Ebubekir
@hackerbecker
Malware Analyst @PRODAFT - @_aucc, Karidesler CTF player @[email protected]
你可能會喜歡
🐌 Subtle Snail (UNC1549), an Iran-nexus espionage group 🇮🇷, is targeting European 🇪🇺 telecom, aerospace, and defense organizations. The group uses LinkedIn HR lures and Azure-based C2. Read the full report 👉 catalyst.prodaft.com/public/report/… #ThreatIntel #Malware #APT #IOC

🚨 BIG NEWS: THE SYS INITIATIVE 🚨 For years, cyber criminals have hidden in the shadows of forums. They operated behind fake names, encrypted channels, and closed communities. Reputation and trust were their most valuable currencies. Now is the time to shift from defense to…
Merhaba! Teknolojinin baş döndürücü hızla geliştiği günümüzde, siber güvenlik hepimizin gündeminde en üst sıralarda yer alıyor. 🤩 İşte tam bu yüzden, seni Siber Güvenlik Zirvesi 2025’e davet ediyoruz! 🚀 Bu etkinlikte: 💻 Alanında uzman konuşmacılardan en yeni siber tehdit…

Diferansiyel denklemler dersi almış mühendis bir tanıdığınız varsa , hayat boyu bu dersin anılarını dinleyeceksinizdir. Not: askerlik anılarıyla yarışır . xdxdxd
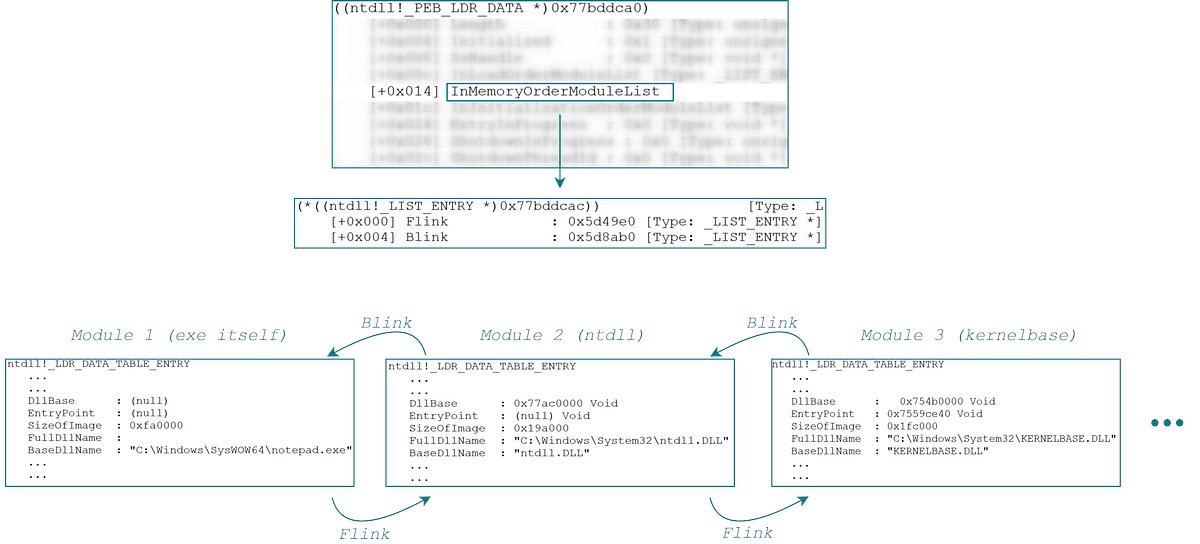
