You might like
Threat Actors when they trip the EDR
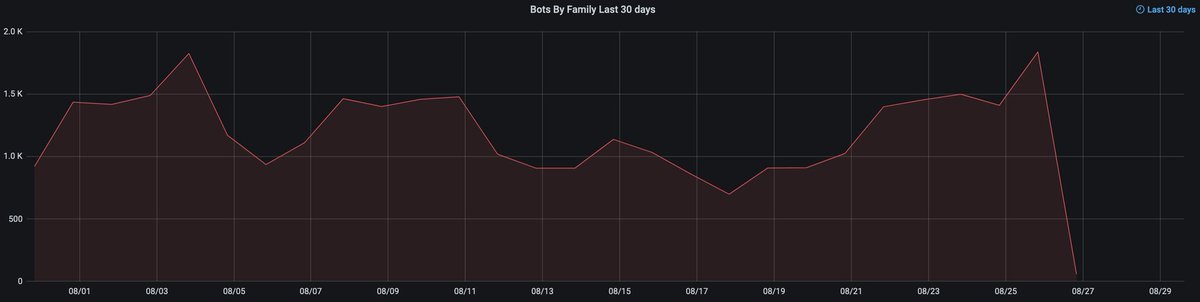
The Operation Duck Hunt 🎯🦆 #QakBot takedown, from a perspective of bot (victim) connections to recently-polled active C2s. Things started to go south around 20:30 UTC on Friday evening (25 August). team-cymru.com/malware-and-bo… #BARS
🎯#Qakbot Botnet Takedown in Operation Duck Hunt! 💻 700,000 Victim Computers 💰 $8.6m in cryptocurrency seized by DOJ 💰 Qakbot has earned $58m in ransoms 🔒 Qakbot used by Conti, ProLock, Egregor, REvil, MegaCortex, and Black Basta ransomware groups justice.gov/usao-cdca/pr/q…
🌐 #Ransomware Groups Statistics May 2023: - Lockbit: 77 🔻 - BlackCat: 42 🔻 - Royal: 31 🔺 - Play: 23 🔺 - BianLian: 22 🔺 - Akira: 21 🔺 - Medusa: 14 🔺 - Black Basta: 12 🔻 - Trigona: 10 🔺 - 8Base: 9 🆕 Total Victims: 351 (April 347) 🔺 ➡️ DARKFEED.IO

De Digger A search/discovery engine that allows you to find public files on Google Drive dedigger.com #OSINT
#OffensiveCon23 recordings are now live! Hope you enjoy :) youtube.com/playlist?list=…
*hacker voice*: "I'm in"
Hello. This is a message to the many up and coming ransomware groups we see. STOP. USING. BABUK. It is buggy. It fails decrypting large files and other edge cases. If you're going to be a criminal group, do it correctly. Your victims won't be able to recover files, dumbie.
Major concerns as Google is launching new #TLD s .zip and .mov which are valid file endings as well. Expecting frequent use for #phishing.
Today, Google Registry is launching eight new top-level domains: .dad, .phd, .prof, .esq, .foo, .zip, .mov and .nexus. Learn more ↓ blog.google/products/regis…
SparkRAT Infrastructure 🔍 There's been some excellent reporting on SparkRAT, but I have yet to find steps to identify possible infrastructure. The below Shodan query uses the default port, 8000, and HTTP response to identify servers. *Manual verification may be needed.

