#anomalydetection search results
Discover how the AKD1500 enables real-time anomaly detection! Join us at Embedded World North America, Booth 3080, Anaheim. #EmbeddedWorld #NeuromorphicInnovation #AnomalyDetection #EdgeComputing #TechInnovation #SmartTechnology #AnaheimEvents #IoTDevices #FutureOfTech
Our BLAW #AI Engineering team’s Vikram Sunil Bajaj (@vikram_bajaj) is presenting "Can #LLMs Find a Needle in a Haystack? A Look at #AnomalyDetection Language Modeling" during #EMNLP2025's Virtual Poster Session today (8-9 AM CST) bloom.bg/4qFzWe3 #NLProc #GenAI (1/3)

This research introduces a novel approach utilizing #LLMs for textual #anomalydetection across binary, multi-class, and unlabeled modalities bloom.bg/4qFzWe3 #EMNLP2025 #NLProc (2/3)

Our BLAW #AI Engineering team’s Vikram Sunil Bajaj (@vikram_bajaj) is presenting "Can #LLMs Find a Needle in a Haystack? A Look at #AnomalyDetection Language Modeling" during #EMNLP2025's Virtual Poster Session today (8-9 AM CST) bloom.bg/4ozsjV5 #NLProc #GenAI (1/3)

Exploring anomaly detection in RTI. How to easily identify anomalies and create an agentic workflow. Making AI tangible and demonstrating its business impact. #RealTimeIntelligence #AnomalyDetection youtube.com/watch?v=4aoGqT…
Anomaly detection you can actually use. Pattern recognition that delivers clear answers. 📈🧠 AI is ready to change the game. Coming this November… #AnomalyDetection #AI #Cybersecurity

ICCV’25: RareCLIP frames online zero-shot industrial AD with a rarity estimator on top of CLIP. Single-pass, streaming-friendly, and real-time oriented. Paper: openaccess.thecvf.com/content/ICCV20… #ICCV2025 #AnomalyDetection #VisualInspection #ZeroShot #CLIP
いよいよ画像の異常検知もVLMの時代になってきました。 VLM対応によってZero-shotやFew-shotが可能となり、これまで大量の学習が必要だった分類・セグメンテーション・物体検出といった従来手法は、異常検知においてはもはや不要になりつつあると思います。#異常検知 #anomalydetection #VLM

🔥 Read our Paper 📚 Anomaly Detection in Machining Centers Based on Graph Diffusion-Hierarchical Neighbor Aggregation Networks 🔗 mdpi.com/2076-3417/13/2… 👨🔬 by Jiewen Huang et al. #machiningcenter #anomalydetection

#CFP for the #SpecialIssue "Anomaly and Intrusion Detection in Networks", edited by Dr. Eszter Kail, Dr. Anna Bánáti, Prof. Miklós Kozlovszky. mdpi.com/journal/future… #anomalydetection #intrusiondetection #machinelearning #legacynetworks #XAI #IoT #IIoT

Threats aren’t always loud. Sometimes they’re subtle. Discover how anomaly detection gives security teams new eyes in this week’s Unlocked ⤵️ 🔗 unlocked.everykey.com/p/anomaly-dete… #Cybersecurity #AnomalyDetection #InfoSec #Everykey

100% real time anomaly detection. Uptycs flags unusual CPU, disk, and network activity as it happens, giving teams visibility to stop threats before they spread. hubs.ly/Q03Kx81Z0 #ThreatDetection #AnomalyDetection

Anomaly detection through unsupervised learning identifies the unusual by first understanding the usual. It's statistical intuition—recognizing when something doesn't fit the pattern, even when we can't articulate why. #UnsupervisedLearning #AnomalyDetection #StatisticalIntuition…
Unplanned downtime = lost yield, lost revenue, lost margin. That’s why Intel partnered with Seeq to transform their fab facility operations. ⚡ Spots are limited, register now: ow.ly/8Vnj50WU0M8 #SmartManufacturing #AnomalyDetection #OperationalExcellence

