Adam Slowik
@omnitheon
Offensive Security / Threathunter / Detection Engineer / @CDMDepaul and @NationalCCDC Alum
If your agent gets flooded - detect the flooding. If code gets obfuscated - detect the obfuscation. If ETW gets silenced - detect the silence. If the EDR gets killed - detect the killing. If logs get cleared - detect the clearing. The act of hiding is often more suspicious than…
Places on Earth that don't look real - thread 🧵 1. Basilica Cistern, Istanbul

🚨 Top 5 Remote Access Tools Exploited by Threat Actors in the First Half of 2025. ⚠️ While legitimate and widely used by IT teams, Remote Monitoring and Management tools are increasingly used by threat actors to establish persistence, bypass defenses, and exfiltrate data.…

Jim Rohn explains the Secret to making more Money.‼️‼️
⏰ Scott Redler’s #630club - LIVE Stock Market Analysis $NVDA $TSLA $AMZN $SPY ➡️ FREE NEWSLETTER: t3live.com/show x.com/i/broadcasts/1…
With Gemini Live on Google #Pixel9, there’s a whole new way to talk with your phone: goo.gle/3Q8mbDu #TeamPixel
This might be one of the best reddit posts I've seen in a while no cap fr fr

Kobe is a 5x NBA Champion. He also holds the all-time record for missed shots. Babe Ruth is a 7x World Series Champion. He also led the MLB in strikeouts for 5 seasons. Tom Brady is a 7x Superbowl Champion. He also holds the record for most passes intercepted in Superbowl…
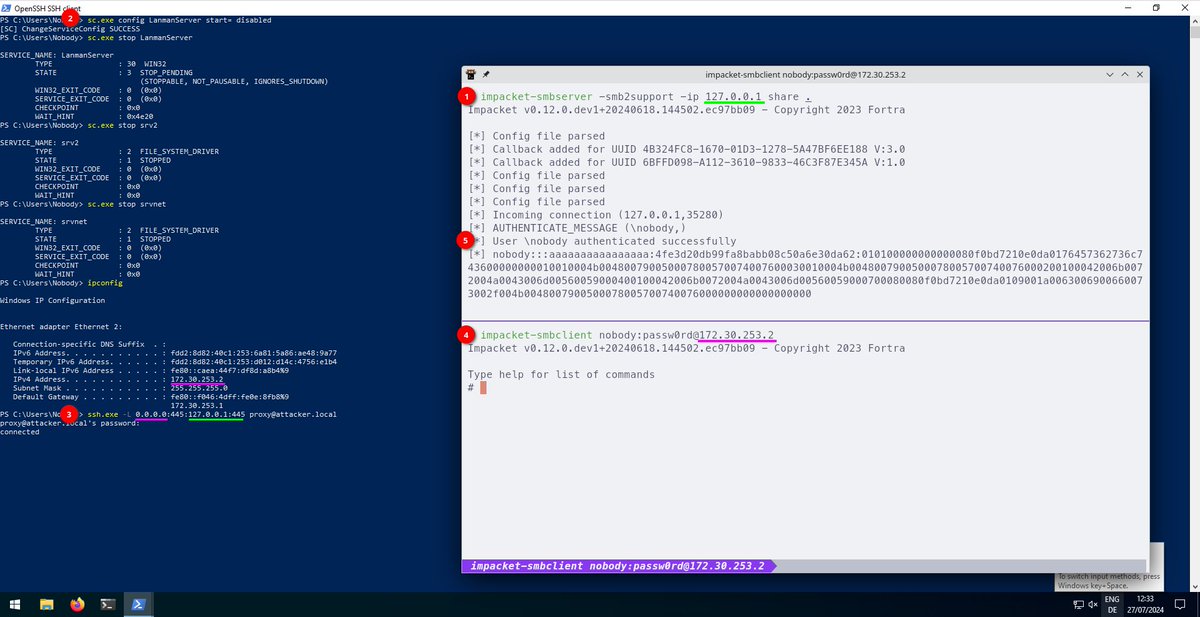
Binding to port 445 on Windows without WinDivert. This is highly useful for NTLM relaying. Big thanks to @zyn3rgy for the talk.
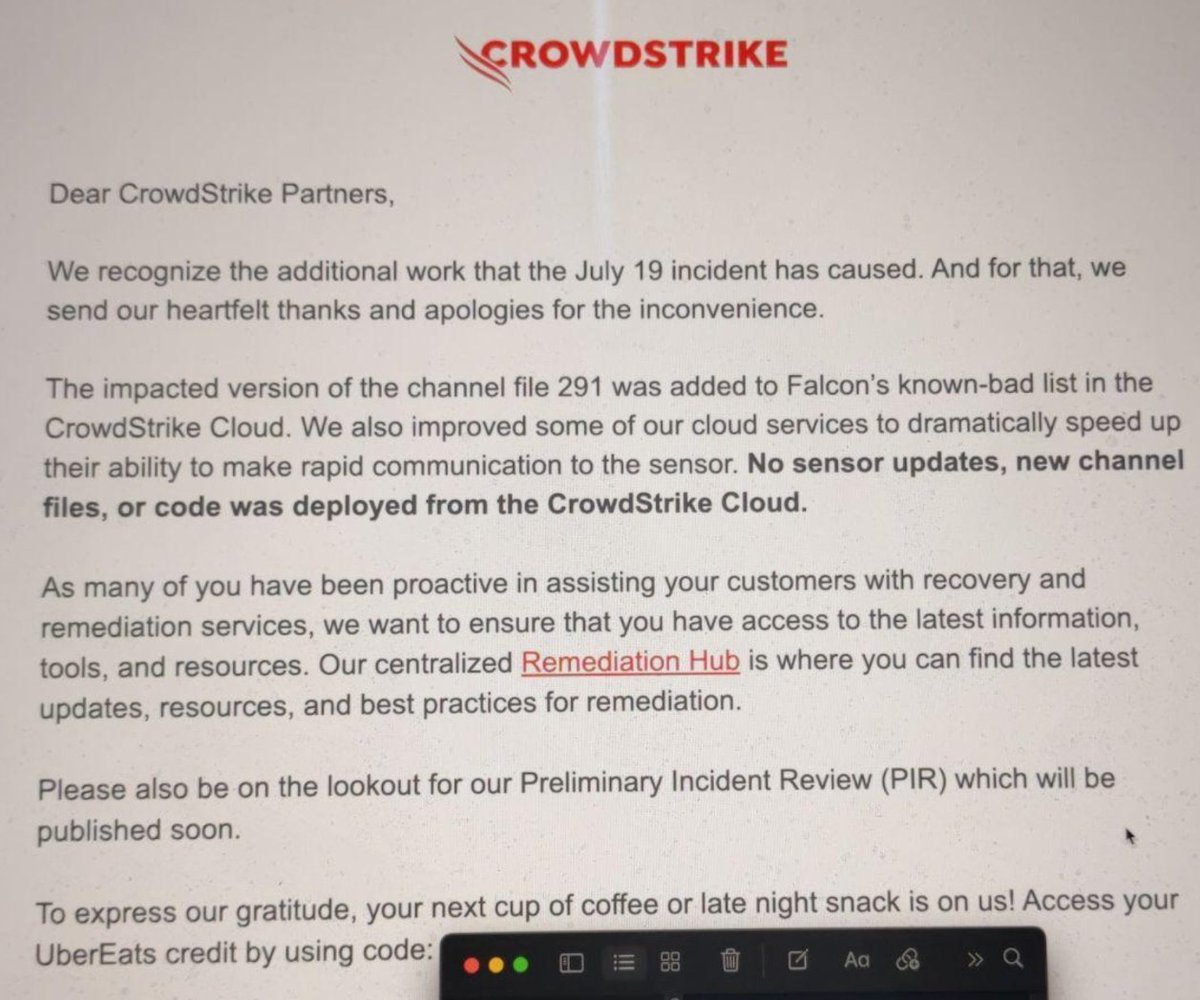
CrowdStrike is offering its partners a $10 Uber Eats gift card as an apology. When TechCrunch checked the voucher, the Uber Eats page provided an error message that said the gift card “has been canceled by the issuing party and is no longer valid.” : techcrunch.com/2024/07/24/cro…
modern cs textbooks should just be this

