#networksecurity ผลการค้นหา
Network Security today it’s the Core of new network deployments. Watch these Tech tips to discover it #networksecurity #CyberSecurity #ransomwareattack #ransomwaredefense
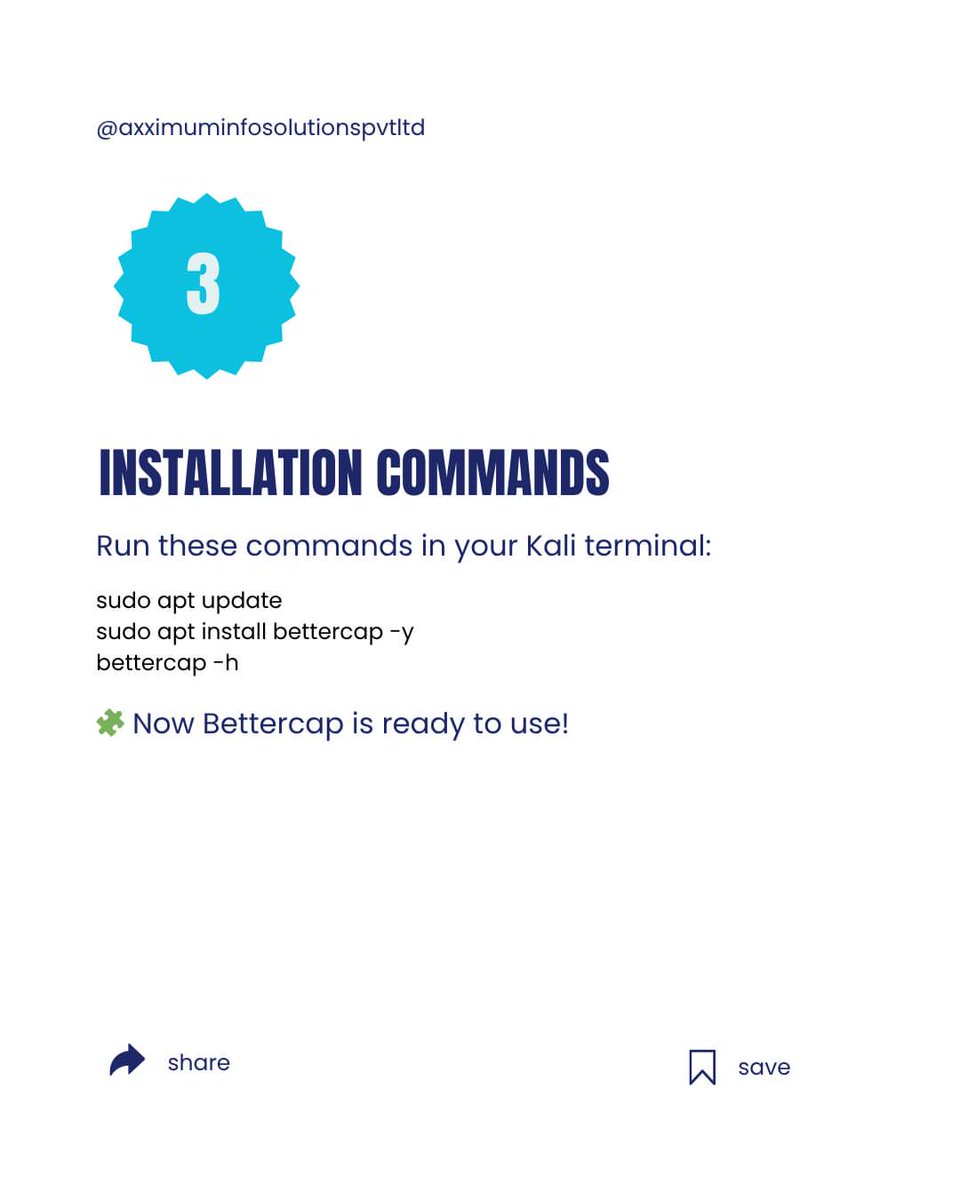
🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection



Protecting what matters most — from defense to digital finance. Path keeps critical systems online, secure, and trusted. 💬 Which sector do you think faces the toughest uptime challenges today? #NetworkSecurity

Today, I completed Module 6 of Networking basics, and I learnt the following. -Network media Types -Component of each media type -Criteria’s to take note of when choosing the media type #NetworkSecurity

Just concluded module 5 of Networking basics . I learnt about: -Communication standards -Communication protocols -Network communication models #Networking