AI is revolutionizing cybersecurity by rapidly detecting and predicting digital threats through anomaly detection and pattern analysis. It acts as a digital guardian, offering capa... #AIandCybersecurity #DigitalGuardians #AnomalyDetection youaccel.com/blog/ai-and-cy…
Balancing Narrative Complexity and Actionability in Real-Time Anomaly Detection Using Generative AI 🔗 hubs.li/Q03HXvby0 #AnomalyDetection #ExplainableAI #LLM #GenAI #OperationalAI #RealTimeAI #AppliedAISummit

#IoT #AnomalyDetection using #Python-based Deep Learning! #BigData #Analytics #DataScience #AI #MachineLearning #IIoT #PyTorch #Python #RStats #TensorFlow #Java #CloudComputing #Serverless #DataScientist #Linux #Books #Programming #Coding #100DaysofCode geni.us/IoT-Anomaly

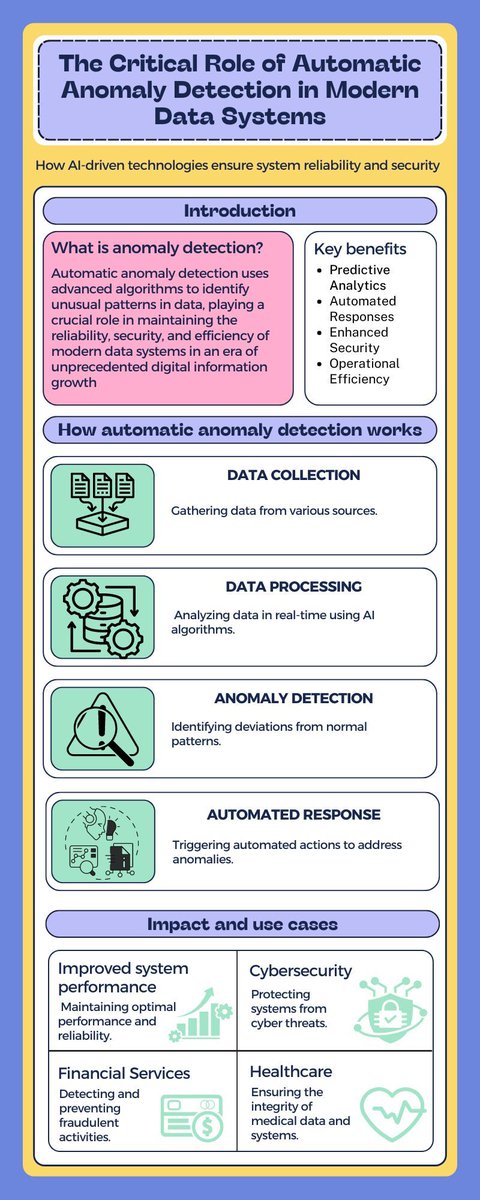
Automated anomaly detection in business metrics alerts you to problems before they become crises. AI continuously monitors KPIs, learning what's normal and flagging deviations instantly. Proactive problem detection. #AIAnalytics #AnomalyDetection #ProactiveMonitoring…
Use anomaly detection on delivery network telemetry to flag unusual spending patterns or emerging inefficiencies before they become material. #AnomalyDetection #Telemetry #CostSavings #StreamingNetworks #Fintech #ArtificialIntelligence #ITSM #FinOps #ServiceNow

Discover how the AKD1500 enables real-time anomaly detection! Join us at Embedded World North America, Booth 3080, Anaheim. #EmbeddedWorld #NeuromorphicInnovation #AnomalyDetection #EdgeComputing #TechInnovation #SmartTechnology #AnaheimEvents #IoTDevices #FutureOfTech
Our BLAW #AI Engineering team’s Vikram Sunil Bajaj (@vikram_bajaj) is presenting "Can #LLMs Find a Needle in a Haystack? A Look at #AnomalyDetection Language Modeling" during #EMNLP2025's Virtual Poster Session today (8-9 AM CST) bloom.bg/4ozsjV5 #NLProc #GenAI (1/3)