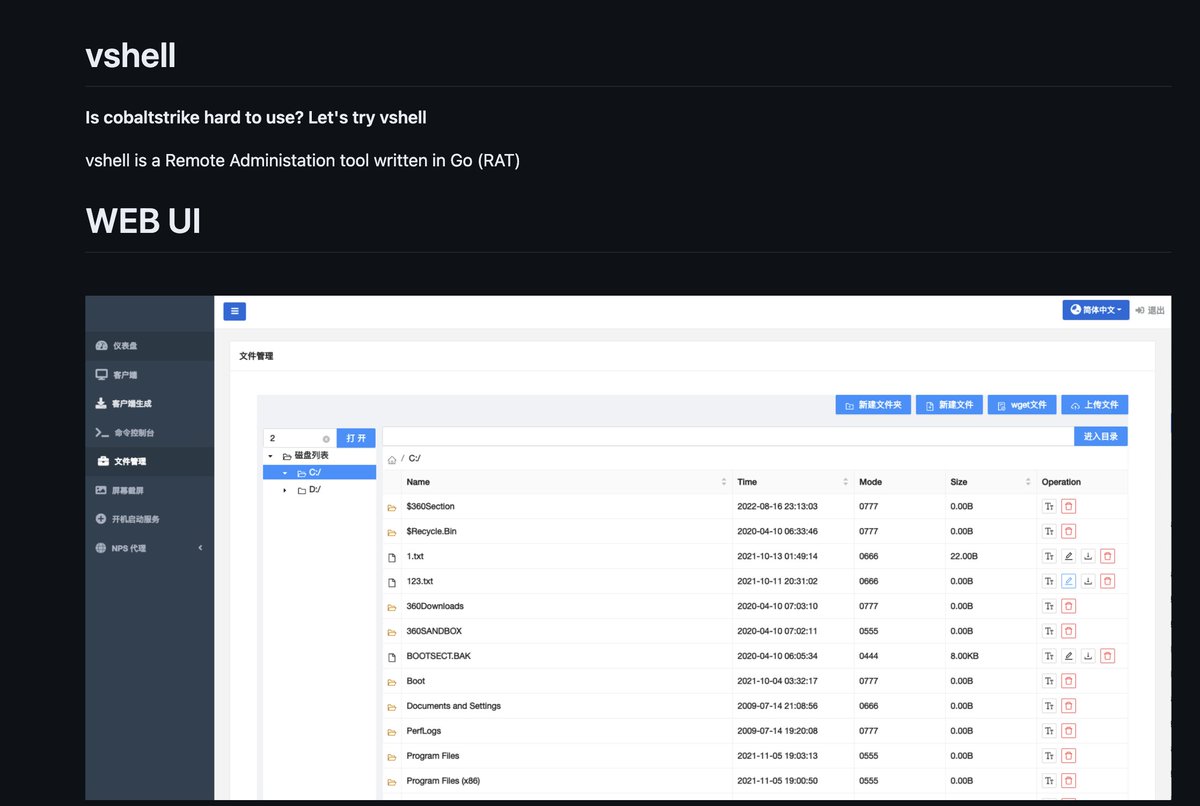
Vshell infra 🎯 073fb179ccb5a8ecad40fad2c940ef3bd3ce06f1 search.censys.io/search?resourc… "Is cobalt strike hard to use? Lets try vshell" vshell is a remote administration tool written in Go (RAT) github.com/veo/vshell/blo… 8.222.140.105 39.98.173.197 43.136.116.140 45.76.97.205…

Go-Based #Kaiji #botnet #malware aka #Ares group Total Active C2 Panel count is (13)👇 threatfox.abuse.ch/browse/malware… which owns multiple botnets and provides rental services for #DDoS #attacks. Payload hosted Link: 154.19.243.107:8868 154.7.10.30:89 cc: @r3dbU7z



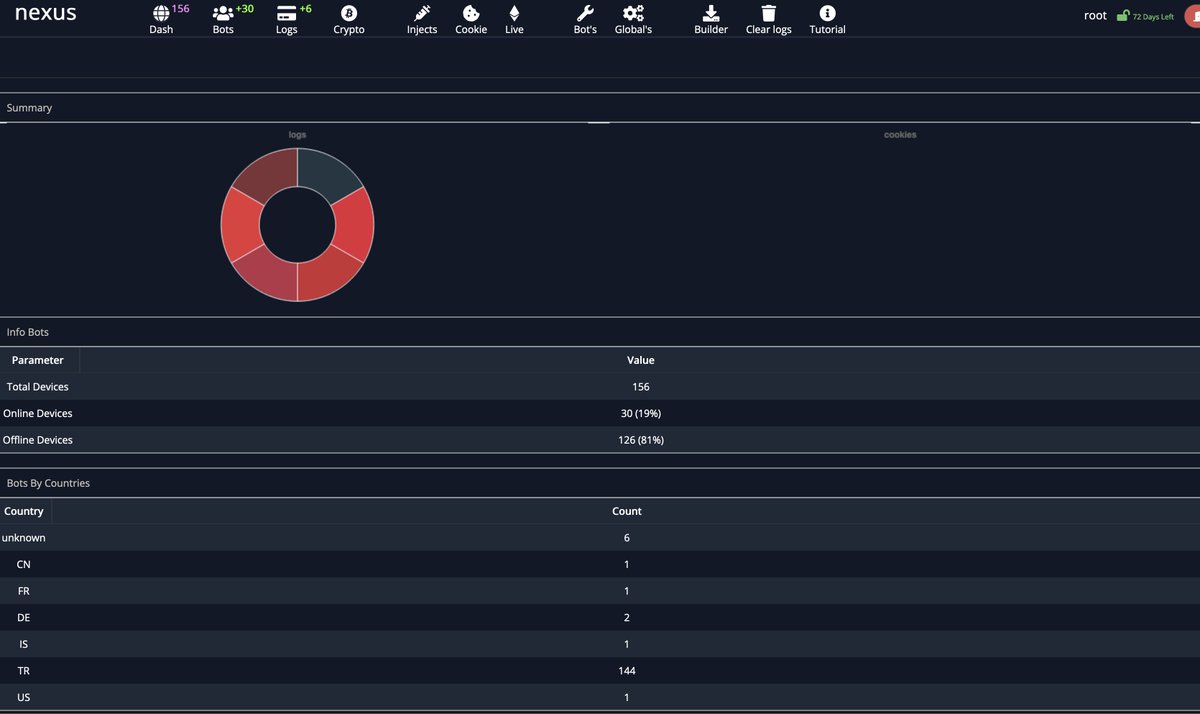
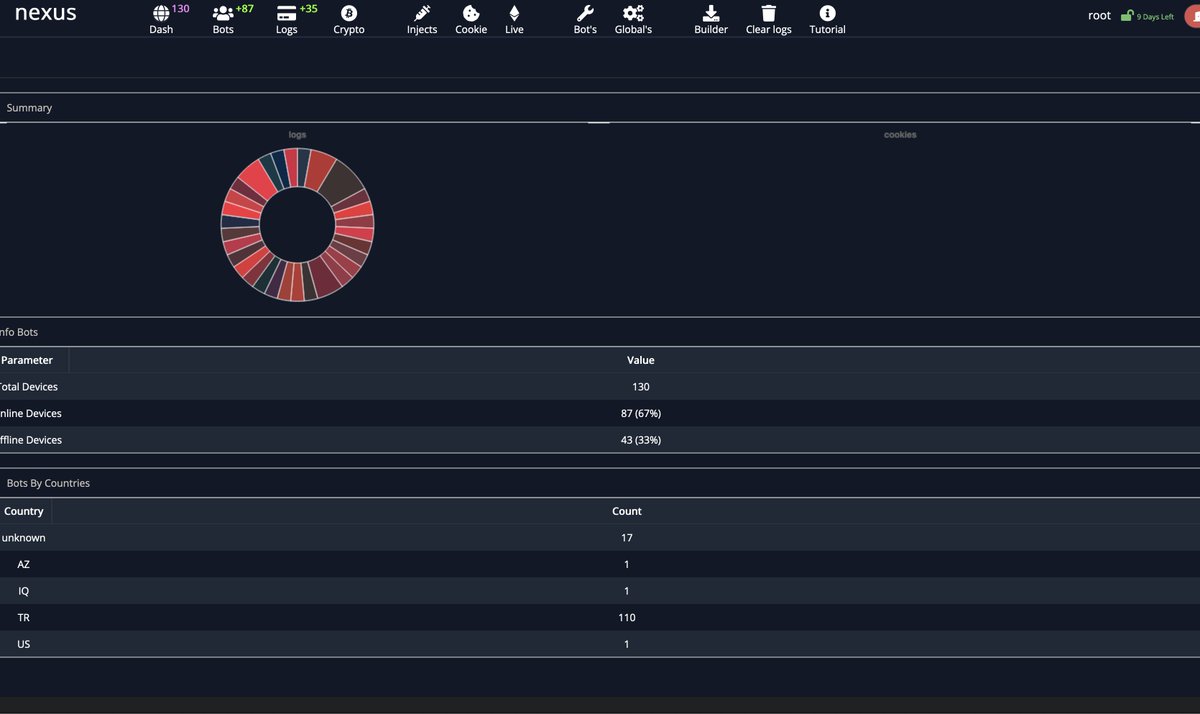
Currently #Nexus #Android #Banking #Botnet Targeting Turkey | Threat actor made turkey injects. cc: @TheHackersNews @3xp0rtblog


