#react2shell search results
Plenty of post-exploitation analysis here by @HuntressLabs. - Crypto-miners - Linux backdoors - Reverse proxy tunnels - Go-based post-exploitation implants This goes to show the ease of exploitation and that numerous groups are/have taken advantage. #react2shell…
gracias mark zukember por meterme un rce <#<3 #react2shell #zukembergijoputa #zimbawelohizo #paguenloatrasado o #dinamitolavps
Critical CVE-2025-55182 (React2Shell) in React Server Components allows unauthenticated remote code execution via a single HTTP request. Exploited by China-linked groups, upgrades and runtime protections recommended. #React2Shell #NodeJS #China ift.tt/HV7Q6Ur
Super hyped to share that @HuntressLabs published a Rapid Response blog on the recent #React2Shell post-exploitations observed. We discovered and analyzed a few payloads that were named #PeerBlight, #CowTunnel and #ZinFoq. We also observed a variant of #Kaiji malware. 3 Modelo's…
If you think about it the #React2Shell attacks now are just a bunch of script kiddies running an automated PoC scripts, yes it is a threat but the real threat is the groups that already been using this vulnerability since forever, go back and hunt them in your old SIEM logs 👀!
New story is out, as usual free link is at the top of the story #React2Shell #BugBounty #bugbountytips blog.fadyothman.com/react2shell-cv…
Es alarmante la magnitud de activos expuestos en México. Solo en el primer mes de análisis identificamos 32,593 activos potencialmente vulnerables, pertenecientes (aparentemente) a empresas privadas y entidades gubernamentales. La mayoría están vinculados al vector #React2Shell,…
React2Shell (CVE-2025-55182) is a critical vulnerability in React Server Components allowing unauthenticated remote code execution via crafted HTTP POST. Over 4,100 attacks observed within 2 hours. #React2Shell #RemoteCodeExecution #USA ift.tt/yJpGZs5
hendryadrian.com
React2Shell: Remote Code Execution Vulnerability (CVE-2025-55182)
