HackerContent
@hacker_content
We create content and manage socials for your cybersecurity organization. 🚀 Sound good? 👉 http://hackercontent.com Founded by @hakluke
你可能會喜歡
Building brand awareness in the cybersecurity space isn't just about a single campaign; it's a strategic, full-circle effort to ensure your brand is seen and heard by the right people. We provide a holistic approach to building your brand's presence and authority. Our…
Want to know if you have energy and battery issues? Use this command to get a report 👇 #Windowscommand #TechTip #BatteryLife
Do you know the difference between the greedy and lazy quantifiers when using regular expressions (regex)? 🤔 Don't miss out on our Black Friday sale to master Regex👇 hhub.io/2025blackfrida…
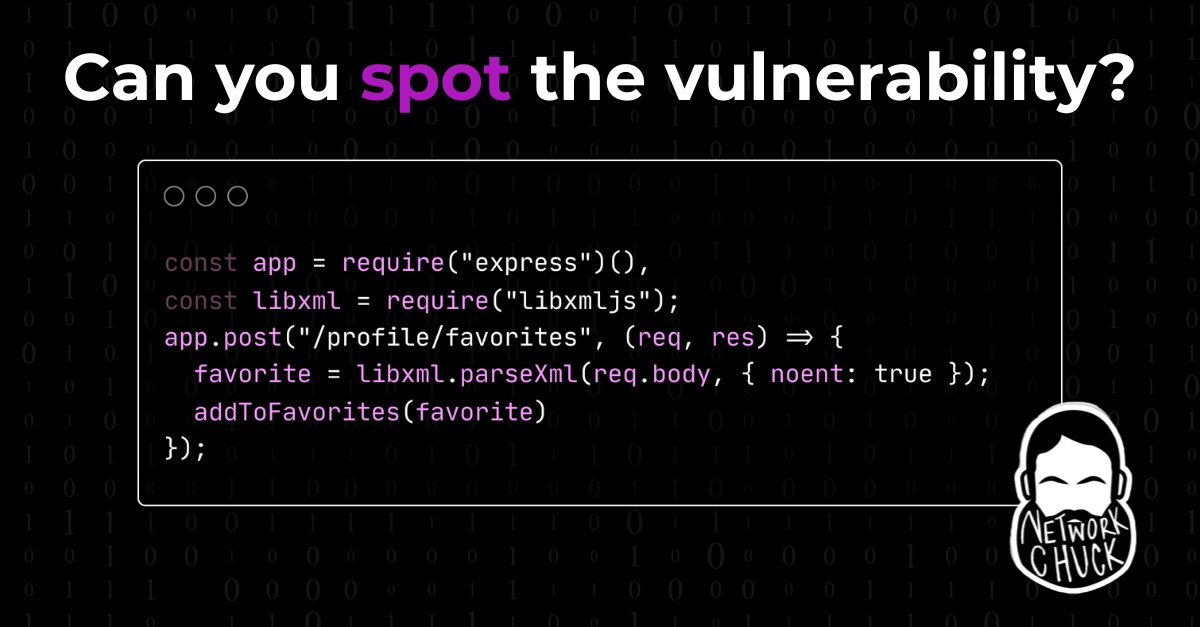
Want to learn about how a fascinating XSS vulnerability found by @ethiack engine led to an interesting rabbit hole of bypassing WAFs and parameter injection? Read the blog post here 👇 blog.ethiack.com/blog/bypassing…
