Smilehacker
@_smile_hacker_
Full-time Bug Bounty hunter | Founder @sudarshana_io | Ex- HackerOne |
你可能會喜歡
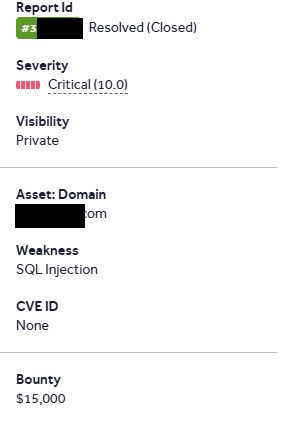
We earned a $15,000 bounty on @Hacker0x01 with @saur1n! His persistence on the target paid off, uncovering SQLi leads on a major social network. The exploit was straightforward once the query structure leaked due to verbose errors, revealing the injection point by commenting.…
Post a picture YOU took. Just a pic. No description.

a new write-up on how to pentest NextJs framework apps Enjoy #security_tips_with_daoud deepstrike.io/blog/nextjs-se…
i was looking at an app this morning with @xssdoctor and we figured out something really neat. if you have a CSRF you can't exploit due to sec-fetch-site, you can use desktop apps (like electron apps or iMessage, etc) b/c they set sec-fetch-site to none which can be a bypass
🔥
We just published a new quick read on how we performed LFI via XSS in a PDF generator. #BugBounty #bugbountytips #hackerone #bugcrowd #cybersecurity blog.sudarshana.io/blog/local-fil…
Crazyyy!
Xbow raised $117M to build AI hacker agents, in @AliasRobotics open-sourced it and made it completely free. Github: github.com/aliasrobotics/… Paper: arxiv.org/abs/2504.06017
‼️ My New Video covers how you can find API keys for AWS, OpenAI, secret keys, etc., as well as how you can discover new subdomains and leaked credentials. Must Watch! youtu.be/xz_jeBxTJ58?si…

youtube.com
YouTube
Bug Bounty Tip: Advanced GitHub Dorking for Maximum Results!
During a recent pentest, the target had an SQL injection vulnerability but was behind a WAF. Standard payloads using LIKE, =, IN, etc., were blocked, preventing exploitation. As the target used PostgreSQL, I bypassed this using the ~ operator, unique to PostgreSQL. The…
Now you can listen to my "Snake Bytes" Podcast on @Spotify ✨ Don't forget to follow 💚 #infosec #hacking open.spotify.com/episode/0zdcrD…

Using @Sudarshana_io ASM, me and @VirenPawar_ got rewarded $20000 Bounty in July on @Hacker0x01 #hackerone #BugBounty💪


United States 趨勢
- 1. Chiefs 107K posts
- 2. Branch 32.6K posts
- 3. Mahomes 32.7K posts
- 4. #TNABoundForGlory 54.1K posts
- 5. #LoveCabin 1,105 posts
- 6. #LaGranjaVIP 65.6K posts
- 7. LaPorta 10.5K posts
- 8. Bryce Miller 4,412 posts
- 9. Red Cross 34.8K posts
- 10. Binance DEX 5,066 posts
- 11. Goff 13.6K posts
- 12. Rod Wave 1,168 posts
- 13. Dan Campbell 3,792 posts
- 14. Kelce 16.4K posts
- 15. #OnePride 6,371 posts
- 16. Butker 8,462 posts
- 17. Mariners 49.3K posts
- 18. #DETvsKC 4,958 posts
- 19. Eitan Mor 6,039 posts
- 20. JuJu Smith 4,289 posts
你可能會喜歡
-
 Ninad Mathpati 🇮🇳
Ninad Mathpati 🇮🇳
@Ninad_Mathpati -
 Cr33pb0y
Cr33pb0y
@cr33pb0y -
 Udit Bhadauria
Udit Bhadauria
@udit_thakkur -
 Aman Mahendra
Aman Mahendra
@amanmahendra_ -
 Ved Parkash
Ved Parkash
@v3d_bug -
 Sourav
Sourav
@souravbaghz -
 Deepak Dhiman🇮🇳
Deepak Dhiman🇮🇳
@Virdoex_hunter -
 Aditya sharma 🇮🇳
Aditya sharma 🇮🇳
@Assass1nmarcos -
 Abhinav
Abhinav
@abhinav_one -
 Avanish Pathak
Avanish Pathak
@avanish46 -
 ~Ankit Tiwari
~Ankit Tiwari
@Debian_Hunter -
 Samuel V.
Samuel V.
@sign3tsh3l1 -
 Debangshu 🇮🇳🥷
Debangshu 🇮🇳🥷
@ThisIsDK999 -
 Sayaan Alam
Sayaan Alam
@ehsayaan -
 Sharik Khan
Sharik Khan
@4non_Hunter
Something went wrong.
Something went wrong.