
- 3. AI Alert 1,418 posts
- 4. Market Focus 2,557 posts
- 5. #centralwOrldXmasXFreenBecky 555K posts
- 6. SAROCHA REBECCA DISNEY AT CTW 575K posts
- 7. #MondayMotivation 7,576 posts
- 8. #BaddiesUSA 66.1K posts
- 9. #LingOrmDiorAmbassador 295K posts
- 10. NAMJOON 56.3K posts
- 11. Check Analyze N/A
- 12. Token Signal 1,884 posts
- 13. Rams 30.5K posts
- 14. #LAShortnSweet 24.4K posts
- 15. DOGE 183K posts
- 16. Chip Kelly 9,328 posts
- 17. Vin Diesel 1,577 posts
- 18. Stacey 23.8K posts
- 19. Scotty 10.5K posts
- 20. Gilligan 4,083 posts