Social media posts with video get up to 10x more engagement than those without. For cybersecurity companies, this is a powerful tool to cut through the noise. Video allows you to simplify complex topics, build trust, and showcase your expertise in a dynamic way. We can help you…
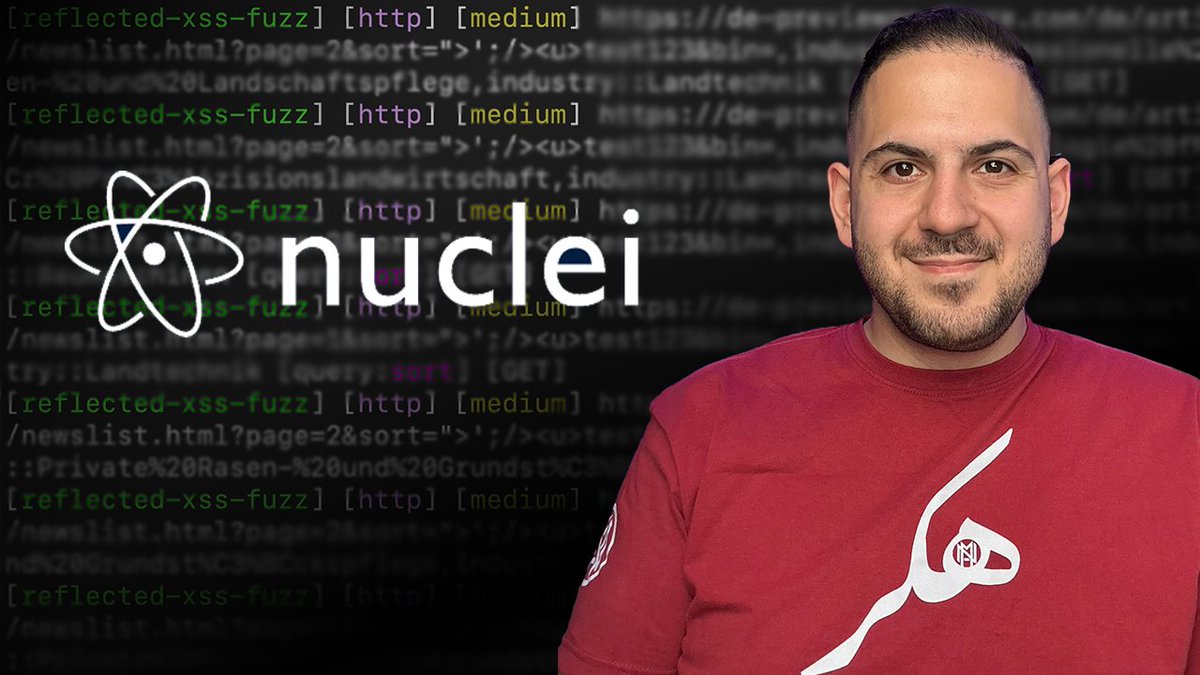
I automated finding reflected XSS using Nuclei and some passive recon data and ran it against a bug bounty program. Watch it here 👉🏼 youtu.be/WCXW9uKYm48
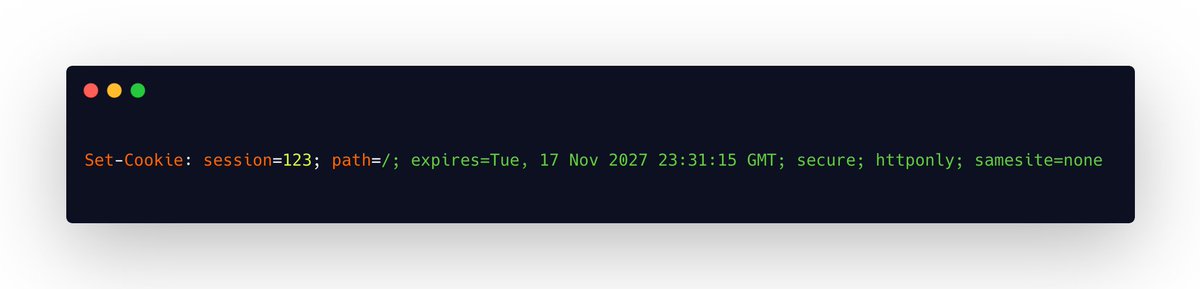
Confused about how the Cookie SameSite attribute works? - SameSite=None: all cross-site requests will include the cookie; if no other protections are in place, opens up the site to CSRF attacks - SameSite=Lax: only GET requests triggered by a top-level navigation will include…
Hiring: someone who loves hacking, can edit images, and writes well. DM me.
