Smilehacker
@_smile_hacker_
Founder @sudarshana_io | Ex- HackerOne |
Może Ci się spodobać
Don’t Miss the New Video! 🔥 - How I Found a $500 Bug Bounty + AI Recon Tips! youtu.be/kmm1Y_QZqjY?si…

Is this a coincidence? First AWS Second Azure Third Cloudflare
Decorations in Sydney, Australia 🔥
❄️[New Video] - The Most Overlooked Bug in Web Apps: HTTP Request Smuggling (Deep Dive) (P.S. Only Real Wannabe Hackers can Watch it) youtu.be/6Zck1649AP0
![medusa_0xf's tweet image. ❄️[New Video] - The Most Overlooked Bug in Web Apps: HTTP Request Smuggling (Deep Dive)
(P.S. Only Real Wannabe Hackers can Watch it)
youtu.be/6Zck1649AP0](https://pbs.twimg.com/media/G3ZtDsgWIAAdq_U.jpg)
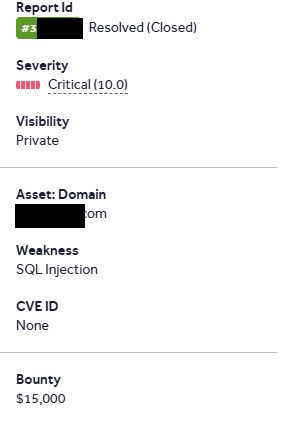
We earned a $15,000 bounty on @Hacker0x01 with @saur1n! His persistence on the target paid off, uncovering SQLi leads on a major social network. The exploit was straightforward once the query structure leaked due to verbose errors, revealing the injection point by commenting.…
Post a picture YOU took. Just a pic. No description.

app.intigriti.com/profile/smileh… This looks cool, good work @intigriti
app.intigriti.com
smilehacker - Intigriti
Intigriti offers bug bounty and agile penetration testing solutions powered by Europe's #1 leading network of ethical hackers.
a new write-up on how to pentest NextJs framework apps Enjoy #security_tips_with_daoud deepstrike.io/blog/nextjs-se…
i was looking at an app this morning with @xssdoctor and we figured out something really neat. if you have a CSRF you can't exploit due to sec-fetch-site, you can use desktop apps (like electron apps or iMessage, etc) b/c they set sec-fetch-site to none which can be a bypass
🔥
We just published a new quick read on how we performed LFI via XSS in a PDF generator. #BugBounty #bugbountytips #hackerone #bugcrowd #cybersecurity blog.sudarshana.io/blog/local-fil…
United States Trendy
- 1. Caleb Love 2,457 posts
- 2. Sengun 8,512 posts
- 3. Mamdani 444K posts
- 4. Reed Sheppard 3,642 posts
- 5. Norvell 3,461 posts
- 6. #SmackDown 45K posts
- 7. Suns 18.6K posts
- 8. Marjorie Taylor Greene 65.7K posts
- 9. Lando 43K posts
- 10. Collin Gillespie 3,643 posts
- 11. Morgan Geekie N/A
- 12. UNLV 2,126 posts
- 13. Rockets 16.6K posts
- 14. Florida State 10.8K posts
- 15. Blazers 3,790 posts
- 16. NC State 5,803 posts
- 17. Wolves 16.5K posts
- 18. #OPLive 2,557 posts
- 19. #LasVegasGP 68K posts
- 20. The View 97.1K posts
Może Ci się spodobać
-
 Vegeta
Vegeta
@_justYnot -
 Udit Bhadauria
Udit Bhadauria
@udit_thakkur -
 Aman Mahendra
Aman Mahendra
@amanmahendra_ -
 Ved Parkash
Ved Parkash
@v3d_bug -
 Sourav
Sourav
@souravbaghz -
 Deepak Dhiman🇮🇳
Deepak Dhiman🇮🇳
@Virdoex_hunter -
 Aditya sharma 🇮🇳
Aditya sharma 🇮🇳
@Assass1nmarcos -
 Avanish Pathak
Avanish Pathak
@avanish46 -
 ~Ankit Tiwari
~Ankit Tiwari
@Debian_Hunter -
 Debangshu 🇮🇳🥷
Debangshu 🇮🇳🥷
@ThisIsDK999 -
 Sayaan Alam
Sayaan Alam
@ehsayaan -
 Sharik Khan
Sharik Khan
@4non_Hunter -
 StarKrish
StarKrish
@PD_5ive -
 Rajesh 🇮🇳
Rajesh 🇮🇳
@_rajesh_ranjan_ -
 Prateek Thakare 🇮🇳
Prateek Thakare 🇮🇳
@thakare_prateek
Something went wrong.
Something went wrong.