#networksecurity search results
Modern enterprises depend on networks built for speed, security, and scalability. Learn how to optimize your infrastructure for AI, IoT, and edge performance. ➡️ hubs.li/Q03V-bBG0 #EnterpriseIT #NetworkSecurity #CiscoMeraki

⚠️ Configura la seguridad de tus servidores #WindowsServer para que estén blindados contra ataques DDoS y más. #networksecurity #ciberseguridadparatodos

Your organization’s safety starts with everyday decisions. Small habits create strong defenses. Let’s rethink how we protect what matters. #CyberSecurity #NetworkSecurity #Infosec #DataProtection #Malware




🚨 Cada segundo cuenta cuando ocurre un ataque. La monitorización te permite actuar a tiempo. ⏱️🛡️ #concienciacionciberseguridad #networksecurity

For FREE Help Designing A Custom #Cybersecurity Strategy/Framework For Your Organization Simply Ask Here=> ds3-bandwidth.com/quote-request/ #CISO #NetworkSecurity @Nicochan33 @ChuckDBrooks @harshleenchawl2 @cybergeekgirl @BillMew @CaffSec @cybervizer @CISOWaterCooler @mclynd @Corix_JC

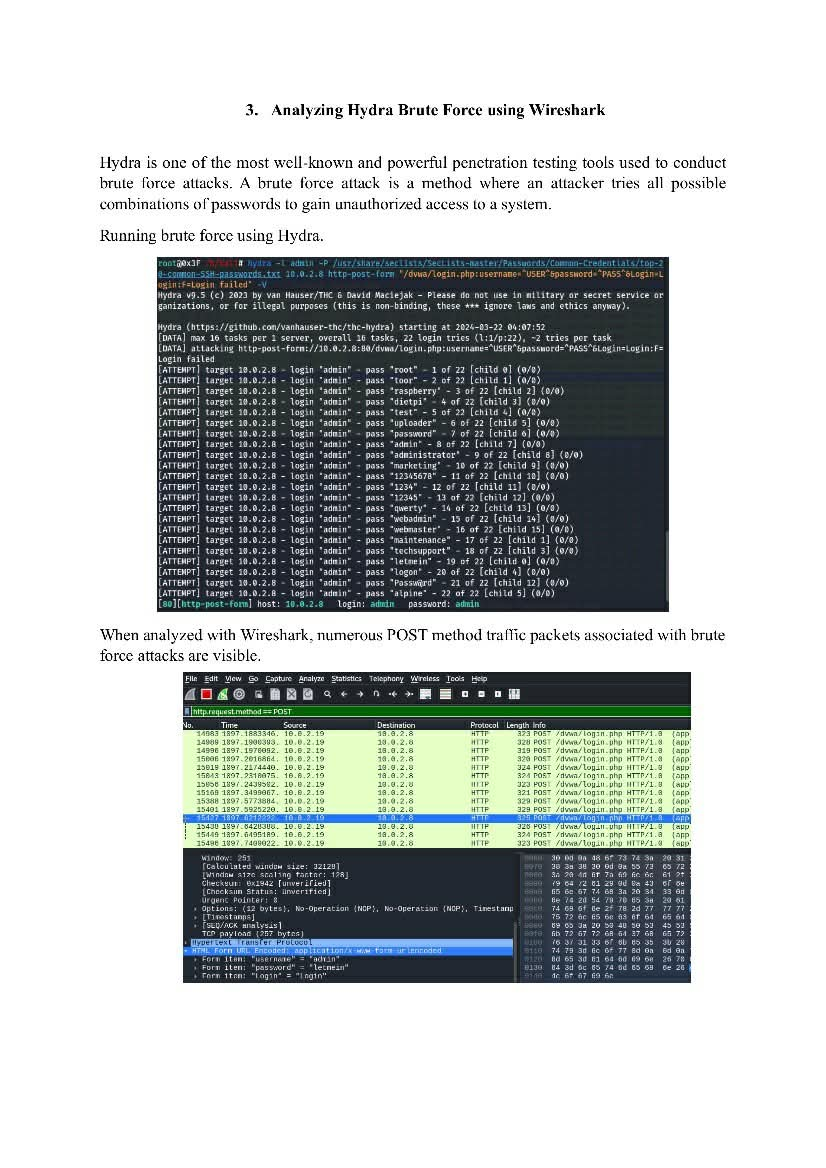
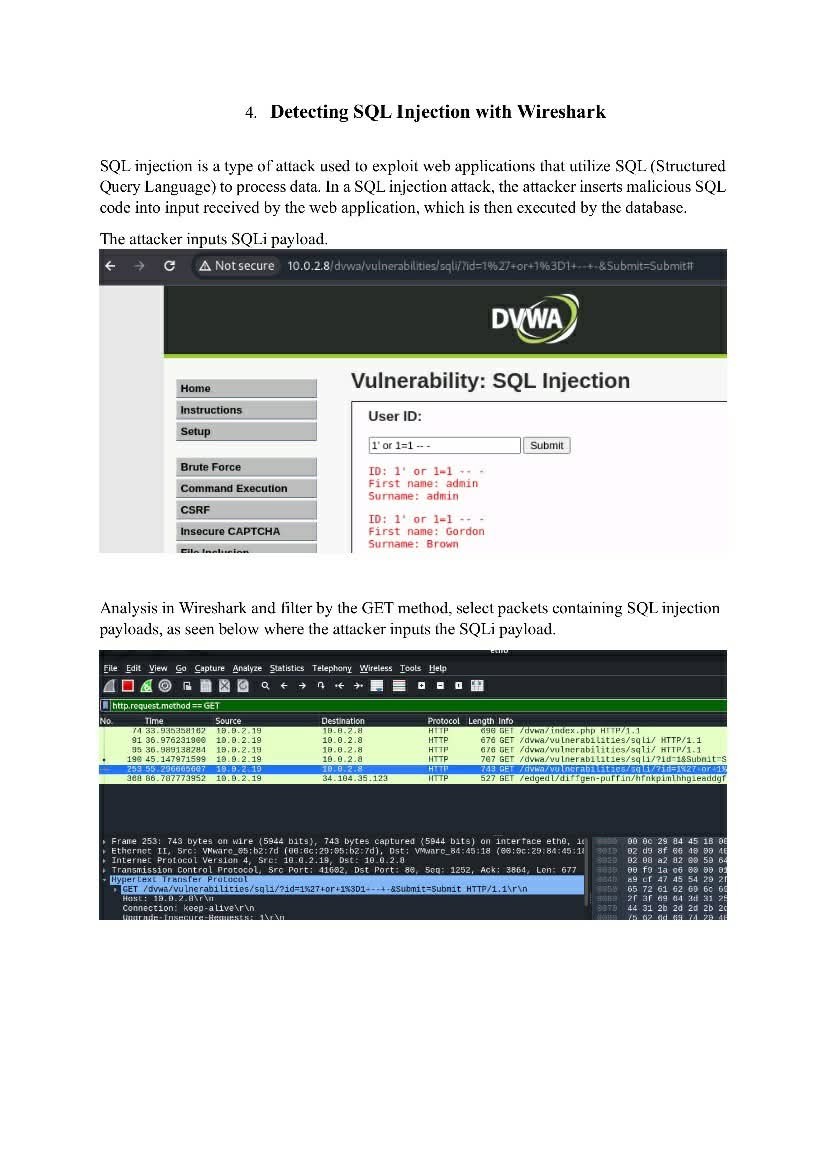
Wireshark Notes 🦈 Quick, essential notes for anyone analyzing network traffic. Perfect for learning packet inspection, spotting anomalies, and improving your network security workflow. 🔖 #Wireshark #NetworkSecurity #PacketAnalysis #CyberSecurity #Infosec #BlueTeam #Pentesting