Talus labs integrates AI with blockchain to create resilient systems for anomaly detection and risk assessment. Our solutionracy and speed are paramount. Discover the Talus labs difference! #TalusLabs #AnomalyDetection #RiskManagement
Talus labs integrates AI with blockchain to create resilient systems for anomaly detection and risk assessment. Our solutions arecuracy and speed are paramount. Discover the Talus labs difference! #TalusLabs #AnomalyDetection #RiskManagement
The authors of "Can #LLMs Find a Needle in a Haystack? A Look at #AnomalyDetection Language Modeling" are our #AI researchers Leslie Barrett, @vikram_bajaj & Robert Kingan bloom.bg/4qFzWe3 #EMNLP2025 #GenAI (3/3)
This research introduces a novel approach utilizing #LLMs for textual #anomalydetection across binary, multi-class, and unlabeled modalities bloom.bg/4qFzWe3 #EMNLP2025 #NLProc (2/3)

Our BLAW #AI Engineering team’s Vikram Sunil Bajaj (@vikram_bajaj) is presenting "Can #LLMs Find a Needle in a Haystack? A Look at #AnomalyDetection Language Modeling" during #EMNLP2025's Virtual Poster Session today (8-9 AM CST) bloom.bg/4qFzWe3 #NLProc #GenAI (1/3)

Threats aren’t always loud. Sometimes they’re subtle. Discover how anomaly detection gives security teams new eyes in this week’s Unlocked ⤵️ 🔗 unlocked.everykey.com/p/anomaly-dete… #Cybersecurity #AnomalyDetection #InfoSec #Everykey

📶🤖 Anomaly Detection Against Fake Base Station Threats Using Machine Learning 🆕 Newly published in the Journal of Cybersecurity and Privacy 📖 Read more: mdpi.com/2624-800X/5/4/… #5G #NetworkSecurity #AnomalyDetection #FakeBaseStation @ComSciMath_Mdpi
Today's pentest crystal ball. Implement and monitor anomaly detection systems. Visit ayb.ad. #AnomalyDetection #CyberMonitoring #AccountSecurity #ThreatDetection

Discover how #anomalydetection is revolutionizing #materialhandling systems. Check out @BeldenInc Vikram Kolluru's interview in @AW_Robotics. #DigitalAutomation #AutomatedWarehouses #Industry40 #Belden sprou.tt/1wzIaxcWx3t
automatedwarehouseonline.com
How is anomaly detection improving material handling systems? - Automated Warehouse
Vikram Kolluru of Belden discussed trends and technologies related to material handling systems, including robotics in warehouses.
Talus labs integrates AI with blockchain to create resilient systemsre tailored for industries like finance and security, where accuracy and speed are paramount. Discover the Talus labs difference! #TalusLabs #AnomalyDetection #RiskManagement
Baron Coleman the Google trends guy Live #CharlieKirk #anomalydetection youtube.com/live/U--7Zta4y…

youtube.com
YouTube
Why The Aggressive Defense of Mikey McCoy? And How Much Were TPUSA...
🧠 New in Journal of Cybersecurity and Privacy 🌐 AI-Powered Security for IoT Ecosystems: A Hybrid Deep Learning Approach to Anomaly Detection 🔗 Read more: mdpi.com/2624-800X/5/4/… #AnomalyDetection #DeepLearning #CNN @ComSciMath_Mdpi
Anomaly detection you can actually use. Pattern recognition that delivers clear answers. 📈🧠 AI is ready to change the game. Coming this November… #AnomalyDetection #AI #Cybersecurity

This research introduces a novel approach utilizing #LLMs for textual #anomalydetection across binary, multi-class, and unlabeled modalities bloom.bg/4qFzWe3 #EMNLP2025 #NLProc (2/3)