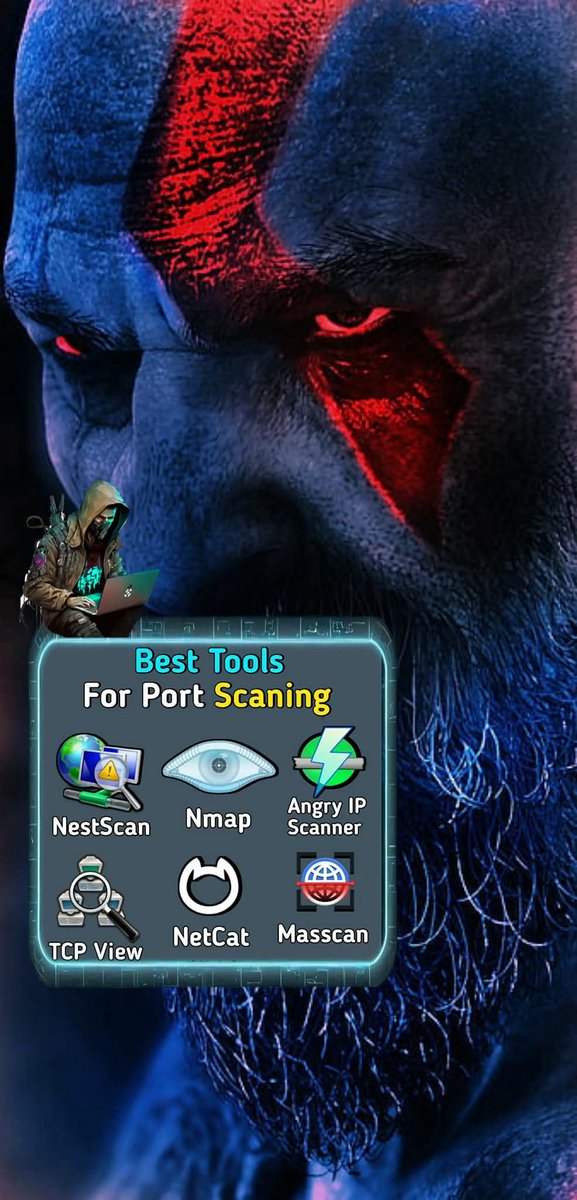
🧠 Best Tools for Port Scanning & Network Analysis 🔍 #NetworkSecurity #PortScanning #CyberSecurity #Nmap #Masscan #Netcat #EthicalUse #NetworkAnalysis #InfoSec #EducationOnly
took the networking module on @CiscoNetAcad where i learnt the fundamentals of networking, mode of signal transmission and also ISP services. @OnijeC @akintunero @cyber_razz #CyberSecurity #NetworkSecurity

Still using #Cisco Firepower firewalls? You'll need to start thinking about what comes next. Here's what you should know about the Hybrid Mesh: hubs.ly/Q03MgNTH0 #CiscoPartner #NetworkSecurity #Firewalls

The Dangerous Misconception About Firewalls Too many organizations think “we have a firewall” means “we are secure.” Firewalls are great but if your users have weak passwords or your IAM is misconfigured, you’re still an open target. #CyberSecurity #NetworkSecurity

🔓 Linux cloud workstations are at risk with Unity-based systems (CVE-2025-59489). Writable paths are gold mines for attackers. Tighten restrictions on cache directories before it’s too late: #hacking #NetworkSecurity #hack bit.ly/3IPwVXH

Dr. Shereen Ismail, Research Scientist: Networking & Cybersecurity at Merit Network, will present two research papers at the @IEEEorg UEMCON 2025 Conference! linkedin.com/feed/update/ur… #Cybersecurity #Research #NetworkSecurity #Innovation #IEEEConference #TexasAM

Cyber threats are getting smarter. Your network should be too. A secure network architecture reduces risks, boosts performance & protects hybrid teams. 🔒 Build a network that’s Zero Trust by design. #CyberSecurity #NetworkSecurity #BetterWorldTechnology…
🕵️ What’s hiding on your network? Untracked devices and unknown software = serious risk. If you can’t see it, you can’t secure it. Start with a full network audit. 👉 Book your free IT Strategy Session: parried.com/get-started #CybersecurityMonth #NetworkSecurity #ITSecurity…



