#hackwithautomation search results
Detect Sitecore RCE (CVE-2024-46938) with Nuclei 🚀 🔹 Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… by @DhiyaneshDK 🔹 Research: assetnote.io/resources/rese… by @assetnote #hackwithautomation #Cybersecurity #AppSec #BugBounty

How to extract a list of enpoints from JS files with katana! 👇 #hacking #cybersecurity #hackwithautomation #bugbounty

🚨 Scan for PHP CGI Argument Injection vulnerability (CVE-2024-4577) discovered by @orange_8361 using Nuclei templates! 🔍 Details: devco.re/blog/2024/06/0… 📑 Nuclei Template: cloud.projectdiscovery.io/public/CVE-202… 🔧 GitHub PR: github.com/projectdiscove… #hackwithautomation #bugbounty #appsec

How to extract subdomains from an ASN using dnsx! ⌨️ echo <ANS> | dnsx -silent -ro -ptr (🔗 link to dnsx in the comments) #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
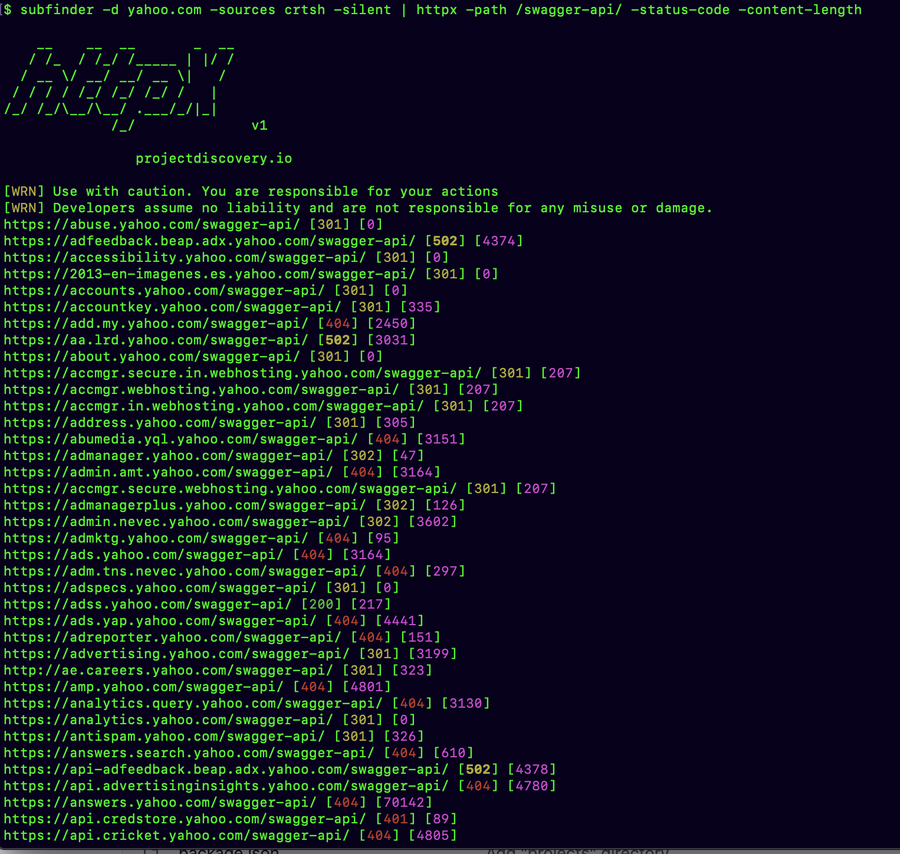
You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. httpx -path /swagger-api/ -status-code -content-length credit:@pdnuclei #hackwithautomation #recon #bugbountytips #infosec
🚨 Scanning Ivanti Cloud Services Appliance - Path Traversal (CVE-2024-8963) Using Nuclei detect it fast and keep your assets secure! 🔍 Template : cloud.projectdiscovery.io/?template=CVE-… Reference: fortinet.com/blog/threat-re… #ivanti #kev #hackwithautomation @pdnuclei

