#unprotectproject search results
#100DaysOfYara Day 15: Wrote a rule for notorious open source crypter malware LimeCrypter. Detecting the RunPE code based on hardcoded constants. Also contributing it to #UnprotectProject github.com/cod3nym/detect…

👽 A new technique, named "FuncIn", has been integrated to #UnprotectProject, showcasing a sophisticated evasion technique with a working open-source demo. In short, FuncIn employs a payload staging strategy, diverging from the conventional method where all malicious…

#100DaysOfYara Day 12: Making a rule for @dr4k0nia NixImports malware loader. Built for evasion without any user strings and dynamically resolving managed functions based on hashes. Also contributing to #UnprotectProject github.com/cod3nym/detect… Checkout the authors blog post…

#100DaysofYARA Day 4: Today we are detecting #ConfuserEx binaries without any watermarks. Messing a bit with hex strings and contributing to #UnprotectProject I wrote a blog post explaining the process behind the creation of this rule: cod3nym.github.io/Detecting-Stea… Find the Yara rule…


#100DaysofYara Day 9: Excited to get this one in. Today we will cover the rules for the latest #PureCrypter's initial and core payloads. PureCrypter is a .NET crypter/loader, which has been used by many RATs and stealers. It also means another contribution to #UnprotectProject ,…


#100DaysOfYara Day 9: Another day another .NET obfuscator #Yara rule. Today I am detecting .NET Reactor and their unique naming conventions. Also contributing to #UnprotectProject github.com/cod3nym/detect… All my obfuscator related rules available for malcat or any other Yara…


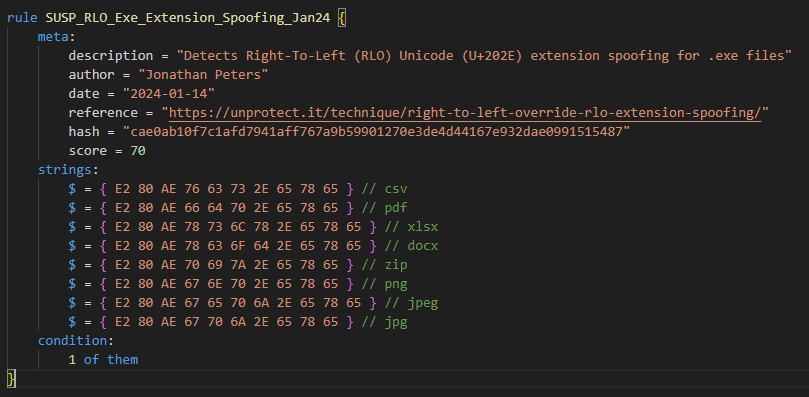
#100DaysOfYara Day 14: Another rule for a #UnprotectProject technique. This rule targets the Right-To-Left (RLO) extension spoofing technique.This spoofing also works on VT but only in the GUI, the URL shows the actual file %E2%80%AEfdp.exe E2 80 AE are the bytes encoding the…


🤓During the #100DaysOfYara, if you are not sure how to contribute, you can always contribute to the #UnprotectProject! cc: @DarkCoderSc

#100DaysOfYara Late Day 13: Wrote a Yara rule for EvasionUsingSyscall from #UnprotectProject Using a hex string to detect the emitted assembly instructions. From the POC code. github.com/cod3nym/detect… unprotect.it/technique/evas…

#100DaysofYara Day 10: Was scrolling through #UnprotectProject for some Yara rule ideas... Today, I picked the rule that detects Base64 encoding in native binaries. Contributing the rule to #UnprotectProject, of course, cc @fr0gger_ 💜 github.com/RussianPanda95…

