New to Cybersecurity ? Start here👇 1️⃣ Learn Basic IT & Networking 2️⃣ Master Linux & Commands 3️⃣ Web App Security 4️⃣ Tools: Nmap, Burp, Wireshark 5️⃣ Certifications (optional): Security+, CEH 6️⃣ Build Labs & Practice Daily If you want, I’ll guide you for free. Follow for…
Hackers can SEE through your walls using Wi-Fi, SDR & AI! Watch NOW: youtube.com/watch?v=rH9oJJ… @three_cube @HoffmanYaniv

youtube.com
YouTube
They’re Watching You Through Wi-Fi… And You Have No Idea
- Programming sits on maths. - Algorithms run on maths. - Every AI model is maths. - Machine learning is maths. - Deep learning is maths. - Graphics are maths. - Simulations are maths. - Cryptography is maths. - Blockchain is maths. - Data science is maths. - Optimization is…

For Ethical Hacking Enthusiasts

Q: Which command shows active network connections on a Linux system?
You put an Application Load Balancer in front of a single EC2 instance running a personal blog that gets 40 visitors per month. - $22/month ALB cost - $18/month EC2 cost - Health checks every 30 seconds - SSL termination for no reason - Target groups with 1 target Your…
🐳The Tech Genius who changed How Software runs & Ships > Meet Solomon Hykes ; the creator behind Docker > Built container tech before “containers” became a buzzword > Solved one core problem: run apps the same everywhere > Created a tool so clean it reshaped DevOps > Introduced…

Q: Which command shows active network connections on a Linux system?
Connecting an LCD to your Raspberry Pi with I2C only uses up 4 GPIO pins. Learn how set it up with this tutorial [VIDEO] youtube.com/watch?v=wCfZ1x… #raspberrypi #maker #diyelectronics
![circuitbasics's tweet image. Connecting an LCD to your Raspberry Pi with I2C only uses up 4 GPIO pins. Learn how set it up with this tutorial [VIDEO] youtube.com/watch?v=wCfZ1x… #raspberrypi #maker #diyelectronics](https://pbs.twimg.com/media/G7kyBDEWQAAF5Qi.jpg)
$600 Smart Toilet Spies on You
Daily CCNA Challenge! | CCN 200-301 v1.1 Start To Learn %60 OFF: ipcisco.com/membership/ Please ReTweet..:) . #cisco #CCNA #networkengineer

Streamline @RedHat #OpenShift upgrades in disconnected setups. Deploy a local OSUS, replicate the "over-the-air" update experience, and manage multiple clusters efficiently. red.ht/48gY9jP
2026 Predictions: Identity, AI-Agents, and The New Guardrails linkedin.com/pulse/2026-pre…
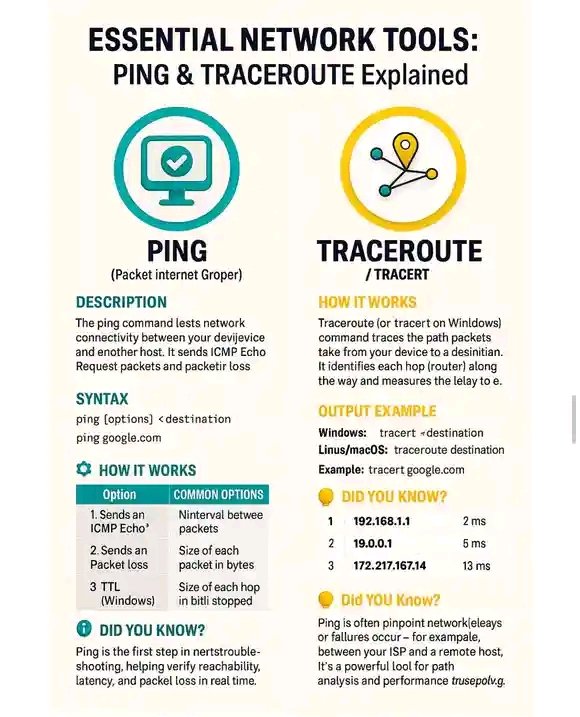
Essential Network Tools : Ping & TRACEROUTE Explained
If you want to start OT/ICS Cybersecurity → start here. Super valuable resource! youtube.com/live/tFDYy7XKR…