How to query all DNS records for single host using dnsx 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

🥳🥳🥳With @pdiscoveryio/Uncover, now easily search for exposed assets through HUNTER.HOW API github.com/projectdiscove… THX @xm1k3_ #hackwithautomation #recon #assetdiscovery #security #bugbounty #bugbountytips #infosecurity #infosec

Have you tried using the ✨OSINT✨ templates yet? Here's how you would look for OSINT regarding the username "johnsmith" 🕵️ ⚛️ nuclei -tags osint -var user=johnsmith #nuclei101 #hackwithautomation #opensource

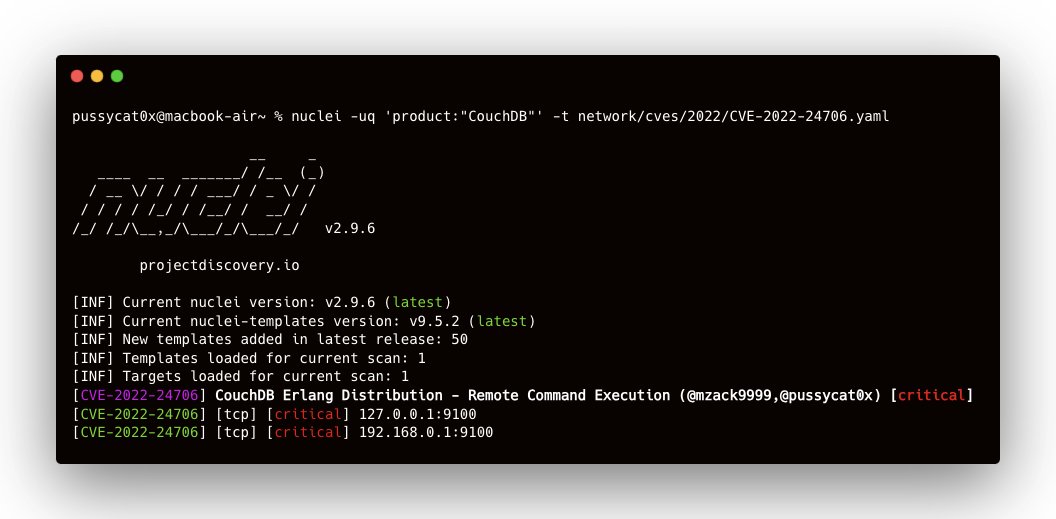
CouchDB Erlang Distribution - Remote Command Execution(CVE-2022-24706) CRITICAL 🚨 nuclei -t /network/cves/2022/CVE-2022-24706.yaml -l ips.txt @pdnuclei Link: github.com/projectdiscove… Follow the thread to see how the template created 😼 #hackwithautomation #pdteam #nuclei
Scan for CVE-2024-47176 (CUPS - Remote Code Execution) with Nuclei Vulnerability discovery and analysis by @evilsocket: evilsocket.net/2024/09/26/Att… Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… #hackwithautomation #cybersecurity #bugbounty

Discover how ProjectDiscovery can modernize your approach to vulnerability management. 🌀 Streamline vulnerability detection and recon 🌀 Cut noise and scale security workflows 🌀 Automate your remediation process Request a demo: projectdiscovery.io/request-demo #hackwithautomation…