We’re honored to be named a Network Security Market Leader in Cyber Defense Magazine's Top InfoSec Innovator Awards for 2025! 🔗 Read the press release: ow.ly/gXxj50XiZX0 #FireMon #NetworkSecurity

AI cybersecurity detects threats 1000x faster than humans! Trust Procal Technologies to secure your future. #Cybersecurity #AI #NetworkSecurity #TechTrends @bsindia

We’re offering free DDoS detection and traffic visibility for non-profit IXPs to support stronger, more resilient Internet connectivity for everyone. More info: eu1.hubs.ly/H0pgJp60 #DDoS #IXP #NetworkSecurity #TrafficVisibility #fastnetmon

A firewall is an application or software installed on a single computer to protect the computer. This is a host-based firewall. A stand-alone network firewall protects an entire network of computers and the host devices.@ireteeh @Abby_amg #NetworkSecurity #EndpointProtection

What is a Firewall? The invisible bodyguard your system can’t live without. It watches, filters, and fights off hackers while you sleep. Silent, strong, and always on duty. 🔐 #NetworkSecurity #Firewall #RedSwitches
Why FCSS_NST_SE-7.6 Is Transforming Fortinet Career Landscape The FCSS_NST_SE-7.6 certification redefines what it means to be a Fortinet support engineer. Read the full story- medium.com/@certifyinside… #FortinetCertification #NetworkSecurity #FortinetProfessionals #Cybersecurity
🔒 Secure Your Network. Strengthen Your Business. 💼 #ElysianCommunication #NetworkSecurity #CyberProtection #DataSafety #BusinessSecurity #FirewallProtection #SmartSecurity #24x7Monitoring #SecureYourBusiness #ITSecurity #CyberSafeBusiness #TechSolutions #CyberSecurity

#NetworkSecurity #Switches #Routers #FrolgateTechnology #SecureConnectivity #Networking #ITInfrastructure
10 Essential Tools for Network Security bit.ly/3WCHOzk #NetworkSecurity #CyberDefense #InfoSec #CyberProtection #SecurityTools #ThreatDetection #DataSecurity #ITSecurity #VulnerabilityManagement #TechUnity

🔥 Riesgo #2 – Puertos abiertos “porque sí” SSH, RPC, SMB... servicios que ni sabés que corren y sin el hardening adecuado. Si navegás desde esa VM o peor aun EN LOCAL, esos puertos quedan expuestos. Y en Wi-Fi público sos un cartel que dice “atacame”. #InfoSec #NetworkSecurity…
Is your network still manual? AI network intelligence enhances speed, security, and optimization. Read our newsletter for insights on its importance for success: hubs.la/Q03RTVF70 #AITrends #NetworkSecurity #OperationalPerformance #ITAutomation

Protecting what matters most — from defense to digital finance. Path keeps critical systems online, secure, and trusted. 💬 Which sector do you think faces the toughest uptime challenges today? #NetworkSecurity

Mix of UDP attack types with a total capacity of 35.45 Gbps and 5.37 Mpps, including heavy DNS amplification, were smoothly filtered by our PYRUS DDoS protection appliance. Customer stayed online and unaffected ✅ #DDoS #CyberSecurity #NetworkSecurity

🛠️ Bettercap — Network Recon & MITM Framework Powerful toolkit for network monitoring, protocol inspection, and authorized MITM-style testing — ideal for defenders to validate detections and for learning how attackers operate. #Bettercap #NetworkSecurity #MITMDetection




The Dangerous Misconception About Firewalls Too many organizations think “we have a firewall” means “we are secure.” Firewalls are great but if your users have weak passwords or your IAM is misconfigured, you’re still an open target. #CyberSecurity #NetworkSecurity

🕵️ What’s hiding on your network? Untracked devices and unknown software = serious risk. If you can’t see it, you can’t secure it. Start with a full network audit. 👉 Book your free IT Strategy Session: parried.com/get-started #CybersecurityMonth #NetworkSecurity #ITSecurity…



Still using #Cisco Firepower firewalls? You'll need to start thinking about what comes next. Here's what you should know about the Hybrid Mesh: hubs.ly/Q03MgNTH0 #CiscoPartner #NetworkSecurity #Firewalls

SpaceX launches 51 @Starlink satellites from Vandenberg expanding low Earth orbit broadband improving global connectivity scaling next-generation internet #networksecurity for commercial & strategic applications. #SpaceX #Starlink #Internetheld #LEO #SpaceExploration #aerodrome

