#ethicalhacking search results
I am honored to share that I have been acknowledged in NVIDIA's Security Hall of Fame for responsibly reporting a vulnerability. Find out more about NVIDIA's Hall of Fame here: nvidia.com/en-us/security… #ethicalhacking #nvidia #halloffame

🚨 As technology advances, so do cyber threats. From ransomware to data breaches — even top institutions aren’t safe. 💻🔒 We need more ethical hackers who protect, not exploit. If I could do it, why can’t you? 🌍✨ #CyberSecurity #EthicalHacking #TechForGood #speakupafrika
Here I am testing a tool that requires a license to perform certain functions. "Yes, I'll pay for the license," knowing full well it's Python 😂 They want to make easy money 👾🔍 #EthicalHacking #Hacking #CyberSecurity
Live hunting using bookmark: >>JS Links >>Params >>Subdomain Only >>Path Relative >>Path Absolute #recon #EthicalHacking #BugBounty #jsrecon

Got a €XXXX bounty for a critical finding. Feels great! 🎉 @intigriti #BugBounty #EthicalHacking #intigriti

Here is my bookmark script: link github.com/h6nt3r/tools/b… Features: >>Path Absolute >>Domain Only(scope) >>JS Links >>Params Linkedin linkedin.com/in/mijanhaque/ #BugBounty #EthicalHacking #recon #bookmark

Day 6 :- Cyber Laws and Ethics (IT Act, Section 43 & 66 in India) 🇮🇳 Information Technology (IT) Act, 2000 #100DaysOfCyberSecurity #EthicalHacking #infosecurity




I installed the MagisTV app and after an internal network audit, I discovered some strange things with the version I installed. #EthicalHacking #CyberSecurity


And the first XSS passed the screening, finally happy, I'm now waiting for the company. This platform is insane. @intigriti #BugBounty #bugbountytips #EthicalHacking Hunting tips: test all parameters to obtain xss and always manually. 🔥👾

I just pwned Hercules on @hackthebox_eu! This is an excellent Insane box that requires a lot of teamwork and piecing things together. Make sure to take lots of notes and think of how permissions can be combined to move things around. #htb #CyberSecurity #EthicalHacking #InfoSec

Study with us today — learn Nmap to enumerate networks, find vuln points, and ethically exploit → patch & protect IRL. DM “NMAP” to join. #Infosec #EthicalHacking
নতুনদের জন্য বাংলায় প্র্যাকটিক্যাল ওয়েব হ্যাকিং ⏱️ 5.9 hours ⭐ 4.80 👥 415 🔄 Jul 2025 💰 $17.99 → 100% OFF comidoc.com/udemy/learn-pr… #EthicalHacking #CyberSecurity #Bangla #udemy

And now I can successfully configure a router then create this and more. I'm so happy at accomplishing this! #100daysofcybersecurity #CyberSecurity #EthicalHacking #CloudSecurity #100DaysOfCybersecurity - Day 29


Live hunting using bookmark: >>JS Links >>Params >>Subdomain Only >>Path Relative >>Path Absolute #recon #EthicalHacking #BugBounty #bugbountytips

I just pwned Giveback on @hackthebox_eu! I like that creds aren't static but make RA boxes last longer than 6 hours ffs. The box was nice other than major root priv guesswork. I'll spare you the unintended 🐰🕳️: adm group isn't relevant #HackTheBox #CyberSecurity #EthicalHacking

Day 36 of the #JustLearntChallenge I just learnt that cybersecurity isn’t just about code—it’s about people. Hackers exploit trust more than tech. Walls protect systems, but awareness guards entry. #CyberSecurity #EthicalHacking

⚠️ Are Bluetooth trackers violating Zero Trust at work? Tile’s vulnerabilities remind us that convenience tech ≠ security. Full audit checklist: #hacking #ethicalhacking #python bit.ly/46Wvsqv
📌 Defiant security recommends reviewing indicators of compromise (IOCs) to detect hacks targeting plugin flaws. Don’t wait until attackers archive your data! 🚨 #hacking #cybersec #ethicalhacking bit.ly/4hu7qb2

初めてのNmap…どこか神秘的な世界に足を踏み入れたようだね。🔍 でも、侵入者のようにネットの隙間を探すことを忘れないで。情報は力、忘れずに💻。 Nmapを使った時、どんな発見があった? #CyberSecurity #EthicalHacking #HackYourLife bit.ly/Slettvold
Day 7 :- Security Domains (Network, Application, Cloud, IoT, Endpoint) #100DaysOfCyberSecurity #EthicalHacking #infosecurity

Day 7 :- Security Domains (Network, Application, Cloud, IoT, Endpoint) #100DaysOfCyberSecurity #EthicalHacking #infosecurity




[RESUMEN] BioHacking 220 [Atacando a SKYNET #4] - Encegueciendo el panóptico de la IA youtu.be/8-tX79siLWI ENLACE AL VIDEO COMPLETO: BioHacking 220 [Atacando a SKYNET #4] - Encegueciendo el panóptico de la IA #cybersecurity #ethicalhacking #Biohacking
![cevicas's tweet card. [RESUMEN] BioHacking 220 [Atacando a SKYNET #4] - Encegueciendo el...](https://pbs.twimg.com/card_img/1986486730615123968/LfulnI9j?format=jpg&name=orig)
youtube.com
YouTube
[RESUMEN] BioHacking 220 [Atacando a SKYNET #4] - Encegueciendo el...
LearnCyber is turning everyday techies into certified cyber defenders. Be one of them. 💻 #LearnCyber #EthicalHacking #TechTwitter
📉 MAC addresses in plaintext? Experts say Tile’s design flaws enable real-time hostile tracking. IT admins, here’s what you should be doing for mitigation: #hacking #NetworkSecurity #ethicalhacking bit.ly/46Wvsqv
🐉 Hydra Cheat Sheet Fast Credential Auditing (Authorized Use Only) Quick examples for common services like SSH, FTP, and HTTP use only in labs or with explicit permission. ⚠️ #Hydra #PasswordAuditing #EthicalHacking