Lots of interest in LLMs in reverse engineering, but most integrations have been superficial. Want to see how we are pushing the state of the art? See our latest blog post on an upcoming Sidekick feature: binary.ninja/2024/06/28/sid…
If you want to become a world-class programmer, read these 8 books:
ASN enumeration is an important yet frequently overlooked recon method. Finding the ASN can reveal the target's network ranges. Tools include: - asnlookup.com - bgp.he.net - @Yassineaboukir's Asnlookup And more! What tools do you like to use?

Nothing new to be fair. Have seen attackers using Live Response of MDE as well to execute commands, etc.
Abuse of Crowdstrike response shell access for C2. Don't forget that attackers can sometimes use EDRs and other security tools to go from compromising cloud accounts to compromising on-prem machines and user devices.

Moloch, a concept of a self-destructive race to gain rewards, poses a grave threat to humanity. This notion, stemming from an ancient god associated with sacrifice, embodies a race to the bottom with destructive consequences. danielmiessler.com/p/moloch-the-m…
Thanks for sharing. Basically rewrote a large part of my private agent to adapt this and it works wonderful. No more memory toggling. Every function now takes a KnSelf as a first param which is the instance passed. For function like beacon api can use a macro that gets it.



After reading @C5pider's blog I got an idea how to implement global shellcode context without NtProtectVirtualMemory: Add magic header to context struct, place context on stack, append its address to peb.ProcessHeaps and retrieve it from there when needed. No syscalls required.

United States 趨勢
- 1. Jets 104K posts
- 2. James Franklin 37.6K posts
- 3. Drake Maye 11.1K posts
- 4. Justin Fields 20.6K posts
- 5. Penn State 52.2K posts
- 6. Broncos 44.3K posts
- 7. Aaron Glenn 8,657 posts
- 8. Puka 7,212 posts
- 9. Derrick Henry 2,334 posts
- 10. George Pickens 4,014 posts
- 11. Steelers 41.6K posts
- 12. Cooper Rush 1,830 posts
- 13. #RavensFlock 1,654 posts
- 14. Saints 46.6K posts
- 15. Cam Little N/A
- 16. Boutte 2,546 posts
- 17. Tyler Warren 2,020 posts
- 18. Sean Payton 3,673 posts
- 19. London 206K posts
- 20. #DallasCowboys 2,088 posts
Something went wrong.
Something went wrong.