
Get_Started
@Get_StartedTech
Time Waits for No Man
Vous pourriez aimer
Folks, the NIST National Cybersecurity Center of Excellence (NCCoE), Microsoft, and 24 other organizations have collaborated to provide you guidance on Zero Trust implementation, including labs from Microsoft for the Microsoft Security products and services. This is a treasure…

‘Commonwealth Bank - Virtual Internship program’ Introduction to Cybersecurity theforage.com/simulations/co…



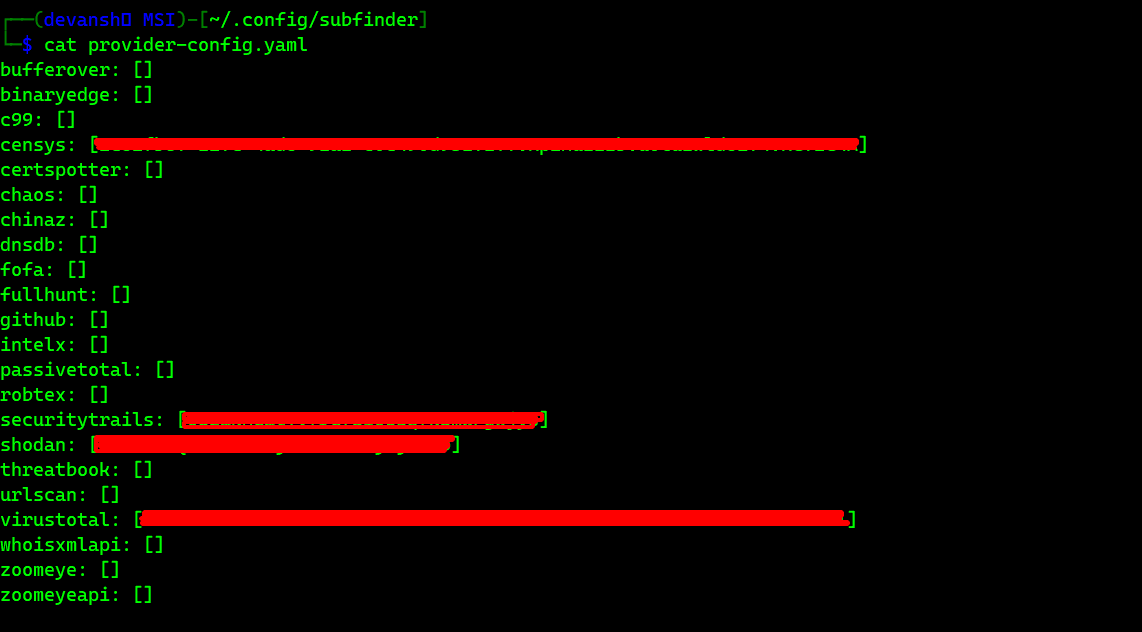
Yeah, sex is great, but have you ever added all API keys to Subfinder's provider-config.yaml?
Practical Techniques for Attacking AI Systems: Red Teaming with LLMs redteamrecipe.com/red-teaming-wi… CTF Platform by @dreadnode: crucible.dreadnode.io data augmentation, and model training in NLP: github.com/QData/TextAtta… #llm #ai #redteam

3 years of web surfing uncovered 7 wild websites. Don't miss out on these!

Hacking windows using telegram bot and windows defender enabled
Mobile Pentest Like a Pro redteamrecipe.com/mobile-pentest… Penetration applications assess iOS and Android security. Jailbreak/root methods, hooking, SSL pin, root detection, logging, storage, Content Providers, and static scanning vulnerabilities. #mobile #bugbounty #android #ios

Make $700 monthly by just TALKING to lonely people online. All you need is: 1. A Smartphone 2. Wi-Fi 3. Time Open Thread 👇
CookieKatz: Dump cookies directly from Chrome process memory meterpreter.org/cookiekatz-dum…
meterpreter.org
CookieKatz: Dump cookies directly from Chrome process memory
CookieKatz is a project that allows operators to dump cookies from Chrome, Edge, or Msedgewebview2 directly from the process memory
🚀Join us as we complete @cyberdefenders RE101 📚6 Challenges for Beginner Malware Analysts 🔍Extracting Encrypted Flags 🔓Decoding in CyberChef 🔧Fixing file headers 🔎Used a debugger to find a flag 🔐Xor Encrypted Strings 🔗youtu.be/_lzPubejr4U

This is the guy Who made the NORMAL internet 4.5 million times Faster For context, it is 340 million MB/s. Here is what you need to know

Digital Forensics Guide : Learn all about Digital Forensics, Computer Forensics, Mobile device Forensics, Network Forensics, and Database Forensics : github.com/mikeroyal/Digi… credits @MikeR256
Steps: 1. Get all urls (waymore) 2. Extract all Parameters (paramspider) 3. Use nuclei dast templates nuclei -l parameter_based_urls.txt -t nuclei-templates/dast/ -dast Post Credit: Mijanur Rahman #hackerone #ethicalhacking #bugbounty #cybersecurity #sqli #xss #infosec

If you are software developer, data scientist, AI enthusiast or entrepreneur, join us for Microsoft GenAI for Software Developers free online series where we delve into the depths of AI and its transformative impact on the software development landscape: msft.it/6014Yp8Zq

