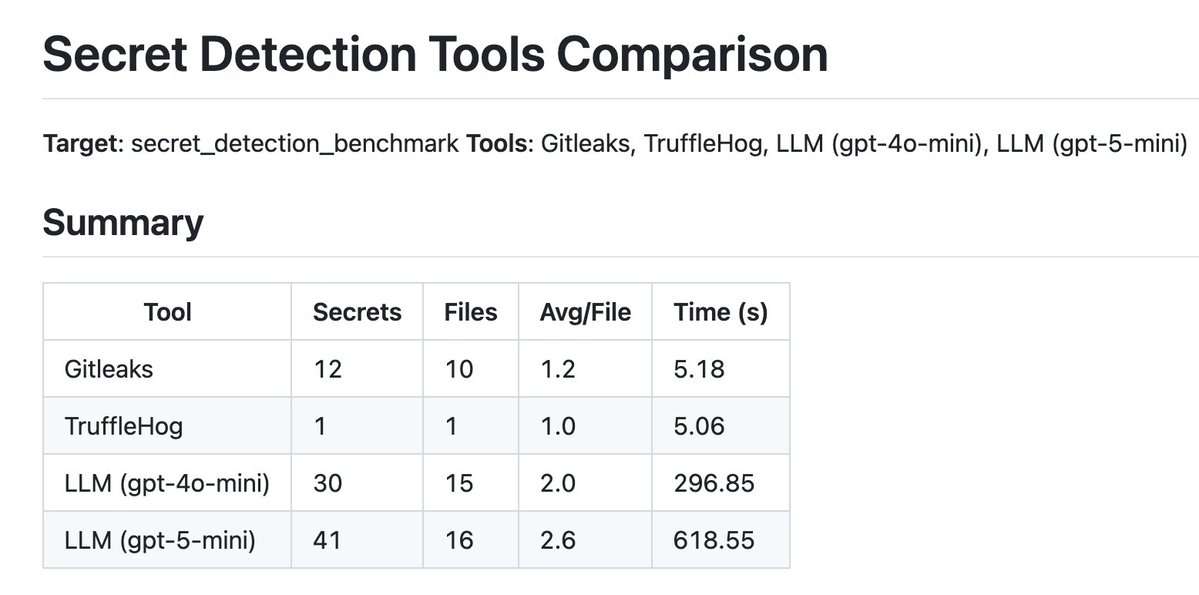
LLMs are beating regex in secret detection. We benchmarked Gitleaks, TruffleHog, and two LLMs on real-world codebases. GPT-5-mini hits 84.4% recall vs Gitleaks at 37.5% vs TruffleHog at 0.0% LLMs catch: – Split secrets – Obfuscated tokens – Decoded vars – Even commented-out…
Our latest Dojo challenge, Hardware Monitor, has come to an end! ✅ We know this one gave many of you a hard time… so why not dive into the solution? You can now check out the best write-up and see how it was cracked 👉 yeswehack.com/dojo/dojo-ctf-… #YesWeRHackers #CTF #BugBounty

The swag is gonna be awesome
Drumroll, please… 🥁 We have the winners for our latest Dojo challenge! Congrats nater1ver, @_Ali4s_ and @noraj_rawsec: you win a swag pack! Keep an eye on your mailbox 👀 Want to win swag and program invites? Stay tuned 👉 dojo-yeswehack.com/challenge-of-t… #YesWeRHackers

Giveaway brought to you by @hackinghub_io: 5x Blind XSS vouchers 5x Web Exploitation vouchers How to enter: 1⃣ Follow @BugBountyDEFCON + subscribe to our YouTube channel 2⃣Follow @hackinghub_io 3⃣ ❤️+🔃 this post 4⃣Comment this post Winners will be picked on Friday 8/29…
Using Golang for backdoors is cool but even cooler would be Rust as right now, it's still bloody hard to RE and understand. This is why @juanandres_gs's talk next month @BlackHatEvents is gonna be epic blackhat.com/us-24/briefing…
Security analysis and exploitation of Xiaomi WiFi Routers blog.thalium.re/posts/rooting-… Credits @thalium_team #embedded

👇You can search on Hunter using the following query: header="Content-Type: text/html" and header!="charset" and web.body!="charset" 🔗Hunter Link:hunter.how/list?searchVal… #hunterhow #infosec #infosecurity #Infosys #Vulnerability
🔥 XSS on any website with missing charset information? 😳 Attackers may leverage the ISO-2022-JP character encoding to inject arbitrary JavaScript code into a website. Read more in our latest blog post: sonarsource.com/blog/encoding-… #appsec #security #vulnerability

I spent the last 5 months reverse engineering Denuvo's protection in Hogwarts Legacy and finally managed to bypass it using more than 2000 hooks 😂 One of the toughest challenges of my life. Here's my blog post about it: momo5502.com/posts/2024-03-…
"Can I advertise our drainer?" "Can I advertise my new Breached-like forum?" "Can I advertise my Infostealer?" Bro, we're probably on every watchlist on the planet. The very nanosecond we took dirty money we'd hear helicopters and the "COPS" theme song.
We're seeing people on Xitter discuss being approached by brands and companies – offering them thousands of dollars for a single tweet. This is absolutely disgusting. Why aren't we being approached? The only people offering us large sums of money are criminals 😂😂😂
Statement on glibc/iconv Vulnerability Recently, a bug in glibc version 2.39 and older (CVE-2024-2961) was uncovered where a buffer overflow in character set conversions to the ISO-2022-CN-EXT character set affects PHP. Read our full statement at php.net/archive/2024.p…
Since my @offensive_con talk is not out yet, I'll spoil it a little bit: you can use iconv() to get RCE on @roundcube. See you on Monday for part 2!
As promised, here's how you can attack @roundcube using CVE-2024-2961. Not to be redundant with my @offensivecon talk, I go for a data-only attack, giving more insight into the PHP engine.
Iconv, set the charset to RCE (part 2): @cfreal_ exploits direct iconv() calls to hack the PHP engine, and its most popular webmail, @Roundcube (CVE-2024-2961). ambionics.io/blog/iconv-cve…
🔥 XSS on any website with missing charset information? 😳 Attackers may leverage the ISO-2022-JP character encoding to inject arbitrary JavaScript code into a website. Read more in our latest blog post: sonarsource.com/blog/encoding-… #appsec #security #vulnerability

United States Trends
- 1. Nancy Pelosi 72.3K posts
- 2. Marshawn Kneeland 46.7K posts
- 3. Ozempic 6,814 posts
- 4. Craig Stammen 1,936 posts
- 5. Michael Jackson 72.4K posts
- 6. Gordon Findlay 3,007 posts
- 7. Pujols N/A
- 8. Oval Office 25.8K posts
- 9. #MichaelMovie 68.5K posts
- 10. GLP-1 5,223 posts
- 11. Kyrou N/A
- 12. Jaidyn 1,752 posts
- 13. Abraham Accords 5,266 posts
- 14. Novo Nordisk 7,306 posts
- 15. Kazakhstan 7,073 posts
- 16. #NO1ShinesLikeHongjoong 38.4K posts
- 17. Unplanned 9,335 posts
- 18. #영원한_넘버원캡틴쭝_생일 37.6K posts
- 19. #ChelleyxEOS 1,635 posts
- 20. Baxcalibur 6,456 posts
Something went wrong.
Something went wrong.








































