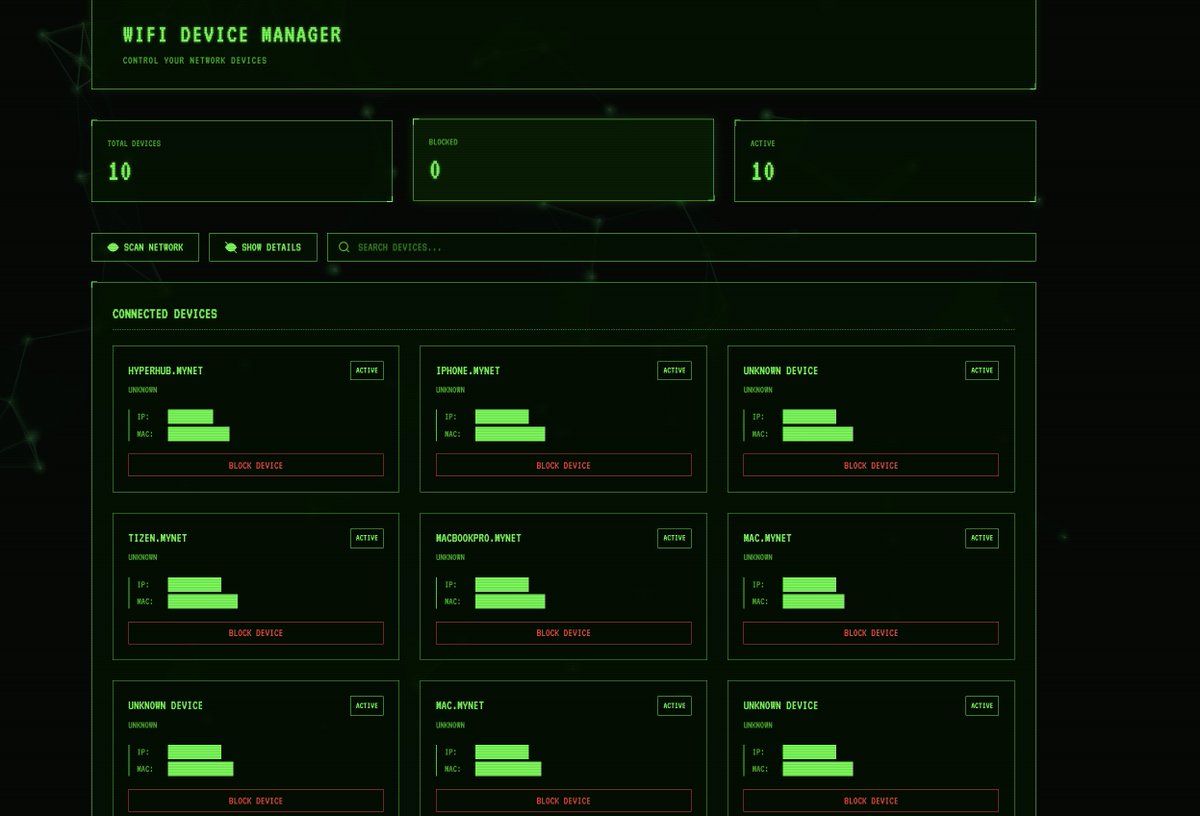
Building out a WiFi device manager with ARP spoofing to block/unblock devices on my network. Managing raw socket permissions and ARP packets in Node.js is tricky as hell #NetworkSecurity #privacy
Thieves cutting overhead cables have seen @Optus stung by yet another network outage, leaving thousands without access to emergency services. #Telecoms #Optus #NetworkSecurity #5GInfrastructure #TripleZero Read more here: buff.ly/DIS0Ixg