React2Shell (CVE-2025-55182) is a critical RSC vulnerability that enables unauthenticated remote code execution on affected React servers via a crafted HTTP POST with malicious multipart/form-data....
🚨 Execute arbitrary code on the server and even compromise the underlying infrastructure. This is what an attacker can do by exploiting CVE-2025-55182. How can the exploitation of #React2Shell be prevented, detected, and mitigated? 👇🏻 tarlogic.com/blog/cve-2025-…
🚨 Ejecutar código arbitrario en el servidor y llegar a comprometer la infraestructura subyacente. Esto es lo que puede hacer un atacante que explote la CVE-2025-55182. ¿Cómo se puede prevenir, detectar y mitigar la explotación de #React2Shell? 👇🏻 tarlogic.com/es/blog/cve-20…
North Korean hackers linked to Lazarus are exploiting React2Shell (CVE-2025-55182) in React and Next.js frameworks using EtherRAT malware and Ethereum smart contracts to steal crypto and deploy implants. #NorthKorea #React2Shell #EtherRAT ift.tt/VA9d1uP
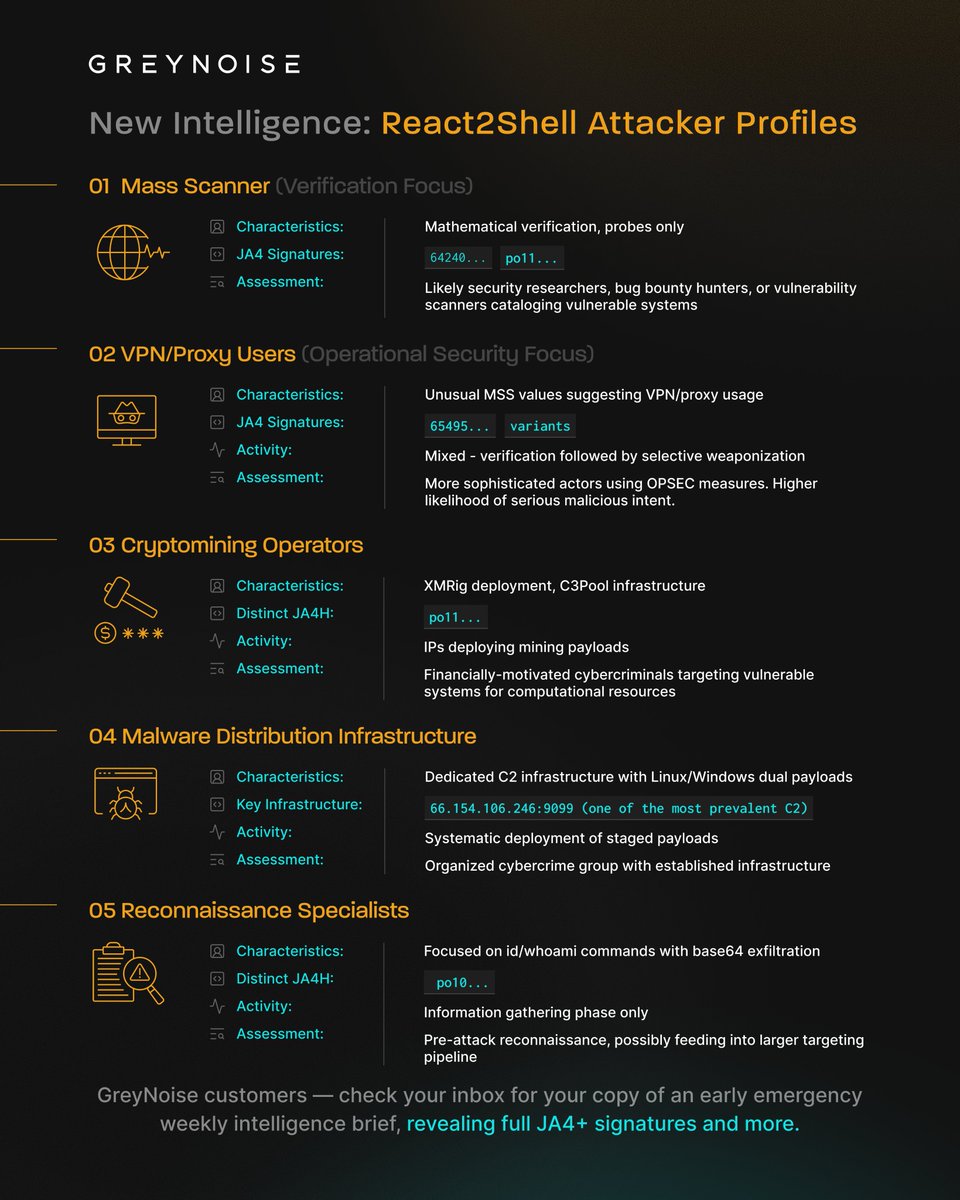
👀 React2Shell attacker profiles fresh from GreyNoise telemetry: info.greynoise.io/hubfs/PDFs-Sal…, don't miss the latest contribution from GreyNoise Labs on React2Shell: labs.greynoise.io/grimoire/2025-… #React2Shell #Nextjs #CVE202555182 #CVE #GreyNoise
🇰🇵🐀 north korean hackers deploy etherrat via react2shell A new implant, EtherRAT, leverages five Linux persistence methods and Ethereum smart contracts after exploiting the React2Shell flaw. #react2shell #northkorea #malware #etherrat #cyberattack

Something went wrong.
Something went wrong.
United States Trends
- 1. #BTCCBestCEX 1,872 posts
- 2. Slept 20.4K posts
- 3. Mets 37.6K posts
- 4. Markstrom N/A
- 5. Dodgers 44.1K posts
- 6. Eileen Higgins 7,633 posts
- 7. Maresca 39.8K posts
- 8. White Sox 3,718 posts
- 9. Villanova 1,605 posts
- 10. Clemson 7,364 posts
- 11. Kentucky State University 3,464 posts
- 12. Diaz 80.3K posts
- 13. Garrison 1,617 posts
- 14. #ShootingStar N/A
- 15. 2026 MLB Draft 2,810 posts
- 16. Stearns 12.4K posts
- 17. Roch Cholowsky N/A
- 18. GeForce Season 4,521 posts
- 19. #NBACup N/A
- 20. Eric Collins N/A