JaeRyoung Oh
@h4z3dic
Just a coder and a trader
Вам может понравиться
GitHub - LazyTitan33/DNS-Exfilnspector: Automagically decode DNS Exfiltration queries to convert Blind RCE into proper RCE via Burp Collaborator github.com/LazyTitan33/DN…
GitHub - sdancacypnexi8/dnsrecce: 🔍 Perform fast and efficient DNS reconnaissance with dnsrecce, supporting A/NS/MX queries, brute force, Google scraping, and structured output. github.com/sdancacypnexi8…
Estimates USD cost for LLM prompts and completions github.com/AgentOps-AI/to…
I'm compiling a list of good fp8 training libraries: - transformer_engine github.com/NVIDIA/Transfo… - torchao github.com/pytorch/ao/blo… - MS-AMP github.com/Azure/MS-AMP/t… Which one(s) do you prefer - ease of use, stability, support? Which ones am I missing? Thank you!
Earthonion +PS4+ Poc for ps4 vue js injection via mitm TEST: github.com/earthonion/Vue…

#Infographics #Offensive_security Active Directory Pentest Mindmap 2025 mayfly277.github.io/posts/AD-mindm… ]-> Source code - github.com/Orange-Cyberde…
기부 하나^^ 2019년 중국에서 출판한 옵션 책의 한글 판입니다. 필요없는 것 삭제하고 옵션의 특징, 이항모형, 변동성, 델타헤지에 대한 것만 추렸습니다. 어렴풋이 알던 델타헤지 등의 개념을 정립하는데 도움이 되리라 생각합니다. 마음껏 보세요. ^^ drive.google.com/file/d/1HI280m…

this repo teaches you how to build agents from scratch, step by step. it goes from fundamentals to advanced, all you need to master agents: → local LLMs and inference → LLMs through APIs → prompt engineering → GPU parallel processing → streaming and response control →…