JUST CREATED MY FIRST CLUSTER NETWORK ON PACKET TRACER LFFGGG AND GUES WHAT EVERYTHING FUCKING PINGS 😅😅😅. ROAD TO I DON'T EVEN KNOW TO BE HONEST BUT MAYBE ROAD TO CCNA ONE DAY LOL. #CyberSecurity #NetworkSecurity @CiscoNetAcad @OnijeC
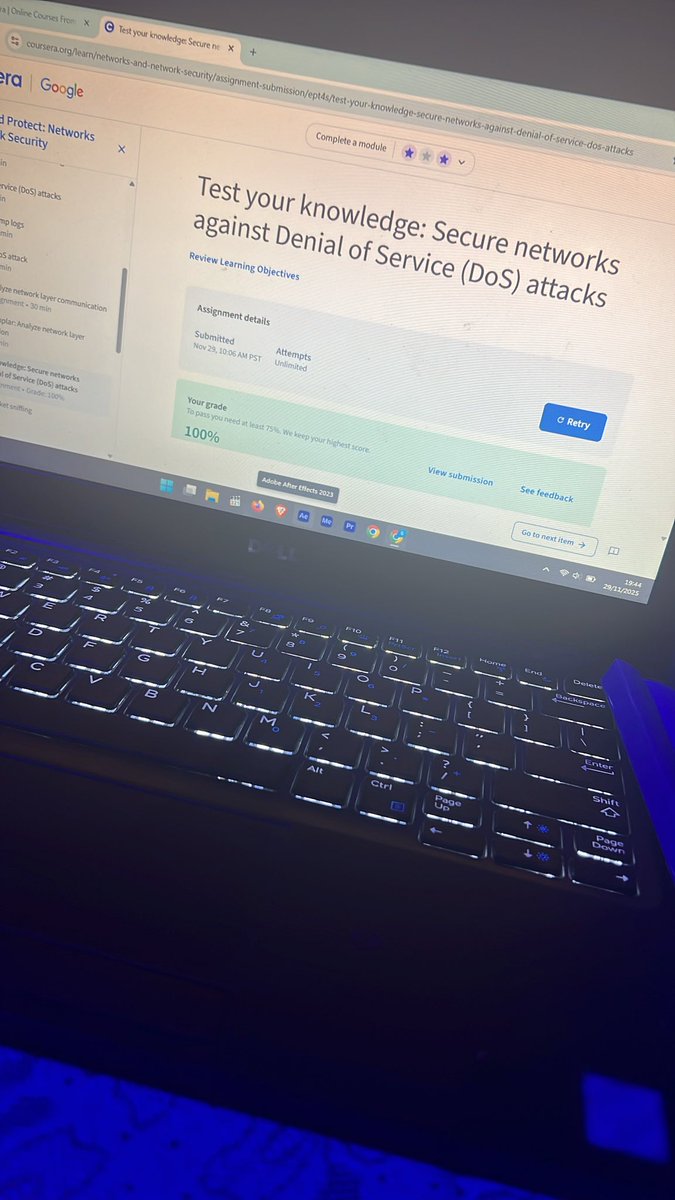
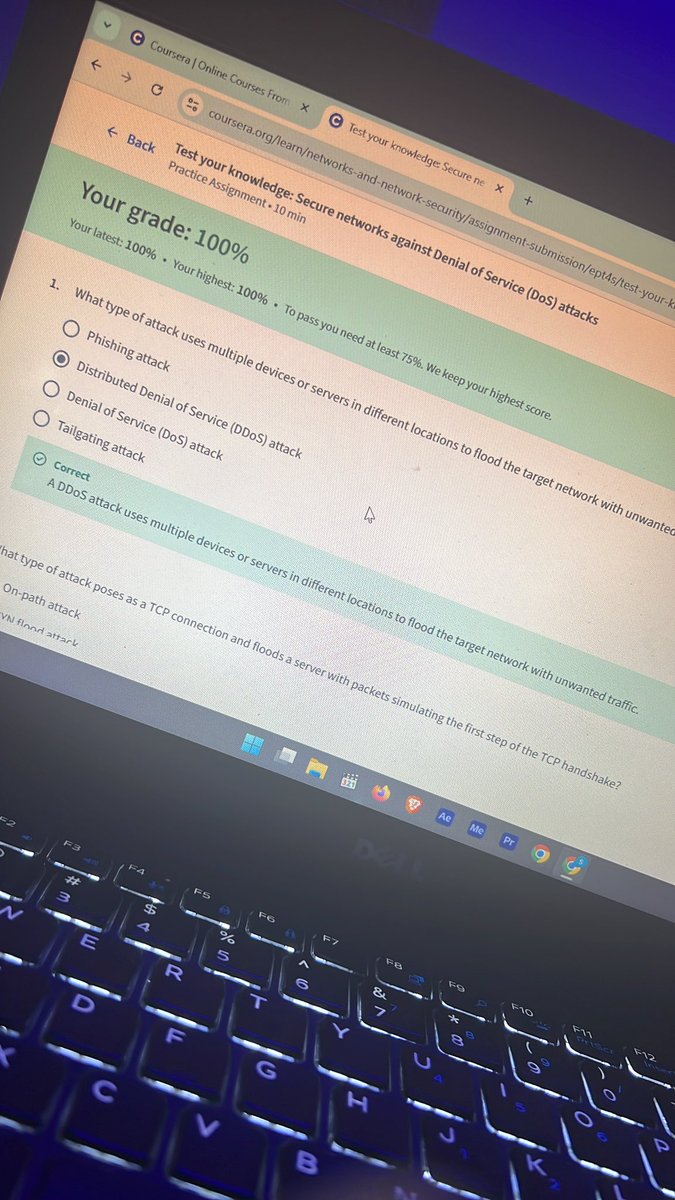
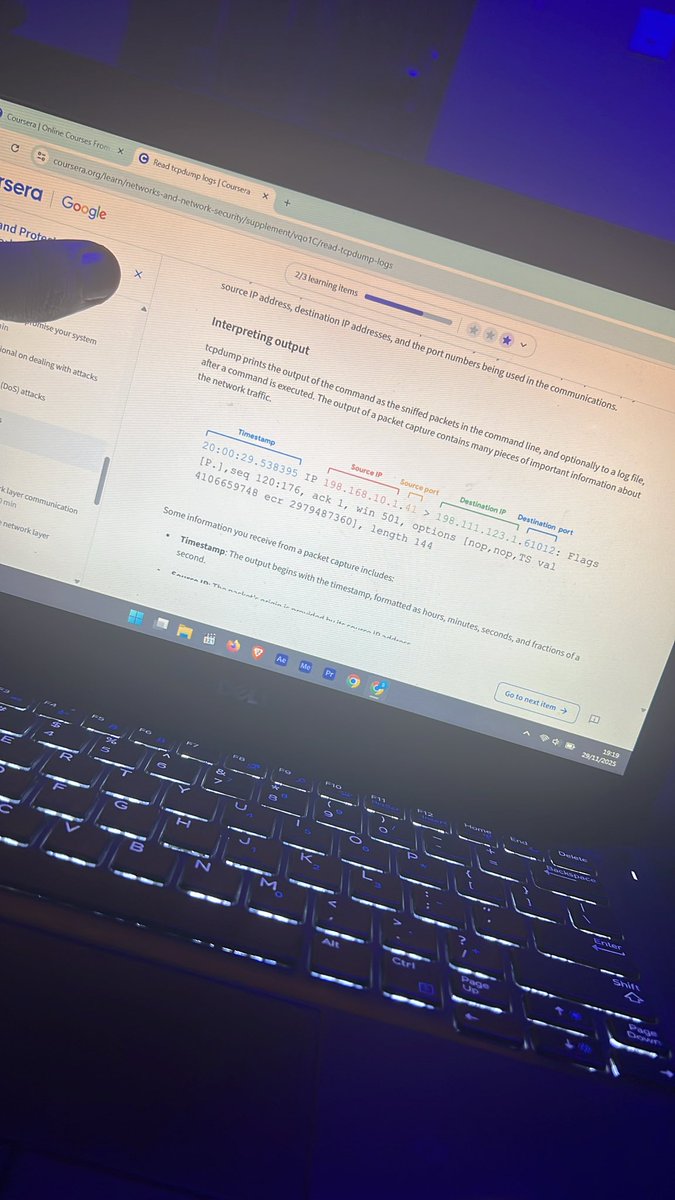
Day 8: Revisiting my previous Coursera course and documenting it. Today I refreshed my knowledge on DoS/DDoS attacks, ICMP floods, packet sniffing (active vs passive), and interpreting packet captures. Staying sharp! 🔐🛡️ #CyberSecurity #NetworkSecurity @OnijeC @segoslavia
📡 When you track Linux server change only superficially you miss the real risk. The article states that file-integrity tools alone aren’t enough to detect system drift and you need deeper state analytics #linux #hacking #NetworkSecurity bit.ly/4i6bgYi