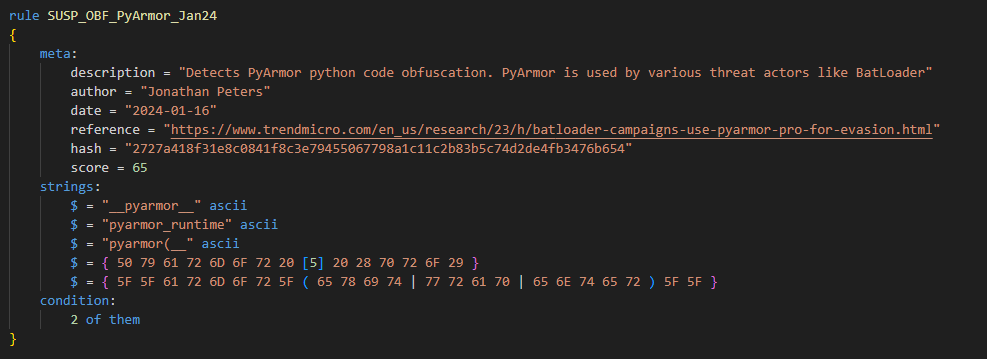
#100DaysOfYara Day 16: Today I wrote a rule for the PyArmor python obfuscator. A simple rule checking for common strings used by the obfuscators runtime. Also contributing this to #UnprotectProject github.com/cod3nym/detect…
#100DaysofYara Day 7 + 8: Cheating a bit with the days. Today I target ConfuserEx again and and contribute to #UnprotectProject Detecting ConfuserEx compression packer github.com/cod3nym/detect… But I got a bonus for you: How I come up with these rules a mini write up below:


Just a little teaser ( non definitive UI and exhaustive features ) , coming very soon 😎 #UnprotectProject #Malware #InfoSec #DFIR cf: @fr0gger_

Love investigating malware? You can preorder and get early access to "Evasive Malware: Understanding Deceptive and Self-Defending Threats" - use coupon code "EVASIVE25" to get 25% off and send some ❤️ to the #UnprotectProject (@fr0gger_ /@DarkCoderSc) securityliterate.com/evasive-malwar…

📢Big news! We recently did a major update on the #UnprotectProject; we are now supporting evasion techniques on Windows, Linux, and macOS. Still a WIP but Pull Requests are welcome! 🤓 cc: @DarkCoderSc #malware #evasion

Huge thank you to @fr0gger_ and #UnprotectProject for the awesome swag, was a lot of fun to contribute to the project so far. If you're interested in detection rules and malware techniques make sure to check out unprotect.it

⭐ New entry in the #UnprotectProject in Network Evasion with SMTP Exfiltration. Including code snippet and I also added a yara rule! Contribution by @tasdir_x cc: @DarkCoderSc #100daysofyara unprotect.it/technique/exfi…

We have great candidates for the #UnprotectProject Linux edition @DarkCoderSc 🧐 Great writeup on the latest Ivanti zero-day 👇 cloud.google.com/blog/topics/th…

Thank you so much for the Unprotect Ambassador Coin 🪙 and the badass sticker 👽 @fr0gger_ ❤️🥹 It is a great pleasure to contribute to your project at #UnprotectProject

Check out this new entry in the #UnprotectProject by my friend @DarkCoderSc! 😎 *Indirect Memory Writing* for example an attacker calls standard Windows APIs that accept an output pointer. You can point that pointer at executable memory. The attacker can then build a payload…
Has anyone ever seen or used this evasion technique? I have been using it for many years and still find it effective (particularly with macro's), so I was surprised to see it continue to work so I decided to document it on Unprotect : unprotect.it/technique/indi… Feedback appreciated!
That's a good one, it could be added to the #unprotectProject unprotect.it
Nice compilation of search evasion techniques #UnprotectProject #Home #TechniqueList #CodeSnippets #DetectionRules unprotect.it
🤓 We have just added couple of Linux anti-forensic techniques to the #UnprotectProject, based on the latest campaign observed by Mandiant that exploit two vulnerabilities, CVE-2025-0282 and CVE-2025-0283, on Ivanti Connect Secure! cf: @DarkCoderSc 👇 unprotect.it/category/anti-…

🧐 The abuse of the Apple XProtect encryption algo from the Banshee malware is very interesting, so I added it in #UnprotectProject! MacOS evasion techniques are still early in the project, but there are plenty of techniques to be added! @DarkCoderSc ➡️unprotect.it/technique/xpro…