#IoT #AnomalyDetection using #Python-based Deep Learning! #BigData #Analytics #DataScience #AI #MachineLearning #IIoT #PyTorch #Python #RStats #TensorFlow #Java #CloudComputing #Serverless #DataScientist #Linux #Books #Programming #Coding #100DaysofCode geni.us/IoT-Anomaly

100% real time anomaly detection. Uptycs flags unusual CPU, disk, and network activity as it happens, giving teams visibility to stop threats before they spread. hubs.ly/Q03Kx81Z0 #ThreatDetection #AnomalyDetection

Great learning, networking opportunity! The Real time analytics conf is from May 7-9 in San Jose, CA. If you want to register, you can save 30% on your ticket with the code MANTRI30 Link to Realtime Summit website in the comments #RealTimeAnalytics #RTASummit #anomalydetection

Cove's Matt Bayliss introduces the first capability of #AnomalyDetection, starting with #Honeypots - an always-on defense mechanism for detecting brute force attacks. Watch now: spr.ly/6013ABYst Learn more: spr.ly/6016ABYsa #cyberresilience

#AnomalyDetection and Autoencoders in #Keras. #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #Python #RStats #TensorFlow #JavaScript #ReactJS #GoLang #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode buff.ly/3L9BCc7




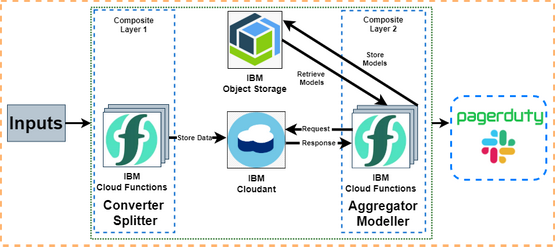
Discussing the implementation of a deep learning-based anomaly detection system for IBM Cloud platforms. #CloudComputing #AnomalyDetection #DeepLearning
いよいよ画像の異常検知もVLMの時代になってきました。 VLM対応によってZero-shotやFew-shotが可能となり、これまで大量の学習が必要だった分類・セグメンテーション・物体検出といった従来手法は、異常検知においてはもはや不要になりつつあると思います。#異常検知 #anomalydetection #VLM

🕵️♂️ Exploring anomaly detection tools. They help spot unusual patterns in datasets. Great for outlier detection! Try this example with PyOD. #AnomalyDetection #MachineLearning

