You might like
🪄 CNBC ranked Wiz among the TOP 5 disruptors for 2023, along with @OpenAI and @canva ✨ Thank you @CNBC for including us on your shortlist and validating our commitment to providing customers with the best cloud security ☁️ 🧙♂️ Why CNBC chose us: bit.ly/cnbcdisruptorw…
Introduction to forensics in the cloud: A container was compromised. What’s next? 🪄 Learn what tools and data you need to use in cloud forensics investigation and how they come into practice in a real-life example 👇 #cloudsecurity #cloud #security wiz.io/blog/intro-to-…
wiz.io
Intro to forensics in the cloud: A container was compromised. What’s next? | Wiz Blog
Learn what tools and data sources you need to use in cloud forensics investigation and how they come into practice in a real-life example.
For companies that are scaling, nothing is more important than building secure, resilient, and efficient infrastructure. @AssafRappaport, CEO of @wiz_io, spoke with AWS' @mosescj58 about scaling businesses securely in the cloud. @AWSSecurityInfo go.aws/3DAsUjM
.@41thexplorer from our Threat Research team is an expert in two things: croissants (🥐) and cloud security (☁️). He'll be at Wiz's #RSA booth 1635! Feel free to ask Alon anything about protecting your cloud environment. Magic password (🔓): #Croissants. We mean, #CloudSecurity.

Introducing the Wiz Admission Controller 🪄 What can it do? 1️⃣ Fine-grained Kubernetes admission control policy 2️⃣ View Kubernetes admission review rates 3️⃣ View your Kubernetes event or create your own custom policies Find out more 👇 #cloud #CISO wiz.io/blog/shift-lef…
🤯 work by the Wiz research team!! #cloudsecurity
Continuing the #BingBang thread, many have asked how we found the vulnerable Bing Trivia endpoint. Let me share our unique Azure Active Directory cloud reconnaissance technique to find misconfigured authentication prompts🧵

🔥Just launched: CISOtopia.com - world's 1st #cybersecurity toy store🧸for CISOs & teams!🎉 🎱Incident Response Magic 8 Ball 🤏Attack Surface Reductor 🌈CISO Juggling Balls 🙈Legal Team Blindfolds & more! Limited stock: 👀
cisotopia.com
Toys | CISOtopia
Toys | CISOtopia
The story of the #BingBang — a Bing.com vulnerability, in less than 90 seconds 🔥👇 Kudos to our fantastic research team! @hillai @shirtamari
Uncover hidden app misconfig risks! 🚀 Wiz Security Graph now reveals host misconfigurations, including new application misconfiguration rules to protect against RCE and information disclosure. Learn more: wiz.io/blog/detect-cr… #cloudsecurity 🔍💥
wiz.io
Detect critical application misconfiguration risks | Wiz Blog
Some application misconfigurations are equivalent to remote code execution or information disclosure vulnerabilities, but often go unnoticed. Wiz’s agentless capabilities detect these and correlate...
Did you know we are a March 2023 @Gartner_inc Representative Vendor in the Market Guide for Cloud-Native Application Protection Platforms report? Find out why: wiz.io/lp/gartner-mar…

Yesterday we published a report on a curious website hijacking campaign we've been monitoring since last October. Our investigation turned up ~10K hacked websites, a few loose ends, and IOCs and samples to check for signs of infection and research further. wiz.io/blog/redirecti…
fun "predictions' article by @rak_garg on the security startup industry in 2023. I too hope for a single big product, rather than a hundred point solutions. And may more people learn from Wiz!🎉 rakgarg.substack.com/p/securitys-fi…

