
Logicalis CI
@LogicalisCI
The largest IT services company in the Channel Islands Logicalis offers a comprehensive range of Information and Communications Technology solutions & services.
You might like
Online threats can be very daunting, however, there are many ways to address cyber security and reduce your organisations risk from a cyber-attack. Once you have your online security in place, you can get back to what you do best and feel confident that this area is in hand!

Our inherent curiosity and trusting nature are any organisations biggest security risk, so let’s make sure employees are provided with the knowledge, understanding and tools to dramatically increase cyber security. buff.ly/36Qo3Je #cybersecurity
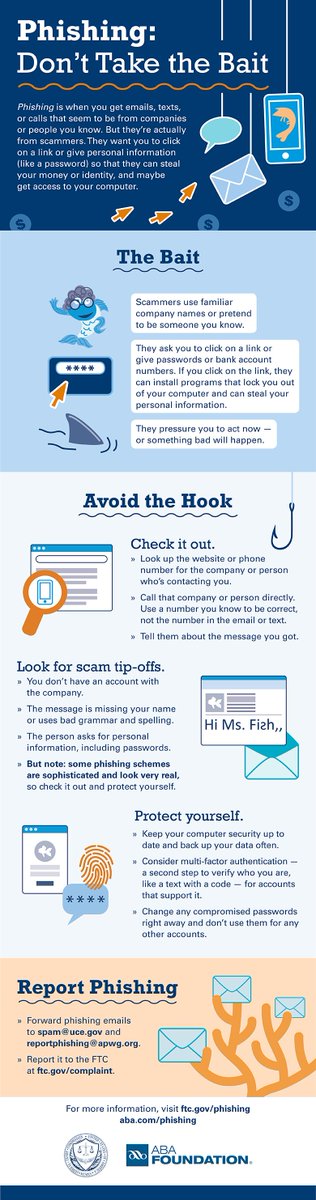
Phishing emails are our biggest online threats, but there are also some simple tell-tale signs we can look out for to avoid them. The following blog by Stay Safe Online offers five ways to spot a phishing email: buff.ly/2NQs4XD
As technology continues to transform the global business environment, more and more companies are seeing cyber risk as a top priority. #cybersecurity

An in-depth incident response plan is what you need! Having a plan in place helps you to identify a cyber-attack and minimize the possible damages and costs. An incident response plan can also help to find the cause and prevent future attacks. #incidentresponse #cyberattack

Online security expert Roger Grimes, has seen many a company policy stating that they will fire anyone for just ONE accidental phishing offence, so, challenges these policy makers to let him attempt to phish them buff.ly/2OPML6g #onlinesecurity

We all know the importance of a fire safety drill in helping to reduce the negative repercussions from an emergency – the same can be applied to your cyber security. Contact a member of our team on 288 000 today to discuss cyber-attack drills – what, how and why. #cyberattack

Companies are most at risk from phishing attacks, however, with regards to cyber security, it is still one of the things least worked on in organisations. One way to reduce the chance of a phishing attack is to improve employee's knowledge. #CyberSecurity #OnlineSafety
Social Engineering and phishing is responsible for 70-90% of all malicious data breaches – so it’s time to get your company informed and train your employees on how to be vigilant and avoid being victim of a successful phishing attack. Figure from Roger Grimes 2017. #phishing

Quick detection of a cyber-attack is key to reduce repercussions. Niall Sookoo, the Labour party executive director of elections - “I would I like to pay tribute to all the teams at Labour HQ who identified this risk and acted quickly to protect us.” buff.ly/32ZhGR0

The best solution to ransomware attacks is to prevent them from happening in the first place. Compuquip Cybersecurity discuses preparation as the key to preventing ransomware attacks in the following article: buff.ly/2Xar31j #Ransomware #cyberattacks #CyberSecurity

Claranet UK looks at the benefits of working with a managed service provider. “... (MSP) helps to bridge the gap between the capacity of your IT department, and the increasing demand for fast-moving, stable, high-performance business technology.” buff.ly/2XL5Mbz

Threat modelling is an important step in the development of a new piece of software and comes with the major advantage of sorting security issues when there is time to do so. buff.ly/2XgxFuZ #threatmodelling #CyberSecurity #ethreat #cybercrime

Know Be4 offer a clear explanation of social engineering, what it is, how it works and why it is dangerous. buff.ly/2QXpn55 #socialengineering #

How do you decide whether managed services is right for you? Get in touch with Logicalis CI today with any queries or to discuss how we may be able to help. Call us on 01534 288 000. buff.ly/2Xd5EEH #managedit

