twentyeight
@b_sendpacket
Security Researcher | Malware Analysis & Reverse Engineering | https://infosec.exchange/@0x1c
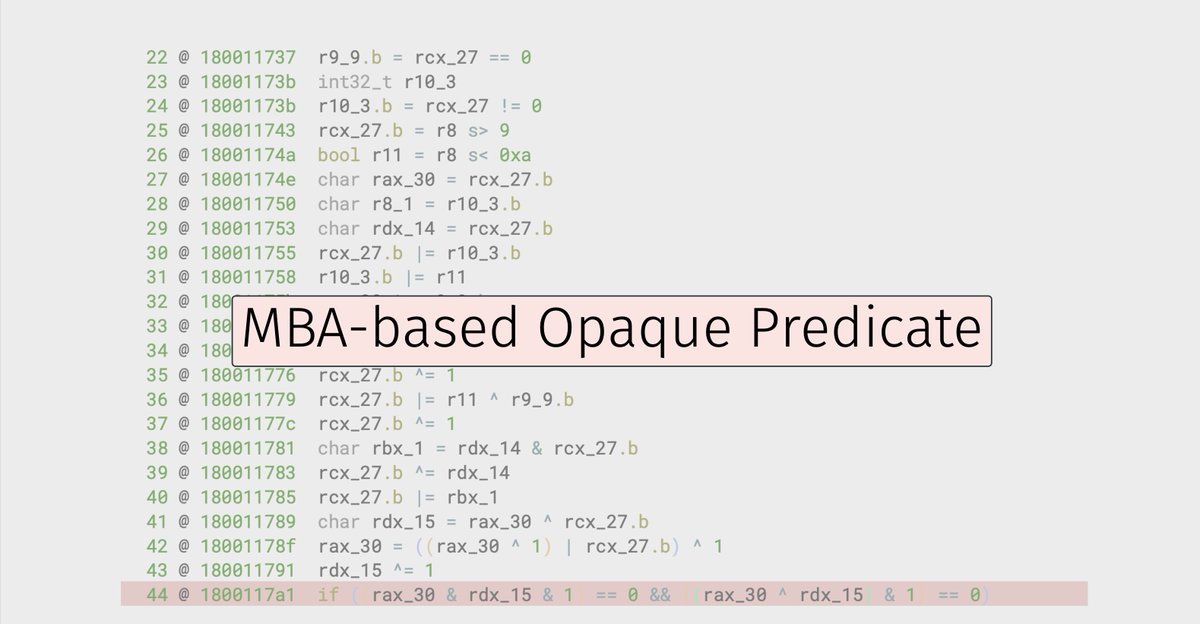
The slides from our @reconmtl talk, "Breaking Mixed Boolean-Arithmetic Obfuscation in Real-World Applications" (CC @nicolodev), are now online! Slides: synthesis.to/presentations/… Plugin: github.com/mrphrazer/obfu…
Did you know that WinDbg has a `dx` command that lets you define variables, cast memory, and walk structures? Here's some absolutely cursed code I wrote today to walk the PEB, locate ntdll.dll, and dump its exports - using only `dx`!

After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering. As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings). Blog:👉blog.washi.dev/posts/recoveri…