Found a vulnerability in Cisco AnyConnect? Submit your findings today at ssd-disclosure.com/cisco-anyconne… and get the BIG payouts you deserve 💰💰💰

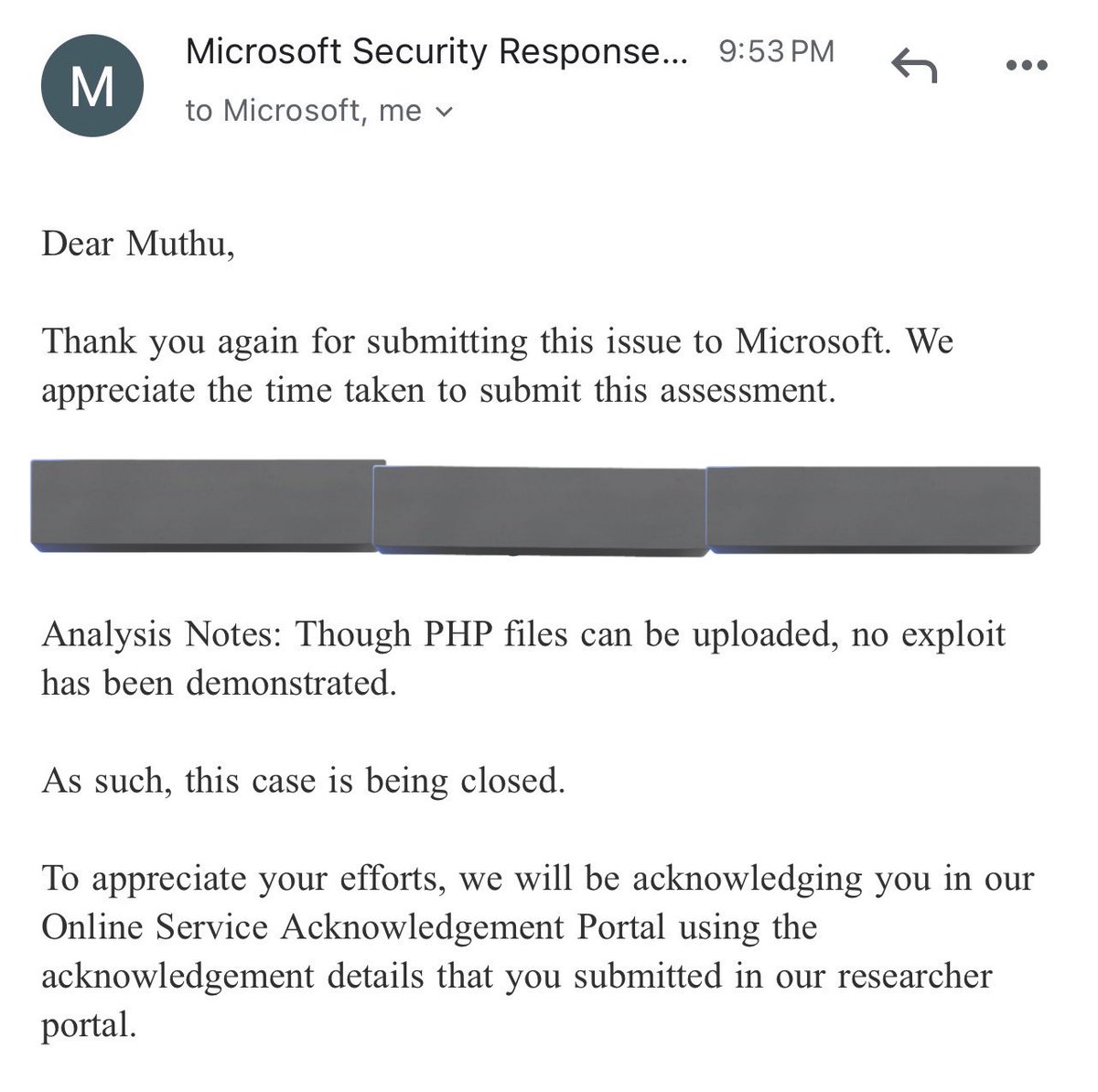
File upload bypass 😎 But can’t achieve RCE 🤡 #Microsoft #BugBounty
Python Projects For Hacking👇

United States Tendances
- 1. #SmackDown 38.1K posts
- 2. Mamdani 390K posts
- 3. Reed Sheppard 2,053 posts
- 4. Marjorie Taylor Greene 46.5K posts
- 5. Syla Swords 2,379 posts
- 6. #BostonBlue 3,325 posts
- 7. Azzi 13.7K posts
- 8. #OPLive 1,892 posts
- 9. Aiyuk 5,491 posts
- 10. Derik Queen 3,443 posts
- 11. UConn 6,616 posts
- 12. Melo 15.7K posts
- 13. Derrick White N/A
- 14. Duce 1,194 posts
- 15. Norvell 1,290 posts
- 16. Zohran 188K posts
- 17. Kevin Love 1,179 posts
- 18. Todd 24.4K posts
- 19. #OPNation N/A
- 20. Castellanos 1,239 posts
Vous pourriez aimer
Something went wrong.
Something went wrong.





















































































