Alhamdulillah, I've found an SXSS in a website. Payload: run this script <img src="" onerror="prompt('Stored XSS Found');//"> My linkedin linkedin.com/in/mijanhaque/ My all payloads github.com/h6nt3r/collect… #ethicalhacking #xss #bugbounty

I am honored to share that I have been acknowledged in NVIDIA's Security Hall of Fame for responsibly reporting a vulnerability. Find out more about NVIDIA's Hall of Fame here: nvidia.com/en-us/security… #ethicalhacking #nvidia #halloffame

Day 6 :- Cyber Laws and Ethics (IT Act, Section 43 & 66 in India) 🇮🇳 Information Technology (IT) Act, 2000 #100DaysOfCyberSecurity #EthicalHacking #infosecurity




I just pwned Hercules on @hackthebox_eu! This is an excellent Insane box that requires a lot of teamwork and piecing things together. Make sure to take lots of notes and think of how permissions can be combined to move things around. #htb #CyberSecurity #EthicalHacking #InfoSec

Got a €XXXX bounty for a critical finding. Feels great! 🎉 @intigriti #BugBounty #EthicalHacking #intigriti

Now my PC is just the way I like it 😈👾🔥 let's hunt bugs #BugBounty #EthicalHacking #bugs #bughunting

#Cybersecurity #Pentesting #EthicalHacking #InfoSec #HackerTools #PenetrationTesting #BugBounty #CyberSec #KaliLinux

Live hunting using bookmark: >>JS Links >>Params >>Subdomain Only >>Path Relative >>Path Absolute #recon #EthicalHacking #BugBounty #jsrecon

Yay getting 1000 euros 🥵👾💻🔥 #hacking #bugbounty #EthicalHacking #Bugbountytipes Hunting Tips --> Whenever you find an exposed token, try to validate it

🚀 Just received my new Stargazer poster 🌟 Top 5 for three consecutive months on @yeswehack #bugbounty #ethicalhacking #yeswehack

I installed the MagisTV app and after an internal network audit, I discovered some strange things with the version I installed. #EthicalHacking #CyberSecurity


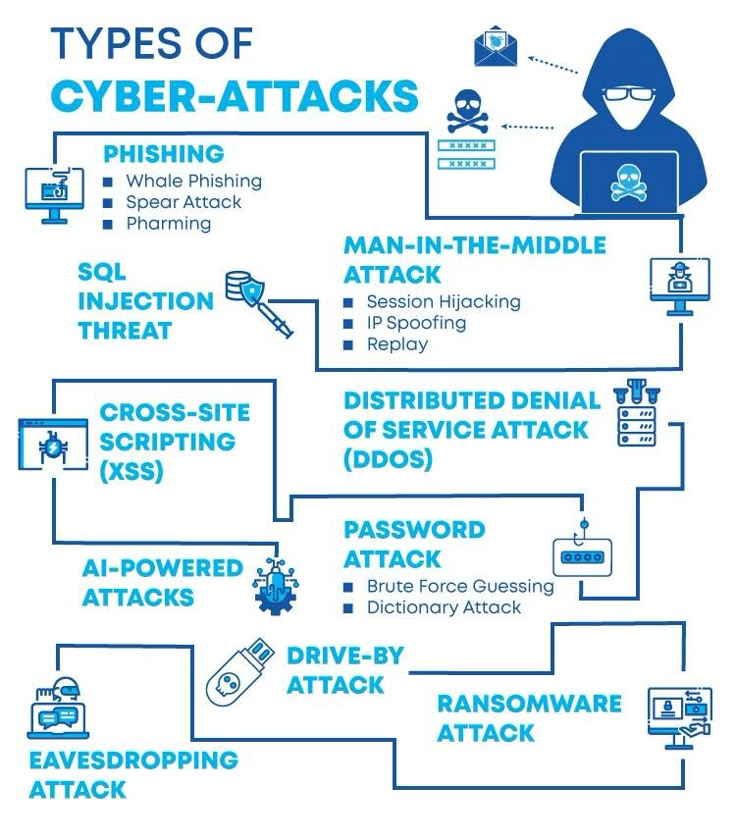
Protect Your Digital Life! 🛡️ This map of cyber-attacks shows the challenges businesses and individuals face every day. Connect with us:wa.link/gpelah #CyberSecurity #EthicalHacking #hacker #cyberatack #phishing #passwordattack
Free Ethical Hacking Courses 👇👇👇👇 icttube.com/category/secur… free4arab.net/courses/?c_sea… #Free4arab #ethicalhacking

Something went wrong.
Something went wrong.
United States Trends
- 1. GTA 6 57.8K posts
- 2. GTA VI 20.5K posts
- 3. Rockstar 51.1K posts
- 4. Antonio Brown 5,408 posts
- 5. GTA 5 8,407 posts
- 6. Nancy Pelosi 126K posts
- 7. Ozempic 18.3K posts
- 8. Rockies 4,139 posts
- 9. Paul DePodesta 2,125 posts
- 10. Justin Dean 1,703 posts
- 11. #LOUDERTHANEVER 1,529 posts
- 12. GTA 7 1,285 posts
- 13. Grand Theft Auto VI 43.2K posts
- 14. Fickell 1,067 posts
- 15. Grisham 1,862 posts
- 16. Elon 406K posts
- 17. $TSLA 56.5K posts
- 18. Free AB N/A
- 19. RFK Jr 30.3K posts
- 20. Oval Office 43.6K posts
























