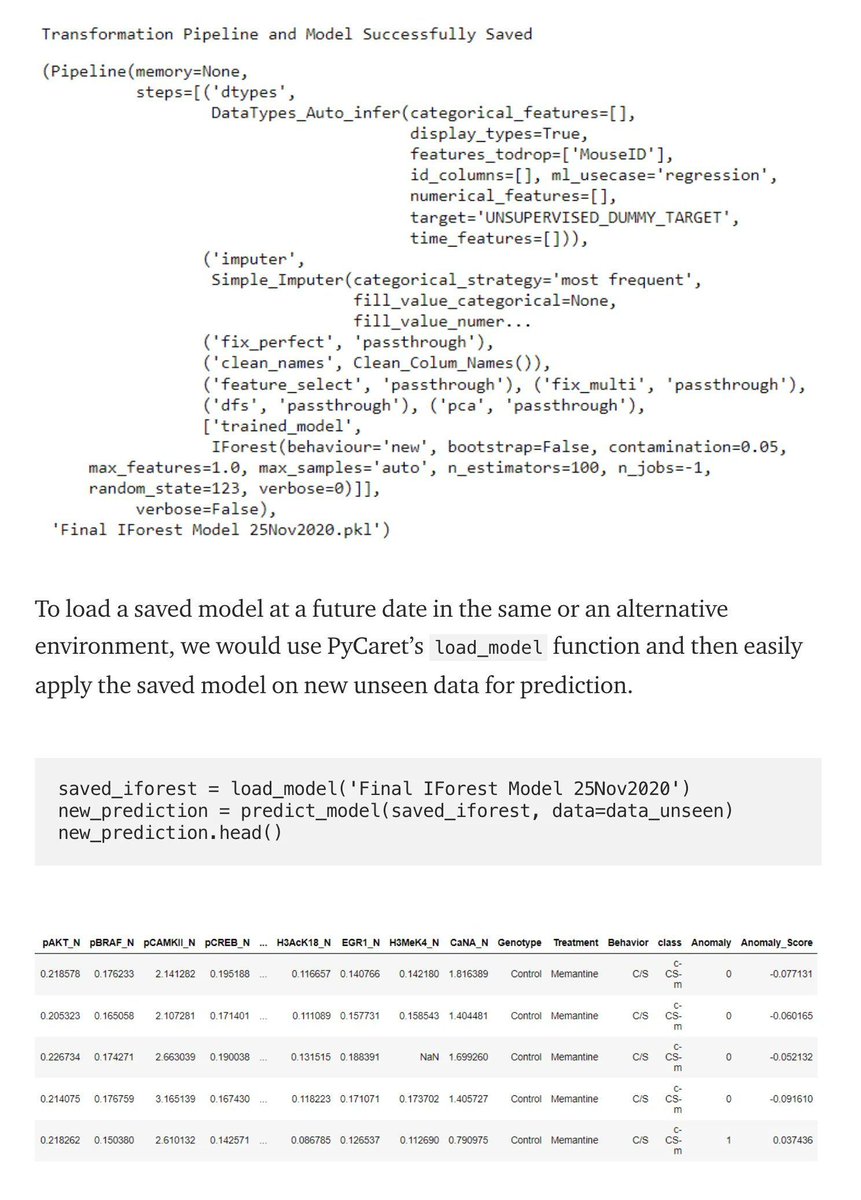
Intro to #AnomalyDetection in #Python with #PyCaret. #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #RStats #TensorFlow #Java #JavaScript #ReactJS #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode geni.us/Python-with-Py…
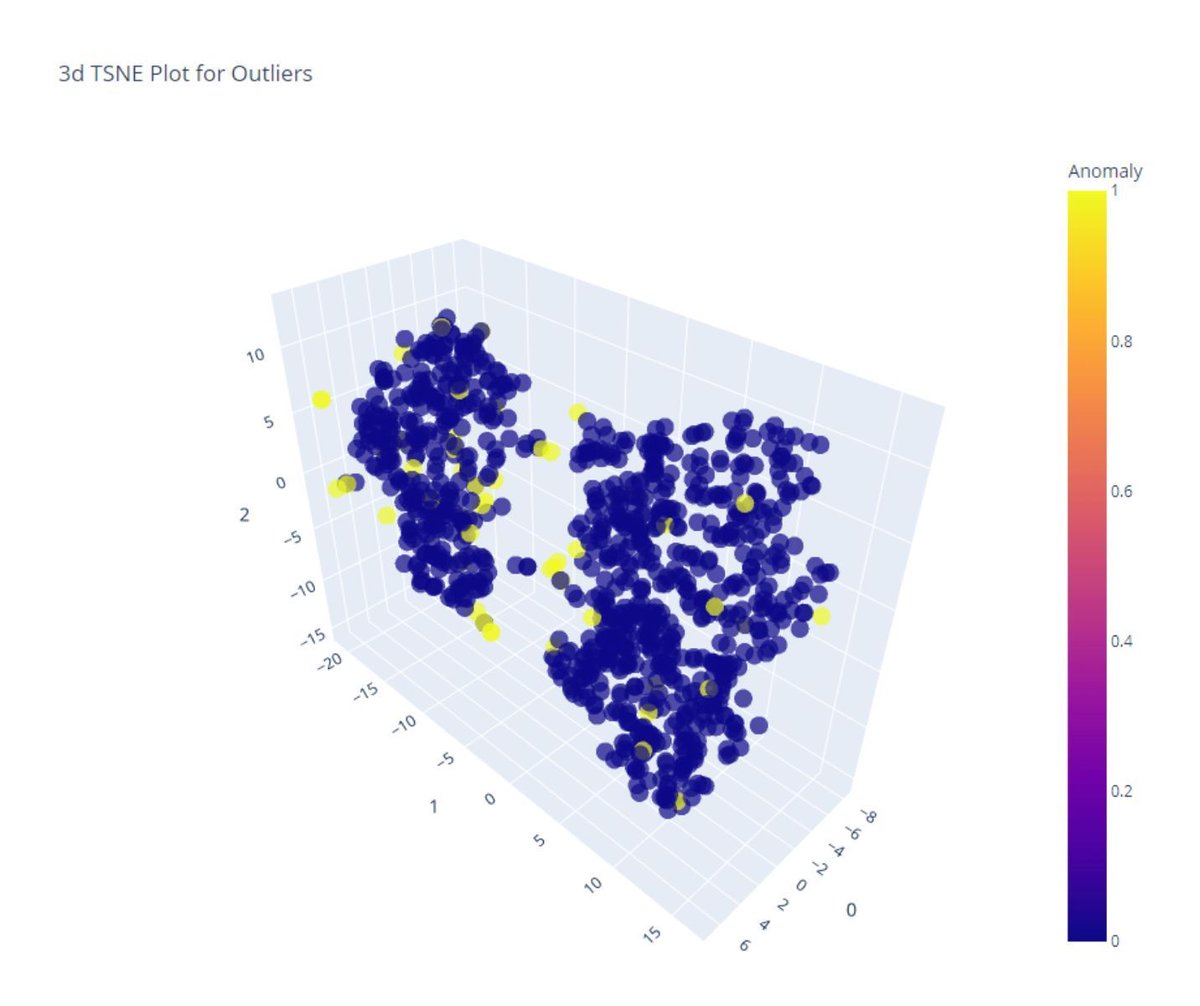
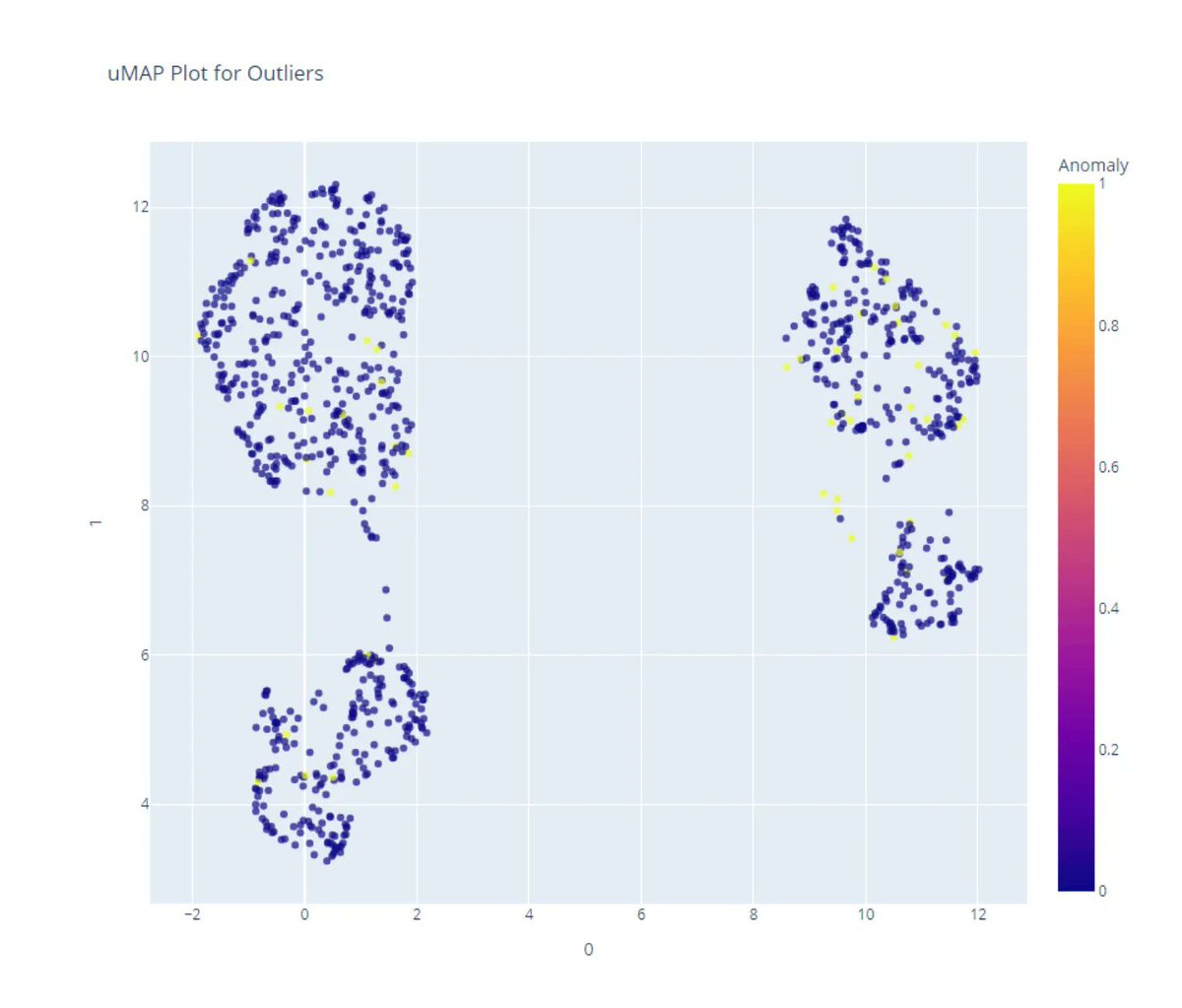