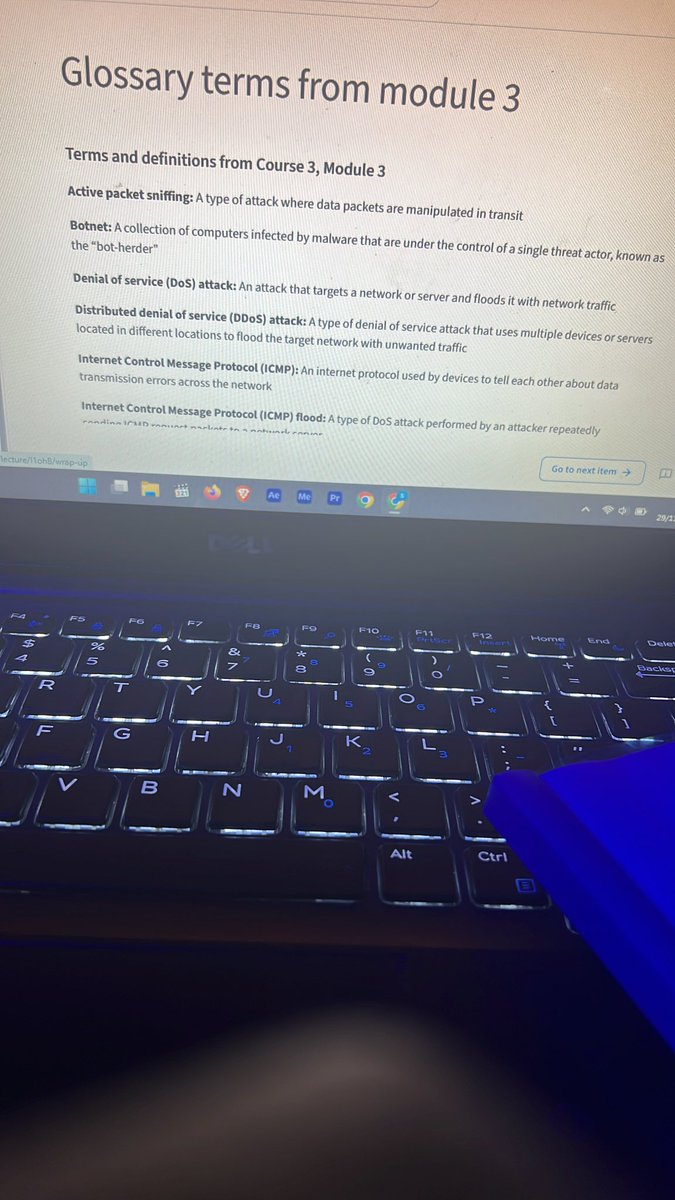
Path inspects every single request at the application level, blocking threats that bypass traditional DDoS protection without slowing down your server. #cybersecurity #NetworkSecurity #technology
Lawmakers Want to Ban VPNsAnd They Have No Idea What They're Doing #law #networksecurity #vpn eff.org/deeplinks/2025…
🔍 Nmap Commands — From Basic to Advanced 🔖 #Nmap #NetworkSecurity #CyberSecurity #InfoSec #Scanning #BlueTeam #EthicalHacking #SecurityTools #NetworkMapping #CyberAwareness




