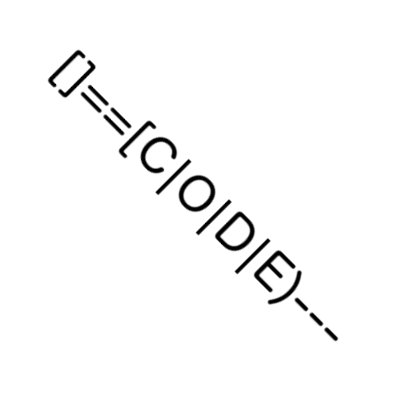
#codeinjection 搜尋結果
I admire several security companies, @TrendMicro one of them. Happy to help with the safety of your products. #bugbounty #codeinjection
Code Injection: Windows Taskbar x0r19x91.gitlab.io/post/code-inje… #Pentesting #ReverseEngineering #CodeInjection #Windows #CyberSecurity #Infosec




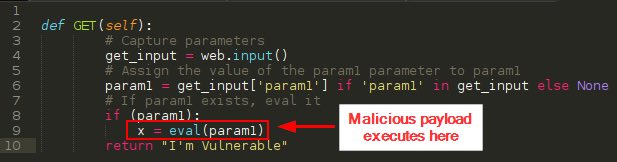
Userland API Monitoring and Code Injection Detection 0x00sec.org/t/userland-api… #Pentesting #API #CodeInjection #CyberSecurity #Infosec



Userland API Monitoring and Code Injection Detection goo.gl/YSWAHh #CodeInjection #ExploitDev #Infosec

Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection. github.com/LordNoteworthy… #Malware #CodeInjection #Debugging #CyberSecurity #Infosec

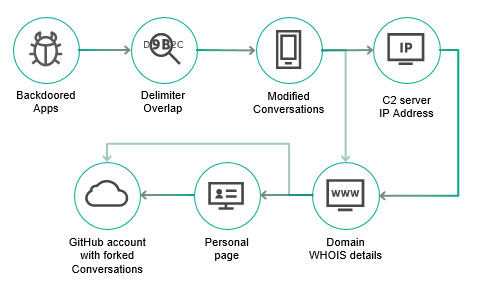
#Backdoor #CodeInjection #InstantMessengers #MobileMalware #TargetedAttacks #Trojan #VulnerabilitiesAndExploits #CyberSecurity ViceLeaker Operation: mobile espionage targeting #MiddleEast securelist.com/fanning-the-fl…
New notes on code injection via process hollowing and image Windows PE image relocations ired.team/offensive-secu… #processhollowing #codeinjection #evasion

Email tracing script appearing in all pages opened in Google Chrome stackoverflow.com/questions/6664… #googlechrome #codeinjection #javascript

Turns out, hackers love a good meme as much as the rest of us. Find out the meme reference we've found in nearly 10,000 WordPress attacks in this week's Sucuri Sync-Up! 📖 Read the blog: sucur.it/3ePOJOW --- #codecomments #codeinjection #malware #cybersecurity
Script-based attacks, dual-use tools and #codeinjection techniques are often hard to predict and prevent. Watch this demonstration, to see how we are able to prevent a #ransomware based on a #fileless attack vector >> hubs.ly/H0gxSp50
Dirty Vanity is a new #codeinjection technique that abuses forking, a lesser-known mechanism that exists in Win OS. In this post, Deep Instinct's security researcher, Eliran Nissan, explores forking and its legitimate use: deepinstinct.com/blog/dirty-van… #EDR #DeepLearning

