You might like
If you found a package.json file in the wild, you might find some internal packages vulnerable to a dependency confusion attack 👀 Check for it quicker using this cool new tool by JSMon: app.jsmon.sh/tools/npm-vali… 👇
I think the top bug hunters should be rewarded by the bug bounty platforms with DATA. I want to know which projects are actually worth my time to audit, not waste hours on trial and error. Give us a transparent list of projects that actually care about security. It’d save a…
REGEXSS: How .* Turned Into over $6k in Bounties Overly-greedy regex replacements can break HTML sanitisation & lead to XSS. Includes a live demo you can try exploiting it yourself! sec.stealthcopter.com/regexss #BugBounty #BugBountyTips #XSS #AppSec
I discovered how to use CSS to steal attribute data without selectors and stylesheet imports! This means you can now exploit CSS injection via style attributes! Learn how below: portswigger.net/research/inlin…

Reporting reflected XSS as critical.

This #NahamCon2025 talk has generated over $50,000 in bounties for @YShahinzadeh and a few other hackers: Puny-Code, 0-Click Account Takeover. 🎥👉🏼youtu.be/4CCghc7eUgI

Full-Width Symbols, a useful cheatsheet to bypass WAF by @therceman

We've updated our URL validation bypass cheat sheet with this shiny Domain allow list bypass payload contributed by @dyak0xdb!

Discover blocklist bypasses via unicode overflows using the latest updates to ActiveScan++, Hackvertor & Shazzer! Thanks to @ryancbarnett and @thecyberneh for sharing this technique. Writeup 👇

Bug Bounty Tip Don't forget to check for the /_wpeprivate/config.json endpoint on a website (usually with WordPress) for information disclosure. Google Dork 👉 Site: *.example.com inurl:"_wpeprivate" Cheers!

Successfully bypassed a SSRF WAF by using a combination of IPV6 + Unicode. Payload for Metadata instances: http://[::ⓕⓕⓕⓕ:①⑥⑨。②⑤④。⑯⑨。②⑤④]:80 Check images for response difference between 169.254.169.254 and the above payload I shared 🔥 #bugbounty #infosec #waf
![HusseiN98D's tweet image. Successfully bypassed a SSRF WAF by using a combination of IPV6 + Unicode. Payload for Metadata instances:
http://[::ⓕⓕⓕⓕ:①⑥⑨。②⑤④。⑯⑨。②⑤④]:80
Check images for response difference between 169.254.169.254 and the above payload I shared 🔥
#bugbounty #infosec #waf](https://pbs.twimg.com/media/F1VWZnOWYAAUC2h.png)
![HusseiN98D's tweet image. Successfully bypassed a SSRF WAF by using a combination of IPV6 + Unicode. Payload for Metadata instances:
http://[::ⓕⓕⓕⓕ:①⑥⑨。②⑤④。⑯⑨。②⑤④]:80
Check images for response difference between 169.254.169.254 and the above payload I shared 🔥
#bugbounty #infosec #waf](https://pbs.twimg.com/media/F1VWZlzX0AEfNq2.png)
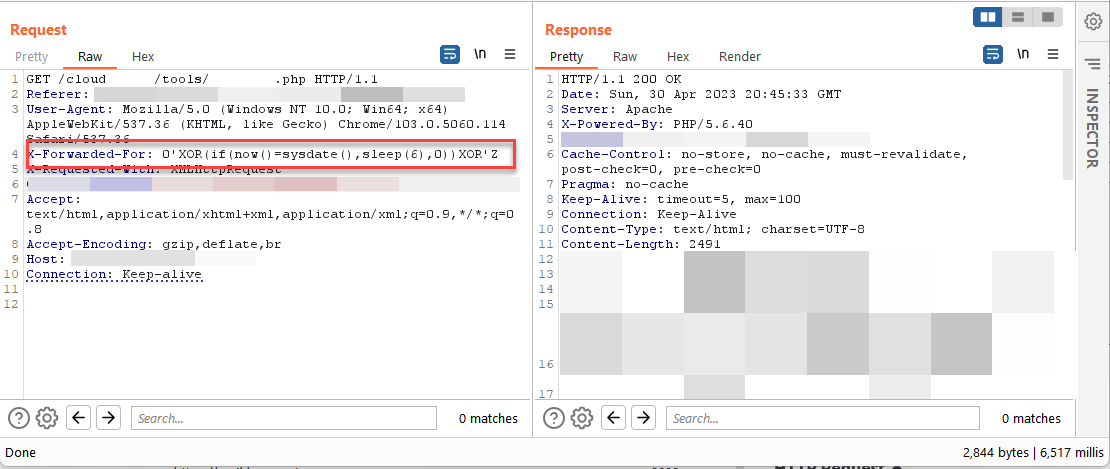
I found 2 Blind time-based SQL Injections in X-Forwarded-For: header just using Burp Intruder. Made a list of 500+ HTTP request and tested one by one for 3+ hours, here is the result.. X-Forwarded-For: 0'XOR(if(now()=sysdate(),sleep(6),0))XOR'Z #BugBounty