Can I DIY SSL on Debian without a chaos monkey throwing bananas at my server? 🐒🍌 Source: devhubby.com/thread/how-to-… #ITSecurity #NetworkSecurity #Encryption #TechTutorial #webserver #web

Today, I completed Module 6 of Networking basics, and I learnt the following. -Network media Types -Component of each media type -Criteria’s to take note of when choosing the media type #NetworkSecurity

Just concluded module 5 of Networking basics . I learnt about: -Communication standards -Communication protocols -Network communication models #Networking

AI cybersecurity detects threats 1000x faster than humans! Trust Procal Technologies to secure your future. #Cybersecurity #AI #NetworkSecurity #TechTrends @bsindia

#CyberSec #KaliLinux #NetworkSecurity #WebSecurity #HackingTools #CyberAwareness #RedTeam #SecureCoding #Pentester

Legal & General establishes digital infrastructure investment fund, targeting #datacenters, fiber #networksecurity & #Cloud assets to drive connectivity, digital economy growth & institutional investor returns. #DataCenter #CloudComputing #SmartInvesting #DigitalTransformation

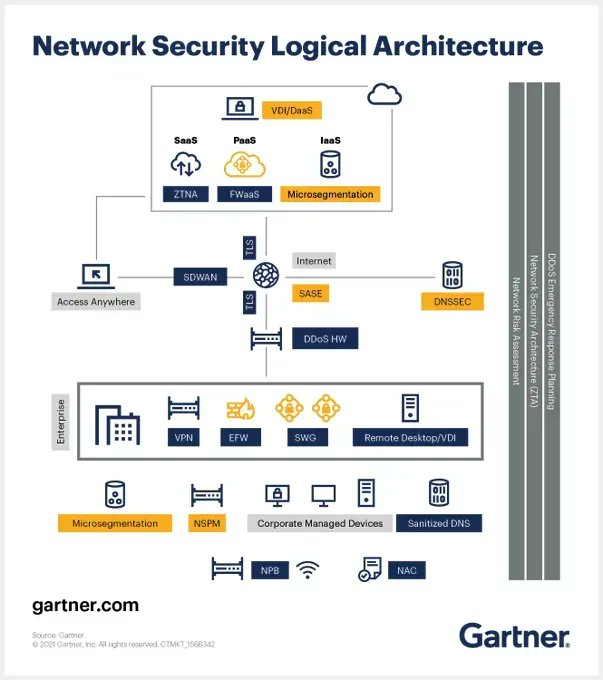
Changes in network architecture require new approaches to network security that combine reliable stalwarts with new technologies. Source @Gartner_inc Link gtnr.it/3nnDxyV RT @antgrasso #NetworkSecurity #CloudComputing #EdgeComputing
Smith has named Mike Mercado Chief Information Officer! In this role, Mike will lead our #IT department in enhancing our advanced #NetworkSecurity and developing cutting-edge technology initiatives. Read more: smth.bz/rwj #IntelligentDistribution

took the networking module on @CiscoNetAcad where i learnt the fundamentals of networking, mode of signal transmission and also ISP services. @OnijeC @akintunero @cyber_razz #CyberSecurity #NetworkSecurity

🧠 Best Tools for Port Scanning & Network Analysis 🔍 #NetworkSecurity #PortScanning #CyberSecurity #Nmap #Masscan #Netcat #EthicalUse #NetworkAnalysis #InfoSec #EducationOnly

Even the best firewalls cannot protect against direct port misuse. Network port blocking devices provide a physical barrier that works alongside software security for complete protection. #NetworkSecurity #PortProtection #CyberDefense #DataSecurity #ITSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Lakers 78.6K posts
- 2. #Talus_Labs N/A
- 3. Good Thursday 20.2K posts
- 4. Luka 69.9K posts
- 5. Wemby 27K posts
- 6. Marcus Smart 6,196 posts
- 7. #LakeShow 5,722 posts
- 8. #AmphoreusStamp 7,225 posts
- 9. Blazers 8,892 posts
- 10. Russ 11K posts
- 11. Ayton 16.5K posts
- 12. Will Richard 6,613 posts
- 13. #RipCity N/A
- 14. #dispatch 64.8K posts
- 15. Unplanned 5,709 posts
- 16. Podz 2,433 posts
- 17. Nico Harrison 1,999 posts
- 18. Klay 8,567 posts
- 19. Shroud 5,694 posts
- 20. Deni 6,295 posts































































