blueberryinfosec
@bbinfosec
Just Another guy whom plays 0 and 1 to make the people secure!
おすすめツイート
By Col Wattal (retd),PARA’s It was a total intelligence failure. Well, That’s what they want you to believe. But the truth? It isn’t trending. It’s buried beneath…
First pause the crowdstrike update via gpo,and for the bitlocker do mass rotation via gpo using intune we can rotate the bitlocker in bulk for temporary activity github.com/christopherbax… #Crowdstrike #bitlocker #bsod
Temp workaround would be Computer configuration\Windows Components\Bitlocker drive Encryption\OS Drive\Save Bitlocker Key in AD DS #bitlocker
💧 SYSTEM PROMPT LEAK 💧 gm! here's OpenAI's system prompt for the Custom GPT Editor: """ ## System Prompt You are ChatGPT, a large language model trained by OpenAI, based on the GPT-4 architecture. You are an iterative prototype playground for developing a new GPT. The user…
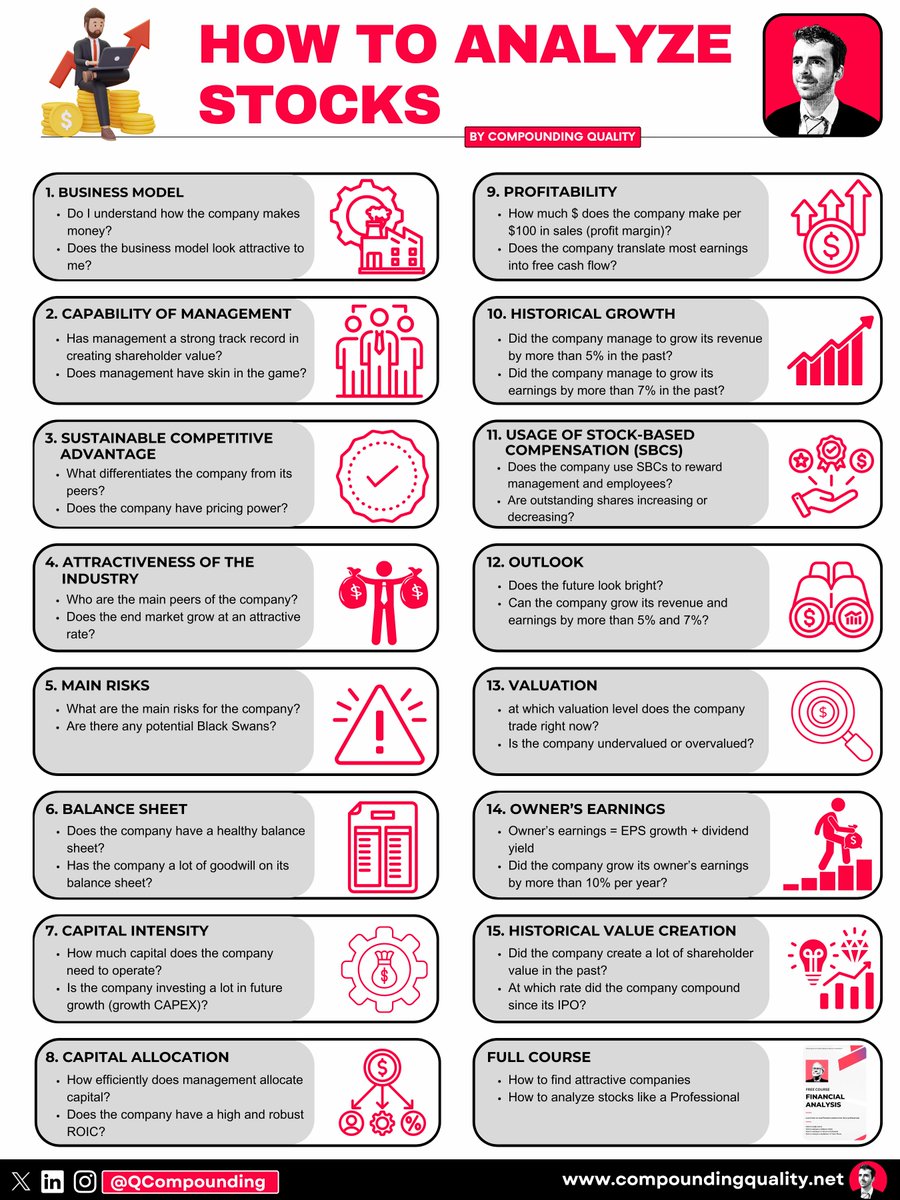
How to analyze stocks:
IAFs upgraded SAP-518 electronic warfare pods for its Su-30 MKI fleet, now have the capability to jam enemy AESA, LPI and FHSS radars.