☃️ Bug Bounty Reference ☃️ A repository that contains huge list of bug bounty writeups categorized by the bug nature such as ➡️ SQLi ➡️ XSS ➡️ RCE and more ...

GitHub - EmperialX/XSS-Automation-Tool: "XSS automation tool helps hackers identify and exploit cross-site scripting vulnerabilities in web apps. Tests for reflected and persistent XSS. Customize request headers, cookies, proxies, and auth github.com/EmperialX/XSS-…
GitHub - 0xTeles/jsleak: a Go code to detect leaks in JS files via regex patterns github.com/0xTeles/jsleak
I created a repository to keep track of cool XSS payloads github.com/terjanq/Tiny-X… Check this out! credit:@terjanq #xss #bugbountytips

I use this tool regularly! It's very simple, it does reverse DNS lookups as fast as possible. It's a great way of discovering domains and subdomains owned by a company when you know their IP address range(s). github.com/hakluke/hakrev…

when you are looking for bugs like SSRF & Open Redirect. and there is a blacklisted character. try to bypassed using other Unicode characters. I found Open Redirect Bypass Using (。) Chinese dot "%E3%80%82". poc: redirect_to=////evil%E3%80%82com credit:@h4x0r_dz #bugbountytip

Updates & Fixes: 1. Increased the sleeping time between the requests 2. made a checking for the status code == 200 (( that would avoid faking the XSS alerts )) 3. Removed the saving for the nothing results, It's useless option github.com/SirBugs/Xssor.…
United States Trends
- 1. Veterans Day 192K posts
- 2. Veterans Day 192K posts
- 3. Luka 66.8K posts
- 4. Nico 106K posts
- 5. Mavs 23.6K posts
- 6. #csm220 3,153 posts
- 7. Kyrie 5,587 posts
- 8. Dumont 18.3K posts
- 9. #MFFL 1,918 posts
- 10. Wike 42.5K posts
- 11. Vets 18.3K posts
- 12. Venom 16.3K posts
- 13. United States Armed Forces 1,350 posts
- 14. Armistice Day 17K posts
- 15. Mantis 2,873 posts
- 16. Made in China 4,460 posts
- 17. Tomb of the Unknown Soldier 5,538 posts
- 18. Cyclops 3,558 posts
- 19. Shams 3,694 posts
- 20. SoftBank 12.1K posts
You might like
-
 alex
alex
@insertScript -
 Ashar Javed
Ashar Javed
@soaj1664ashar -
 Sasi Levi 🎧
Sasi Levi 🎧
@sasi2103 -
 yappare
yappare
@yappare -
 Jasminder Pal Singh 🟦
Jasminder Pal Singh 🟦
@Singh_Jasminder -
 Roman Shafigullin
Roman Shafigullin
@shafigullin -
 Reginaldo Silva
Reginaldo Silva
@reginaldojsf -
 Stefano Vettorazzi
Stefano Vettorazzi
@stefanovetorazi -
 Ajay Singh Negi
Ajay Singh Negi
@AjaySinghNegi -
 Vignesh Kumar
Vignesh Kumar
@Vigneshkumarmr -
 Andrey Labunets
Andrey Labunets
@isciurus -
 Simone Memoli
Simone Memoli
@Simon90_Italy
Something went wrong.
Something went wrong.
































































































![hunter0x7's profile picture. [Hacker + lover of bash] I Don't know how to hack but i know how to pwnd!](https://pbs.twimg.com/profile_images/1176789748322643968/bEReriMR.jpg)











