The cybersecurity landscape is a complex puzzle. At HackerContent, we provide the missing pieces. Our technical blog post service turns your team’s expertise into original, authoritative content designed to build trust and authority. We make sure it gets seen with an ethical…

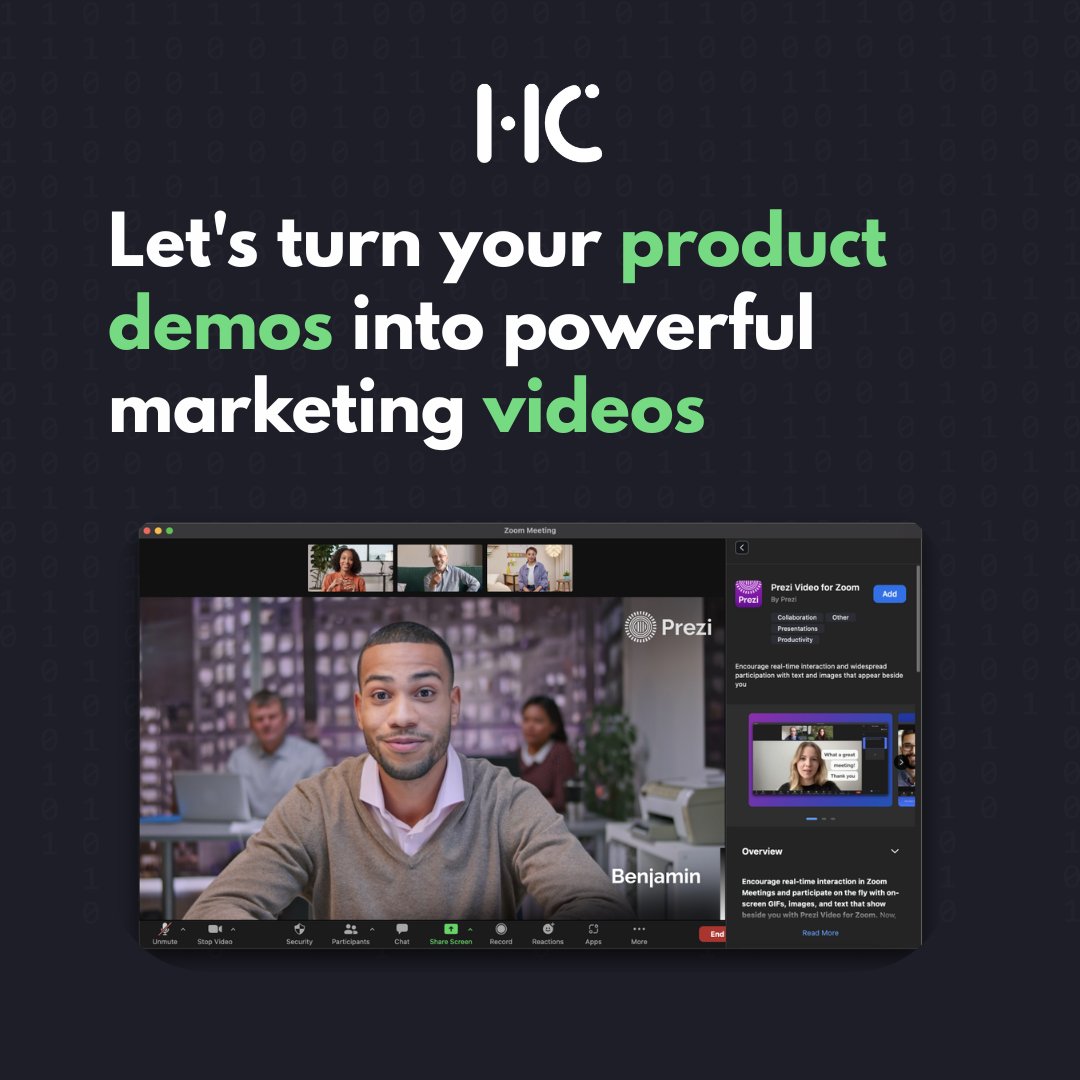
Let's turn your product demos into powerful marketing videos. Your live demos are a powerful sales tool, but their value shouldn't end with a single call. We can transform your product demonstrations into a library of dynamic content that works for you 24/7. From quick,…
Want to make your cybersecurity content stand out? HackerContent helps you get beautiful, polished, and professional videos that convert. Ready to see the difference? Contact us to learn more!👉 hackercontent.com/#contact
This is a trick, not a treat! I HACKED my wife’s browser and the code is SCARY easy! Follow along and learn how to pull off this harmless, but hilarious, Halloween prank! 🎃 Check it out here: youtu.be/3ogyS4KOlXc?si…
Have you noticed that Chuck's socials are always on point? That's (partly) because we help him manage them! If you want the same power for your business, get in touch.
