
M4lcode
@M4lcode
Malware researcher exploring malware, APT groups, and their campaigns across the wild. | Threat Researcher @dexpose_io | Blog Author @anyrun_app & @cyber5w
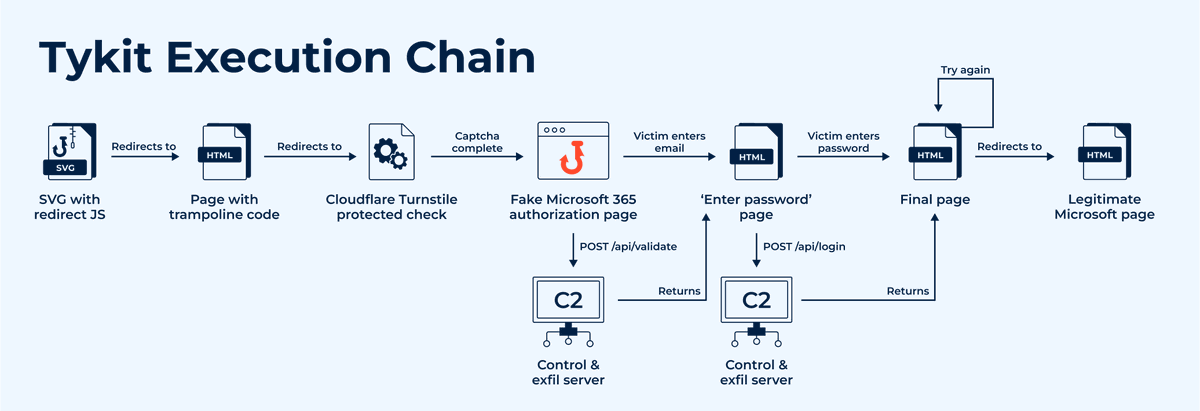
🚨 We uncovered #Tykit, a new #phishing kit targeting hundreds of US & EU companies in finance, construction, and telecom. It uses SVG-based delivery to harvest Microsoft 365 credentials ⚠️ See full analysis, how to detect it, and gather #IOCs: any.run/cybersecurity-…
Fresh malware analysis from @anyrun_app: FunkLocker TTPs, artifacts, and practical takeaways for SOC and DFIR. Read: any.run/cybersecurity-…
Just published a deep dive into APT27 (Emissary Panda/Iron Tiger/Lucky Mouse), a Chinese state-sponsored cyber-espionage group active since 2010, known for spear-phishing, watering-hole attacks and exploitation of internet-facing applications. dexpose.io/threat-actor-p…