⭐ New entry in the #UnprotectProject in Network Evasion with SMTP Exfiltration. Including code snippet and I also added a yara rule! Contribution by @tasdir_x cc: @DarkCoderSc #100daysofyara unprotect.it/technique/exfi…

We have great candidates for the #UnprotectProject Linux edition @DarkCoderSc 🧐 Great writeup on the latest Ivanti zero-day 👇 cloud.google.com/blog/topics/th…

🤓During the #100DaysOfYara, if you are not sure how to contribute, you can always contribute to the #UnprotectProject! cc: @DarkCoderSc

🎨 November: I presented at @BSidesGC, @HCKSYD and @BSidesMelbourne. We launched the #UnprotectProject Scanner with @DarkCoderSc and joined @CyberSecRicki for a career cybersecurity webinar. I also published a blog on building a GenAI CTI assistant. unprotect.it/scan/
You now have the option to keep the uploaded sample private to you in the #UnprotectProject cf: @darkcodersc #malware #infosec 👇 unprotect.it/scan/

📢 We added more functionalities to the #UnprotectProject Scanner! 👽 You can now look for additional information as well as the PEID signature! Check this out! 👇 cc: @DarkCoderSc #malware unprotect.it/scan/

Just a little teaser ( non definitive UI and exhaustive features ) , coming very soon 😎 #UnprotectProject #Malware #InfoSec #DFIR cf: @fr0gger_

📢Big news! We recently did a major update on the #UnprotectProject; we are now supporting evasion techniques on Windows, Linux, and macOS. Still a WIP but Pull Requests are welcome! 🤓 cc: @DarkCoderSc #malware #evasion

Awesome blog, you know it is an entry for the #UnprotectProject 🤩🤩🤩
🤓 We recently added new entries to the #UnprotectProject! Here's a small thread on the latest additions 👇 cc: @darckcodersc #malware #evasion
Thanks @fr0gger_! If you order Evasive Malware from the #UnprotectProject website, you get 25% off and also support the project! 😎
Added 2 YARA sigs to #UnprotectProject on - Al-Khaser Write_Watch anti-debug technique - WinDef AV Emulator goat-files as evasion technique @fr0gger_ @DarkCoderSc github.com/fr0gger/Unprot…
github.com
Al-khaser_writewatch and WinDefAVEmu_Goatfiles techniques by albertzsigovits · Pull Request #69 ·...
2 more evasion techniques covered via YARA rules FYI @fr0gger
Got a gift in the mail from @fr0gger_ and @DarkCoderSc! Thanks guys! Happy to support #UnprotectProject and keep up the great work - it’s an amazing project 😎
#100DaysOfYara Day 15: Wrote a rule for notorious open source crypter malware LimeCrypter. Detecting the RunPE code based on hardcoded constants. Also contributing it to #UnprotectProject github.com/cod3nym/detect…

#100DaysofYara Day 9: Excited to get this one in. Today we will cover the rules for the latest #PureCrypter's initial and core payloads. PureCrypter is a .NET crypter/loader, which has been used by many RATs and stealers. It also means another contribution to #UnprotectProject ,…


👽 A new technique, named "FuncIn", has been integrated to #UnprotectProject, showcasing a sophisticated evasion technique with a working open-source demo. In short, FuncIn employs a payload staging strategy, diverging from the conventional method where all malicious…

Just a little teaser ( non definitive UI and exhaustive features ) , coming very soon 😎 #UnprotectProject #Malware #InfoSec #DFIR cf: @fr0gger_

Love investigating malware? You can preorder and get early access to "Evasive Malware: Understanding Deceptive and Self-Defending Threats" - use coupon code "EVASIVE25" to get 25% off and send some ❤️ to the #UnprotectProject (@fr0gger_ /@DarkCoderSc) securityliterate.com/evasive-malwar…

I did a thing! I created my first GPT named "MagicUnprotect". This GPT is connected to the #UnprotectProject knowledgebase. You can ask anything related to evasion techniques! I'll share it when the test is done 🤓 #infosec #malware @DarkCoderSc