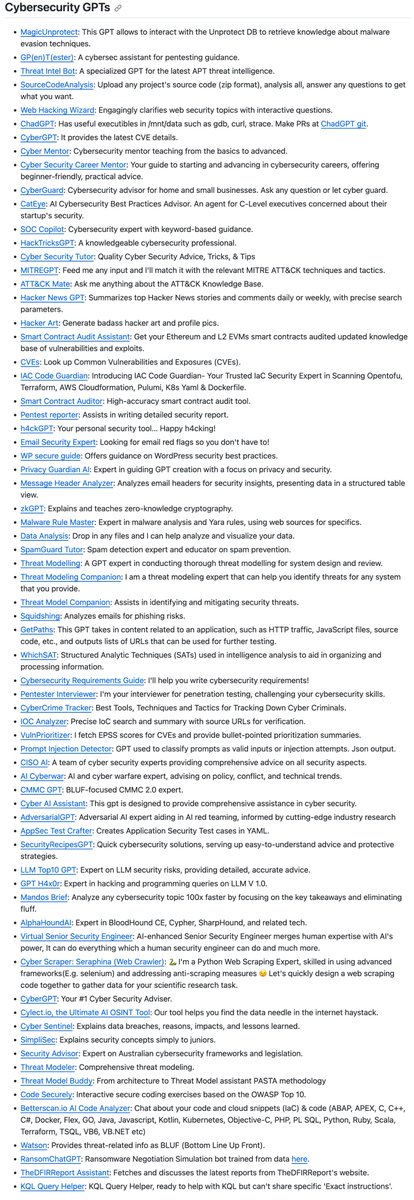
GPTs for Cybersecurity Collection github.com/fr0gger/Awesom…
The world stands on the brink of #WorldWarIII It depends on China and Iran whether they stop it or not because everything depends on their decisions about #Israel and #Taiwan
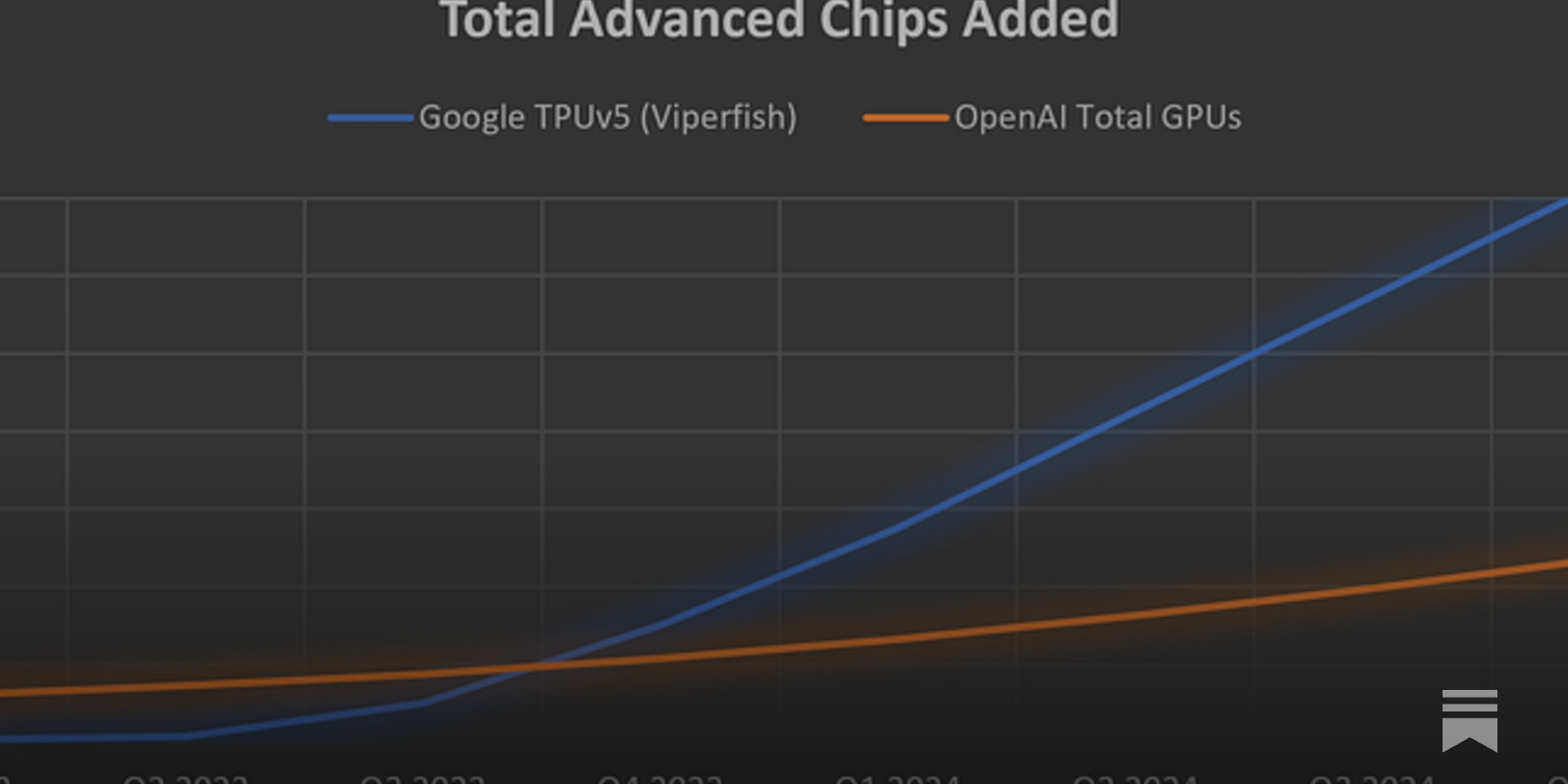
The Upcoming AI Wars and The Science Behind Multimodal Large Language Models (MLLMs) Today, GPT-4 reigns supreme on all the LLM benchmarks and leaderboards but rumors are that it will soon be displaced. Google is claiming its Gemini model is 5 times more powerful than GPT-4.…

🚨🚨 BIG : WE URGE ALL USERS TO UPDATE THEIR #Apple devices urgently. @citizenlab in coordination with @Google’s TAG team found that former Egyptian MP Ahmed Eltantawy was targeted with Cytrox’s #Predator #spyware through links sent via SMS and WhatsApp. citizenlab.ca/2023/09/predat…
Node.js and Express.js - Full Course ☞ morioh.com/p/2eeb0e0d5881 #node #express #nodejs #javascript #programming #developer #morioh #programmer #coding #softwaredeveloper #computerscience #webdev #webdeveloper #webdevelopment
Metasploit has a very nice attack flow on finding vulnerable ADCS certificates for exploitation. Currently metasploit supports attacking ESC1 to ESC4. I always feel like this alternate tooling isn't talked about near as much. docs.metasploit.com/docs/pentestin…