Very intelligent #android #malware actor filming his #C2 and giving away the URL. Targeting #spain and #portugal it seems. C2: hxxps://190.211.255.218/YTFlMzViNjNiNWM3/OTI0NGRhMTFlMDNk/index.php Probably: #Octo / #Coper android banker. malpedia.caad.fkie.fraunhofer.de/details/apk.co… @1ZRR4H…
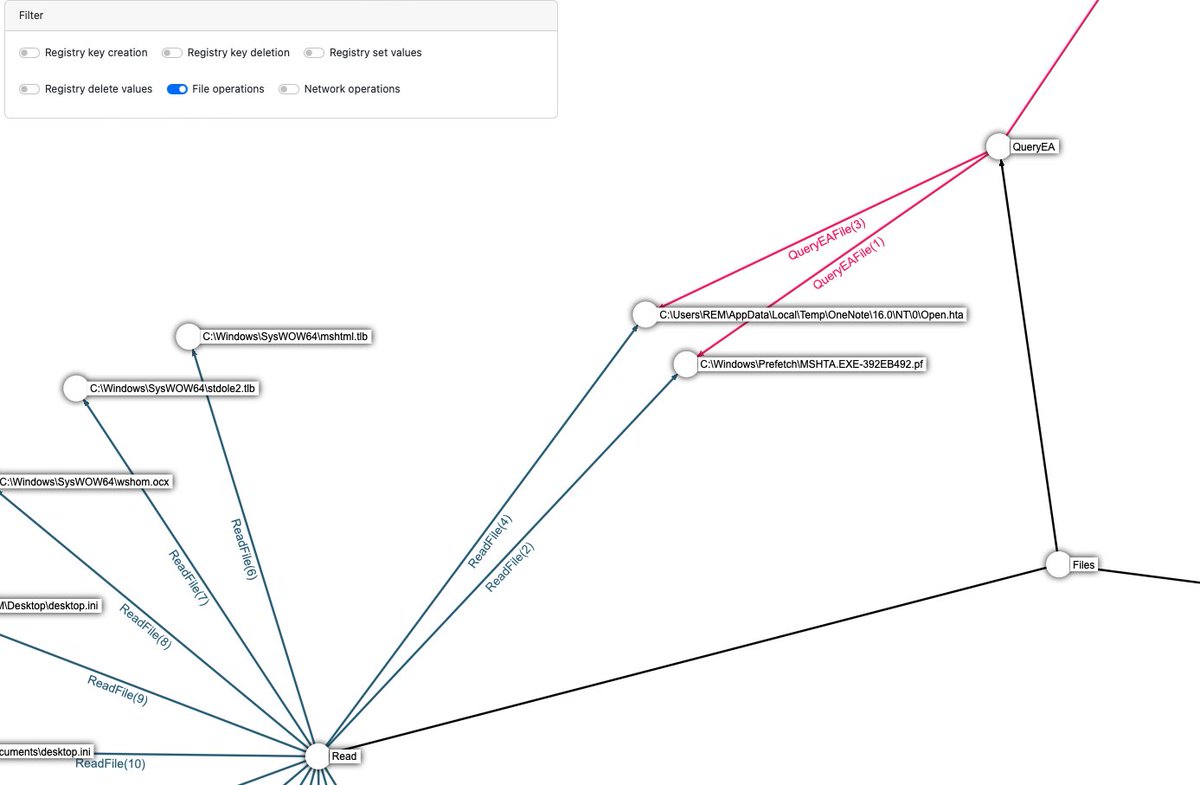
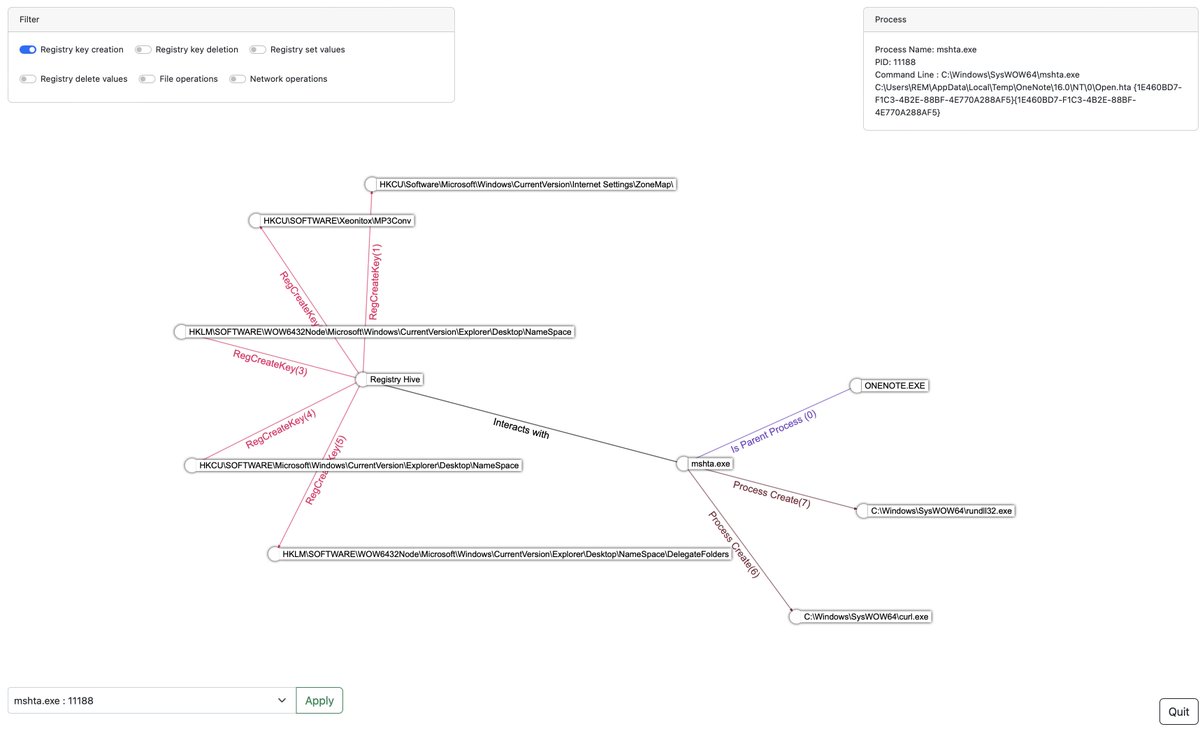
I am happy to release a new malware analysis tool. VISION-Process. A fast and cross platform Procmon visualization application written in Rust & TS. github.com/forensicxlab/V… An demo with QBOT : forensicxlab.com/posts/vision-p… Happy Hunting ! @pr0xylife #DFIR

Recent #truebot #malware activities #silence b7fed593e8eb3646f876367b56725e6c dbecfe9d5421d319534e0bfa5a6ac162 82d4025b84cf569ec82d21918d641540 ee1ccb6a0e38bf95e44b73c3c46268c5 c2: qweastradoc.]com (92.118.36.]213) Currently 54 infections See: huntress.com/blog/investiga…