So you've heard of TCPdump and TShark, right? But you know what's better? Termshark. Check this out 👇
Think you have what it takes to leverage an RCE and extract data even with strict firewall rules in place? Find the lab and the full video here 👇 app.hackinghub.io/hubs/interacti…
If you're marketing a cybersecurity brand, and you haven't already hired @hacker_content to run your socials, why not? This is a crazy-good offering. It will make your brand stand out, get you more clients, and the cost is probably lower than you think.
Nice testimonial from one of our awesome clients!
100% this, we love working with @hakluke and the team. Having a marketing team that actually know what you’re talking about is priceless
You have the knowledge. It's time to share it. Your team's technical expertise is your company's most valuable asset. But without a voice, that expertise remains hidden from the wider industry. Let's turn your technical expertise into valuable blog posts. Our service is…
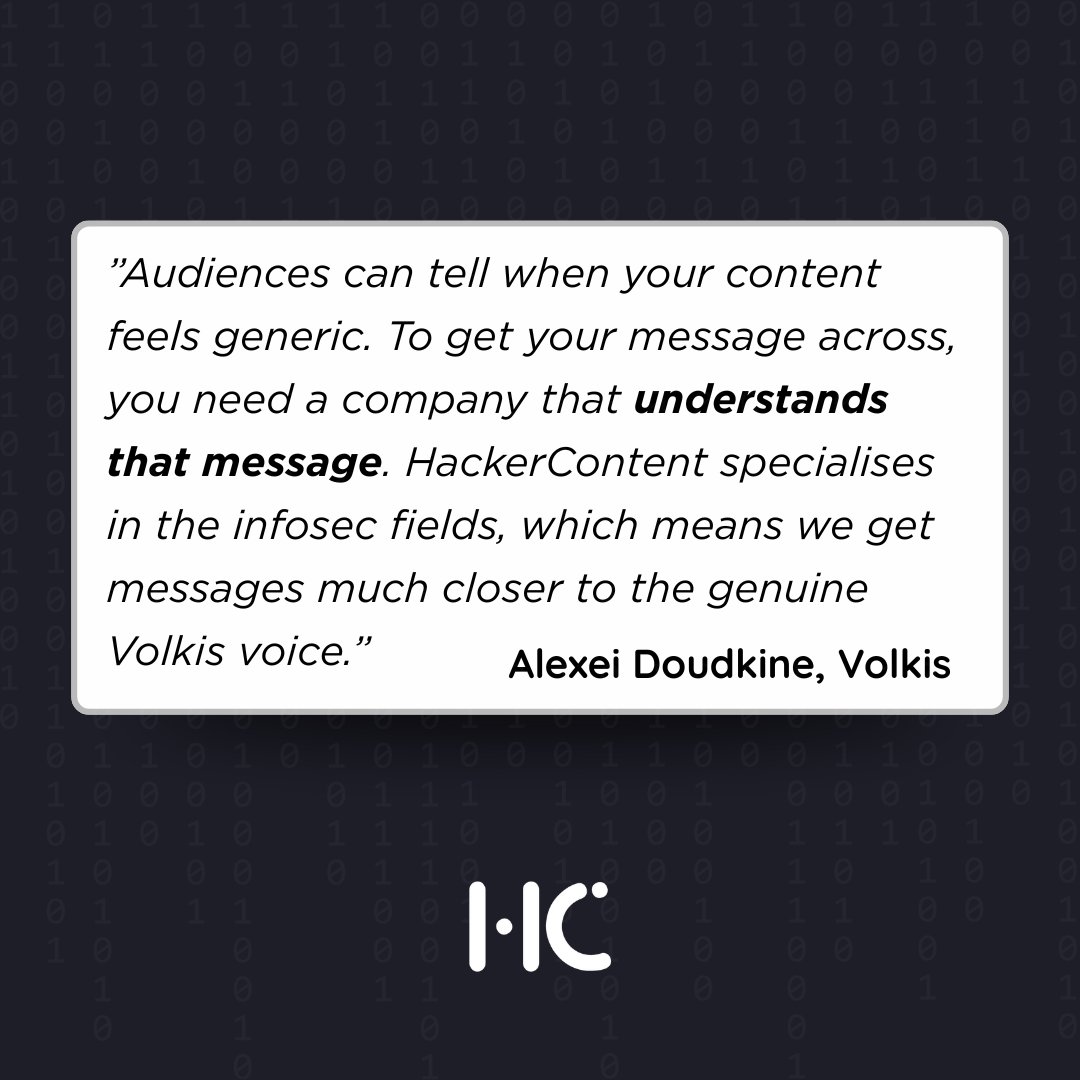
Stop sounding generic. Start sounding like the experts you are. 🎯 @VolkisAU can confirm, our deep specialization means we understand the cybersecurity audience and messaging better than anyone. We capture your authentic voice! Want content that truly connects? Let's talk. 👇…