Balancing Narrative Complexity and Actionability in Real-Time Anomaly Detection Using Generative AI 🔗 hubs.li/Q03HXvby0 #AnomalyDetection #ExplainableAI #LLM #GenAI #OperationalAI #RealTimeAI #AppliedAISummit

#AnomalyDetection Using Auto Encoder! #BigData #Analytics #DataScience #AI #MachineLearning #IoT #IIoT #PyTorch #Python #RStats #TensorFlow #Java #ReactJS #GoLang #CloudComputing #Serverless #DataScientist #Linux #Programming #Coding #100DaysofCode geni.us/ADAE-Encoders


Threats aren’t always loud. Sometimes they’re subtle. Discover how anomaly detection gives security teams new eyes in this week’s Unlocked ⤵️ 🔗 unlocked.everykey.com/p/anomaly-dete… #Cybersecurity #AnomalyDetection #InfoSec #Everykey

CMS Unveils AI Algorithm to Spot Anomalies at Large Hadron Collider generalknowledge.tech/ai/cms-ai-algo… #anomalydetection #artificialintelligence #CompactMuonSolenoid #dataanalysis #LargeHadronCollider #machinelearning #particlephysics

Oh that takes me back to #clevabit. #AnomalyDetection and daylight savings time. Via @usenix #SREConEu

#AnomalyDetection in #ML is used to identify instances that fall outside the normal range. Learn how it works, different types and examples here: bit.ly/4dqHkT1

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 56.2K posts
- 2. Luka 56.5K posts
- 3. Wemby 22.3K posts
- 4. Marcus Smart 4,376 posts
- 5. #LakeShow 4,566 posts
- 6. Blazers 6,722 posts
- 7. Richard 45K posts
- 8. Ayton 11.1K posts
- 9. Horford 1,602 posts
- 10. Westbrook 8,700 posts
- 11. #RipCity N/A
- 12. #AEWDynamite 19.3K posts
- 13. Podz 2,249 posts
- 14. Champagnie 1,144 posts
- 15. Kuminga 3,135 posts
- 16. #AmphoreusStamp 4,178 posts
- 17. Spencer Knight N/A
- 18. Thunder 31.2K posts
- 19. #Survivor49 3,280 posts
- 20. Deni 5,964 posts