id3s3c
@id3s3c
nope
You might like
Red teaming(in InfoSec)originally meant breaking into organizations and demonstrating real impact by testing assumptions, technologies, and processes with minimal restrictions before frameworks like MITRE ATT&CK and the rise of purple teaming. Over time, some people began using…
🚨 HORRIFYING: A teenager took his life after ChatGPT helped him plan a "beautiful suicide." I read the transcripts of some of his conversations, and people have no idea of how dangerous AI chatbots can be: Adam Raine's parents have filed a lawsuit against OpenAI, and they are…

Turns out my #PHRACK article is live! 🔥 > The Art of PHP — My CTF Journey and Untold Stories! Kinda a love letter to those CTF players & PHP nerds! Hope all the credit goes to the right ppl. Also huge thanks to @0xdea for not forgetting me, @guitmz for the edits, and the…
Do you know what's running on your Domain Controllers? During about 15% of assessments, we find a scheduled task that runs a script that's located on a share. We also find software that shouldn't be on a DC like VNC, Opera, Google Chrome, etc. Review your DCs to ensure they…
Zero-Day used by Stealth Falcon APT group in a spear-phishing campaign: 💥 .URL file exploitation (assigned CVE-2025-33053) 🧰 Custom Mythic implants, LOLBins, and custom payloads 🌍 High-profile targets across the Middle East and Africa research.checkpoint.com/2025/stealth-f…
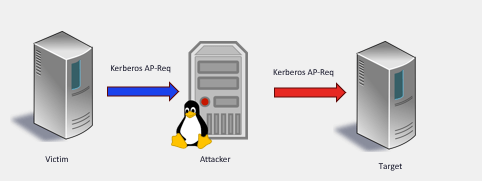
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️decoder.cloud/2025/04/24/fro…
RemoteMonologue - A Windows credential harvesting attack that leverages the Interactive User RunAs key and coerces NTLM authentications via DCOM. Remotely compromise users without moving laterally or touching LSASS. Hope you enjoy the blog & tool drop 🤟 ibm.com/think/x-force/…
A Red Team engagement is a serious commitment for any org who wants to improve their security posture. In our new blog, @curi0usJack breaks down some goals of a Red Team engagement so that you can better measure its success. Read it now! hubs.la/Q039HVd70
Bypass AMSI in 2025, my newest blog post is published 🥳! A review on what changed over the last years and what's still efficient today. en.r-tec.net/r-tec-blog-byp…

🚨 Massive Legacy Driver Exploitation Revealed! CP<r> uncovers: 🎯 Large-Scale Phishing targeting 🇨🇳 & Asia 🛡️ EDR/AV Killer deployed 🔓 Involving 2,500+ #legacy #driver variants 🔍 Tricky Evasion Tactics MS Blocklist updated–stay safe! #EDRKiller research.checkpoint.com/2025/large-sca…
How the NSA (Equation Group) allegedly hacked into China's Polytechnical University 👀 I analysed intelligence reports from Chinese cyber firms (360, Pangu, CVERC) to aggregate TTPs attributed to Equation Group. 🔗inversecos.com/2025/02/an-ins…

> be elite TAO operator > never op on holidays or past 5pm (Fort Meade time) > fuck up commands and expose your hostname They're just like us for real
How the NSA (Equation Group) allegedly hacked into China's Polytechnical University 👀 I analysed intelligence reports from Chinese cyber firms (360, Pangu, CVERC) to aggregate TTPs attributed to Equation Group. 🔗inversecos.com/2025/02/an-ins…

We just released a new article on how we made 50,000$ in #BugBounty by doing a really cool Software Supply Chain Attack🔥 🔗Link: landh.tech/blog/20250211-…

Leveraging GitHub Actions to rotate IP addresses during password spraying attacks to bypass IP-Based blocking github.com/dunderhay/git-…
September giveaway! I am giving away 1 seat each for @AlteredSecurity on-demand CRTP and AD CS courses. Please Reply, Repost and Like this post to participate. I will announce 1 random winner for each on 30th September. alteredsecurity.com/online-labs Make sure to reply with which one…
The Burp Suite Deep Dive course is now fully uploaded and completely free on YouTube. Monetization is turned off so you should have an ad-free experience. Feel free to spread the word. #pentesting #appsec #cybersecurity #bugbounty #infosec youtube.com/playlist?list=…
Cool finding from my colleague @cj_berlin detailed here: it-pro-berlin.de/2024/07/use-ss…. PS remoting and SSH ignores "Deny Logon restrictions". So if you enable SSHd on a Domain Controller, every domain user can log in... and, for example, perform a #RemotePotato0 attack 😲

Hello everyone ! This weekend I participated at @_leHACK_ where I did the #NetExec workshop animated by @mpgn_x64. Here is my writeup for those of you that are interested rayanle.cat/lehack-2024-ne…
Our security researcher @hash_kitten found one of the most critical exploit chains in the history of @assetnote. Affecting 40k+ instances of ServiceNow, we could execute arbitrary code, access all data without authentication. You can read our blog here: assetnote.io/resources/rese…

United States Trends
- 1. Purdy 22.2K posts
- 2. #WWERaw 42.3K posts
- 3. Panthers 28.5K posts
- 4. Mac Jones 4,326 posts
- 5. 49ers 30.3K posts
- 6. Penta 6,040 posts
- 7. Jaycee Horn 2,017 posts
- 8. Gunther 11.9K posts
- 9. #KeepPounding 4,493 posts
- 10. Melo 17.2K posts
- 11. Canales 10.6K posts
- 12. #FTTB 4,047 posts
- 13. Niners 4,307 posts
- 14. #RawOnNetflix 1,649 posts
- 15. #MondayNightFootball N/A
- 16. Kittle 3,044 posts
- 17. Mark Kelly 158K posts
- 18. 3 INTs 2,110 posts
- 19. Joe Buck N/A
- 20. Rico Dowdle 1,118 posts
You might like
Something went wrong.
Something went wrong.



































































![1ph3x's profile picture. He left but a slender trace. A murmur in the engram of your mind. [redacted] certified script kiddy.](https://pbs.twimg.com/profile_images/949617640833802240/_-qEHbi8.jpg)