My first blog post, "Understanding the Process Environment Block (PEB) for Malware Analysis," is out! I've explained key PEB techniques and demonstrated them with examples from #StealC and #BlackMatter ransomware. metehan-bulut.medium.com/understanding-… #malware #ReverseEngineering #infosec
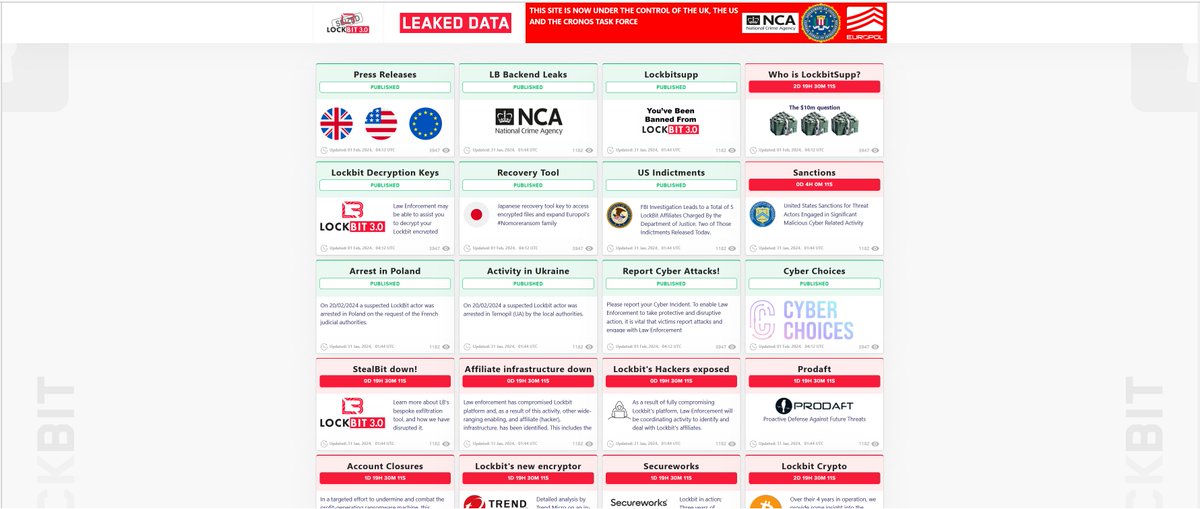
Since LOCKBIT’s first entry into the cybercrime ecosystem, we at PRODAFT have been assisting NCA, FBI and other partners of #OpCronos to better comprehend and disrupt this large criminal enterprise. Researching this ill-famous cybercrime syndicate has been challenging, but our…
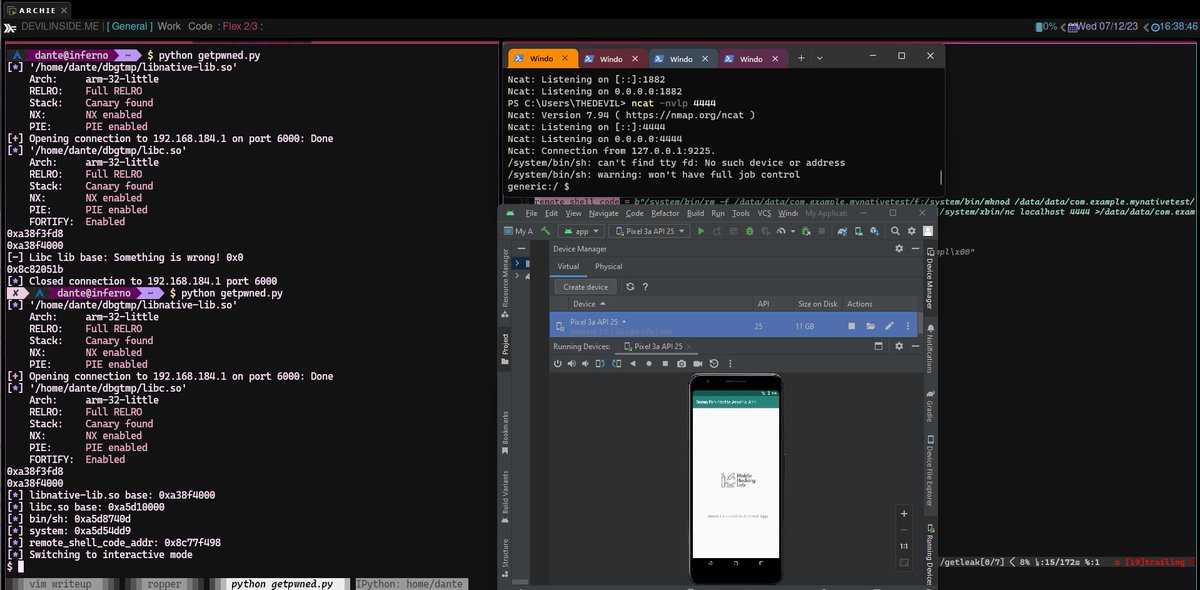
a writeup for mobilehackinglab.com's "Damn Exploitable Android App" challenge. devilinside.me/blogs/android-…
Here, IDAPython script to count how many times a function has been called. High call count usually points to decryption functions in obfuscated malware. github.com/batcain/idapyt…

🚀 We keep adding more fuel to our growing Spotify channel! 🎵 🤭 Each of our teams has a unique music taste (to say at least) - something you can definitely see reflected in the diverse range of playlists we have curated for y’all. Let’s see... 👀 🤺 Lively songs that make…