🚨#ANYRUN’s TI Feeds now offer a connector for Microsoft Sentinel Get fresh, filtered #IOCs from the latest attacks worldwide, updated every 2 hours and enriched with sandbox analyses Expand incident monitoring, boost detection rate, and slash MTTR 👇 any.run/cybersecurity-…
As-salamu Alaykum I wrote 3 #yara rules about #RedLine stealer , #ArrowRAT, and #MilleniumRat. RedLine:github.com/muha2xmad/yara… ArrowRAT:github.com/muha2xmad/yara… MilleniumRat:github.com/muha2xmad/yara…
PureLogs is live. A new challenge created by me. good luck
Just published a new blog post on how Microsoft’s “Mouse Without Borders” can be abused for data exfiltration & lateral movement. Features KAPE Target, C# scripts, and a BOF as a poc: 0xsultan.github.io/dfir/Exfiltrat…
Open directory spotted: 20.243.255[.]185 Hosting multiple suspicious files, including: shell_le: Metasploit ELF payload - recently submitted to VirusTotal. true.png: PNG file with embedded VBScript (1/61 on VT) - recently submitted to VirusTotal main_mips: ELF binary flagged…
![M4lcode's tweet image. Open directory spotted: 20.243.255[.]185
Hosting multiple suspicious files, including:
shell_le: Metasploit ELF payload - recently submitted to VirusTotal.
true.png: PNG file with embedded VBScript (1/61 on VT) - recently submitted to VirusTotal
main_mips: ELF binary flagged…](https://pbs.twimg.com/media/GtZ7YRqXEAEWRXT.jpg)
![M4lcode's tweet image. Open directory spotted: 20.243.255[.]185
Hosting multiple suspicious files, including:
shell_le: Metasploit ELF payload - recently submitted to VirusTotal.
true.png: PNG file with embedded VBScript (1/61 on VT) - recently submitted to VirusTotal
main_mips: ELF binary flagged…](https://pbs.twimg.com/media/GtZ7YRqX0AAEzI4.png)
![M4lcode's tweet image. Open directory spotted: 20.243.255[.]185
Hosting multiple suspicious files, including:
shell_le: Metasploit ELF payload - recently submitted to VirusTotal.
true.png: PNG file with embedded VBScript (1/61 on VT) - recently submitted to VirusTotal
main_mips: ELF binary flagged…](https://pbs.twimg.com/media/GtZ7YRqWgAAT-T9.png)
![M4lcode's tweet image. Open directory spotted: 20.243.255[.]185
Hosting multiple suspicious files, including:
shell_le: Metasploit ELF payload - recently submitted to VirusTotal.
true.png: PNG file with embedded VBScript (1/61 on VT) - recently submitted to VirusTotal
main_mips: ELF binary flagged…](https://pbs.twimg.com/media/GtZ7YRpWYAAqAlD.png)
#clickfix #booking #fakecaptcha bokparthub[.]click → (Under Construction) apartmenr-di16[.]click → PowerShell (files.catbox.moe/09fd7c[.]txt) → LightYellow4.zip → LightYellow4.pfx Hex-based ZIP reconstructed → payload cleaned → executed via regsvr32.exe abuse (LOLBins)
![M4lcode's tweet image. #clickfix #booking #fakecaptcha
bokparthub[.]click → (Under Construction)
apartmenr-di16[.]click → PowerShell (files.catbox.moe/09fd7c[.]txt) → LightYellow4.zip → LightYellow4.pfx Hex-based ZIP reconstructed → payload cleaned → executed via regsvr32.exe abuse (LOLBins)](https://pbs.twimg.com/media/GtK9KL_W8AAgxNo.jpg)
![M4lcode's tweet image. #clickfix #booking #fakecaptcha
bokparthub[.]click → (Under Construction)
apartmenr-di16[.]click → PowerShell (files.catbox.moe/09fd7c[.]txt) → LightYellow4.zip → LightYellow4.pfx Hex-based ZIP reconstructed → payload cleaned → executed via regsvr32.exe abuse (LOLBins)](https://pbs.twimg.com/media/GtK9KM0XAAATqjZ.jpg)
![M4lcode's tweet image. #clickfix #booking #fakecaptcha
bokparthub[.]click → (Under Construction)
apartmenr-di16[.]click → PowerShell (files.catbox.moe/09fd7c[.]txt) → LightYellow4.zip → LightYellow4.pfx Hex-based ZIP reconstructed → payload cleaned → executed via regsvr32.exe abuse (LOLBins)](https://pbs.twimg.com/media/GtK9KJZXgAAB3dW.png)
![M4lcode's tweet image. #clickfix #booking #fakecaptcha
bokparthub[.]click → (Under Construction)
apartmenr-di16[.]click → PowerShell (files.catbox.moe/09fd7c[.]txt) → LightYellow4.zip → LightYellow4.pfx Hex-based ZIP reconstructed → payload cleaned → executed via regsvr32.exe abuse (LOLBins)](https://pbs.twimg.com/media/GtK9zd-XoAAuyLY.png)
We’re excited to announce the launch of malops.io , a platform built by analysts, for analysts and it’s completely free. You can join and enjoin with our frist challenge about RokRat Loader.

Lately, I've been working on analyzing several stealers and a PE injector. Take a look 😃 Fileless pe injector uses reflective loading : blog.dexpose.io/analysis-of-ar… Purelogger: blog.dexpose.io/purelogger-dee… Salat Stealer: blog.dexpose.io/understanding-… Flesh Stealer: blog.dexpose.io/flesh-stealer-…

FExcited to share that ANY.RUN now supports Android OS inside its interactive sandbox! You can analyze APK behavior in real time, right in the cloud. 🔥 Available for ALL plans (yes, even free!). 📷 Let’s check it out together! app.any.run/?utm_source=x_…

United States Тренды
- 1. Godzilla 25.2K posts
- 2. Shabbat 3,182 posts
- 3. Trench 7,541 posts
- 4. $DUOL 2,712 posts
- 5. Barca 98.7K posts
- 6. Brujas 28.6K posts
- 7. Lamine 67.5K posts
- 8. Barcelona 155K posts
- 9. #dispatch 40.3K posts
- 10. Brugge 49.9K posts
- 11. Richardson 3,424 posts
- 12. Flick 38.6K posts
- 13. Toledo 10.3K posts
- 14. Captain Kangaroo N/A
- 15. Alastor 88.5K posts
- 16. Sharia 120K posts
- 17. Jared Golden 2,210 posts
- 18. Foden 22.6K posts
- 19. SCOTUS 37.4K posts
- 20. Anthony Taylor 1,906 posts
Something went wrong.
Something went wrong.



































































































