Prerak Mittal
@masquerad3_r
Security Research @ CISPA || Co-Founder @DCG91135 || Automating life with Python and Go
你可能會喜歡
Hey, don't miss Tim's YuraScanner presentation today at 11:40 in session 2B, "Web Security" at NDSS '25! Our new task-driven web security scanner features LLM, XSS, and a pinch of 0-days.

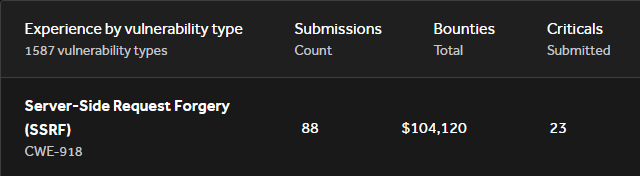
I've made over 100k on SSRF vulnerabilities. They aren't always as simple as pointing it at localhost or AWS Metadata service. Here are some tricks I've picked up over the past 5 years of web app testing:
$15k+ Worth of IDORs in the past couple of months; it takes a lot of manual verification, but use this regex in BurpSuite in order to filter out potential parameters: (?i)\b\w*id\b(?!\w)\s*=\s*("[^"]*"|'[^']*'|[^&\s}]*) #bugbountytips #CyberSecurity
![moblig_'s tweet image. $15k+ Worth of IDORs in the past couple of months; it takes a lot of manual verification, but use this regex in BurpSuite in order to filter out potential parameters:
(?i)\b\w*id\b(?!\w)\s*=\s*("[^"]*"|'[^']*'|[^&\s}]*)
#bugbountytips #CyberSecurity](https://pbs.twimg.com/media/F1-9kFVWYAQI5s1.jpg)
📣 Stealth and supercharging your offensive security testing using: 🔥 Axiom 🔥 by @pry0cc & @0xtavian Resources and musings on this epic framework. 👇a thread👇
💰 New article by our researcher Andrey Bachurin: "Binance Smart Chain Token Bridge Hack" The article explains the technical details of one of the largest cryptocurrency hacks ever. Read the blog post: swarm.ptsecurity.com/binance-smart-…
🔍 My ultimate workflow for simple and easy JavaScript Analysis ⚡️ Comprehensive JavaScript analysis in offensive security, appsec testing, and red teaming wins. Often you can find juicy hidden endpoints, parameters, & domains buried JS! A thread 🧵 1/x 👇
Are you constantly struggling to keep up with the information security cyber security, bug bounties…the list goes on 🙄 So much info but such little time ⏱️ Check out the newsletters I use the most to keep up with the industry below 📬 A thread 🧵 1/7
I don't think this blog post has been shared enough times, but this is what got me into smart contract security, I have read it countless times. Written by code4rena's #1 @cmichelio cmichel.io/how-to-become-…
7 projects that will improve your subdomain enumeration game today ⚒️
If you want to master SSRF, open this thread! Server-Side Request Forgery vulnerabilities are attacks that allow attackers to send arbitrary requests from the server often resulting in gaining authorized access to data!🤯 A Thread 🧵👇
Read my blog on how I was rewarded $$$ for HTTP Request Smuggling leading to webpage defacement: an0nymisss.blogspot.com/2022/08/http-r… Collaborated with @masquerad3_r 🤝
🔥 SQL Injection at Scale🔥 | Powered By @pdiscoveryio | Using a combination of subfinder, httpx, katana, GF, and sqlmap. #bugbounty #bugbountytip #bugbountytips #AppSec #hacker #owasp

taking endpoint parameters and getting sql injection vulnerabilities with sqlmap

None => Critical (10/10) Second Order Account Takeover : (attacker's VERIFIED email attached to attacker's UNVERIFIED email merged can takeover vicitm's VERIFIED account) H1 : Closing as Self Account Takeover (none). Me : Should I Takeover your Account? H1 : Sure! Me : BOOOM

If you want to master API security, open this thread! APIs are used EVERYWHERE for applications to communicate, but let's see how you can HACK them! 👩💻 A Thread 🧵👇
Audited an OSS product running on a Synack target, found over 20 vulns (0 days) including RCE, XXE, path traversal, auth bypass, and many XSS. Hoping to summarize in a blog post once they (and the product) can be safely disclosed. I love this stuff!

In past 2 months I wrote a lot about Smart Contract and Blockchain security. Here is the recap of @SolidityScan blogs. RT if you find it valuable :) A thread 1/12 1) Access Control vulnerabilities in Smart contracts blog.solidityscan.com/access-control… #security #smartcontracts
Add to your list #SQL #injection payload #BugBounty 1%27/**/%256fR/**/50%2521%253D22%253B%2523 == "0\"XOR(if(now()=sysdate(),sleep(9),0))XOR\"Z", === query=login&username=rrr';SELECT PG_SLEEP(5)--&password=rr&submit=Login == ' AND (SELECT 8871 FROM (SELECT(SLEEP(5)))uZxz)
-> On Web App UI 403 Forbidden to low-level user to access this endpoint: /admin/users -> I got API Endpoint : /API/users/v1/users -> 403 Forbidden -> API Endpoint on BurpJSLinkFinder : /API/users/v1/users/basic -> Full organization users email,firstname,lastname,role disclose

Perhaps you already know what IDORs are. They are very COMMON. But did you know about Second Order IDORs? If not, @ozgur_bbh wrote an AWESOME blog about this lesser known class of bugs Read it👇 ozguralp.medium.com/a-less-known-a… #bugbounty #bugbountytips #infosec #CyberSecurity


United States 趨勢
- 1. #UFC322 196K posts
- 2. Islam 310K posts
- 3. #LingTaoHeungAnniversary 648K posts
- 4. LING BA TAO HEUNG 648K posts
- 5. Morales 39.5K posts
- 6. #byucpl N/A
- 7. Ilia 8,904 posts
- 8. Wuhan 11.8K posts
- 9. #GirlPower N/A
- 10. Valentina 16.9K posts
- 11. Prates 38K posts
- 12. #INDvsSA 18.6K posts
- 13. Khabib 15.9K posts
- 14. Georgia 90.5K posts
- 15. Dagestan 4,353 posts
- 16. Dillon Danis 16.2K posts
- 17. Sark 6,442 posts
- 18. Topuria 7,040 posts
- 19. Shevchenko 13.7K posts
- 20. Weili 8,896 posts
Something went wrong.
Something went wrong.






























![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)