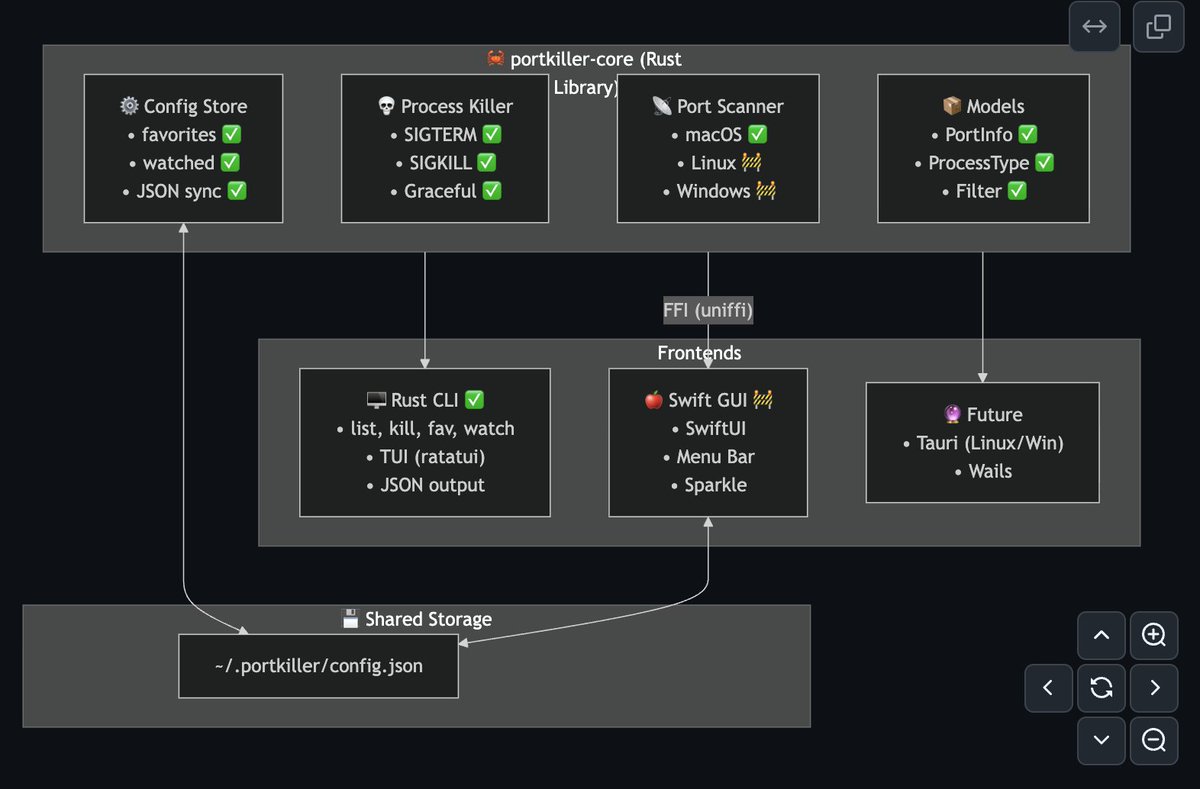
PortKiller v4: is taking a new direction, with a possible transition from Go to Rust. This will let us support all operating systems and ship features faster. We’d be glad to have you with us. Pr: github.com/productdevbook… Discussion: github.com/productdevbook…
New BSides Canberra 2025 talk by ByungHyun Kang is now live: “Breaking COMposure: Journey to Hunting Windows COM Vulnerabilities.” Watch here: youtu.be/TBMyjoTDf-0
youtube.com
YouTube
Breaking COMposure: Journey to Hunting Windows COM Vulnerabilities -...
Claude Code Templates just hit 100+ Skills on aitmpl.com Installing is easy - one click to copy the install command, paste it in your project's .claude folder, done. - 67K npm installs - 13K+ GitHub stars - fully open source Thanks to the community for…
my buggy experiment is a live @ bleedingedgealpha.net register an account for free then the connection works important to remember that this is only an experiment. if it goes well, we can continue working on this.
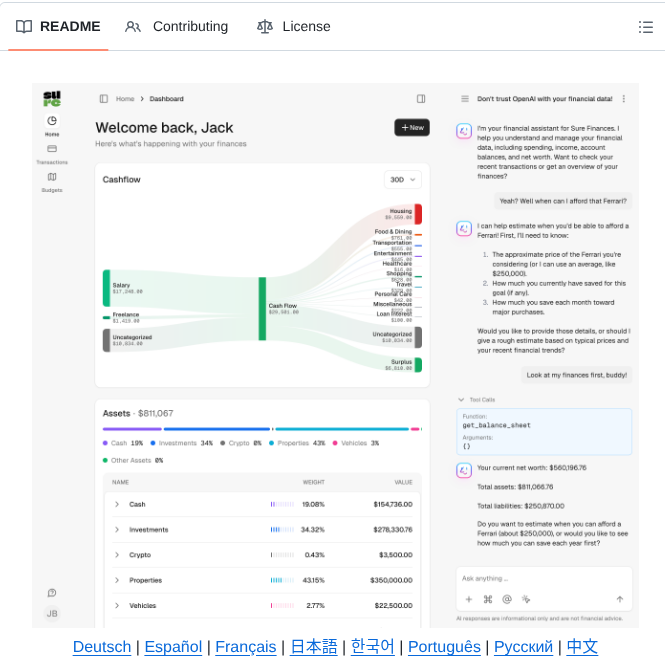
Personal finance app with AI assistant github.com/we-promise/sur…
👉👉 UnDER: Unsupervised Dense #PointCloud #Extraction Routine for UAV Imagery Using #DeepLearning ✍️ John Ray Bergado and Francesco Nex 🔗 brnw.ch/21wYuQc
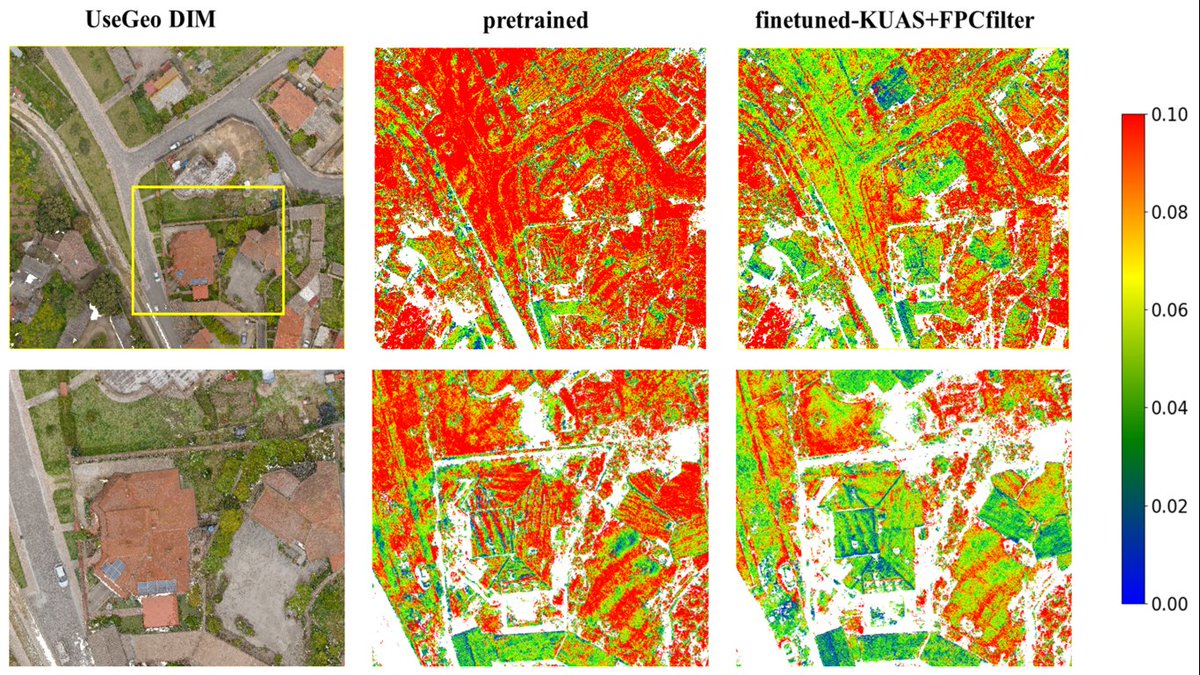
The recording of the GeoAI workshop at the #AGU25 is now available. Notebook: agu2025.workshops.geojupyter.org/modules/integr… Video: youtu.be/OW26XShiqeI In this workshop, you will: - Discover the core capabilities of the GeoAI package, including data preprocessing, feature extraction, and…