Excited to welcome Hiral Sharma, Manager – Systems Engineering, @Fortinet, as a Speaker at the 19th Digital Transformation Conclave & Awards, 4–5 Dec 2025, Bhubaneswar. 🔗 digitaltransformationconclave.com #DTCOdisha #CyberSecurity #NetworkSecurity #CyberResilience #AIDrivenSecurity

CCNA Cybersecurity Associate: Your security career foundation Master 5 critical domains: Security concepts & monitoring Host-based analysis Network intrusion analysis Security policies & procedures Digital forensics fundamentals bit.ly/47P8mTf #NetworkSecurity

⚠️ Configura la seguridad de tus servidores #WindowsServer para que estén blindados contra ataques DDoS y más. #networksecurity #ciberseguridadparatodos

Modern enterprises depend on networks built for speed, security, and scalability. Learn how to optimize your infrastructure for AI, IoT, and edge performance. ➡️ hubs.li/Q03V-bBG0 #EnterpriseIT #NetworkSecurity #CiscoMeraki

🚨 Cada segundo cuenta cuando ocurre un ataque. La monitorización te permite actuar a tiempo. ⏱️🛡️ #concienciacionciberseguridad #networksecurity

Join us at AISS 2025 as Simarjeet Singh breaks down one of today’s toughest cybersecurity challenges, detecting threats in an increasingly encrypted world. #AISS2025 #Vehere #NetworkSecurity #NetworkDetectionandResponse #EnterpriseSecurity

WatchGuard shines as a Leader in the G2 Grid Report & wins TrustRadius Buyer’s Choice & Top-Rated Awards! User feedback and satisfaction scores highlight the top solutions across various product categories, including #networksecurity & #endpointsecurity buff.ly/n5ekZng

Discover how the YOM token strengthens network security and offers powerful incentives for long-term users! Join the movement now @YOM_Official #NetworkSecurity #Incentives
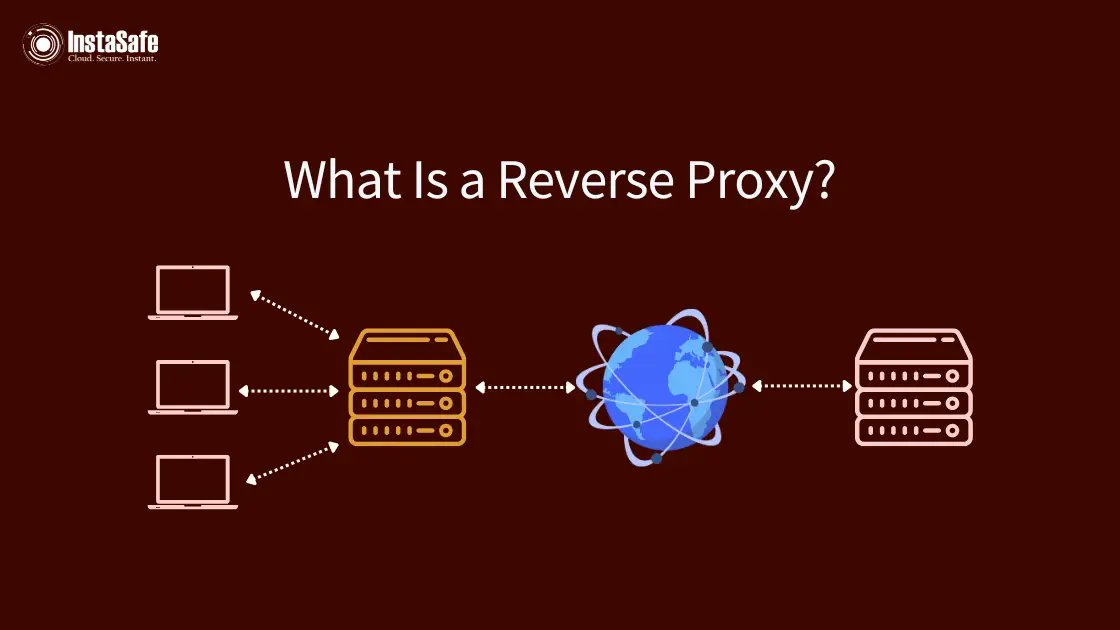
What Is a Reverse Proxy? 🔄 A reverse proxy sits before servers, routing traffic & adding security layers like load balancing and DDoS protection. Explore More:👉zurl.co/lRMGH #ReverseProxy #NetworkSecurity #WebSecurity #CyberSecurity #InstaSafe
Lawmakers Want to Ban VPNsAnd They Have No Idea What They're Doing #law #networksecurity #vpn eff.org/deeplinks/2025…
Protect your business from cyber threats with expert network security. 24/7 monitoring, +61 435 660 644 ✉ [email protected] 📧 #NetworkSecurity #CyberProtection #ITSupport #DataSafety #FirewallSecurity #CyberAttackPrevention simplypostit.com.au/listing/advanc…
Excited to welcome Hiral Sharma, Manager – Systems Engineering, @Fortinet, as a Speaker at the 19th Digital Transformation Conclave & Awards, 4–5 Dec 2025, Bhubaneswar. 🔗 digitaltransformationconclave.com #DTCOdisha #CyberSecurity #NetworkSecurity #CyberResilience #AIDrivenSecurity

