#springsecuritytutorial ผลการค้นหา
Cybersecurity Developer Learning Roadmap |-- Foundations of Cybersecurity | |-- Understanding Cyber Threats & Attack Vectors | |-- Principles of Confidentiality, Integrity & Availability (CIA Triad) | |-- Types of Cyber Attacks: Malware, Phishing, DDoS, MITM | |-- Security…


FREE SIEM Training Resources and Practical Projects to Level Up Your Cybersecurity Skills If you’ve been thinking about deepening your hands-on experience with various SIEM platforms or working on real projects, now’s the perfect time to get started! If you’re seeking to…

💡 Need A Clue On Today's Quiz? Phishing is a fraudulent method used by attackers to steal sensitive information by pretending to be a legitimate service. Learn more: spurprotocol.com/post/what-is-a…

Keep Your Smartphone Smart & Secure! 📱 Regular updates, trusted apps, and strong passwords keep your device safe. Use security tools and turn off Bluetooth when not needed. Small habits create strong digital protection! #SmartphoneSecurity #CyberSafety #ProtectYourDevice…

Spring Boot Microservices Security with JWT Authentication sourcecodeexamples.net/2024/05/spring… #java #springboot #microservices #jwt #springsecurity
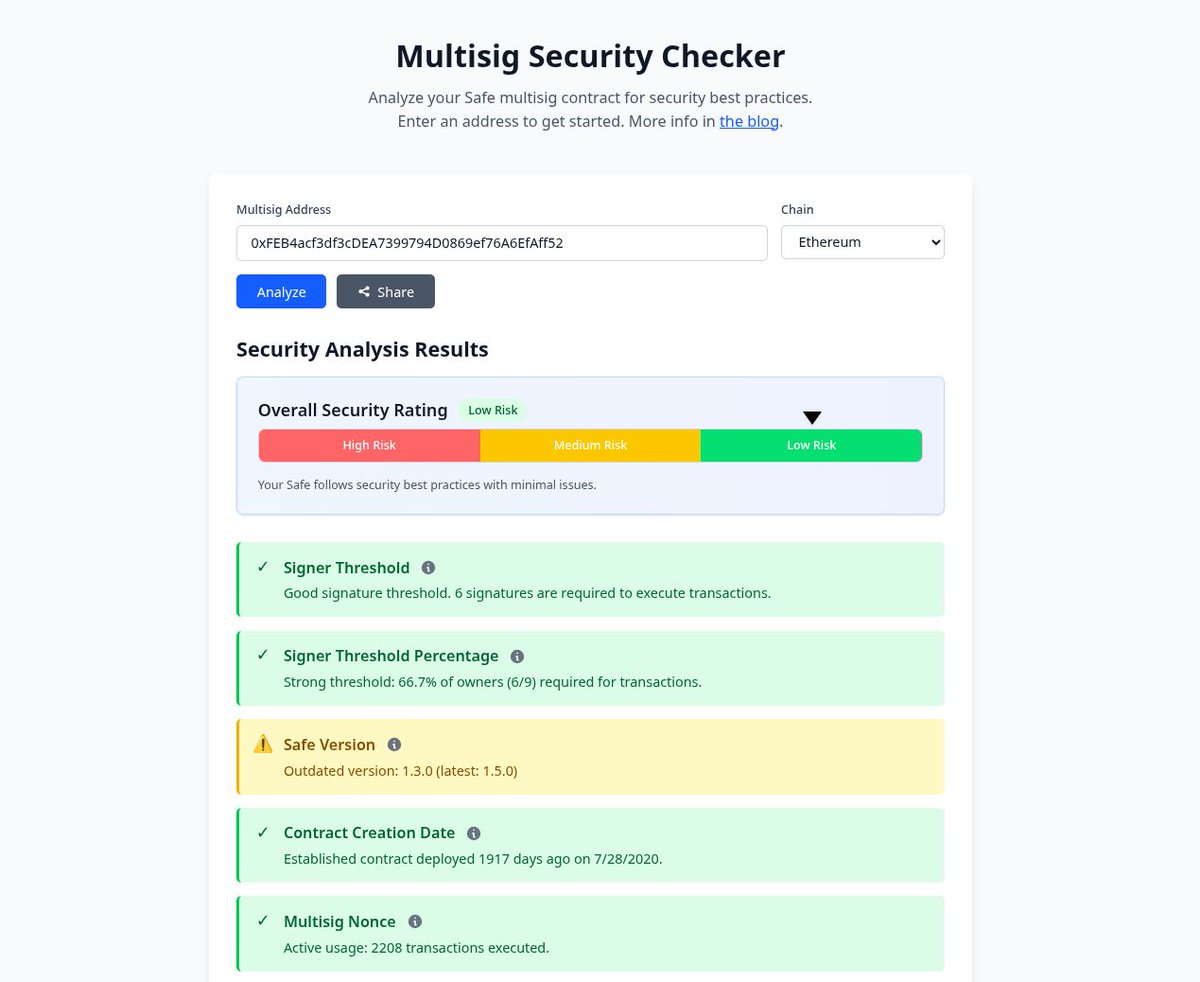
In honor of multisig security month, I'm happy to present a new tool that analyzes the security of a Safe multisig's configuration. 🛠️ Not every Safe is safe! Test it out on the example multisig addresses 👇
Everyone has a Smart TV. But when was the last time you updated it? 👀 This 63-sec clip will make you think twice before switching it on. 🎥 Full story → youtu.be/cqDaOhqsHU0 #SmartTVHack #CyberSecurity #IoT #DecodingCyberSecurity
These days, cyberattacks are becoming increasingly common. If you're a developer, you should level up your cybersecurity skills. In this tutorial, Alex goes over common cyberattacks like cross-site scripting (XSS) and insecure API calls, and how you can protect your sites…