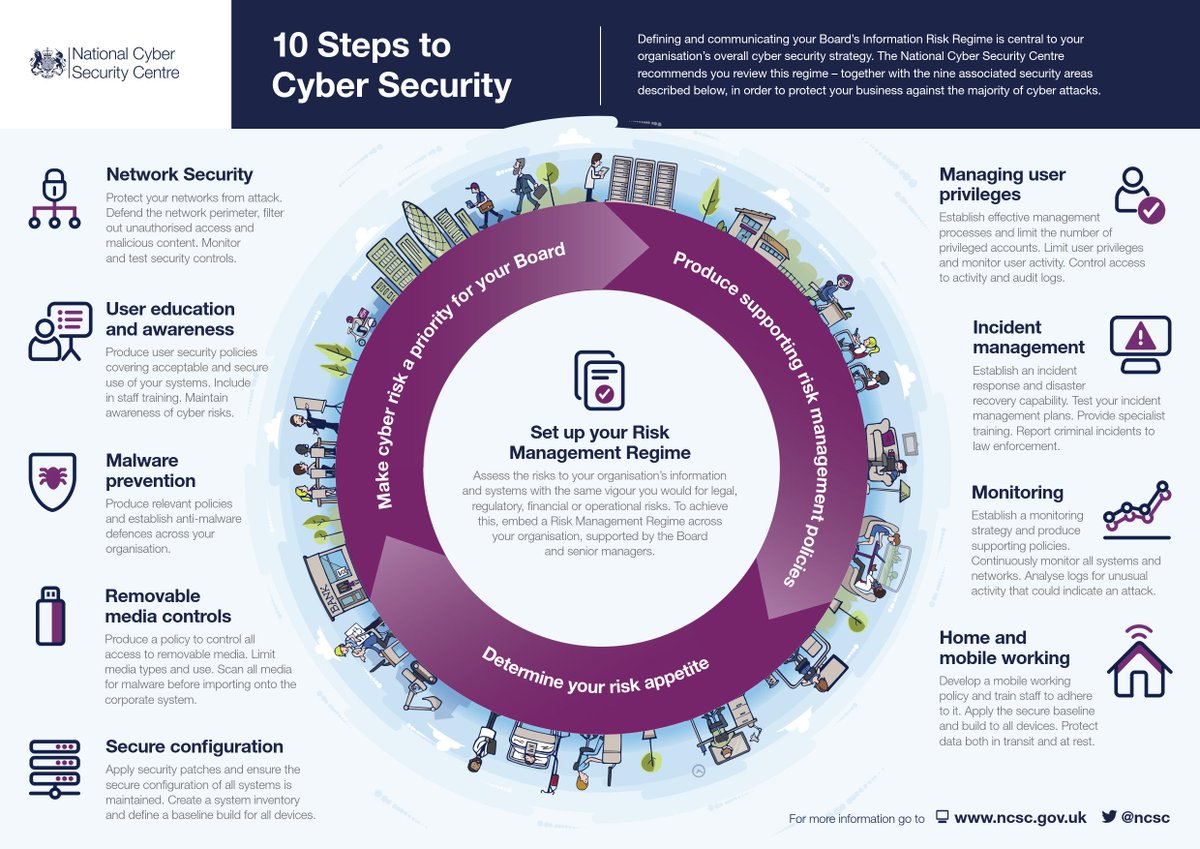
The National Cyber Security Centre’s 10 steps to cyber security. #cybersecurity #esafe #technology
Increased efforts are being made within organisations to improve security, such as looking at new ways to authenticate beyond passwords. The following article explores why biometrics shouldn’t be considered as replacements for passwords : buff.ly/2XL475R #passwords
Phishing attacks tend to be more successful when they appear as something known to the victim. Microsoft, Paypal and DHL are listed among the top impersonated brands in attacks. The following article offers a list of the top ten impersonated brands: buff.ly/2Iw1Q85

Ransomware victims in 2019 may have more to worry about than business disruption and recovery costs. "... cover their tracks by dropping ransomware inside an infrastructure after they’ve successfully achieved their goals.” - Liviu Arsene buff.ly/2WJVP1E #Ransomware

An individual's ability to resist a scam heavily depends on their prior knowledge of scams and awareness of what to look out for, hence why internal training is pivotal to decreasing a company’s cyber risk. buff.ly/2XTkLjT

United States Trends
- 1. #HardRockBet 3,925 posts
- 2. Arsenal 276K posts
- 3. Tottenham 86.7K posts
- 4. #ARSTOT 14.9K posts
- 5. #AskFFT 1,178 posts
- 6. Thomas Frank 6,172 posts
- 7. Mason Rudolph 2,971 posts
- 8. Richarlison 8,807 posts
- 9. #COYG 6,765 posts
- 10. Klay 43.1K posts
- 11. Merino 20.1K posts
- 12. Raya 16.9K posts
- 13. Trossard 16K posts
- 14. Great for 60 N/A
- 15. Sean Tucker 1,137 posts
- 16. #sundayvibes 7,886 posts
- 17. PEAKTOOZ 2,195 posts
- 18. Emanuel Wilson N/A
- 19. Full PPR 1,580 posts
- 20. NFL Sunday 7,908 posts
Something went wrong.
Something went wrong.







































