Why pay the ransom if you can decrypt your files? 🤔 💸 🕵️♂️ Last month, the PTI team noticed an emergence of a new ransomware dubbed PlutoCrypt. PlutoCrypt is a customized version of an ill-known malware #CryptoJoker. 🃏 It has been observed that the ransomware is targeting banks…

radareorg/radare2 disclosed a bug reported by @echel0n_1881 (CVE-2023-1605) - Patch: github.com/radareorg/rada… huntr.dev/bounties/9dddc… #hunter #infosec #opensource

My latest project, Evasion Escaper! It's a powerful tool that bypasses checks made by the malware to detect if it's running in a sandbox. It includes innovative techniques for DLL tracking and new bypass methods. Check it out and share your feedback! vvelitkn.com/malware%20anal…
Keyword exclude ekledim, keyword listesini deprem ile alakalı kelimelerle güncelledim. Kullanmak isteyen olursa buraya bırakıyorum. github.com/batcain/phishi… Şimdiye kadar bulduğum ve daha sonra bulacağım alan adlarını da aşağıdaki repoya ekliyor olacağım. github.com/batcain/olta
Merhaba, ben x0rz'a ait phishing catcher aracını kullanıyorum. Araç domainlere yeni alınmış sertifika streamini vereceğiniz keywordlere ve tldlere göre filtreliyor. Ancak, exclude mekanizması bulunmuyor. Dolayısıyla epey noise yaratıyor ve manuel kontrol gerektiriyor.
Currently looking for remote mid malware analyst/hunter job alongside reverse engineering, just so you know. End of transmission.
One of the best malware analyst and reverse engineer I know
Currently looking for remote mid malware analyst/hunter job alongside reverse engineering, just so you know. End of transmission.
Today’s #OALABS AMA… Malware Analysis Tips and Tricks 🧨 — One Trick To Level Up Your Reverse Engineering youtu.be/EjVVbM6ub00 — How To Identify Unknown Crypto Functions youtu.be/BGIDMpSztSk — .NET Static Config Extractor Tips youtu.be/n435uL01T_E —

📢📢 2022-2023 dönemi için tanışma toplantımızı gerçekleştirdik 🎉🎊 Güncel sunuma buradan erişebilirsiniz: raw.githubusercontent.com/AUCyberClub/sl…



Hello guys! I created a helper #YARA module that gets the data at the given offset and size. Kudos to @_n1ghtw0lf for inspiring awesome blog post! Here is my blog post: devilinside.me/blogs/configur… You can find used samples and example usages in this repository:github.com/theatha/YARA_f…
. @tmpout'ın volume 1'inden tam 5 yazıyı Türkçe'ye tercüme eden @echel0n_1881 ve @batcain_, devamının da yolda olduğunu söyledi. Şuradan derginizi edinebilirsiniz: - tmpout.sh/1/tr/

United States 趨勢
- 1. #SmackDown 24.6K posts
- 2. #WorldSeries 72.2K posts
- 3. Snell 8,761 posts
- 4. Paolo 12.4K posts
- 5. Halo 141K posts
- 6. Celtics 19.1K posts
- 7. Cole Anthony 1,624 posts
- 8. #TheLastDriveIn 1,549 posts
- 9. Darryn Peterson 1,883 posts
- 10. Jade Cargill 6,219 posts
- 11. Grizzlies 3,834 posts
- 12. Knicks 22.9K posts
- 13. Purdue 6,637 posts
- 14. PlayStation 66.4K posts
- 15. Kyshawn George N/A
- 16. Hugo 48.4K posts
- 17. Yesavage 7,563 posts
- 18. Daulton Varsho 2,247 posts
- 19. Zelina 1,833 posts
- 20. #LetsGoDodgers 6,425 posts
你可能會喜歡
-
 batcain
batcain
@batcain_ -
 Furkan Öztürk
Furkan Öztürk
@furk4n0zturk -
 Kağan IŞILDAK
Kağan IŞILDAK
@kaganisildak -
 meto
meto
@meto0x3d -
 Eren
Eren
@aporlorxl23 -
 Berk Albayrak
Berk Albayrak
@brkalbyrk7 -
 ty
ty
@_theatha -
 Murat Y
Murat Y
@divinepwner -
 sh4d0wless
sh4d0wless
@sh4d0wlesss -
 cyx
cyx
@cyx0d -
 redjh0n
redjh0n
@redjh0nn -
 𝚎𝚌𝚑𝚎𝚕𝚘𝚗
𝚎𝚌𝚑𝚎𝚕𝚘𝚗
@echel0n_1881 -
 ahmet kotan
ahmet kotan
@ahmetcode -
 fatih
fatih
@fatihsnsy -
 Utku Çorbacı
Utku Çorbacı
@rhotav
Something went wrong.
Something went wrong.