🔊 There’s no shortage of noise in cybersecurity. What really matters? The fundamentals. Our guide breaks down 11 essential security controls every org needs to: 🔹 Strengthen defenses 🔹 Build resilience 🔹 Limit attack impact Get the checklist: bit.ly/434EL6G
Security keeps user data safe, ensures only authorized access, and protects applications from attacks. Learning Spring Security taught me how to build secure, reliable software a key skill for every software engineer. #SoftwareEngineering #SpringSecurity #WebSecurity #Java
Bug Bounty Giveaway for Learners! I’m giving away this complete Bug Bounty & Web Security Course Folder (18 modules) — covering: - SQL Injection - XSS & CORS - Brute Forcing - File Vulnerability - Burp Suite + Labs setup …and everything from beginner to advanced! Cost About -…
Multifactor authentication never hurts! Add an extra layer of security by enabling multi-factor authentication, and avoid the pain of a hacked account. Learn more with your #CybersecurityAwarenessMonth toolkit: hubs.la/Q03L_vNN0
Spring Office Hours: S4E28 - Securing MCP Servers with Spring AI dy.si/7QW9V

youtube.com
YouTube
Spring Office Hours: S4E28 - Securing MCP Servers with Spring AI
Stay alert, stay protected! Avoid clicking on suspicious links, update your passwords, and report cyber incidents to CERT-In. Stay Safe Online! #IndianCERT #Cybersecurity #CyberAwareness #NCSAM #MeitY #ISEA #MyGoV #DigitalIndia #CSK #CyberJagritBharat

Something went wrong.
Something went wrong.
United States Trends
- 1. SNAP 1.01M posts
- 2. Jamaica 244K posts
- 3. $NVDA 85.6K posts
- 4. Don Lemon 3,416 posts
- 5. Nelson 28.9K posts
- 6. Nvidia 40.3K posts
- 7. Tucker 97.8K posts
- 8. Amare 2,304 posts
- 9. Hurricane Melissa 177K posts
- 10. #NationalFirstRespondersDay 1,420 posts
- 11. New Hope 34.8K posts
- 12. Wikipedia 116K posts
- 13. Fuentes 78K posts
- 14. Nokia 14.8K posts
- 15. Western Union 5,294 posts
- 16. Jensen 10.8K posts
- 17. Ben Shelton N/A
- 18. Riley Gaines 105K posts
- 19. Grokipedia 182K posts
- 20. Carlton 1,621 posts