AI agents trade crypto futures across exchanges github.com/NoFxAiOS/nofx/
Analyzes stock trends with large language models github.com/hengruiyun/AI-…
made an epstein file viewer because the governments website sucks hosted for free at: epstein-files-browser.vercel.app
The original GTA Vice City is now playable right in your browser! - Original game with all key features - Fast startup - All screen resolutions - Gamepads and touch controls - Local and cloud saves Play here: dos.zone/grand-theft-au…


Downloads Udemy courses for offline use github.com/heliomarpm/ude…

United States Тренды
- 1. Carson Beck 2,383 posts
- 2. Dawson 5,378 posts
- 3. Texas A&M 18.3K posts
- 4. Toney 3,383 posts
- 5. Clinton 439K posts
- 6. Marcel Reed N/A
- 7. Isak 13.4K posts
- 8. College Station 2,548 posts
- 9. Kyle Field 2,300 posts
- 10. #GigEm 3,462 posts
- 11. Aggies 3,163 posts
- 12. #CFPplayoff N/A
- 13. Go Birds 4,634 posts
- 14. Pringle N/A
- 15. Mario Cristobal N/A
- 16. Wirtz 18.2K posts
- 17. Brainiac 13.1K posts
- 18. Xavi Simons 5,320 posts
- 19. #CFP2025 N/A
- 20. Fletcher 5,270 posts
Вам может понравиться
-
 Piotr Bania
Piotr Bania
@PiotrBania -
 Jacob Soo
Jacob Soo
@_jsoo_ -
 REhints
REhints
@REhints -
 Ethical Hacker
Ethical Hacker
@offethhacker -
 Alex Matrosov
Alex Matrosov
@matrosov -
 Stephen A. Ridley
Stephen A. Ridley
@s7ephen -
 Vay3t
Vay3t
@vay3t -
 beist
beist
@beist -
 Securityblog
Securityblog
@Securityblog -
 gartzen
gartzen
@Gartzen72 -
 보안프로젝트
보안프로젝트
@ngnicky -
 Minh-Triet Pham Tran
Minh-Triet Pham Tran
@MinhTrietPT -
 Alessio
Alessio
@alessio_dp -
 Constantin Milos ♏@Tinolle infosec.exchange
Constantin Milos ♏@Tinolle infosec.exchange
@Tinolle1955 -
 Sanoop Thomas ⠵
Sanoop Thomas ⠵
@s4n7h0
Something went wrong.
Something went wrong.