Discover how the YOM token boosts network security and rewards long-term operators! Join the movement now. Stay secure, stay rewarded! @YOM_Official #NetworkSecurity #IncentiveMechanism
Your network isn’t only threatened by hackers — it’s threatened by simple mistakes. Weak passwords, missed updates, unchecked access… one small error can expose everything. Prevention starts with awareness — & the right IT partner. #CESTech #Cybersecurity #NetworkSecurity

Understanding Network-Based Cyber Attacks and How to Prevent Them bit.ly/4pc9VBR #NetworkSecurity #CyberAttacks #CyberDefense #NetworkProtection #ThreatPrevention #CyberAwareness #InfoSec #SecurityBestPractices #DigitalSecurity #CyberRiskManagement #TechUnity

6 Ways Network Security Protects Industrial Automation bit.ly/4anEeRw #IndustrialSecurity #NetworkSecurity #AutomationSafety #OTSecurity #ICSProtection #SecureAutomation #CyberIndustrial #IndustrialCybersecurity #CriticalInfrastructureSecurity #TechUnity

Understanding the distinction between VPN types is key for organizational security. Business VPNs provide centralized administration, enabling IT teams to manage user access and enforce security policies #BusinessVPN #NetworkSecurity Read more 👉 lttr.ai/AksWU

The most dangerous cyberattacks start with silence, not packets Connect with us : linktr.ee/bervice Website : bervice.com Website : blog.bervice.com #Bervice #Cybersecurity #NetworkSecurity #PassiveReconnaissance #CyberThreats #InfoSec #AdvancedAttacks
Modern enterprises depend on networks built for speed, security, and scalability. Learn how to optimize your infrastructure for AI, IoT, and edge performance. ➡️ hubs.li/Q03V-bBG0 #EnterpriseIT #NetworkSecurity #CiscoMeraki

⚠️ Configura la seguridad de tus servidores #WindowsServer para que estén blindados contra ataques DDoS y más. #networksecurity #ciberseguridadparatodos

Wireshark Notes 🦈 Quick, essential notes for anyone analyzing network traffic. Perfect for learning packet inspection, spotting anomalies, and improving your network security workflow. 🔖 #Wireshark #NetworkSecurity #PacketAnalysis #CyberSecurity #Infosec #BlueTeam #Pentesting




Thieves cutting overhead cables have seen @Optus stung by yet another network outage, leaving thousands without access to emergency services. #Telecoms #Optus #NetworkSecurity #5GInfrastructure #TripleZero Read more here: buff.ly/DIS0Ixg

Path inspects every single request at the application level, blocking threats that bypass traditional DDoS protection without slowing down your server. #cybersecurity #NetworkSecurity #technology

Your organization’s safety starts with everyday decisions. Small habits create strong defenses. Let’s rethink how we protect what matters. #CyberSecurity #NetworkSecurity #Infosec #DataProtection #Malware




CCNA Cybersecurity Associate: Your security career foundation Master 5 critical domains: Security concepts & monitoring Host-based analysis Network intrusion analysis Security policies & procedures Digital forensics fundamentals bit.ly/43fpNe7 #NetworkSecurity

🚨 Cada segundo cuenta cuando ocurre un ataque. La monitorización te permite actuar a tiempo. ⏱️🛡️ #concienciacionciberseguridad #networksecurity

Building out a WiFi device manager with ARP spoofing to block/unblock devices on my network. Managing raw socket permissions and ARP packets in Node.js is tricky as hell #NetworkSecurity #privacy

Get security that scales with your platform. We take care of the audit and the implementation. Book a quick consultation. #NetworkSecurity #PathNetwork #CyberResilience

Firewall compliance used to be a bottleneck. Now it’s a strength. See how FireMon helped a global financial institution simplify, automate, and scale without slowing down. Explore the full story: ow.ly/mIk450XowI2 #FireMon #NetworkSecurity #ComplianceAutomation

Day 8: Revisiting my previous Coursera course and documenting it. Today I refreshed my knowledge on DoS/DDoS attacks, ICMP floods, packet sniffing (active vs passive), and interpreting packet captures. Staying sharp! 🔐🛡️ #CyberSecurity #NetworkSecurity @OnijeC @segoslavia