![ViriBack's tweet image. Recent #truebot #malware activities #silence
b7fed593e8eb3646f876367b56725e6c
dbecfe9d5421d319534e0bfa5a6ac162
82d4025b84cf569ec82d21918d641540
ee1ccb6a0e38bf95e44b73c3c46268c5
c2: qweastradoc.]com (92.118.36.]213)
Currently 54 infections
See: huntress.com/blog/investiga…](https://pbs.twimg.com/media/FopZtm6X0AA-qzq.jpg)
United States Trends
- 1. #IDontWantToOverreactBUT 1,222 posts
- 2. Thanksgiving 144K posts
- 3. #GEAT_NEWS 1,404 posts
- 4. Jimmy Cliff 23.6K posts
- 5. #WooSoxWishList 1,965 posts
- 6. #MondayMotivation 13.3K posts
- 7. #NutramentHolidayPromotion N/A
- 8. DOGE 230K posts
- 9. Victory Monday 4,196 posts
- 10. $ENLV 18.2K posts
- 11. Good Monday 51.7K posts
- 12. Monad 171K posts
- 13. TOP CALL 4,892 posts
- 14. Justin Tucker N/A
- 15. Feast Week 1,916 posts
- 16. The Harder They Come 3,558 posts
- 17. $GEAT 1,311 posts
- 18. $MON 33.3K posts
- 19. AI Alert 2,989 posts
- 20. Soles 99.2K posts
You might like
-
 Taisiia G.
Taisiia G.
@cyberhust1er -
 Baranduin
Baranduin
@Baranduin23 -
 Who said what?
Who said what?
@g0njxa -
 Lyn
Lyn
@Lucifer_UD -
 Livia
Livia
@liviatibirna -
 Francisco Dubois
Francisco Dubois
@synfinner -
 Hacking y Mas
Hacking y Mas
@hackingymas -
 Ususamah
Ususamah
@Ususamah2nd -
 Rolf
Rolf
@Rolf_Govers -
 Scritches JRC
Scritches JRC
@scritches -
 Goriyona
Goriyona
@goriyona -
 crudd (@[email protected])
crudd (@[email protected])
@crudd_re -
 v0lundr
v0lundr
@v0lundr_ -
 Aidan H
Aidan H
@thehappydinoa -
 ian_chen
ian_chen
@ianchena
Something went wrong.
Something went wrong.