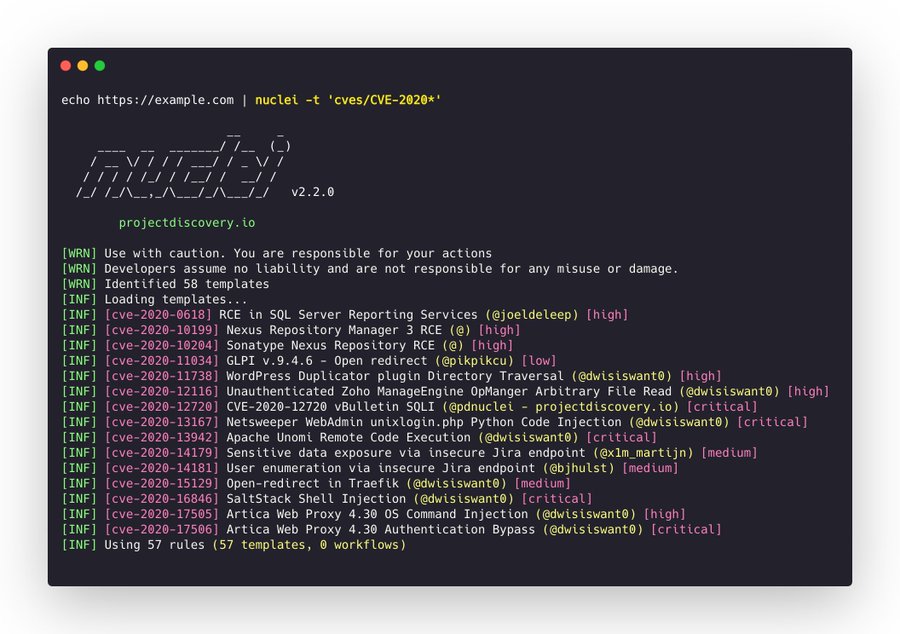
Using wildcard glob support in nuclei, you can quickly scan for CVEs of specific years, for example, 𝗻𝘂𝗰𝗹𝗲𝗶 -𝘁 '𝗰𝘃𝗲𝘀/𝗖𝗩𝗘-𝟮𝟬𝟮𝟬*' will scan for all the CVEs assigned in 2020 from nuclei templates project. credit:@pdnuclei #nucleitips #hackwithautomation
🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH] Nuclei Template : github.com/projectdiscove… @pdnuclei #hackwithautomation #bugbounty #cve2023 #Ivanti
![DhiyaneshDK's tweet image. 🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH]
Nuclei Template : github.com/projectdiscove… @pdnuclei
#hackwithautomation #bugbounty #cve2023 #Ivanti](https://pbs.twimg.com/media/GFZpBpeWoAAE8fI.jpg)
CVE-2023-26469 - Jorani 1.0.0 - Remote Code Execution 💣 Shodan: http.favicon.hash:-2032163853 Nuclei Template:- github.com/projectdiscove… @pdnuclei Reference: github.com/Orange-Cyberde… Follow this thread to see How this Template made? #hackwithautomation #pdteam #cve2023

⚡You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. ✅httpx -path /swagger-api/ -status-code -content-length 👉Credit:@pdnuclei #hackwithautomation #recon #bugbountytips…

🚨 Scanning Ivanti Cloud Services Appliance - Path Traversal (CVE-2024-8963) Using Nuclei Template shared by johnk3r 🔍 Template : cloud.projectdiscovery.io/?template=CVE-… #ivanti #kev #hackwithautomation

Not sure what nuclei template you need? Just ask -ai! 🤖 All you need to do is briefly explain what you want to do and it will find the templates you need! 🤩 Check it out 👇 #hackwithautomation #nuclei #cybersecurity
How to extract subdomains from an ASN using dnsx! ⌨️ echo <ANS> | dnsx -silent -ro -ptr (🔗 link to dnsx in the comments) #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
How to extract a list of enpoints from JS files with katana! 👇 #hacking #cybersecurity #hackwithautomation #bugbounty

How to query all DNS records for single host using dnsx 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Discover how ProjectDiscovery can modernize your approach to vulnerability management. 🌀 Streamline vulnerability detection and recon 🌀 Cut noise and scale security workflows 🌀 Automate your remediation process Request a demo: projectdiscovery.io/request-demo #hackwithautomation…

If you like our open source tools, you'll LOVE our platform! It's all our tools AND MORE in one place! 🚀 Enter your domain for a free vulnerability scan today: projectdiscovery.io #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Not sure what nuclei template you need? Just ask -ai! 🤖 All you need to do is briefly explain what you want to do and it will find the templates you need! 🤩 Check it out 👇 #hackwithautomation #nuclei #cybersecurity
WE'RE AT @BlackHatEvents USA 2025! Come and find the ProjectDiscovery team at booth #6826! You won't regret it. #BHUSA #BHUSA25 #hackwithautomation #hacking #cybersecurity