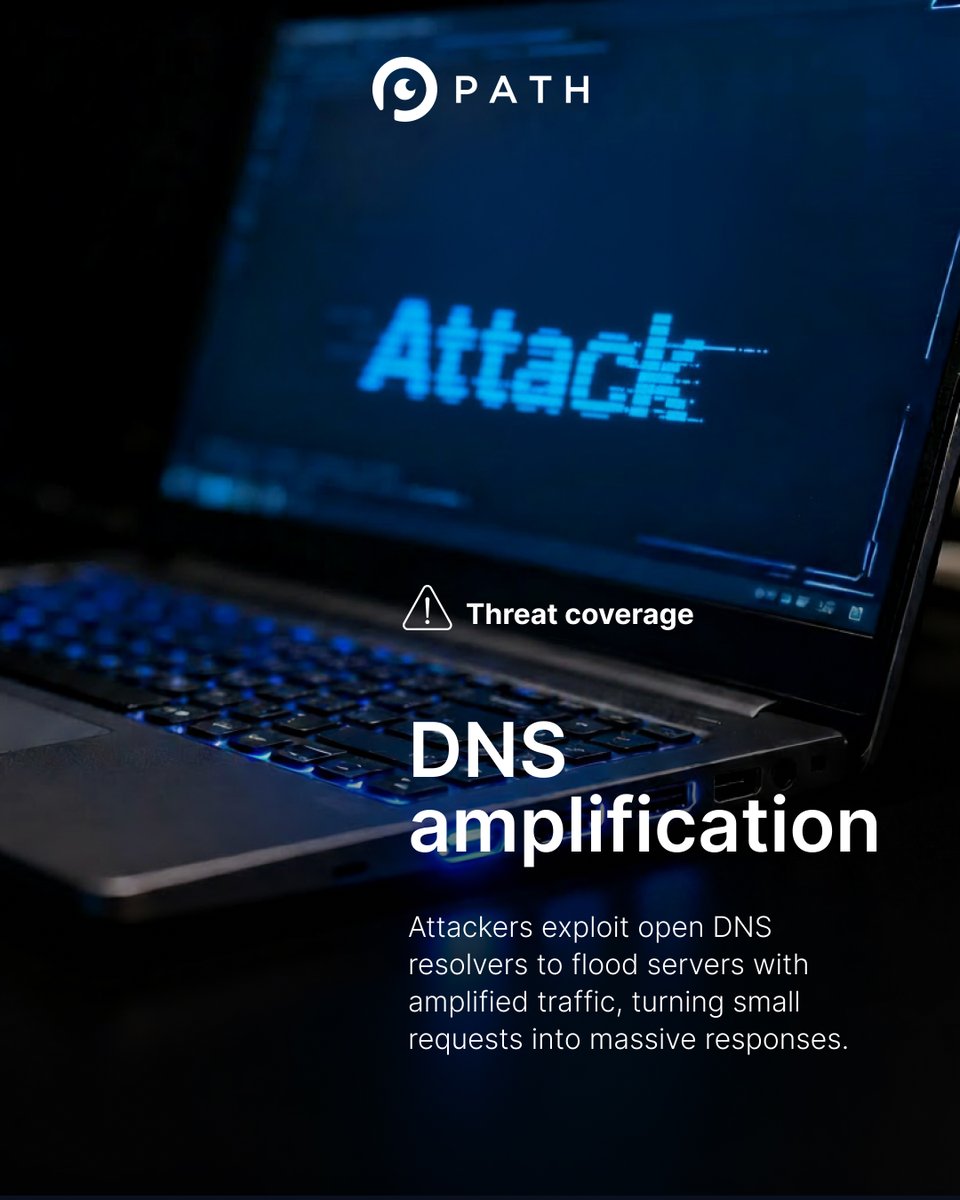
DNS amplification attacks are efficient - for attackers. By abusing open resolvers, they multiply small requests into huge traffic waves that overwhelm targets. Path Network’s real-time DNS filtering detects and stops these floods before they take shape. #NetworkSecurity
For FREE Help Designing A Custom #Cybersecurity Strategy/Framework For Your Organization Simply Ask Here=> ds3-bandwidth.com/quote-request/ #CISO #NetworkSecurity @Nicochan33 @ChuckDBrooks @harshleenchawl2 @cybergeekgirl @BillMew @CaffSec @cybervizer @CISOWaterCooler @mclynd @Corix_JC

🔍 Nmap Commands — From Basic to Advanced 🔖 #Nmap #NetworkSecurity #CyberSecurity #InfoSec #Scanning #BlueTeam #EthicalHacking #SecurityTools #NetworkMapping #CyberAwareness




Network security doesn't have a final boss. It’s an infinite game. Start your mission today: ow.ly/oYEK50XusKh #FireMon #NetworkSecurity #Cybersecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. #GivingTuesday 14.8K posts
- 2. The BIGGЕST 426K posts
- 3. #JUPITER 233K posts
- 4. #ALLOCATION 233K posts
- 5. #csm222 N/A
- 6. Lucario 13.8K posts
- 7. Costco 38K posts
- 8. #NXXT_NEWS N/A
- 9. Good Tuesday 38.9K posts
- 10. NextNRG Inc 1,194 posts
- 11. Susan Dell 2,339 posts
- 12. Michael and Susan 1,616 posts
- 13. Taco Tuesday 13.4K posts
- 14. Trump Accounts 7,522 posts
- 15. Hoss Cartwright N/A
- 16. King Von 1,086 posts
- 17. Dart 42.9K posts
- 18. Project M 22.2K posts
- 19. Kanata 29.4K posts
- 20. Mainz Biomed N.V. N/A