Join us on the ProjectDiscovery Discord! Get inside the conversation and connect with the community. 🌀Join here: discord.com/invite/project…

United States 趨勢
- 1. The BONK 278K posts
- 2. FINALLY DID IT 609K posts
- 3. Namjoon 66.1K posts
- 4. Good Saturday 21.6K posts
- 5. #albatross 3,391 posts
- 6. #AAA2025 130K posts
- 7. The EU 366K posts
- 8. #SaturdayVibes 2,766 posts
- 9. #launch 3,270 posts
- 10. #raven 3,654 posts
- 11. Aston Villa 34.3K posts
- 12. Cocona 142K posts
- 13. Gunther 26.5K posts
- 14. Flag Day 3,547 posts
- 15. 5 YEARS WITH MC WONYOUNG 18.3K posts
- 16. YUNHO 30.3K posts
- 17. Dizzy 6,624 posts
- 18. Tulane 14.8K posts
- 19. fnaf 2 67.1K posts
- 20. St. Nicholas 6,136 posts
你可能會喜歡
-
 Godfather Orwa 🇯🇴
Godfather Orwa 🇯🇴
@GodfatherOrwa -
 Altered Security
Altered Security
@AlteredSecurity -
 Critical Thinking - Bug Bounty Podcast
Critical Thinking - Bug Bounty Podcast
@ctbbpodcast -
 HACKLIDO
HACKLIDO
@hacklido -
 Cybertix
Cybertix
@thecybertix -
 ReconOne
ReconOne
@ReconOne_bk -
 Deepak bug_vs_me
Deepak bug_vs_me
@bug_vs_me -
 InfoSec Pat
InfoSec Pat
@Infosecpat -
 Nithin 🦹♂️
Nithin 🦹♂️
@thebinarybot -
 Bug Bounty Reports Explained
Bug Bounty Reports Explained
@gregxsunday -
 Mike Takahashi
Mike Takahashi
@TakSec -
 bugcrowd
bugcrowd
@Bugcrowd -
 Luke Stephens (hakluke)
Luke Stephens (hakluke)
@hakluke -
 Anton
Anton
@therceman -
 MorningStar
MorningStar
@0xMstar
Something went wrong.
Something went wrong.