Netsec
@NetsecSE
Bank-grade Security - Next Gen Thought Leader
You might like
Windows Server 2028 will include mandatory "Azure NTP", giving you modern cloud time sync capabilities for only $1/month/server.
So long WSUS! Hope everyone has $5/month/server in their budget for Azure patch management. A service that previously was available for $0/server through Azure Automation. techcommunity.microsoft.com/t5/windows-it-…
While #CrowdSrtike had a massive outage, CISOs and many security managers asked me about delaying updates in Microsoft Defender. This article discusses these possibilities in MDAV and MDI. Still, you should decide what is best for your organization and technological…
A out-of-bounds write vulnerability [CWE-787] in FortiOS may allow a remote unauthenticated attacker to execute arbitrary code or command via specially crafted HTTP requests. "Workaround : disable SSL VPN (disable webmode is NOT a valid workaround)" fortiguard.com/psirt/FG-IR-24…
Begs the question why MSFT who spends billions on LLMs can't make their phishing filter more effective. Should be a perfect match for Defender for Office? x.com/markrussinovic…
Not comforted by the fact that Microsoft doesn't clearly and publicly address this question that obviously worries alot of people. If there wasn't anything fishy being planned here, why not just post a blog and clear all confusion?
As an EA customer, I can chime in here that we've been told the standalone SKU is no longer available for us either; "that SKU cannot be ordered as Microsoft is moving towards Azure consumption for this product."
No, just No! If this requirement remains, then it's time to look for an alternative for MDE.
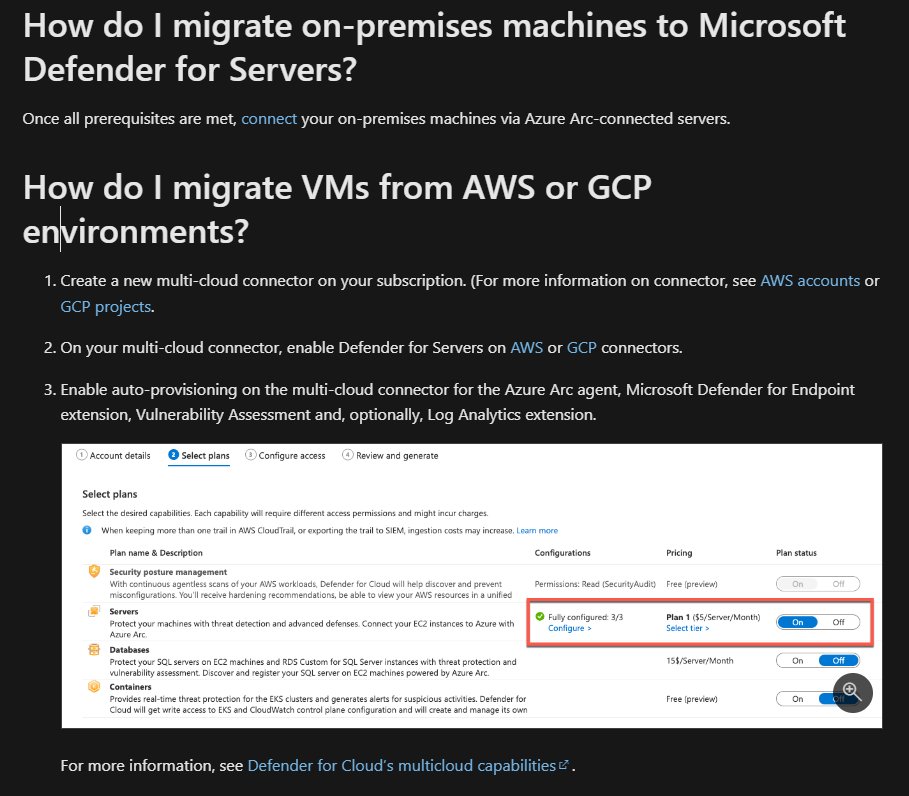
MDE for Servers will are longer be sold. Instead you need to buy Microsoft Defender for Servers through Azure. Microsoft is forcing customers to move toward Azure, whether they like it or not. Shitstorm incoming.