How Component Object Model (COM) works. #ThreatHunting #DFIR #Windows #Microsoft

victim does WHAT

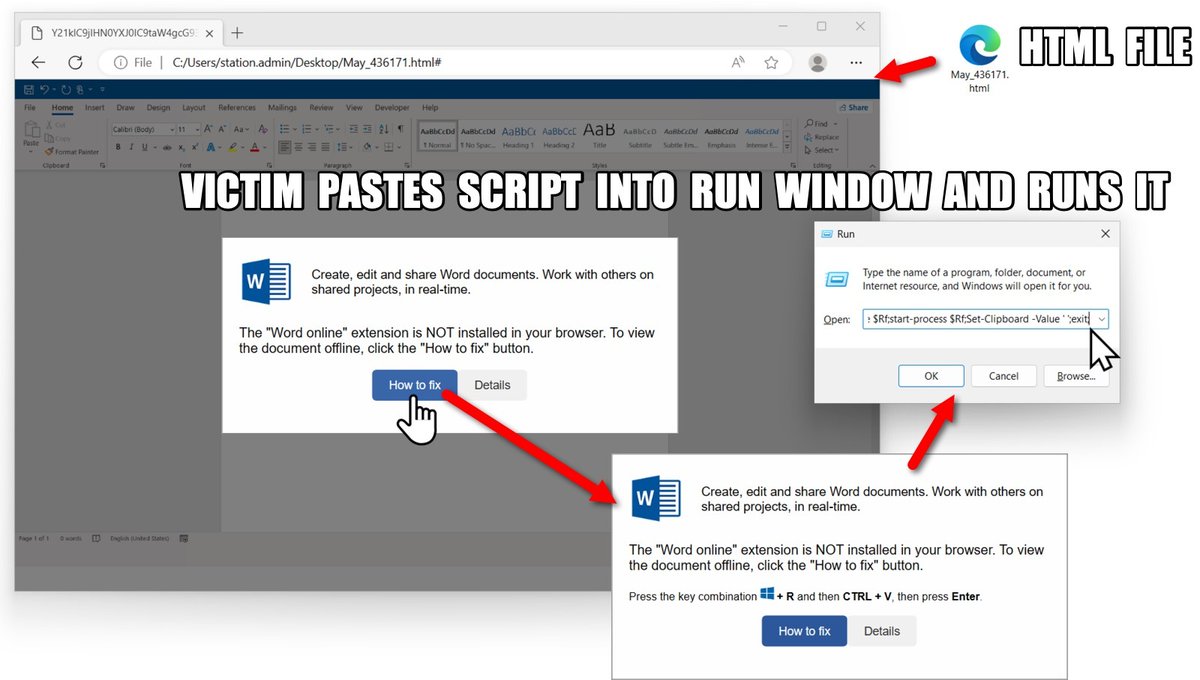
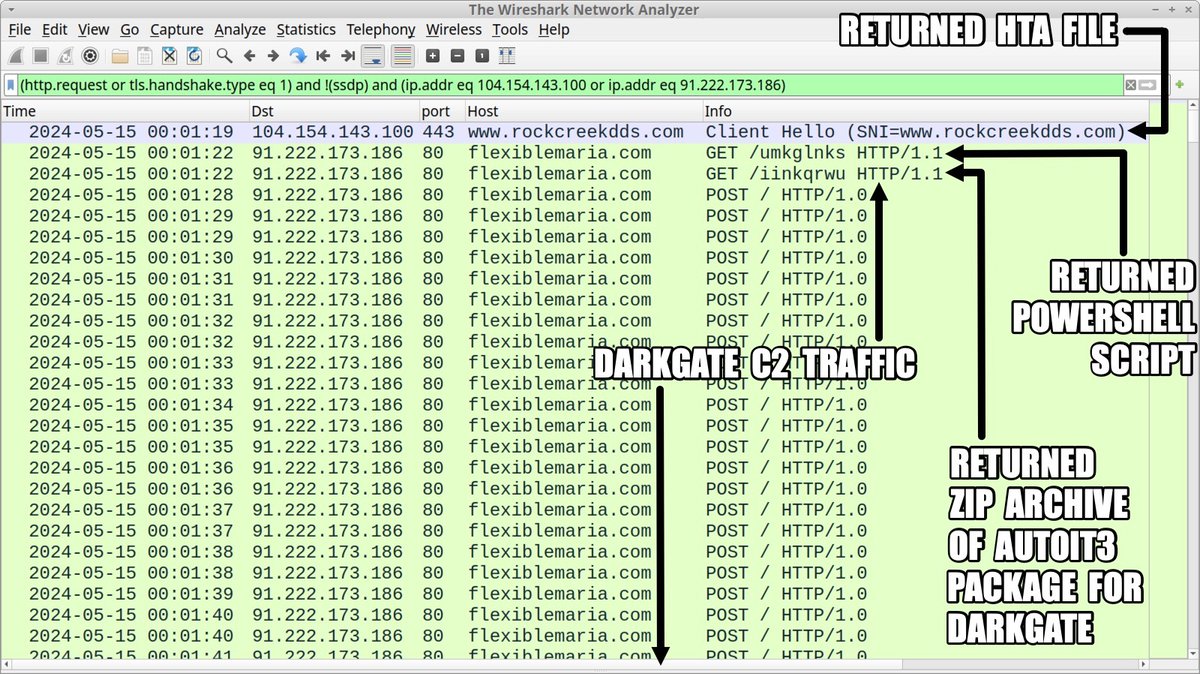
2024-05-14 (Tuesday): #DarkGate activity. HTML file asks victim to paste script into a run window. Indicators available at bit.ly/4bjvMAC #TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionTraffic


What a great opportunity for a #BinaryRefinery showcase! xt exe | xt | push [ | bat | carve -d string | iffs = | b64 | pop k i | carve -sd b64 | aes --iv=eat:i eat:k | zl | peek -mm ] 📌 github.com/binref/refiner…
![huettenhain's tweet image. What a great opportunity for a #BinaryRefinery showcase!
xt exe | xt | push [
| bat
| carve -d string
| iffs =
| b64
| pop k i
| carve -sd b64
| aes --iv=eat:i eat:k
| zl
| peek -mm ]
📌 github.com/binref/refiner…](https://pbs.twimg.com/media/GLxeoUCXQAAONp_.png)
In this video we'll explore #OneNote process activity using #procmon/Process Hacker. Then use #onedump to fully unravel the attack chain. We'll also investigate some anti-analysis in a .NET dropper and decrypt the final payload, which leads to #AsyncRat. youtu.be/3MVu0s5ofxE

Huge congrats to @b_sendpacket and @Autonomatom for being the first students to finish the Introduction to Malware Binary Triage (IMBT) course! They have now received their certificates of completion 🥳
United States Trends
- 1. Branch 37.7K posts
- 2. Chiefs 112K posts
- 3. Red Cross 56.5K posts
- 4. #njkopw 9,608 posts
- 5. Lions 90K posts
- 6. Exceeded 5,893 posts
- 7. Binance DEX 5,185 posts
- 8. Rod Wave 1,708 posts
- 9. Mahomes 35K posts
- 10. Air Force One 58.9K posts
- 11. Eitan Mor 18.5K posts
- 12. #LaGranjaVIP 84.1K posts
- 13. Knesset 16.6K posts
- 14. #LoveCabin 1,401 posts
- 15. Ziv Berman 21.7K posts
- 16. #TNABoundForGlory 60.4K posts
- 17. Alon Ohel 19K posts
- 18. Tel Aviv 61.1K posts
- 19. Matan Angrest 17.1K posts
- 20. Omri Miran 17K posts
Something went wrong.
Something went wrong.