youtube.com
YouTube
How to Get Started in OT/ICS Cybersecurity
Here is the LinkedIn post link 🖇️ linkedin.com/posts/mikeholc…
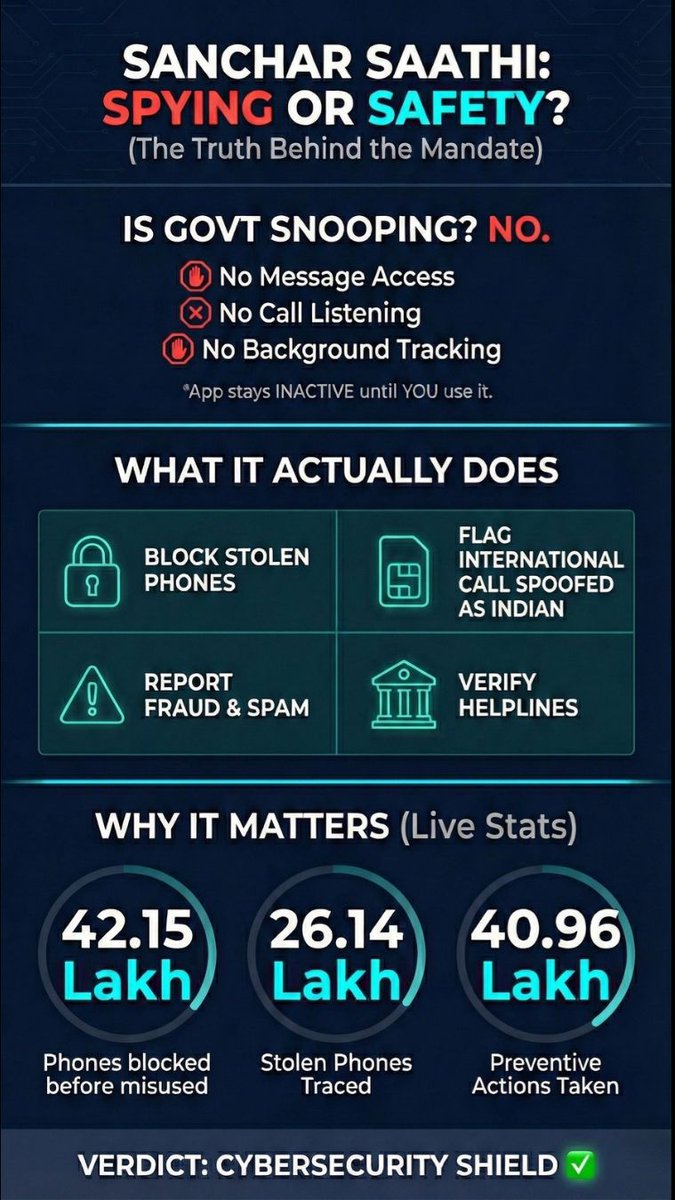
What exactly Sanchar Sathi App do ? What is your view? #SancharSaathiApp
Network attacks are malicious attempts by threat actors to disrupt, steal, modify, or gain unauthorized access to network systems, data, or devices. --- 🔐 Major Types of Network Attacks 1. Passive Attacks (Silent Monitoring) Attacker only observes the data without altering…



🔍 What is OSINT? (Open-Source Intelligence) #cybersecurity #osint #infosec OSINT is one of the most powerful skills in cybersecurity, ethical hacking, investigations, and threat intelligence. It allows us to gather publicly available information for security analysis,…

United States 트렌드
- 1. #IDontWantToOverreactBUT N/A
- 2. Good Monday 49.1K posts
- 3. #GoldenGlobes 41.5K posts
- 4. #MondayMotivation 9,119 posts
- 5. Harada 11.5K posts
- 6. Victory Monday 1,354 posts
- 7. Tekken 27.7K posts
- 8. JUNGKOOK X ROLLING STONE 56.5K posts
- 9. #MYNZ_CRCRevolution N/A
- 10. #OrmxHausNowhereBKK 778K posts
- 11. ORM HAUS NOWHERE GOP 757K posts
- 12. NextNRG Inc N/A
- 13. Mainz Biomed N.V. N/A
- 14. Eva Victor 1,302 posts
- 15. MAGICAL WITH WILLIAMEST 352K posts
- 16. Will Hall 4,653 posts
- 17. Emily Blunt 2,029 posts
- 18. Orm Kornnaphat 40.3K posts
- 19. John Lennon 11.6K posts
- 20. Zara 11.8K posts
Something went wrong.
Something went wrong.