This is a powerful concept wherein given that Wiz is already scanning disk snapshots for vulnerable libraries and malware, it can also scan for application and OS misconfigurations, including custom checks you create, without a performance impact to the running servers.
Say goodbye to tedious config management tasks! Wiz's agentless custom host rules revolutionize the way you manage your infrastructure. No agents or manual commands needed. Create your own rule logic for full coverage across your cloud estate. Learn more: wiz.io/blog/streamlin…
The IBM Cloud security team was super professional; They caught us right after exploiting the first vulnerability but allowed us to continue the research. At the same time, they shared our account id with their SOC team to ignore any malicious-looking activity from our account.
Today we're publicly disclosing #HellsKeychain. We proved that by using a chain of vulnerabilities, it's possible to gain access to an internal CI/CD server & carry out a supply-chain attack against IBM Cloud's managed DB service>>
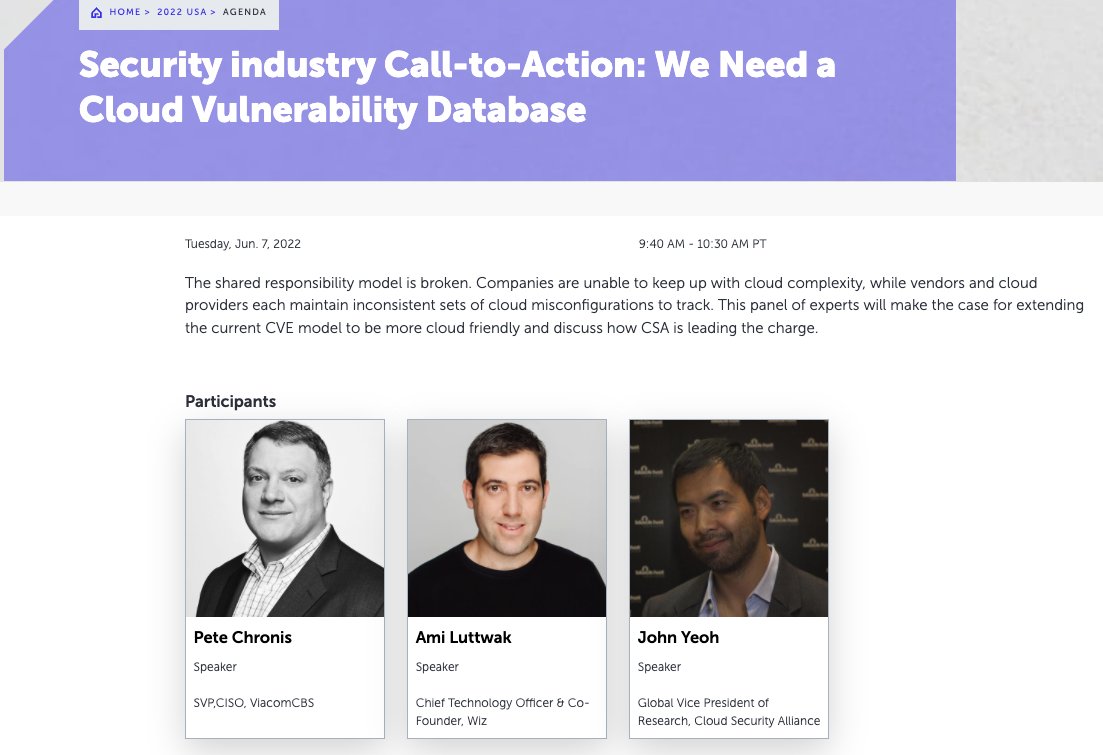
With the release of today's #ExtraReplica Azure vulnerability, and its lack of CVE, we'd be remiss if we didn't mention that @amiluttwak, @chronis and @YoTheShow will be at #RSAC to discuss why the industry needs a CVE-like database for cloud rsaconference.com/usa/agenda/ses… #nottooearly
We gathered 350+ Wizards in Miami this week for our first ever company kick-off. Incredible that it's only been two years since @assaf_rappaport, @amiluttwak, @c0stica and @ReznikRoy founded Wiz. And look at us now! #welcometomiami



Proud to be named one of the top 30 #Cybersecurity Company set to blow up in 2019 by @businessinsider. #deceptiontech #attacksurface #nofalsepositives okt.to/9GkpPe

What about the other 64%? Click to discover why only 36% of Ponemon Survey respondents felt their #security team is effective in detecting & investing #cybersecurity incidents before serious damage occurs okt.to/e3tWjN #ponemon #cyberthreats #databreach @PonemonPrivacy

United States Trends
- 1. Washington Post N/A
- 2. WaPo N/A
- 3. Bezos N/A
- 4. #NGWSD N/A
- 5. The Post N/A
- 6. Ryan Routh N/A
- 7. Maxine Waters N/A
- 8. Scott Bessent N/A
- 9. #NSD26 N/A
- 10. #WorldCancerDay N/A
- 11. Mickey Lolich N/A
- 12. National Signing Day N/A
- 13. Frisco N/A
- 14. Meeks N/A
- 15. Emre N/A
- 16. #ForeverWithYouTH N/A
- 17. taehyun N/A
- 18. Secretary Bessent N/A
- 19. #텬냥이생일_모아가_축하한다고냥 N/A
- 20. Frank Reich N/A
Something went wrong.
Something went wrong.