#100DaysofYARA Day 4: Today we are detecting #ConfuserEx binaries without any watermarks. Messing a bit with hex strings and contributing to #UnprotectProject I wrote a blog post explaining the process behind the creation of this rule: cod3nym.github.io/Detecting-Stea… Find the Yara rule…


#100DaysofYara Day 10: Was scrolling through #UnprotectProject for some Yara rule ideas... Today, I picked the rule that detects Base64 encoding in native binaries. Contributing the rule to #UnprotectProject, of course, cc @fr0gger_ 💜 github.com/RussianPanda95…

#100DaysOfYara Day 9: Another day another .NET obfuscator #Yara rule. Today I am detecting .NET Reactor and their unique naming conventions. Also contributing to #UnprotectProject github.com/cod3nym/detect… All my obfuscator related rules available for malcat or any other Yara…


#100DaysOfYara Day 12: Making a rule for @dr4k0nia NixImports malware loader. Built for evasion without any user strings and dynamically resolving managed functions based on hashes. Also contributing to #UnprotectProject github.com/cod3nym/detect… Checkout the authors blog post…

🤓During the #100DaysOfYara, if you are not sure how to contribute, you can always contribute to the #UnprotectProject! cc: @DarkCoderSc

#100DaysOfYara Late Day 13: Wrote a Yara rule for EvasionUsingSyscall from #UnprotectProject Using a hex string to detect the emitted assembly instructions. From the POC code. github.com/cod3nym/detect… unprotect.it/technique/evas…

🤩 New anti-sandboxing technique added by @HuntressLabs into the #UnprotectProject, it includes a code snippet, and I just added a loose yara rule 👇 cc: @HuskyHacksMK thanks for your contribution 🫶 unprotect.it/technique/buil… @DarkCoderSc #infosec #malware #evasion

We have great candidates for the #UnprotectProject Linux edition @DarkCoderSc 🧐 Great writeup on the latest Ivanti zero-day 👇 cloud.google.com/blog/topics/th…

New entry in the #UnprotectProject: "Process Argument Spoofing" by @__nuts7 including code snippet! Check this out! 👇 cf: @DarkCoderSc #infosec #evasion #malware unprotect.it/technique/proc…

#100DaysOfYara Day 14: Another rule for a #UnprotectProject technique. This rule targets the Right-To-Left (RLO) extension spoofing technique.This spoofing also works on VT but only in the GUI, the URL shows the actual file %E2%80%AEfdp.exe E2 80 AE are the bytes encoding the…



🎇It's almost New Year, and if you're looking for a fun challenge to kick off 2024, check out the #100DaysOfYara by @greglesnewich – it's a good one! And if you're not sure where to start, we're in need of Yara contributors for the #UnprotectProject! #infosec #malware #evasion…

⭐ New entry in the #UnprotectProject in Network Evasion with SMTP Exfiltration. Including code snippet and I also added a yara rule! Contribution by @tasdir_x cc: @DarkCoderSc #100daysofyara unprotect.it/technique/exfi…

Something went wrong.
Something went wrong.
United States Trends
- 1. Broncos 60.5K posts
- 2. Bo Nix 16.8K posts
- 3. Geno 17.1K posts
- 4. $SMILEY 1,206 posts
- 5. YEONJUN 122K posts
- 6. Sean Payton 4,411 posts
- 7. #TNFonPrime 3,861 posts
- 8. Kenny Pickett 1,450 posts
- 9. Chip Kelly 1,859 posts
- 10. Jalen Green 6,190 posts
- 11. Bradley Beal 3,008 posts
- 12. Pete Carroll 1,703 posts
- 13. #NOLABELS_PART01 44.7K posts
- 14. Jeanty 6,316 posts
- 15. #criticalrolespoilers 3,868 posts
- 16. Troy Franklin 2,359 posts
- 17. NO LABELS NOVEMBER 16.5K posts
- 18. Thursday Night Football 6,364 posts
- 19. DANIELA 19.4K posts
- 20. TALK TO YOU OUT NOW 16.3K posts