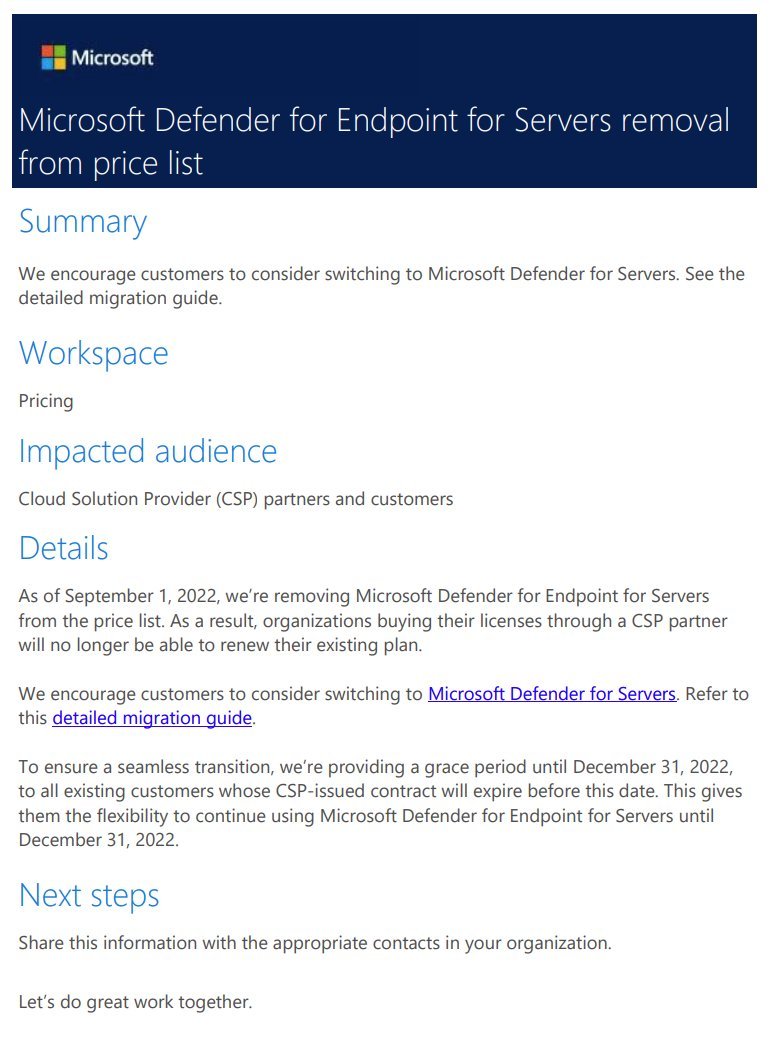
I'm normally very Pro-MSFT, but this is ridiculous. Just when you thought MSFT were positioning themselves well as regards security, this will drive enterprises and possibly CSP's to choose other vendors as opposed to forcing customers to unneeded Azure subs. #msftsecurity
Whelp, not good news... This seems to affect EA too. This decision will drive many orgs away from MDE, not just on servers but clients too, which devalues E5 licensing affecting all other groups All to drive Azure sales that were never on the table
This is what happens when people making decisions have no comprehension of the technical side and don't have anyone helping them I can see how an unknowing PM could see upsell opportunities, but they've obviously never lived a single deployment of the solution in their life
Whelp, not good news... This seems to affect EA too. This decision will drive many orgs away from MDE, not just on servers but clients too, which devalues E5 licensing affecting all other groups All to drive Azure sales that were never on the table
Whelp, not good news... This seems to affect EA too. This decision will drive many orgs away from MDE, not just on servers but clients too, which devalues E5 licensing affecting all other groups All to drive Azure sales that were never on the table
A capability I'd very much like to see. But doubt it'll work with current implementation of group write back(?).