A detailed two part video showing how we found a DNS parsing vulnerability and wrote a remote root exploit for it🤌 Part 1: Finding the vulnerability via "fuzzing" and reverse engineering with Ghidra 👾 youtube.com/watch?v=xWoQ-E… Part 2: Understanding vulnerability constraints and…


“HuggingFace’s leaderboards show how truly blind they are because they actively hurting the open source movement by tricking it into creating a bunch of models that are useless for real usage.” Ouch. semianalysis.com/p/google-gemin…
KRBJack A Kerberos AP-REQ hijacking tool with DNS unsecure updates abuse. github.com/almandin/krbja… #infosec #pentesting #redteam #cybersecurity

BalCCon2k23 - System Failure - 8 | 9 | 10 September 2023, Novi Sad, Serbia is right about the corner!!! Preliminary speaker list for #BalCCon2k23 is online: lnkd.in/eXtPQCHS Tickets/BalCCon2k3 Badge/T-Shirts are available for pre-order: lnkd.in/evfni2ay
"Azure-AD-Incident-Response-PowerShell-Module: The Azure Active Directory Incident Response PowerShell module ..." #infosec #pentest #redteam github.com/AzureAD/Azure-…
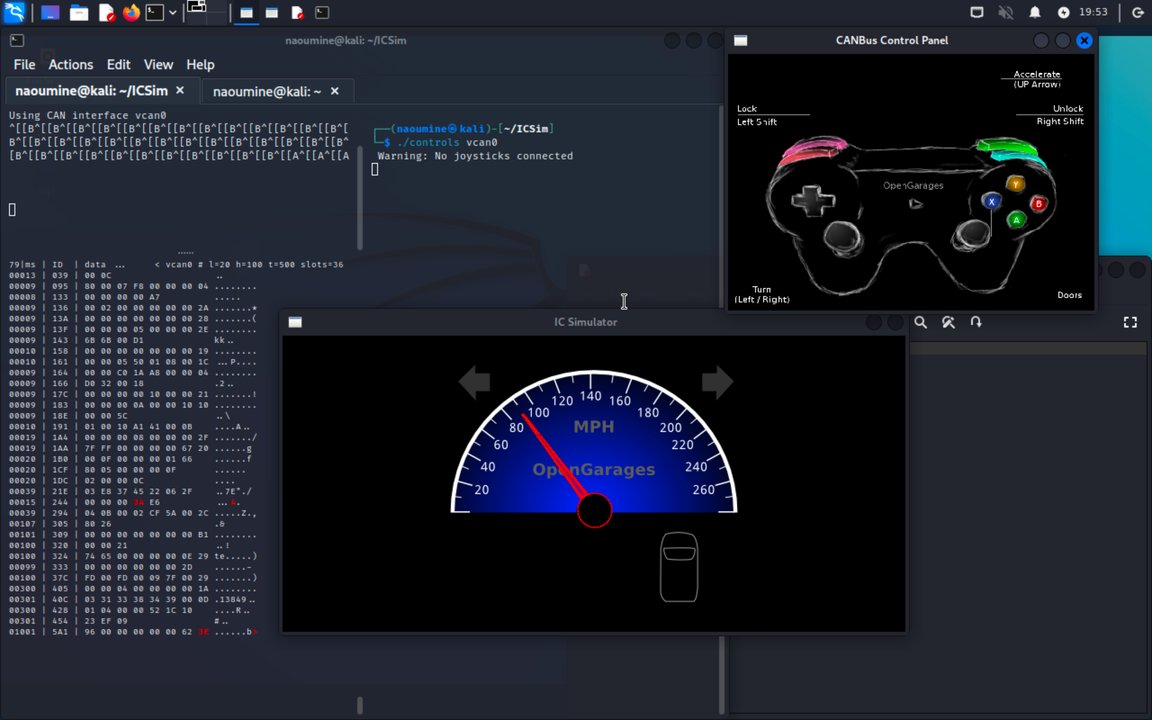
Vehicle Hacking with ICSim - By ESRA Source: medium.com/@naoumine/vehi… #Hacking #infosec #redteam #cybersecuritytips #cybersecurity