How to display the HTTP status codes and titles for a list of targets with httpx and the -sc and -title flags 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

What's new with ProjectDiscovery Cloud Platform? Here's what you need to know about v.1.3.0 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource
How to use httpx and the -path flag to check for juicy paths 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

How to get a list of CIDR ranges associated with an organization using ASNmap! This simple command yields 377 CIDRs associated with a target. That's equivalent to more than 2.3 million IP addresses! 😮 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Did you know you can use our cloud platform to get a list of all the active assets related to a domain? Just add your domain to "cloud.projectdiscovery.io/assets/domain/<domain>" and you're good to go! And it's totally free! Check out all the data you can get 👇 #hackwithautomation…
Did you know you can scan UDP ports with naabu? Here's how 👇 #opensource #hackwithautomation #naabu #portscanning #hacking

How to get subdomains, validate DNS, and probe with httpx - all in JSON! This one-liner is a great start to your automation and the best thing is, all the output is saved in JSON so it captures and saves ALL of the output from each tool. Try this 👇 #hackwithautomation…

How to use Katana to find and crawl any robots.txt or sitemap.xml files that are present. 🚀 katana -u tesla.com -kf robotstxt,sitemapxml NOTE: This functionality is turned off by default. #katana #hackwithautomation #crawl

Did you know you can set Proxify as an upstream proxy? Here's how you do it! 👇 Check out the change of User-Agent once the request is forwarded from Burp Suite to Proxify to the web server. #proxify #burpsuite #hackwithautomation
🚨 New Critical CVE Alert: CVE-2025-31324 🚨 Scan for SAP NetWeaver Metadata Uploader - Unauthenticated Deserialization using @pdnuclei 🔗 Detection templates in comment 👇 #hackwithautomation #sap #infosec

🚀 Day 4 of Launch Week @pdiscoveryio Our free AI-powered Nuclei Template Editor is here! Convert vulnerability reports into automatable tests via UI & @pdnuclei CLI. #Cybersecurity #Infosec #hackwithautomation
🚨 Scan for PHP CGI Argument Injection vulnerability (CVE-2024-4577) discovered by @orange_8361 using Nuclei templates! 🔍 Details: devco.re/blog/2024/06/0… 📑 Nuclei Template: cloud.projectdiscovery.io/public/CVE-202… 🔧 GitHub PR: github.com/projectdiscove… #hackwithautomation #bugbounty #appsec

CouchDB Erlang Distribution - Remote Command Execution(CVE-2022-24706) CRITICAL 🚨 nuclei -t /network/cves/2022/CVE-2022-24706.yaml -l ips.txt @pdnuclei Link: github.com/projectdiscove… Follow the thread to see how the template created 😼 #hackwithautomation #pdteam #nuclei

Detect Sitecore RCE (CVE-2024-46938) with Nuclei 🚀 🔹 Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… by @DhiyaneshDK 🔹 Research: assetnote.io/resources/rese… by @assetnote #hackwithautomation #Cybersecurity #AppSec #BugBounty

CVE-2023-26469 - Jorani 1.0.0 - Remote Code Execution 💣 Shodan: http.favicon.hash:-2032163853 Nuclei Template:- github.com/projectdiscove… @pdnuclei Reference: github.com/Orange-Cyberde… Follow this thread to see How this Template made? #hackwithautomation #pdteam #cve2023

🥳🥳🥳With @pdiscoveryio/Uncover, now easily search for exposed assets through HUNTER.HOW API github.com/projectdiscove… THX @xm1k3_ #hackwithautomation #recon #assetdiscovery #security #bugbounty #bugbountytips #infosecurity #infosec

🚨 Scanning Ivanti Cloud Services Appliance - Path Traversal (CVE-2024-8963) Using Nuclei detect it fast and keep your assets secure! 🔍 Template : cloud.projectdiscovery.io/?template=CVE-… Reference: fortinet.com/blog/threat-re… #ivanti #kev #hackwithautomation @pdnuclei