Hmm… so would it be possible to use AzureAD PIM as a PAM solution for OnPrem AD with TTL group memberships? :) I mean, the wait for AADConnect sync could be a challenge, but it would be an AWESOME extension!
This is gonna be fun to play with.
You can now hunt for URL clicks data! All details 👉🏾 aka.ms/AAgsa0q #CyberSecurity #ThreatHunting #m365d #XDR
Security Policy & Regulatory Compliance would be nice, but hardly worth 3x the cost of P1 imho.
We released a new #Defender for Servers Plan, now you can select between P1 and P2 in the dashboard. More info here docs.microsoft.com/en-us/azure/de…
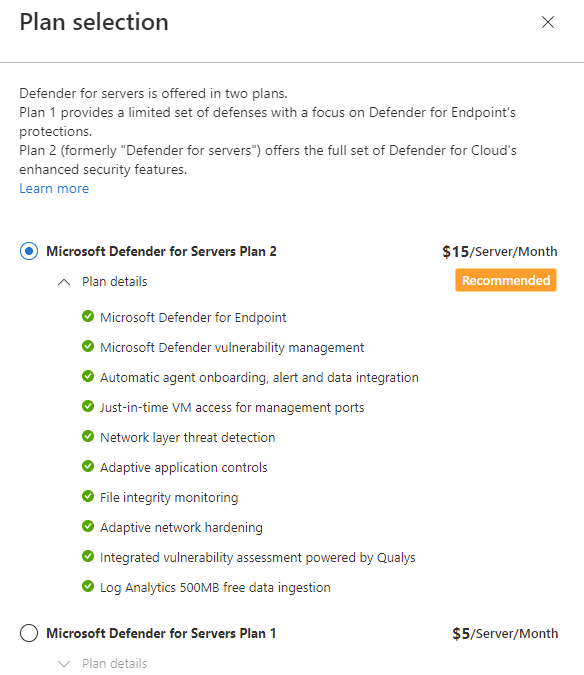
So hurry up and take number matching out of preview? microsoft.com/security/blog/…

Admin came to us after we retrieved his credentials in plaintext with mimikatz. Asked us not to put his credentials in the report as he used it for all his accounts(work and private). And he didn't want to have to change it.
Love the FalconFriday posts. Educational and actionable content that has helped me to build several new detections in my environment.
It is #FalconFriday again! This time we have a detection for suspicious named pipe use in #MDE. This logic can also be applied to #Sysmon telemetry. medium.com/falconforce/fa… #ThreatHunting #DetectionEngineering #NamedPipes
See askwoody.com/ms-defcon-syst… going to be sending out a special alert in the morning warning about business patching side effects. Going to MS-DEFCON 1
For MDE it would be useful to have something for domains that's similar to the prevalence count available for executables. Not sure if technically feasible though. In general I think there's much potential for adding features that leverages the DNS telemetry already collected.
Vendors happily informing you that they use Log4j 1.x is the equivalent to "This patch Tuesdays vulnerabilities does not affect us since all our servers run Windows 2000".
lol. i knew it someone is gonna make this one.
United States Trends
- 1. #UFC325 N/A
- 2. Shu Shu N/A
- 3. Dan Hooker N/A
- 4. Ruffy N/A
- 5. #AEWCollision N/A
- 6. Tuivasa N/A
- 7. Fiziev N/A
- 8. Doug Shows N/A
- 9. Keyshawn N/A
- 10. #RoyalRumble N/A
- 11. Herb Dean N/A
- 12. Cooper Flagg N/A
- 13. Arkansas N/A
- 14. #LopezStevenson N/A
- 15. Ciampa N/A
- 16. #OPLive N/A
- 17. Teixeira N/A
- 18. Kentucky N/A
- 19. Saint Denis N/A
- 20. Jarrell Miller N/A
Something went wrong.
Something went wrong.