Microsoft warns that attackers are deploying malware in ViewState code injection attacks using static ASP. NET machine keys found online. #codeinjection #CyberAlerts bleepingcomputer.com/news/security/…
Code injection on Android without ptrace #CodeInjection #Android #Rust #Shellcode #SELinux erfur.dev/blog/dev/code-…
erfur.dev
Code injection on Android without ptrace
Code injection on Android without ptrace
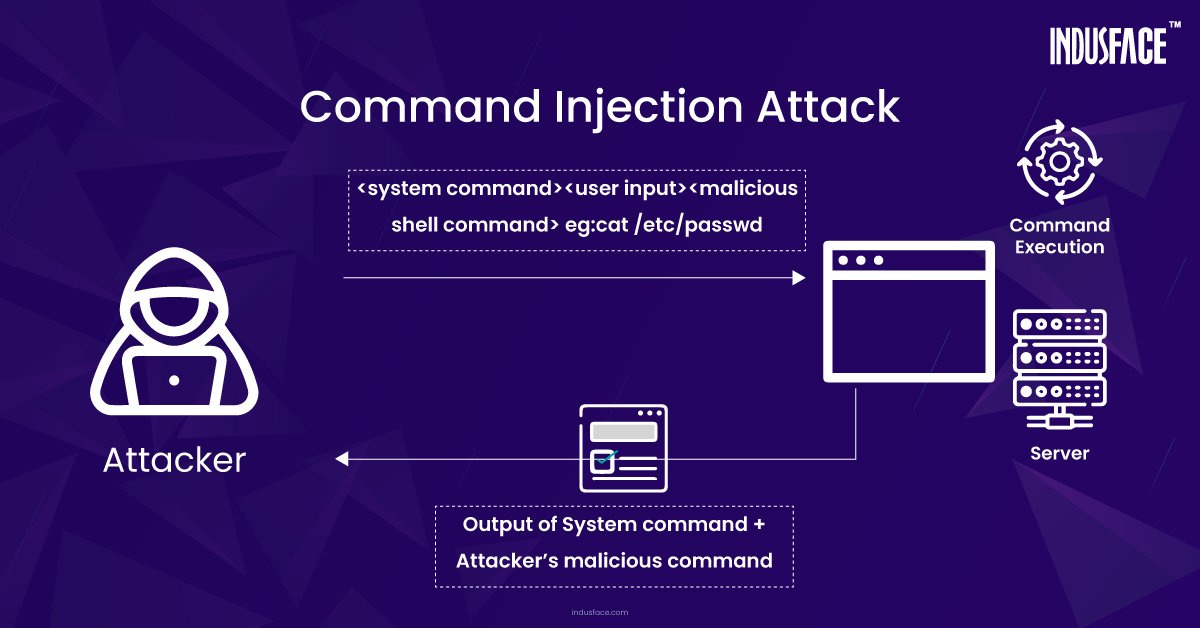
💉 Learn about #commandinjection attack and how it works by visiting the link in the thread. #commandinjectionattack #codeinjection #injectionattacks #owasp #applicationsecurity #cyberattacks #databreaches #vulnerabilities #waap #waf #apptrana #indusface
Our March @secthings @Meetup with Dewitt Seward @siliconlabs on securing embedded devices from #codeinjection #InternetOfThings thanks again to @WPI for hosting at their #seaport location!

In 2019 we discovered hackers using a code injection method via a customized Mach-O loader. Rated as one of the "Coolest Hacks of 2019" our VP of Research, Shimon Oren explains why it's so easy to use via @DarkReading. hubs.ly/H0mCskD0 #deeplearning #codeinjection

🚨 Threat Spotlight: Code Injection Without protection, attackers can inject malicious code into your app at runtime, stealing data or hijacking functionality. AppShield blocks this automatically. #KnowYourRisks #CodeInjection
🔄5/11: AgentHopper spreads using prompt injection payloads in code repositories, getting processed by other agents to continue the cycle. #CodeInjection
SAP’s August 2025 Patch Tuesday fixes 26 flaws, including 4 critical code injection vulnerabilities in SAP S/4HANA and Landscape Transformation, risking full system compromise via privilege escalation. #SAPSecurity #CodeInjection #Germany ift.tt/mnL94fF
SAP’s August 2025 Patch Tuesday fixes 15 vulnerabilities in S/4HANA and NetWeaver, including critical code injection flaws CVE-2025-42950 and CVE-2025-42957 enabling remote code execution. #SAPPatches #CodeInjection #Germany ift.tt/gIHOPXL
🚨 CRITICAL: Easy Stripe code injection flaw (CVSS 10) risks remote takeover! No patch yet—mitigate now. 🛡️ Details: radar.offseq.com/threat/cve-202… #OffSeq #CodeInjection #PaymentSecurity
#Vulnerability #codeinjection Kibana Code Injection Vulnerability: Prototype Pollution Threat (CVE-2024-12556) securityonline.info/kibana-code-in…
securityonline.info
Kibana Code Injection Vulnerability: Prototype Pollution Threat (CVE-2024-12556)
A vulnerability (CVE-2024-12556) in Kibana allows code injection via prototype pollution, file upload, and path traversal. Upgrade to the latest version or disable the integration assistant to...
Critical #CodeInjection flaw (CVE-2025-49013) in WilderForge GitHub Actions lets attackers run arbitrary code. Devs must act now! Details: radar.offseq.com/threat/cve-202… #OffSeq #CyberSecurity #GitHub #CVE

💥New 'Rules File Backdoor' Attack Lets Hackers Inject Malicious Code via AI Code Editors💥 thehackernews.com/2025/03/new-ru… #CyberSecurity #AIThreats #CodeInjection #Malware #SoftwareSecurity #SupplyChainAttack #BackdoorAttack #CyberAttack
💥New 'Rules File Backdoor' Attack Lets Hackers Inject Malicious Code via AI Code Editors💥 thehackernews.com/2025/03/new-ru… #CyberSecurity #AIThreats #CodeInjection #Malware #SoftwareSecurity #SupplyChainAttack #BackdoorAttack #CyberAttack
Code Injection: Windows Taskbar x0r19x91.gitlab.io/post/code-inje… #Pentesting #ReverseEngineering #CodeInjection #Windows #CyberSecurity #Infosec




I admire several security companies, @TrendMicro one of them. Happy to help with the safety of your products. #bugbounty #codeinjection

Userland API Monitoring and Code Injection Detection 0x00sec.org/t/userland-api… #Pentesting #API #CodeInjection #CyberSecurity #Infosec




Userland API Monitoring and Code Injection Detection goo.gl/YSWAHh #CodeInjection #ExploitDev #Infosec

Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection. github.com/LordNoteworthy… #Malware #CodeInjection #Debugging #CyberSecurity #Infosec

Email tracing script appearing in all pages opened in Google Chrome stackoverflow.com/questions/6664… #googlechrome #codeinjection #javascript

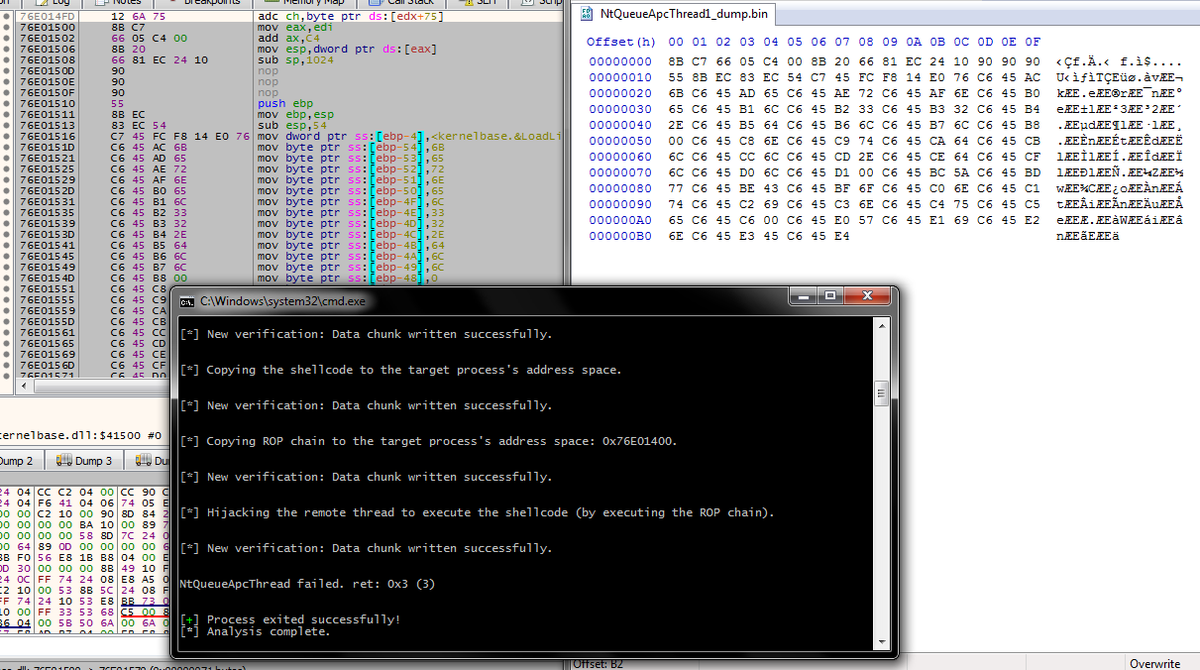
Using Syscalls to Inject Shellcode on Windows: solomonsklash.io/syscalls-for-s… #codeinjection #shellcode #windows #security
#Backdoor #CodeInjection #InstantMessengers #MobileMalware #TargetedAttacks #Trojan #VulnerabilitiesAndExploits #CyberSecurity ViceLeaker Operation: mobile espionage targeting #MiddleEast securelist.com/fanning-the-fl…

New notes on code injection via process hollowing and image Windows PE image relocations ired.team/offensive-secu… #processhollowing #codeinjection #evasion

WIll HTMLEncode stop Javascript Code Injection? stackoverflow.com/questions/6168… #htmlencode #javascript #codeinjection

#CodeInjection #DataLeaks #Malware #SQLInjection #VulnerabilitiesAndExploits #VulnerabilityStatistics #Vulnerability #WebsiteHacks #CyberAttack #CyberSecurity The cybercrime ecosystem: attacking blogs. securelist.com/the-cybercrime…

#Hackers Found Using A New #CodeInjection Technique to Evade Detection - buff.ly/2IOxImX #security #earlybird #cybersecurity #infosec

React Native Apps Secure From this attack stackoverflow.com/questions/6676… #hsts #codeinjection #reactnative

Something went wrong.
Something went wrong.
United States Trends
- 1. Marshawn Kneeland 26.7K posts
- 2. Nancy Pelosi 32.7K posts
- 3. #MichaelMovie 42.4K posts
- 4. #NO1ShinesLikeHongjoong 30.3K posts
- 5. #영원한_넘버원캡틴쭝_생일 29.6K posts
- 6. ESPN Bet 2,535 posts
- 7. Baxcalibur 4,233 posts
- 8. Madam Speaker 1,480 posts
- 9. Chimecho 6,197 posts
- 10. Gremlins 3 3,406 posts
- 11. Joe Dante N/A
- 12. #thursdayvibes 3,140 posts
- 13. Jaafar 12.7K posts
- 14. Chris Columbus 3,038 posts
- 15. #LosdeSiemprePorelNO N/A
- 16. Diantha 1,798 posts
- 17. Rest in Peace 19.6K posts
- 18. Good Thursday 37.4K posts
- 19. Korrina 5,160 posts
- 20. VOTAR NO 27.7K posts