Scan for CVE-2024-47176 (CUPS - Remote Code Execution) with Nuclei Vulnerability discovery and analysis by @evilsocket: evilsocket.net/2024/09/26/Att… Nuclei Template: cloud.projectdiscovery.io/?template=CVE-… #hackwithautomation #cybersecurity #bugbounty

🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH] Nuclei Template : github.com/projectdiscove… @pdnuclei #hackwithautomation #bugbounty #cve2023 #Ivanti
![DhiyaneshDK's tweet image. 🚨 CVE-2024-21893 - Ivanti SAML - Server Side Request Forgery (SSRF) - [HIGH]
Nuclei Template : github.com/projectdiscove… @pdnuclei
#hackwithautomation #bugbounty #cve2023 #Ivanti](https://pbs.twimg.com/media/GFZpBpeWoAAE8fI.jpg)
How to extract a list of enpoints from JS files with katana! 👇 #hacking #cybersecurity #hackwithautomation #bugbounty

How to query all DNS records for single host using dnsx 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Scan for latest CVE-2023-47246 (SysAid Server - Remote Code Execution) using nuclei templates Template: github.com/projectdiscove… Advisory: sysaid.com/blog/service-d… #hackwithautomation #appsec #bugbounty #cybersecurity

Detect CyberPanel RCE with Nuclei 🚀 🔹 Template: cloud.projectdiscovery.io/?template=cybe… 🔹 Research by @dreyand_: dreyand.rs/code/review/20… #hackwithautomation #BugBounty #Cybersecurity

You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. httpx -path /swagger-api/ -status-code -content-length credit:@pdnuclei #hackwithautomation #recon #bugbountytips #infosec

⚡You can use #httpx to request any path and see the status code and other details on the go, filter, or matcher flags if you want to be more specific. ✅httpx -path /swagger-api/ -status-code -content-length 👉Credit:@pdnuclei #hackwithautomation #recon #bugbountytips…

Check out the latest blog - Azure Config Review - Nuclei Templates v10.0.0 🎉 - from ProjectDiscovery! buff.ly/4djspdf #hackwithautomation #opensource #bugbounty #appsec #security

🚨 Scanning Ivanti Cloud Services Appliance - Path Traversal (CVE-2024-8963) Using Nuclei Template shared by johnk3r 🔍 Template : cloud.projectdiscovery.io/?template=CVE-… #ivanti #kev #hackwithautomation

How to use httpx and the -path flag to check for juicy paths 👇 #hackwithautomation #cybersecurity #hacking #bugbounty #opensource

Have you tried using the ✨OSINT✨ templates yet? Here's how you would look for OSINT regarding the username "johnsmith" 🕵️ ⚛️ nuclei -tags osint -var user=johnsmith #nuclei101 #hackwithautomation #opensource

Detect CVE-2024-24919 using nuclei templates shared by @johnk3r Shared Template URL - cloud.projectdiscovery.io/@sandeep/TXzmK… #hackwithautomation #appsec #bugbounty #cybersecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. #CARTMANCOIN 1,567 posts
- 2. Broncos 64.5K posts
- 3. Broncos 64.5K posts
- 4. yeonjun 189K posts
- 5. Bo Nix 17.8K posts
- 6. Geno 18.1K posts
- 7. $SMILEY N/A
- 8. Sean Payton 4,681 posts
- 9. Kenny Pickett 1,501 posts
- 10. daniela 38.2K posts
- 11. #TNFonPrime 3,971 posts
- 12. #criticalrolespoilers 4,641 posts
- 13. Chip Kelly 1,945 posts
- 14. Bradley Beal 3,385 posts
- 15. Jalen Green 7,133 posts
- 16. TALK TO YOU OUT NOW 25K posts
- 17. Pete Carroll 1,912 posts
- 18. Kehlani 8,919 posts
- 19. Jeanty 6,480 posts
- 20. Troy Franklin 2,402 posts