United States トレンド
- 1. Kalani 5,333 posts
- 2. REAL ID 6,749 posts
- 3. Milagro 29.7K posts
- 4. Cyber Monday 59.5K posts
- 5. Vanguard 11.6K posts
- 6. Penn State 8,573 posts
- 7. TOP CALL 11.8K posts
- 8. Admiral Bradley 10.3K posts
- 9. Hartline 3,851 posts
- 10. MRIs 4,464 posts
- 11. #GivingTuesday 3,983 posts
- 12. Merry Christmas 49.7K posts
- 13. Jason Lee 2,306 posts
- 14. #OTGala11 99.2K posts
- 15. Shakur 8,201 posts
- 16. Jay Hill N/A
- 17. MSTR 34.3K posts
- 18. Check Analyze 1,196 posts
- 19. Token Signal 4,552 posts
- 20. Brent 9,948 posts
おすすめツイート
-
 Pratik Yadav
Pratik Yadav
@pratikyadav7_ -
 Vegeta
Vegeta
@_justYnot -
 nikhil(niks)
nikhil(niks)
@niksthehacker -
 Gopesh Sharma
Gopesh Sharma
@MrSharmaX -
 Akshay Sharma 🇮🇳
Akshay Sharma 🇮🇳
@akshaysharma71 -
 D33p4k
D33p4k
@BeingN00b -
 Debangshu 🇮🇳🥷
Debangshu 🇮🇳🥷
@ThisIsDK999 -
 வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
வீப்பியார் (ᴠ ᴇ ᴇ ᴘ ᴘ ɪ ᴀ ᴀ ʀ)
@veeppiaar -
 Bhavuk Jain
Bhavuk Jain
@bhavukjain1 -
 Dhanesh Sivasamy
Dhanesh Sivasamy
@DhaneshSivasamy -
 Crowdfense
Crowdfense
@crowdfense -
 Jeya Seelan
Jeya Seelan
@rootxjs -
 Cyber Adam
Cyber Adam
@iam_amdadam -
 Raunak Parmar
Raunak Parmar
@trouble1_raunak -
 HK@seyon
HK@seyon
@seyon0x
Something went wrong.
Something went wrong.